Spliced feed for Security Bloggers Network |
| Verviers again called a terrorist center or not ? [belsec] [Belgian Security Blognetwork] Posted: 29 Apr 2008 06:21 AM CDT | ||
| Feedburner Stat Trouble? [Vitalsecurity.org - A Revolution is the Solution] Posted: 29 Apr 2008 03:32 AM CDT For the last month or so, my Feed subscriber count has been fluctuating wildly - it currently says 1,319 which is correct but (more often than not) keeps showing at around the 900 mark, which is way off the real total. I eventually worked out that this is because Feeburner is having issues with anyone subscribed to the site via Netvibes as they upgrade to their new release. Whoops. Apparently they claim subscribers aren't affected, it just makes your stats look more rubbish than they actually are. I've noticed this sudden drop-off affecting quite a few security blogs out there so if you're wondering where all your subscribers are going, it's down to Netvibes. No ETA on when this will be fixed, which sucks. | ||
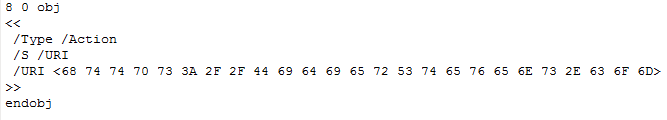
| PDF, Let Me Count the Ways… [Didier Stevens] [Belgian Security Blognetwork] Posted: 29 Apr 2008 01:21 AM CDT In this post, I show how basic features of the PDF language can be used to generate polymorphic variants of (malicious) PDF documents. If you code a PDF parser, write signatures (AV, IDS, …) or analyze (malicious) PDF documents, you should to be aware of these features. Official language specifications are interesting documents, I used to read them from front to back. I especially appreciate the inclusion of a formal language description, for example in Backus–Naur form. But nowadays, I don’t take the time to do this anymore. While browsing through the official PDF documentation, I took particular interest in the rules to express lexemes. There are many ways to write the same token, offering opportunities to evade known-pattern recognition systems, like AV and NIDS. Building a test file Before I show some examples, let’s build a test PDF file that will start the default browser and navigate to a site each time the document is opened. Opening a web page from a PDF file can be done with an URI action, like this:
This is the same type of object used in the malicious mailto PDF files. An action must be triggered by an event, examples of such triggers are the association of an action to the display of a page or the opening of the PDF document. We will use the OpenAction to trigger our URI action object each time our test PDF document is opened:
I add the URI action object and the OpenAction event to the hello world PDF file I used in a previous post, to build our test PDF. You can download all examples here. Opening the test PDF document launches IE:
Now that we have our test PDF, let’s look at the ways we can change its representation without changing its rendering. This is what I’m covering (this list is not exhaustive):
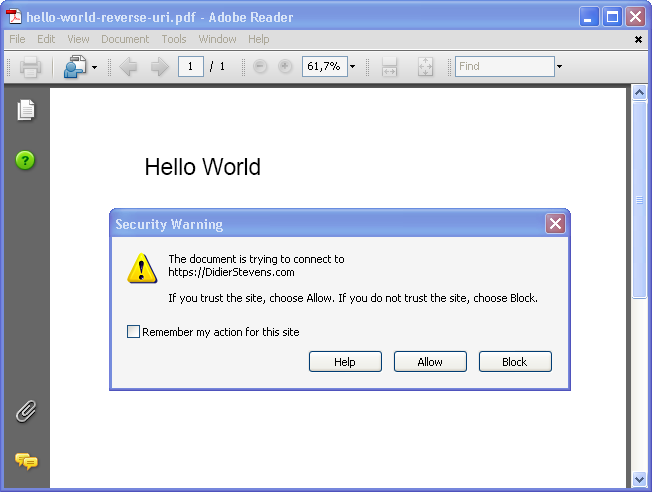
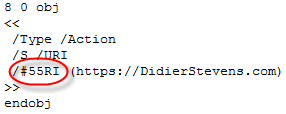
Name representation The tokens preceded by a / (slash) in the URI action object are called Names in the official PDF description. Names are case-sensitive. The characters used in a Name are limited to a specific set, but since PDF specification version 1.2, a lexical convention has been added to represent a character with its hexadecimal ANSI-code, like this #XX. This allows use to rewrite the /URI name in several ways, for example: #55RI.
Or #55#52#49
Pattern matching algorithms must take into account these different representations to successfully match a pattern. A standard way to deal with this is canonicalization. First, the token is reduced to a canonical form (e.g. replace all #xx representations by the character they stand for), and second, pattern matching is performed on the canonical form. String representation Strings too can be represented in many forms. One way to represent strings, is to type the text between parentheses:
Splitting strings over several lines can be done by adding a backslash (\) at the end of each line:
Of course, we are not limited by the numbers of lines, we can add a backslash after each character:
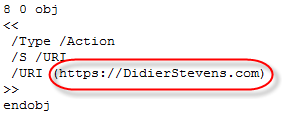
A character in a string can be represented by its octal code, like this:
And this can be done for every character in the string:
One more way to represent a string, is hexadecimal:
You’re allowed to put whitespace between the hex digits:
And you’re not limited in the amount of whitespace you use:
This whitespace usage reminds me of the IE zero-byte trick in html. I want to finish this long list of examples with PDF encryption. One more way to change the representation of a PDF document is encryption. PDFs can be encrypted without requiring the user to provide a password to view the encrypted document, this form of encryption is used for DRM. Ever had a PDF with printing or text copy disabled? That’s an encrypted PDF. When a PDF is encrypted, only the strings and streams are encrypted, the objects themselves are not encrypted. Encrypted strings are one more way to change the representation of a string. Here’s an example:
I know that PDF encryption has already been used to mislead SPAM filters. Final thoughts These many features of the PDF language providing flexibility in representation of names and strings, can also be used to generate polymorphic forms of the same malicious PDF. If you need to scan PDF documents, you need to be aware of all these features and have tools that support them. There are indications that most AV products don’t canonicalize PDF documents prior to signature matching. I did some tests with a malicious mailto PDF document, and changing the string representation of the mailto URI action using the hexadecimal forms allows AV detection evasion. Adding whitespace wasn’t necessary, switching to hex was enough. The ClamAV source code for PDF documents has more evidence of PDF canonicalization issues in AV software, here is a string compare for the Length name without canicalization:
This will not match if hex codes are used (#). I tested all my examples with Adobe Acrobat Reader 8.1.2 and Foxit Reader 2.2 without problems. But Foxit Reader 2.2 gave me an unpleasant surprise, more on this in a next post. I wonder if malicious PDF samples will be used in the Race to Zero.  | ||
| Links for 2008-04-28 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 29 Apr 2008 12:00 AM CDT | ||
| links for 2008-04-29 [Raffy's Computer Security Blog] Posted: 28 Apr 2008 09:33 PM CDT
| ||
| Just Because You’re An Expert Doesn’t Make You An Expert [securosis.com] Posted: 28 Apr 2008 08:14 PM CDT Had another one of those real world experiences today that was just begging for a blog post. A couple hours ago I was driving down the highway on my way to my physical therapy appointment when I saw a rollover car accident on the side of the road near an on-ramp. There were a bunch of bystanders, but the first police officer was just pulling up and there was no fire or ambulance in sight. There is some good news and some bad news if you get in an accident by that particular on-ramp. The good news is it’s right down the road from the Mayo clinic. The bad news is a lot of doctors drive on and off that ramp at any given moment. Very few of them work in the emergency department. I first became an EMT in 1990, went on to become a full-time paramedic, and have dabbled in everything from ski patrol to mountain rescue to HAZMAT over the years. I’m still an EMT, although not doing much with it since moving to Phoenix. If I’d knocked someone up when I got certified they’d be getting ready for college right about now. That is, to be honest, a little scary. Since no responders were on scene yet I identified myself and asked if they needed help. The other bystanders, including the first doctor, stepped back (she was calling the patient’s parents). The patient was looking okay, but not great, crying and complaining about neck and head pain. She did not remember the accident. The next bit went like this:
For the record, I’ve never met an ER doctor in the world that will clear a patient’s c-spine in the field with that mechanism (a rollover) and pain on touch and movement. I would never pretend to be able to anesthetize a patient, but this bozo, like many doctors, thinks he’s fully capable of directing field treatment completely outside his experience. Here’s the thing;as professionals we train hard at becoming experts in a particular domain. This doesn’t make us experts in adjacent domains. For example, I may be a security expert, but despite some broad knowledge I’ve specialized in certain areas, like information-centric security. If, for example, you needed me to read your IDS logs or deploy your UTM I’d send you to someone with practical network security knowledge. When doing risk assessments or practical, on-the-ground security, make sure you engage the right domain experts before you break something. You may have kung-fu, but that doesn’t mean you aren’t a total freaking idiot. | ||
| WAFs , PCI and the United Nations SQL injection [Security4all] [Belgian Security Blognetwork] Posted: 28 Apr 2008 08:14 PM CDT | ||
| Trust, but verify [Kees Leune] Posted: 28 Apr 2008 08:07 PM CDT Someone asked me today if I had contacts in Law Enforcement in The Netherlands. As a matter of fact, I do. The guy (who I only know by his online alias, and "met" only once) wanted me to contact them so I could inform them of a warez site that he knew about, and of a web site that was defaced by the person who operates that site. However, when I asked the person for some evidence to back up his claims, he went quiet. All he told me that "he knew about, but was not connected to the site that was defaced". Obviously, it ended right there for me. It does make you wonder: why does anyone think that I would go to anyone (let alone a law enforcement officer) with a message like: hey, this guy I never met, or have any idea who he really is, would like you to crack down on a site that he claims hosts illegal stuff, but for which he cannot provide any corroborating evidence? Uhuh. | ||
| New Variant of Kraken bot on the loose [Security4all] [Belgian Security Blognetwork] Posted: 28 Apr 2008 07:58 PM CDT | ||
| Presenting Keynote at SANS Toronto 2008 [Andrew Hay] Posted: 28 Apr 2008 07:51 PM CDT
When not presenting I’ll be hanging out at the conference, talking with people, and defending my views on network security. If you’re attending the conference then please pull me aside and say hello. | ||
| Owning Kraken Zombies, a Detailed Dissection [DVLabs: Blogs] Posted: 28 Apr 2008 07:13 PM CDT Posted by Cody Pierce This blog contains the deep technical dive of a two-part blog series exploring the Kraken botnet. See "Kraken Botnet Obervations" for more information regarding general statistics and observations of the botnet. Disclaimer: I don't normally deal with malicious code analysis. My main focuses are on vulnerability discovery and general reversing so dedicating some time to analyzing Kraken was a new and interesting experience. There are many resources available on malware unpacking, PE import table reconstruction etc. so I'll skip right to the specifics of the sample. The offsets and analysis shown below are from sample 31b68fe29241d172675ca8c59b97d4f4 from Offensive Computing. When Kraken first starts it enters an infinite loop trying to locate a master (command and control) server on UDP port 447 over a custom encrypted protocol. The contacted hostnames all reside with dynamic DNS providers with a randomly generated sub-domain. Here is a look at the function responsible for algorithmically generating the domains to connect to, keep a close eye on the second argument which is used as the seed in the generation process: .text:001AE810 mov esi, [ebp+seed] .text:001AE813 sar esi, 1 .text:001AE815 add esi, 0F424Fh .text:001AE81B push edi .text:001AE81C lea ecx, [ebp+var_10] .text:001AE81F mov [ebp+seed], esi ... .text:001AE83D lea ecx, [esi+7] .text:001AE840 lea eax, [esi+0Ch] .text:001AE843 imul eax, ecx .text:001AE846 imul eax, esi .text:001AE849 cdq .text:001AE84A pop ecx .text:001AE84B idiv ecx .text:001AE84D lea ecx, [esi+1] .text:001AE850 imul ecx, esi .text:001AE853 lea ecx, [eax+ecx-0FCFBF88h] .text:001AE85A jmp short loc_1AE87C ... .text:001AE87C imul ecx, 41C64E6Dh .text:001AE882 mov edi, 3093h .text:001AE887 add ecx, edi .text:001AE889 mov eax, ecx .text:001AE88B imul ecx, 41C64E6Dh .text:001AE891 add ecx, edi .text:001AE893 ror eax, 8 .text:001AE896 mov edx, ecx .text:001AE898 imul ecx, 41C64E6Dh .text:001AE89E mov esi, 7FFFh .text:001AE8A3 and eax, esi .text:001AE8A5 ror edx, 8 .text:001AE8A8 and edx, esi .text:001AE8AA imul eax, edx .text:001AE8AD add ecx, edi .text:001AE8AF mov ebx, ecx .text:001AE8B1 ror ecx, 8 .text:001AE8B4 and ecx, esi .text:001AE8B6 sub eax, ecx .text:001AE8B8 push 6 .text:001AE8BA cdq .text:001AE8BB pop ecx .text:001AE8BC idiv ecx .text:001AE8BE add edx, ecx ... The seed is crucial to the position in the control server list and starts at 0 on reboot. At the end of this function we see an array of domain names being access that are appended to the generated name: .text:001AE91D push dynamic_host_names[eax*4] ; lpString .text:001AE924 lea ecx, [ebp+var_20] .text:001AE927 call makeNewString .text:001AE92C push eax .text:001AE92D push [ebp+hostname] .text:001AE930 lea eax, [ebp+var_18] .text:001AE933 push eax .text:001AE934 lea eax, [ebp+var_8] .text:001AE937 push eax .text:001AE938 lea ecx, [ebp+var_10] .text:001AE93B call concatenateStrings .data:001B5064 dynamic_host_names dd offset aDyndns_org .data:001B5064 ; "dyndns.org" .data:001B5068 dd offset aYi_org ; "yi.org" .data:001B506C dd offset aDynserv_com ; "dynserv.com" .data:001B5070 dd offset aMooo_com ; "mooo.com" Each generated host is checked twice before moving on to the next one, here are the first 5 hosts that will attempt to be contacted: rbqdxflojkj.mooo.com bltjhzqp.dyndns.org cffxugijxn.yi.org etllejr.dynserv.com ejfjyd.mooo.com For those who are interested, here is a list of the first 15,000 hosts. Note that as of the time of this research the first Kraken server that was up and responding was 15th down the list afmbtgyktty.yi.org on IP address 66.29.58.119. Armed with this information we registered the first of the available hosts and immediately began getting requests from live Kraken infections in the wild. See "Kraken Botnet Obervations" for more information regarding general statistics and observations of the botnet. Knowing now that it is theoretically possible to overtake the Kraken network the next step is to examine the protocol. Looking through the binary there are several calls on the socket connection it makes over UDP port 447 to the control servers. All of these calls are preceded with a send to the control server with an encrypted header: .text:001A83C5 call getEncryptionKeys .text:001A83CA mov dword ptr [esp+80h+send_buffer], eax .text:001A83CE lea eax, [esp+80h+send_buffer] .text:001A83D2 mov [esp+80h+var_2C], edx .text:001A83D6 mov [esp+80h+var_28], ebx .text:001A83DA mov [esp+80h+var_24], 1 .text:001A83DF mov [esp+80h+var_23], bl .text:001A83E3 mov [esp+80h+var_22], 137h .text:001A83EA mov [esp+80h+var_20], ebx .text:001A83EE mov [esp+80h+var_1C], ebx .text:001A83F2 call encryptHeader ... .text:001A8418 push 10h ; tolen .text:001A841A lea eax, [esp+84h+to] .text:001A841E push eax ; to .text:001A841F push ebx ; flags .text:001A8420 push 18h ; len .text:001A8422 lea eax, [esp+90h+send_buffer] .text:001A8426 push eax ; buf .text:001A8427 push [esp+94h+s] ; s .text:001A842B call ds:sendto As we can see (note that all of the symbols were manually added through reverse engineering) we get some sort of encryption key, build the header, and encrypt the header before sending. Obviously we have to figure out the encryption so we can get a better look at the command and control protocol. I have seen some mention and packet dumps of the header on various blogs. They often state the first 8 bytes of kraken traffic is static and there is a simple reason for this. Kraken, when communicating, prepends its encryption keys so the server can properly decrypt/encrypt traffic. We can see this in the getEncryptionKeys function. It is host specific and computes the 64 bit key from various aspects of the host hardware. Abbreviated pseudo code for the function is below. mov ds:encryption_key_1, 0DCBA2C5Ah mov ds:encryption_key_2, 50E41593h GetAdaptersInfo() while (*adapter_info != 0) { for (i=0; i < adapter_info.AddressLength; i++) {... } adapter_info = *adapter_info } encryption_key_uno += cpuid(0x0).max_input_value encryption_key_dos += cpuid(0x0).inel encryption_key_uno ^= cpuid(0x1).version encryption_key_dos ^= cpuid(0x1).features encryption_key_uno ^= cpuid(0x3).hi_serial encryption_key_dos ^= cpuid(0x3).low_serial encryption_key_uno -= GetVolumeInformation(GetWindowsDirectoryA()).VolumeSerialNumber As previously stated we can easily get the encryption keys from the packets sent to our tap resolved from the dyndns names we registered. This is a good starting point for writing our decryption/encryption routines. At this point we know the traffic is encrypted, we know a header is sent to the remote dyndns server, and we know that in order to see into this traffic on a large scale we must decrypt the traffic. The function for decrypting our header is shown here: .text:001AE7E4 decryptHeader .text:001AE7E4 push ecx .text:001AE7E5 mov eax, [esi+packet_data.seed] .text:001AE7E8 test eax, eax .text:001AE7EA jz short loc_1AE802 .text:001AE7EC push 1 ; flag .text:001AE7EE push eax ; seed .text:001AE7EF push [esi+packet_data.key_2] ; key_2 .text:001AE7F2 lea eax, [esi+packet_data.command] .text:001AE7F5 push [esi+packet_data.key_1] ; key_1 .text:001AE7F7 push 0Ch ; count .text:001AE7F9 push eax ; offset .text:001AE7FA call decryptPacket .text:001AE7FF add esp, 18h .text:001AE802 .text:001AE802 loc_1AE802: .text:001AE802 and dword ptr [esi+8], 0 .text:001AE806 pop ecx .text:001AE807 retn .text:001AE807 decryptHeader endp So we call another function that is used in various places in the binary called decryptPacket passing in various data to specify what we are decrypting. The decryptPacket is a larger function that is a pretty straight forward encryption routine. It does not appear, in my opinion, to be based off of any open encryption algorithm (I will skip the details of the encryption for brevity). After writing the decryption for the header we can see more of the protocol. The first packet being sent by this bot correlates to what we saw in the disassembly above. ac 8d ee d7 94 49 09 3f 00 00 00 00 01 00 37 01 00 00 00 00 00 00 00 00 The protocol breaks down as follows. struct KrakenHeader {unsigned int key_1; unsigned int key_2; unsigned int seed; unsigned short command; unsigned short version; umsigned int size; unsigned int crc; unsigned char payload[size]; } kraken_header; So obviously we head off to see what the commands do. In the main command processing function we see a branch based off the command in our incoming packet. .text:001AC170 mov eax, [esp+2C0h+command] .text:001AC174 sub eax, 7 .text:001AC177 pop ecx .text:001AC178 pop ecx .text:001AC179 jz command7 .text:001AC17F dec eax .text:001AC180 jz command8 .text:001AC186 sub eax, 10h .text:001AC189 jz command18 .text:001AC18F xor esi, esi .text:001AC191 cmp ds:dword_1B109C, ebx .text:001AC197 mov [esp+2B8h+var_2A5], bl .text:001AC19B jle short loc_1AC1D7 ... This is certainly not a complete list of the commands, but it leads us to an interesting function. If we follow command8 we notice a method for updating the bots code. The code takes in an XML-like list of modules, module names, ids, etc. and from there processes the items looking for any updates. Analyzing the code reveals that the following format must be utilized to reach the code we are after: <modules> <module> <version>0</version> <name>core</name> <moduleid>1</moduleid> <crc>0</crc> </module> </modules> The reason for this is when the bot sees that a "core" module is being sent it will download said module, write it to disk, and execute it. In the code you can also determine that the values for version, moduleid, and crc are not really checked when a "core" module is being loaded (Aside from not being 0 in some cases). At this point we realize (and confirm our assumption) that code can arbitrarily be downloaded and executed on the zombie host as long as we can receive its initial beacon. In order to demonstrate this I have removed the details but outlined the needed steps below.
After the zombie has received the payload it decrypts it, and runs a CRC on the payload ensuring it matches what is in the header. This CRC is fairly simple and is below in Python. for x in range(0x100): eax = x for x in range(8): if (output.byte(eax) & 1) == 0: eax >>= 1 else: eax >>= 1 eax ^= 0xedb88320 xor_array.append(eax) eax = ~flag ecx = 0 for x in range(fsize): esi = (0x00000000 | struct.unpack("<B", f[x])[0])edx = eax edx &= 0xff edx ^= esi eax = output.dword(eax) >> 8 eax ^= xor_array[edx] crc = ~eax return output.dword(crc) If we pass the CRC check the payload gets written to a random name in c:\windows\system32 and executed. This can be seen in the binary below. .text:001ADE8C call openWriteFile .text:001ADE91 add esp, 0Ch .text:001ADE94 push 0FFFFFFFFh ; dwMilliseconds .text:001ADE96 push ebx ; char .text:001ADE97 push [ebp+lpCommandLine] ; lpCommandLine .text:001ADE9A call startNewProcess ; do our command Where CommandLine is the path to our newly downloaded payload. As you can see it is certainly possible to upload new code to a bot as long as you can receive traffic from a zombie checking in. To demonstrate this I have created a video that puts all these steps into practice loading arbitrary code on a zombie host running in a VM. http://dvlabs.tippingpoint.com/pub/cpierce/owning_kraken.swf The video first walks you through the code path which will be executed. The video shows two systems. The host system is responsible for emulating the Kraken server. The VMWare image is of a system infected with Kraken. In the end the video will demonstrate a custom Kraken server I have written and the Kraken zombie will eventually spawn a reverse connect back shell that I have uploaded to it via the emulated Kraken server. The shell demonstrates full control over the zombie system. Note: The code used to accomplish the various tasks outlined in this blog are not being released for obvious reasons. If you are a security firm with legitimate reasons for further information and proof-of-concept code contact us. | ||
| Kraken Botnet Infiltration [DVLabs: Blogs] Posted: 28 Apr 2008 07:03 PM CDT Posted by Pedram Amini Earlier this month a number of articles surfaced on the research and disagreements with regards to the size and classification of a large bot net named Kraken. At the front line of the debate was SecureWorks and Damballa. Secureworks claims Kraken is actually Bobax and estimates the bot net to include over 185,000 compromised systems. Damballa disagrees stating that Kraken is an entirely new bot net with a size over twice as large as Storm. Semantics aside no one disagrees that Kraken/Bobax is among the largest of the known bot nets if not the largest. Cody and I thought it would be interesting to examine Kraken with the specific goal of infiltrating the bot network. We started with a sample from Offensive Computing and working from there eventually concluded that we would indeed be able to infiltrate and take over increasingly larger portions of the Kraken bot net. Cody did most of the manual labor of protocol dissection, reverse engineering the encryption routines and eventually creating a fake Kraken server capable of overtaking a redirected zombie. His detailed write up on the reverse engineering process is available under "Owning Kraken". The key to overtaking the botnet is understanding how the overall client-server architecture works. Kraken infected systems attempt to "phone home" to a master command and control server by systematically generating sub-domains from various dynamic DNS resolver services such as dyndns.com. By reverse engineering the list of names and successfully registering some of the sub-domains Kraken is looking for, we can emulate a server and begin to infiltrate the network zombie by zombie. Stated simply, Kraken infected systems world wide start to connect to a server we control. We monitored Kraken connections for a period of one week (seven days). In that time we have received over 1.8 million requests from infected systems worldwide. Of these requests over 65,000 came from unique IP addresses. Here is our list of all uniquely infected IP addresses. This number still does not accurately capture the true infection count monitored. Why? Think about the systems who are constantly rebooted, assigned a new IP address and then re-connect to the command and control server. We can do better thanks to the fact that the initial request from the Kraken zombies contains an encryption key generated in such a manner that makes it constant per system but unique across systems (see "Owning Kraken" for further details). Counting at this level of granularity leaves us with 25,000 truly unique infections monitored over seven days ... and growing, we are seeing a fairly uniform number of new infections a day. Applying a reverse DNS lookup over this set of IP addresses reveals that the bulk of the monitored infected user base is home broadband users. The source country distributions break down as follows:  The initial Kraken zombie request also contains a version field which we parsed and found to contain the following distribution:  Various estimates place the overall size of the botnet to be somewhere between 185,000 and 600,000 zombies. This means that within a single week we would have been able to take over anywhere from 4% to 14% of the infected population ... and this is where we entered into a moral dilemma and ethical discussion. We have the ability to successfully redirect infected systems. We have the ability to provide an 'update' through the existing Kraken protocol that can simply remove the Kraken zombie (again see "Owning Kraken" for a video demonstrating this capability). Is it wrong to do so? Although this discussion is similar to that of writing "good worms" that roam the internet patching vulnerable servers, there is a key difference in that a good worm can't be stopped. Once it has been released it is a self spreading uncontrollable entity. In our specific case however we have the ability to cease at any point. It is simply a one to one relationship. An infected system connects to us, we supply a simple binary to kill the target process, we never hear from the infected system again and neither can the actual botnet owners command and control servers. Cody and I both are pro "cleansing". Dave Endler on the other hand is against. The arguments for pro-cleansing are obvious, the arguments against are a little more complicated. The most interesting of points that Dave brought up is the corner case of what happens if we accidentally crash the target system? What if that target system is responsible for someones life support? Yes the system is already infected with a SPAM delivering zombie capable of receiving arbitrary updates from malicious actors, but at least for now it's running and carrying out the rest of it's functionality. As director of DVLabs Dave's opinion overshadows that of our own so we simply sit and monitor. What are your personal thoughts on the matter?  | ||
| decade old votingcode used for next years elections [belsec] [Belgian Security Blognetwork] Posted: 28 Apr 2008 04:57 PM CDT So they go at it once again. The same code that has now been used during more or less a decade will be used again in the next election next year. There was no alternative as the report from the universities is embroiled in controversy (as their choices include things like RFID and very few controls) and the parliaments still have to organize its debate (and wants to hear some experts and other opinions than the traditional 'no problemo'). The question is when because the same parliaments are already pre-occupied with a lot of typical Belgian institutional questions that dominate the politicians and there advisors (while the populations begins to feel the inflation of the prices of basic food and services) If there are code-gurus or fuzzers out there. Here is the code. They say it has been vetted and controlled already several times by so-called auditors by some of the big 4. If you can find a mistake, than you should take someones place over there (joke). http://www.ibz.rrn.fgov.be/index.php?id=66&L=1 If you don't want to send your code remarks directly, we have backchannels if needed. | ||
| PCI Requirement 11.3.2 - Penetration Testing [Trey Ford - Security Spin Control] Posted: 28 Apr 2008 04:51 PM CDT Tod raised a question in response to the PCI 6.6 Information Supplement Released post, a question heard by many QSAs (and several other email responses to that post.) These concerns were echoed by Rory on his blog. First, we need to be current with the ‘Information Supplement: Requirement 11.3 Penetration Testing‘ on the PCI SSC’s website. [...] | ||
| some interesting documents [belsec] [Belgian Security Blognetwork] Posted: 28 Apr 2008 04:42 PM CDT | ||
| OpenID and the Belgian eID [/dev/random] [Belgian Security Blognetwork] Posted: 28 Apr 2008 04:08 PM CDT
In a previous post, I talked about OpenID: This is a single sign on system for a multitude of websites. To perform my first tests, I installed the OpenID plugin on my Wordpress and used an ID created on myopenid.com. It worked pretty well but why not use a strong authentication method with OpenID? By strong authentication, we mean based on something you [know|have|are] combined with something you [know|have|are]. They are several OpenID providers: myopenid.com, myid.net or Verisign (a complete list is available here). I decided to test TrustBearer because they offer strong authentication. Belgium is one of the first countries which offers electronic identify cards (or eID). I assume that the Wordpress plugin is already installed and configured in your Wordpress. To use the TrustBearer services you need:
(Check their website for a full list of supported hardware/cards) When you start the registration process, TrustBearer will ask you to install a plugin (I used Firefox) which will communicate with the hardware (security note: it means that your browser has to have enough rights, this can be a potentiel security problem). Once installed, insert your token or card and give the pin code. Take care, if you give three bad PIN code, your card will be locked! (like a mobile SIMM card). Otherwise, the process is quite easy. Once the registration done, your OpenID url will look something like: “https://openid.trustbearer.com/ “. It’s now time to test with Wordpress. When you access the login screen, you’ll notice a new field where you can enter your OpenID URL. Enter you freshly registered URL and log in. Wordpress will redirect you to the TrustBearer web site and ask you to authenticate yourself using the registered method. After a successfull login, you will be redirected back to Wordpress. Magic! After a few hours, here are some comments: Check out the demo! | ||
| Wait, what? [Vitalsecurity.org - A Revolution is the Solution] Posted: 28 Apr 2008 04:01 PM CDT I got this in my mailbox today: April 28th, 2008 For Immediate Release: Contact: Colonel Custard (aka the corporate criminal creamer) Footage available: www.GreenwashGuerrillas.org Greenwash Guerrillas Pie Thomas Friedman at Brown University YouTube Censors Video; Pie Thrower Faces University Disciplinary Procedures Providence, RI - New York Times columnist and author Thomas Friedman was pied by the Greenwash Guerillas while giving an Earth Day Lecture at Brown University. The Greenwash Guerillas targeted Thomas Friedman because of his support for U.S. military intervention in the Middle East, neo-liberal economic policies that harm the world's poor, and especially for promoting bogus solutions to the global climate crisis. "We sought to expose the hypocrisy of allowing Friedman, who is known for his influential support of U.S. wars for oil in the Middle East, to call himself an environmentalist," explained Greenwash Guerrilla Margaree Little. "He has blood on his hands that no amount of 'green' can wash away." Little, a Brown University student identified as one of the pie throwers, faces University disciplinary hearings, potentially including expulsion. Colonel Custard, the second pie thrower, remains at large. Little and Custard jumped on stage as Friedman began his talk, entitled "Green is the new Red, White & Blue." The talk focused on how green technology and corporate environmentalism can restore the United States to its "natural place in the global order." They tossed two green-colored cream pies at Friedman and dashed off as leaflets denouncing Friedman were thrown to the crowd. According to the pamphlets, "On behalf of the earth and all true environmentalists – we, the Greenwash Guerillas, declare Thomas Friedman's 'Green' as fake . . . as the cool-whip covering his face." The Greenwash Guerillas object to Friedman's support for nuclear power, coal power, industrial biofuels, and carbon trading markets. "These false solutions are smokescreens, intended to generate massive corporate profits while creating global humanitarian and environmental disasters," said Colonel Custard. Video of the pie throwing incident was posted on YouTube, and received close to 70,000 views in 36 hours, making it one of the most popular videos on the site. Without notice, YouTube abruptly censored the video, removing it from the website. Hundreds of news outlets, blogs, and websites had linked to the video. The Greenwash Guerillas have reposted the clip at: www.GreenwashGuerrillas.org "Given the many other pieings on YouTube(1), the removal of the video can only be understood as an act of political censorship," said Little. "One has to wonder whether Friedman, a billionaire with a lot of connections, has more influence than "you" on YouTube." "The Greenwash Guerillas chose the harmless and humorous tactic of pie-throwing because our goal was to take this perpetual charlatan off his new green pedestal," said Colonel Custard. "Friedman's support for coal and nuclear power is as misguided as his counsel on Iraq." This is the second time Friedman has been hit by a pie. In October 2002, he received a banana pie to his face while promoting his writings on free-market globalization in Boston." Now, that's a pretty awesome thing to appear in your mailbox by any standards. | ||
| iPhone Security Tip: Never Memorize Wireless Networks [securosis.com] Posted: 28 Apr 2008 03:50 PM CDT The other day I was wandering around San Francisco on a work trip, and I freaked out when I noticed the WiFi indicator on my iPhone was showing an active connection to some random network. I never have my phone set to connect to unknown networks, so I quickly jumped into the settings to see what the heck was going on. Turns out I was connected to “tsunami” which is a common default name on Cisco wireless gear. Like the Cisco gear in our community center, which just a week or so before I was playing with. And that got me thinking. Many of you probably connect to wireless networks with common names- like Linksys, 2WIRExx, tsunami, or whatever. In other words, either default networks, or names (like those used at conferences and airports) that are in common use or easy to find. But when you remember those on your iPhone (or computer for that sake), it only remembers the network ID (SSID), not that actual network! Your iPhone doesn’t know the difference between “tsunami” in your community center, “tsunami” in an office building, and “tsunami” running on some bad guy’s laptop to see what naive fools will connect to it. When you trust a network you’re just trusting a name anyone can use, not something really unique to that network. Your iPhone will then connect to any network using that name. Why is that bad? Go read this article I wrote at Dark Reading. An attacker can set up his or her laptop to broadcast that name, then perform a man in the middle attack to anyone who connects. They can sniff and modify any traffic going to your iPhone. Why is this more serious on an iPhone than your laptop? Because you walk around with your phone all the time, often checking things like email in the background. Another problem with the iPhone is that its VPN doesn’t automatically reconnect if the connection drops. Thus, even if you connect via a secure VPN, you might find your connection got dropped and your phone happily continues, sending all your traffic unencrypted. Here are my best practices for iPhone wireless security:
On my phone I only have it set to connect at home (a weird name), and I use AT&T EDGE when I’m out of my house. I have a VPN server set up at home for those rare occasions I connect from a conference network. The good news is that your iPhone doesn’t send out “probes” for known networks. This would be an easy way for a bad guy to know even those obscure SSIDs you use at home. Good move on Apple’s part- now I just want them to make the VPN connections persistent. | ||
| Plausibility checks [Robert Penz Blog] Posted: 28 Apr 2008 03:22 PM CDT Before I get to the actual topic of this post I want to write some sentences about users reactions to my last post. I was asked why I called the hacker a professional one, as that what he is doing is not complicated or cutting edge. That is true, but he makes a living with it and that defines professional for me in this case. So now to the plausibility checks I already talked about. Soon after I posted the link for the blog post to the hacker in the query I got an access to the page from the IP address 75.125.44.xxx, which I believe is the VPN gateway he talked about. This server seems to be a hacked dedicated at US ISP The Planet. This IP address accessed my blog the first time in the last weeks so thats a dead end. But I found something else, the browser agent variable “Mozilla/5.0 (Windows; U; Windows NT 5.1; nb-NO; rv:1.8.1.14) Gecko/20080404 Firefox/2.0.0.14″. OK thats the newest Firefox version but the other stuff doesn’t sound that common (e.g. the language). So I did a check in my logfiles and found following: Users with the same User agent did access following files at the provided times:
Both IP addresses did not access anything else in the last 2 weeks, thats really unusual. The first of the above addresses is an IP address from the Norwegian ISP Get AS. Hmm … could that be the real IP the hacker uses? The first access was before the DDOS and the second time it was under 30min after I talked with the hacker. Thats too much for coincidence. But lets take a look at the other IP address. The reverse lookup of that IP points to a mail server, which looks like a hacked server as the 75.125.44.xxx address did. So the second server with Norwegian browser installed even if it is not located in that country. So even more coincidences, specially as the access happened minutes before the DDOS attack started. But there is still more. This time the browser provided even attentional information. The reference entry: Now I can say it - I don’t believe him. He lied about no knowing my blog and as he accesses it minutes before the attack happened. I believe he attacked my blog! But why? only for posting the source of his maleware? PS: If you ask yourself why I didn’t post the full IP addresses. Thats because it is only a guess (a good one, but still a guess) and it could be someone indecent behind a given address. And even if it’s the hacker and he said the truce about his internet connection, that IP would lead only to a neighbor of himself. | ||
| XP SP3 Changelog [/dev/random] [Belgian Security Blognetwork] Posted: 28 Apr 2008 03:07 PM CDT
The 3rd service pack for Windows XP will be released soon. Here is a changelog. It seems that the pack is already available for download ( ~350MB). The new features regarding security are:
| ||
| Watching CNN can ruin your day! [StillSecure, After All These Years] Posted: 28 Apr 2008 12:45 PM CDT When I work from my home office I usually keep CNN on in the background to keep up on the world. However, I have to say that it is just too damn depressing. A sample of today's news:
Geez, what this country needs is a good fantasy for us to lose ourselves in. A new Star Wars or something to take our mind off of dealing with reality. It has got to get better, doesn't it? | ||
| iSkoot disclosure of Skype credentials resolved - new version by Wednesday [Voice of VOIPSA] Posted: 28 Apr 2008 12:07 PM CDT If you have been following this weekend’s discovery by Dameon Welch-Abernathy, a.k.a. PhoneBoy, of the iSkoot program disclosing Skype usernames and passwords (see also the chronology), you will know that the problem has been fixed and a formal statement from iSkoot would be forthcoming. That statement from iSkoot CEO Mark Jacobstein has now been issued on their blog. The key part related to the vulnerability is this: A recent build allowed a development/pre-production version of the Symbian client to be downloaded in place of our production version, which did indeed produce the issue Phoneboy reported. We have checked our other platforms (Blackberry, J2ME, Windows Mobile, etc.) and fortunately this issue impacted only Symbian devices. We've pulled the development/pre-production build and fixed the bug and will be doing a forced upgrade to every Symbian user no later than Wednesday (4/30). The folks at iSkoot are definitely to be applauded for their quick response. The incorrect build has been pulled from their site and, as stated, they intend to have a new version out no later than Wednesday. In the meantime, I would personally suggest that iSkoot users on Symbian devices simply stop running the application until the new build has been downloaded. Good outcome, all in all. Technorati Tags: | ||
| Risk Management and Car Talk [securosis.com] Posted: 28 Apr 2008 11:37 AM CDT I was driving around listening to Car Talk on NPR this weekend, and it was an incredibly insightful lesson on risk tolerance and risk perception. I tend to do a lot of errands over the weekend around that time, so I usually catch 20-40 minutes of it every week as I’m in and out of stores. Pretty much every week you’ll hear things like:
Gee, that sounds familiar. Or these calls:
Then there are these calls:
Think about all those cavities you could have avoided by going to the dentist on a regular basis, or that big air conditioning repair you could have skipped if you just performed the annual maintenance on time. Then stop complaining that your users “just don’t get it,” or stop whining about the business ignoring you. | ||
| What do you foresee as the next “great-awakening” for network security? [Andrew Hay] Posted: 28 Apr 2008 10:33 AM CDT
Please fill out the following survey (coordinated by Q1 Labs) to indicate what you think is next on the horizon - http://www.surveymonkey.com/s.aspx?sm=16FAHPNF3sHKXczECIGNaQ_3d_3d | ||
| The Tax Rebate for Big Oil Conspiracy :) [The Falcon's View] Posted: 28 Apr 2008 10:19 AM CDT | ||
| Interesting Bits - April 28th, 2008 [Infosec Ramblings] Posted: 28 Apr 2008 10:14 AM CDT I was away for a couple days, so the list today is a bit longer. Some good stuff though: Visit to the Workshop: A Do It Yourself Identity Management Solution (IdM) Web 2.0 and "Defense in Depth" Was the LendingTree Insider Data Breach Avoidable? Be careful with what you leave behind 5 Security Metrics That Matter Cloud Stacks: Please Mind The Gap Spear Phishing with Better Business Bureau complaints 12 Signs that Your Company is Already in the Cloud Dissecting the Automatic Patch-Based Exploit Generator 10 Myths About Life As An IT Security Professional Have a great day! Kevin  | ||
| Information security framework [Kees Leune] Posted: 28 Apr 2008 09:57 AM CDT A 0day with an automatic discovery and dissemination tool shouldn't be a surprise to anyone. The fact that it's hit hundreds of thousands of sites in less than a couple of weeks is slightly surprising, though it mainly means that the bad guys are moving fast. Is this just the next step in Internet security, where we have new 0day vulnerabilities sweeping through web servers on a regular basis?Observations like this once more seem to reconfirm that the bad guys are increasingly focusing on OSI layer 7 and above. While not to be ignored, simply putting up a firewall to keep unwanted traffic out, and an IDS to make sure the firewall is working well (or an IPS, if you prefer) is not sufficient. While hardening systems by applying patches (operating system, as well as all applications) and limiting servers to only provide services that are required remains critical to limit your technical exposure, malicious traffic traveling on legitimate channels remains effective. So what can be done? It is essential that deciding what is desired behavior when it comes to using information is done ahead of time. Users must be educate about proper use of information technology. Processes that use our information must be designed in a way that they reasonably prevent undesired use, and that they behave predictably when they fail. We must develop an enterprise architecture that supports our processes effectively and efficiently. We must put monitoring controls in place to detect when (not if!) our preventative controls fail. We must be prepared and know how to respond when those failures are detected. Bottom line? 1. Develop and maintain information security policy 2. Design and maintain business processes 3. Develop and maintain user awareness 4. Develop and maintain an enterprise architecture that is aligned with the business processes 5. Implement a technical infrastructure based on the enterprise architecture 6. Monitor processes and infrastructure for signs of failure 7. Respond to incidents 8. Go to 1. | ||
| The Daily Incite - April 28, 2008 [Security Incite Rants] Posted: 28 Apr 2008 09:56 AM CDT  April 28, 2008 - Volume 3, #41 Good Morning: The G-men had a pretty good draft and being a Falcons season ticket holder, I'm hoping Matt Ryan lives up to the hype. The few days after the draft are always about what could be. Living in the future is OK, but sooner or later you need to get on the field and play. When does training camp start again?
Top Security News Great, 2.7 million people that have no idea what's going on
Top Blog Postings Maybe a grapefruit will work better? | ||
| Names Can Be Deceiving [The Falcon's View] Posted: 28 Apr 2008 08:55 AM CDT One brief observation based on watching the John Adams miniseries... our modern day Republicans should probably be called Federalists (the party of Adams, not Jefferson), whereas the Democrats are descended from Jefferson's original Democratic-Republican Party. However, neither party really seems... | ||
| Posted: 28 Apr 2008 08:50 AM CDT Given commentary now appearing in the blogosphere around the speed of the response this weekend by both various blogs and also the folks at iSkoot responding to the security issue tracked on this blog, I thought I would take a moment and just capture the chronology of what did occur. (Partly to emphasize what Andy points out in his post today - that the blogosphere can help companies that join in the conversation.) Here’s what I saw - all times converted to Eastern US:
iSkoot CEO Mark Jacobstein also indicated that a public statement will come from them at some point as well (but is not yet visible on their site or blog). If there were other posts during this timeframe from other bloggers that I missed in there, my apologies… I’m just reporting what I personally saw. (And feel free to send me a link to add.) What’s interesting to note from this timeline is that it was about 36 hours - on a weekend - from the time of the initial published report by Dameon to the first published report by Jim that the issue had been resolved. Mark Jacobstein and his team at iSkoot certainly deserve kudos for the speed of their response but its also important to note that part of this came about because iSkoot had previously engaged with the blogosphere. They had worked with Jim Courtney at Skype Journal as well as Andy Abramson at VoIP Watch. Because of those relationships - as well as the communication within the circle of us who write about VoIP online - iSkoot was able to quickly be brought into the issue and get engaged with confirming the problem and working on a resolution. Note, too, that this previous engagement obviously left a positive view because the focus was on trying to confirm the issue and resolve it. There was no animosity or malicious publication, i.e. you could see with a company that people hate where someone could really spin this negatively. There are some other lessons out of all of this, some related to this blog, that I will write about separately. Meanwhile, I just thought capturing this would provide a view into how the blogosphere can respond to an issue in a way that helps a company. I’m just glad to know that the issue was not across all their products and is on the way to being fixed. Technorati Tags: |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |










 I guess I forgot to post this earlier but on Saturday, May 10th I’ll be presenting the keynote at
I guess I forgot to post this earlier but on Saturday, May 10th I’ll be presenting the keynote at  The format is the same as a credit card and a contains all your personal information and your digital certificate (which allow you to digitally sign official documents). To use the card, you need a PIN code. The eID is supported by TrustBearer and my laptop (Dell) has a builtin smart-card reader. Let’s go for a test!
The format is the same as a credit card and a contains all your personal information and your digital certificate (which allow you to digitally sign official documents). To use the card, you need a PIN code. The eID is supported by TrustBearer and my laptop (Dell) has a builtin smart-card reader. Let’s go for a test!

 What do you foresee as the next "great-awakening" for network security? Will it be a breach of the national power grid? Perhaps a horrible botnet, worm, or virus infestation/outbreak? What about a surge in browser threats for desktops or mobile phones? Maybe even a disclosed national security breach by a foreign power?
What do you foresee as the next "great-awakening" for network security? Will it be a breach of the national power grid? Perhaps a horrible botnet, worm, or virus infestation/outbreak? What about a surge in browser threats for desktops or mobile phones? Maybe even a disclosed national security breach by a foreign power? But that's the recorded music. If Springsteen comes to your town, you go. Those folks put on a great show. They played for about 2:45 and took like no breaks. The band was tight, really tight. You can check out the
But that's the recorded music. If Springsteen comes to your town, you go. Those folks put on a great show. They played for about 2:45 and took like no breaks. The band was tight, really tight. You can check out the 

No comments:
Post a Comment