Spliced feed for Security Bloggers Network |
| Chinese advance-fee scam via Skype [The Dark Visitor] Posted: 01 Nov 2008 07:36 AM CDT Thanks to Websense Security Labs for informing us about a new advance-fee scam targeting Chinese Skype users. Apparently, Chinese users get a message indicating that they have won a significant sum of money and prizes. They are directed to a phishing website where they fill out contact information for the prizes but nothing too suspicious. Finally, they are redirected to a bank transfer page where they will have to send in a fee of several hundred RMB to collect the prize. I wonder if the officials reading Tom Skype users’ messages are falling for this too. |
| Win a free full conference pass to CSI [StillSecure, After All These Years] Posted: 01 Nov 2008 06:56 AM CDT
So leave your comment and may be the best person win! |
| Links for 2008-10-31 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 01 Nov 2008 12:00 AM CDT |
| The Geek 100 Pt. 5: Science and Electronics [HiR Information Report] Posted: 01 Nov 2008 12:00 AM CDT See the whole series: The Geek 100 This is a list of 100 basic things and skills every geek should have. I've broken this series up into five parts. Let's face it: a list of 100 things would be tedious to wade through. Over the rest of the week, look for twenty more skills to show up daily. The skills assume you have done it in the past and can remember how to do it right now (or, like a good Geek, you've jotted it down in one of your notebooks). Having it in your personal notebook is okay. Scrambling to the Internet means you don't have the skill... yet. Science. Every geek should be able to:
Electronics. Every geek should be able to:
See the whole series: The Geek 100 |
| Links for 2008-10-31 [del.icio.us] [HiR Information Report] Posted: 01 Nov 2008 12:00 AM CDT
|
| Posted: 31 Oct 2008 11:28 PM CDT |
| Skimming not a violation of PCI DSS [PCI Blog - Compliance Demystified] Posted: 31 Oct 2008 10:42 PM CDT It is important to remember that credit card skimming is an entirely different type of fraud than what the PCI DSS is meant to protect against. Remember that the PCI program has several sub-sections: PCI DSS, PCI PED, and PCI PA-DSS. Each of these are meant to address a different piece of the pie. The PCI DSS is meant to protect against the electronic and paper theft of credit card data within an organization. This applies to the 12 ‘digital dozen’ requirements and sub-requirements. It is not meant to protect against credit card skimming, which is a problem I don’t know anyone can solve. (Though the implementation of Chip-PIN plus iCVV may reduce this in the future.) In fact, skimming, cloning, and other credit card fraud is something that’s rather difficult to curtail. But there is a difference between what PCI DSS is meant to protect and skimming fraud. You see, skimming requires a physical presence. If you are skimming the magnetic stripe or the RFID component, the attacker needs to be there physically. This reduces the risk because (1) the attacker exposes themselves to greater risk of capture, and (2) these types of schemes do not scale well. In I can hack into a computer network (i.e. retailer, restaurant, university) and copy credit card data it does not require a physical presence and I can copy as much data as exists. If the computer system or point of sale (POS) machine contains a million credit card numbers then viola! In order to capture that same level of data from individuals via skimming would take a considerably longer period of time. The goal is always to focus on risk reduction because risk may well never reach zero (or will simply be cost prohibitive.) By properly applying the PCI controls for data security, PIN pad security, and application security you can help reduce your risk of financial loss. |
| Oh noes! They be stealin' our garage doors! (Misc) [HiR Information Report] Posted: 31 Oct 2008 08:11 PM CDT 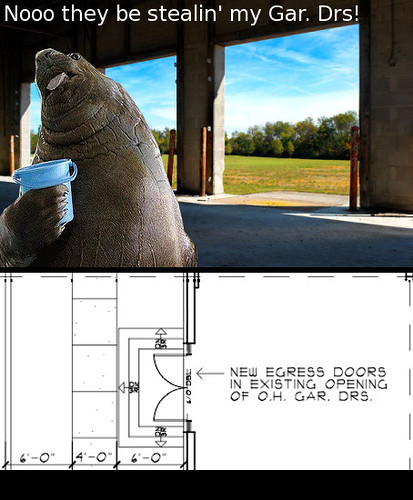 A few things: A few things:First, Cowtown Computer Congress finally got blueprints of the building our hacker space will be located in. That's good news. The bad news? The awesome garage door we thought we'd have might be on the chopping block according to the blueprint -- as shown below the lolrus (which is actually a huge seal since it doesn't have tusks) Not cool. We're gonna try to have them leave the garage door. Also, CCCKC will be thowing a "build it for them to throw it" party on Nov. 22, a few days before the Plaza Lighting Ceremony. This event for CCCKC members will get a bunch of geeks together to build LED Throwies. The plan is to use the throwies for the fund-raiser on the 26th. What better time of year to lob magnetized LEDs at things than the official kick-off of Kansas City's Holiday Season? Become a member of CCCKC, come out and help us build some throwies, and then kick it with all of us at the next fund raiser. Last but not least, I posted a fun project over at i-Hacked today. Not many people knew that my RJ45 cuff links at DefCon were actually functional ethernet loopback testers. I walk you through the steps to build your own ethernet loopback tester that you can keep on your keychain or use as cuff links (if you make two). Photos below:     |
| Security, Drinking Straws, Cavities and Wrinkles... [Rational Survivability] Posted: 31 Oct 2008 07:33 PM CDT
Recently, a friend passed along a tip from a dermatologist: Stop sipping through straws. The doctor said it was the number one cause of wrinkles. Even more recently, at lunch one day my aunt relayed some info from her husband, an orthodontist. He said that drinking through a straw prevents cavities and tooth decay, since straws allow sugary beverages to bypass your teeth. When my aunt said this, everybody around the table (six women) stuck straws in their drinks. But when I countered with the skincare side of the question, my aunt was the first to pluck her straw right back out again. Brings new meaning to "security sucks." What's your favorite "security straw" analogy? /Hoff |
| Posted: 31 Oct 2008 06:33 PM CDT Back in July, I blogged that I had passed my CISM exam. Today I was pleasantly surprised that all the paperwork had cleared and that I am now officially certified.
What's next? We'll see. It's probably time for something more technical. Maybe a SANS class, or maybe something more off-beat, such as the training programs offered by Offensive Security. For the time being, I think I'll just ride the flow a bit and see what comes my way. |
| OpenBSD 4.4 is hitting the mirrors now! [HiR Information Report] Posted: 31 Oct 2008 05:43 PM CDT  OpenBSD 4.4 is scheduled to be officially released November 1, 2008 (that would be tomorrow as of writing). It's already on some of the FTP mirror sites, though. OpenBSD 4.4 is scheduled to be officially released November 1, 2008 (that would be tomorrow as of writing). It's already on some of the FTP mirror sites, though. I am installing this TONIGHT. I may try Ubuntu Intrepid Ibex that was released this week as well, but I'm really more excited about OpenBSD. I'm a little bit of a fanboy, if you can't tell. |
| Heroes: Neil Alden Armstrong [Infosecurity.US] Posted: 31 Oct 2008 03:39 PM CDT |
| Friday Summary: Happy Halloween! [securosis.com] Posted: 31 Oct 2008 02:28 PM CDT Man, I love Halloween; it is the ultimate hacker holiday. When else do we have an excuse to build home animatronics, scare the pants off people, and pretend to be someone else (outside of a penetration test)? Last year I built something I called “The Hanging Man” using a microcontroller, some windshield wiper motors, wireless sensors, my (basic) home automation system, and streaming audio. When trick or treaters walked up to the house it would trigger a sensor, black out the front of the house, spotlight a hooded pirate hanging from a gallows, push out some audio of a screaming guy, drop him 15 feet so he was right over the visitors, and then slowly hoist him back up for the next group. Webcasts, Podcasts, and Conferences:
Favorite Securosis Posts:
Favorite Outside Posts:
Top News:
Blog Comment of the Week: See you all in 2 weeks… |
| Fun Reading on Security AND Compliance – 9 [Anton Chuvakin Blog - "Security Warrior"] Posted: 31 Oct 2008 02:05 PM CDT Instead of my usual "blogging frenzy" machine gun blast of short posts, I will just combine them into my new blog series "Fun Reading on Security." Here is an issue #9, dated October 30th, 2008. BTW, I am renaming it into "Fun Reading on Security AND Compliance"
Enjoy! |
| State Department Data Theft [securosis.com] Posted: 31 Oct 2008 01:15 PM CDT This story has it all … theft of State Department data, forged credit cards, multi-government branch conspiracy, and murdered suspects. Sounds like an afternoon soap opera more than a Stolen Passport Data story from the Washington Post:
The passport applicant database, given the type, quality and quantity of data contained therein, is like winning the identity theft lottery. The State Department has some ’splainin to do! -Adrian |
| VMWare Security Advisory: Updated ESX Internal Packages [Infosecurity.US] Posted: 31 Oct 2008 11:34 AM CDT |
| Genius: Richard Feynman, Ph.D. [Infosecurity.US] Posted: 31 Oct 2008 11:27 AM CDT |
| ICANN: EstDomains Termination Stayed [Infosecurity.US] Posted: 31 Oct 2008 10:08 AM CDT |
| Shimel: Security Bloggers Network Designated Press Bloggers At CSI Conference [Infosecurity.US] Posted: 31 Oct 2008 10:00 AM CDT |
| Microsoft Security Advisory: Cumulative Update - ActiveX Kill Bits [Infosecurity.US] Posted: 31 Oct 2008 08:58 AM CDT |
| The Geek 100 Pt. 4: Development and Cryptography [HiR Information Report] Posted: 31 Oct 2008 06:00 AM CDT See the whole series: The Geek 100 This is a list of 100 basic things and skills every geek should have. I've broken this series up into five parts. Let's face it: a list of 100 things would be tedious to wade through. Over the rest of the week, look for twenty more skills to show up daily. The skills assume you have done it in the past and can remember how to do it right now (or, like a good Geek, you've jotted it down in one of your notebooks). Having it in your personal notebook is okay. Scrambling to the Internet means you don't have the skill... yet. Props to my friend Joshua Kriegshauser for help with the Software Development skills. I'm not a coder. He's the Technical Director of the EverQuest II team at SCEA. That makes him more than qualified to help me out here. Software Development. Every geek should be able to:
Cryptography. Every geek should be able to:
See the whole series: The Geek 100 |
| Google Hacking and the Dangers of Search Engines [ImperViews] Posted: 31 Oct 2008 03:02 AM CDT My main concerns with respect to these threats are: -Lack of awareness (and hence the lack of proper mitigation tools). -Search engine operators, while trying to mitigate some of the issues, do not distinguish between application owners and potential attackers. For example, there is a limit to the search rate based on source IP address. While true attackers are hardly affected by this, site owners are denied the possibility of automated, proactive mitigation. Together with SQL Injection rennaisance, I think that search engine related threads are a growing trend in web application threats. - Amichai |
| Links for 2008-10-30 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 31 Oct 2008 12:00 AM CDT
|
| Links for 2008-10-30 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 31 Oct 2008 12:00 AM CDT
|
| Virtualization? Give me a better OS instead! [Security Balance] Posted: 30 Oct 2008 11:18 PM CDT Do we really need to go that deep into virtualization? I may sound dumb to try to reason against something that everybody is embracing, but that’s usually what I like to do about hypes OK, you’ll probably throw a lot of advantages of virtualization on me. And I agree that most of them are true. I was reading that some companies are being able to increase their hardware processors utilization from 10 to 60% through virtualization. There is also all that high availability stuff from VMotion and other new products that are being released everyday. OK, but… Let’s go back some years and see how we end up where we are. Imagine that you had to put two new applications in production, A and B. To ensure proper segragation you decide to put both applications on their own servers, X and Y. Of course, are they are both critical apps, you also build servers Z and V for high availability purposes. In a few months, people start to complain the servers utilization is too low. They are consuming too much power, rack space, blah blah blah. Ok, then someone gets a nice rabbit from a hat called virtualization. Wow! Now you transform the hardware X and Y into VM servers (or whatever you wanna call it), build separate VMs for A and B and as you VM product has a nice feature of dynamically moving images from a box to another, you don’t need Z and V anymore. Wow! You’ve just saved 50% of servers related cost! OK, could probably be worried about putting those application in the same “real” box. After all, you decided before that they should be running on different servers, and here they are on the same box! But you look into the problem and notice: - One virtual server cannot interact with the other - Problems caused by application A still can’t cause problems on application B server - A security breach on virtual server A will not affect virtual server B Ok, everything is still good and you go to bed happy with the new solution. No, people are greedy! Seriously, now that we have all those servers on the same box, why can’t we have a little more control over their access to resources available? Like, if one server is not using all memory allocated to it, why can’t the other one use that when it needs? Same for processing power, storage? But in order to do that the Hypervisor would need a better view into what is happening into those black boxes…why not make them aware of the VM environment? Build APIs that allow communication between the guest OSes and the hypervisor? Nice! Now things are starting to get really advanced! But where is that segregation that was mentioned before? Won’t all this interaction between the HV and the guest OSes reduce the isolation? Of course it will! Some attacks from guest OSes to the HV or to other guest OSes are now possible. Anyway, it’s the price for better management and better resource utilization. Isn’t it? Yes, it is. We already knew it! Isn’t it the price to put two application on the same REAL box? Let’s see. We want hardware resources to be shared by the applications and something controlling it. One application shouldn’t be affected by the other or access non-authorized resources. And we want high availability too. Well, please tell me if I’m wrong, but for me these things are just the requirements of a good Operating System with cluster capabilities! Virtualization guys usually refer to mainframes as a virtualization success case. They are right about it. But on mainframes LPARs (their name for VMs) are usually used to isolate completely different environments, like development and production. It is very common to find several applications running on the same LPAR, being segregated only by the OS and Security Manager (that can be seen as part of the OS). Usually, LPARs are used because organizations can’t afford different hardware for things like, testing, certification and development, whilst on the “new virtualization” world VMs are used to optimize resource utilization. As far as I remember from my Operating System course classes from university, that was the Operating System role. Are we creating this beast because we couldn’t produce a Operating System that does its job? |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |

No comments:
Post a Comment