Spliced feed for Security Bloggers Network |
| Commtouch Honored with Deloitte Technology Fast 50 [mxlab - all about anti virus and anti spam] Posted: 07 Nov 2008 07:46 AM CST Commtouch, one of our technology partners, has been honored with the Deloitte Technology Fast 50. Read the full article.  |
| WPA2 is not next on the chopping block [Errata Security] Posted: 07 Nov 2008 01:34 AM CST Researchers have announced they can crack WPA in 12-minutes. Some people wonder if WPA2 will soon be next. It won't be. WPA was always known to be a weak hack, WPA2 has always been known to be secure. The reason for the compromise was that that hardware didn't support the AES encryption in WPA2, so a weaker crypto was needed to fix the obvious flaws with WEP without requiring a hardware upgrade. The original WEP was based upon the RC4 encryption algorithm. RC4 is a fine algorithm, it's still used today for SSL today. However, it's a "stream cipher" that needs a unique key per stream. That's why it works for SSL and not WiFi: SSL is one long stream whereas WiFi is a bunch of individual packets. RC4 cannot be used for encrypting packets, just streams. RC4 was baked into the WiFi chips. The correct fix for the WEP-crack problem was to replace RC4 with a "block cipher", namely AES. However, you couldn't get rid of all the hardware in the field. Therefore, an interim solution that still used RC4 was created. The fix was to include a sequence number in each packet, and mix the sequence number with the WEP key to create a unique per-packet key. This was called "TKIP". Both solutions were standardized at the same time. The WPA certification required TKIP, but made AES optional. The WPA2 certification required AES. We use these terms WPA-RC4-TKIP interchangeably and WPA2-AES-CCMP interchangeably, but technically they refer to different things (the standard, the encryption, and the keying method respectively). Even as the compromised was reached, everyone knew WPA-TKIP was going to be hacked eventually. Cryptographers have a good nose for such things, and even while they couldn't immediately figure out a way to crack this, they knew it would probably be hacked in time. However, everyone had full confidence in AES. There are no weakness in AES or the WPA2 standard based upon it. It's going to last for the next 20 years. It's security we can rely upon (at least, as far as encryption goes - there are still issues with authentication). As a side note, the author of this new attack is Erik Tews. He is the 'T' in the "PTW", the latest and greatest attack on WEP. The original WEP crack required millions of packets and a lot of CPU time to crack. However, this evolved quickly with better and better methods. PTW is the latest and best method so far. It requires only 40k packets and a few seconds of CPU time. Therefore, we can trust this method will probably work, although there might be caveats (such as man-in-the-middle attacks on TKIP packets). The moral of the story is that you should always have been planning WPA2-AES-CCMP eventually, and been planning to rely upon that for many years. If you planned to only do WPA-RC4-TKIP, then you were wrong. |
| Links for 2008-11-06 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 07 Nov 2008 12:00 AM CST |
| Open Call for Novafocus Submissions [NovaInfosecPortal.com] Posted: 06 Nov 2008 11:26 PM CST We are looking for NoVA professionals who would be interested in doing periodic blog postings related to infosec in our area. This isn’t intended for those that already have blogs (however if you have a blog and want to repost, we have no problems with that); instead it is for those that would like to post some more in-depth content/analysis once in a while but don’t have time to maintain a full time blog. So if you would periodically like to put out an article, a paper/presentation requiring feedback, a summary of a local infosec event, or something you would like to complain about, let us know via the Contact Us page. I can’t offer much here but fame and fortune (ahhh, well maybe just fame and recognition as an expert in our field). I see it as sort of like what SecurityFocus does with their Infocus series but covering a wider range of topics yet narrowed down to a geographic area. We’ll call ours Novafocus. |
| 2600 Group - Baltimore Infosec Meetup Event - Friday, 11-07: Normal Meeting [NovaInfosecPortal.com] Posted: 06 Nov 2008 11:06 PM CST Here is some information regarding this week’s Friday 2600 Group - Baltimore infosec meetup event.
For more information on the 2600 Group - Baltimore, see its description in our NoVA Meetups section. View our Calendar for a complete list of infosec events in and around the NoVA area. |
| 2600 Group - Arlington Infosec Meetup Event - Friday, 11-07: Normal Meeting [NovaInfosecPortal.com] Posted: 06 Nov 2008 11:02 PM CST Here is some information regarding this week’s Friday 2600 Group - Arlington infosec meetup event.
For more information on the 2600 Group - Arlington, see its description in our NoVA Meetups section. View our Calendar for a complete list of infosec events in and around the NoVA area. |
| Microsoft Issues Security Report for Jan-Jun 2008 [Sunnet Beskerming Security Advisories] Posted: 06 Nov 2008 10:43 PM CST Microsoft's Malware Protection Centre has released Volume 5 of their Security Intelligence Report (SIR), covering January to June 2008. While it may not have the independence of reporting from OWASP, ISC, US-CERT, or a number of other bodies, coming from the largest operating system and software vendor it is a very interesting point of view on the state of computer security, as observed by Microsoft. While the report doesn't cover threats and malware targeting non-Windows operating systems, it provides a very detailed look at the ecosystem of malware and threats that infects Microsoft systems across the globe, including detailed breakdown of per-country infection rates and types. This per-country reporting throws up some interesting statistics about the prevalence of different malware types in different countries. For countries like Brazil and South Korea, the relative distribution of malware types speaks volumes about how these countries have seen their local IT infrastructure and composition evolve. Some of the positive highlights from the report are the improvement (decrease) in the number of vulnerabilities reported, while at the same time seeing an increase in the overall number of serious vulnerabilities being reported. Perhaps Volume 6 of the report will show some different results, with October's large number of security patches, Kaminsky's DNS flaw, the unreleased TCP/IP vulnerability, and the Critical out of cycle patch for the RPC Service potentially skewing the next set of results. One statistic to keep an eye on in future reports is the relative global distribution and percentage of systems requiring cleaning every time the Microsoft security tools are run. As identified in Volume 5, there appears to be a clustering of systems requiring disinfection following tool use in countries that are otherwise considered to be "developing". Given the borderless nature of the Internet, it suggests alternative infection mechanisms for systems in those countries (such as sneakernet). It is also an interesting observation that countries traditionally seen as copyright infringement hotspots are not reporting as such a high risk as others. Perhaps systems using infringing copies of Microsoft software in those countries have been configured not to report back to Microsoft or just aren't running Microsoft's security tools in the first place. Given the depth of excellent data provided in the SIR, it is important to at least be aware of a possible self-selection bias in the reporting of problems detected and removed. It appears that most of the raw data used to compile the report came from Microsoft security tools that had been installed and operated on end user systems, as well as from selected online service providers. This means that systems and sites that use alternate security suites that detected and removed problems before the Microsoft tools will not have their data appearing in the report. Likewise, systems where the "Call Home" feature is disabled or blocked will not see their results appear, either. It does look like Microsoft made an attempt to source data from outside of their own networks and tools, using the datalossdb.org (and attrition.org) site to build statistics about the relative percentages of security breach incidents - data that Microsoft's own tools would not have been able to gather. It should be cautioned that, although it is probably the best online archive of data loss incidents, the information presented through datalossdb.org / attrition.org only identifies openly reported data loss cases. It isn't able to capture incidents that don't receive media coverage, or which aren't reported directly to the site. Despite lacking information on non-Microsoft operating systems and the Internet as a whole, the SIR justifiably takes its place alongside those from OWASP and ISC as being one of the key security reports that should be read and appreciated by the modern Information Security employee. |
| Microsoft's November Patch Release Advance Notice [Sunnet Beskerming Security Advisories] Posted: 06 Nov 2008 09:19 PM CST Last month Microsoft issued 11 patches with their monthly update as well as a Critical out of cycle Update for the RPC Service. Given the ease by which the RPC vulnerability could be targeted on many systems, it led many to fear that another Blaster or Sasser was on its way. Despite the availability of malware prior to the release of MS08-067, and a steadily increasing number of new worms targeting the vulnerability, there have yet to be any significant attacks against Windows systems using this particular vector (though that may still happen). With the second Tuesday of November being next week, Microsoft have issued advance notification of the patches they expect to release with this month's updates. Only two patches are expected this month, one Critical and one Important. Both patches are for as yet unidentified remote code execution vulnerabilities; with the Critical update for Windows and Office - specifically XML Core Services, and the Important update being for Windows. Microsoft's Malicious Software Removal Tool will also be updated, along with the availability of high-priority non-security updates through WSUS and Windows Update. |
| Old Malware Tricks Still Work [Sunnet Beskerming Security Advisories] Posted: 06 Nov 2008 08:43 PM CST When Didier Stevens stumbled across a zero-byte padded piece of malware a year ago he was somewhat surprised to see that many antivirus systems tested against it failed to identify the underlying malware despite the targeted application (Internet Explorer) being quite happy to strip the 0x00 content and run the malware. Didier has revisited his earlier work and happily found that successful detection for the original malware samples has increased markedly in the past twelve months (29/36 for unobfuscated samples). When he lengthened the 0x00 padding within the malware samples, however, the detection rates dropped off significantly. By only doubling the length of padding, the rate of detection dropped from 6 to 3 out of 36 command line scanners. It is still disturbing that by adding 255 bytes worth of 0x00 is enough to see the detection rate drop from 29 to 6 scanners, especially given that the obfuscation technique has been well known for a number of years. Even more interesting is the change in detection when the 0x00 bytes are added to the malware sample. For the engines that do detect the modified file, there is often a change in description of the malware between the unobfuscated sample and the obscured one. In almost all cases it is a move to a generic descriptor (0x00 padded) from a specific definition (original sample), so it doesn't appear that scanning engine developers are claiming a new and unique variant for each 0x00 padded file (which is a good thing). While the generic detection of the modified files points to at least partially-functioning heuristics in some engines, the lack of detection from the clear majority of command line scanners being used at VirusTotal shows that there is still some way to go for antimalware companies as they drag their products away from purely signature-based detection to a more flexible model. As Didier points out in his post, it could be that the command line versions of the scanning engines are lacking in some of the features that the GUI versions will have that could detect his malware samples. It would be better if those features were actually in the command line versions as it would provide a greater level of protection in a managed network environment, where it is more likely that network level scanning is being managed by a command line tool. |
| Interesting Information Security Bits for 11/06/2008 [Infosec Ramblings] Posted: 06 Nov 2008 05:45 PM CST Good afternoon everybody! I hope your day is going well. Here are today’s Interesting Information Security Bits from around the web.
That’s it for today. Have fun! Subscribe to my RSS Feed if you enjoy these daily Interesting Bits posts. Kevin Posted in Interesting Bits |
| New Audio Podcast on my Trip to Madrid [Got the NAC] Posted: 06 Nov 2008 05:31 PM CST I recently returned from ISSE 2008 in Madrid, Spain. The conference highlighted some key differences between U.S. and European information security. Tune into this podcast and you’ll get some food for thought: lessons that you may be able to apply in your own work. Tags: General, ISSE, madrid, spain This posting includes an audio/video/photo media file: Download Now |
| 'Obama Trojan' Highlights The Problem of Compromized Web Servers [ImperViews] Posted: 06 Nov 2008 04:51 PM CST Congratulations to the elected president. I was watching his speech on Tuesday and thought that it was important enough that I allowed my nine-year old son to stay up past his bed time to watch the entire event. Apparently millions of people all over the world couldn't stay up that late, but still wanted to watch (or re-watch) a video recording the next day. As a result, many individuals have now been mis-led by a Trojan. Hundreds of thousands of users whose computers are being infected by malware that bears Obama's name will hopefully remember not to open suspicious emails. Websesnse, as well as several other security vendors, issued warnings about this Trojan. The malware is distributed via compromised sites. According to Websense, "Some of the email attacks contain links to a file called 'BarackObama.exe' which is hosted on a compromised travel site." |
| Chinese hackers cyberattack on Obama and McCain’s websites? [The Dark Visitor] Posted: 06 Nov 2008 04:44 PM CST This comes from Newsweek via Wired that both presidential candidates websites were attacked. There is a lot of speculation in the original Newsweek article which Wired duly notes:
|
| CPISM and CPISA certified individuals [PCI Blog - Compliance Demystified] Posted: 06 Nov 2008 02:33 PM CST
There are over a hundred people already CPISM certified (and one special individual), but tomorrow is the first public offering of the CPISA exam meaning they will be some of the first individuals certified under the CPISA. Good luck to all those who take the exam tomorrow. For more information on these certifications check out the SPSP website. |
| Discovering Rogue Access Points With Nmap [PaulDotCom] Posted: 06 Nov 2008 02:30 PM CST By Paul Asadoorian There are lots of ways to skin this cat. This came up and piqued my interest because I was looking at the Nessus plugin to do this. This is a neat concept, but relies on some really old information from Nmap 3.50 OS fingerprints. I decided that using Nmap directly is probably best to perform this task. Luckily, my handy Nmap Book has a section devoted to this called "8.8 SOLUTION: Detect nmap -PN -n -pT:80,443,23,21,22,U:161,1900,5353 -sU -sV -sS -oA osfinger -O -T4 192.168.69.0/24 The above Nmap command scans the network with no ping options set (-PN), and no name resolution (-n). It only scans selected TCP and UDP ports, which I find is a really neat feature to be able to specify independent lists of UDP and TCP ports using the syntax above. I chose the ports listed because they are most frequently found listening on embedded devices. I want to know if those ports are open (-sU and -sS), and I want to fingerprint them if they are open (-sV). I also want all of the result types (nmap, grepable, and xml) so I can work with the results on XML and if a scan dies, resume with the csv file. I also want an OS fingerprint and use aggressive timing. This is great, but for use in an enterprise I want to run this on a cron job and have it email me the results every day. So I extended using Nmap Parser (a perl library for accessing Nmap results and running Nmap scans) and came up with: RogueAPDetect, written in perl.
I installed the latest version of Nmap Parser, version 1.13. [Editors Note: Nmap Parser 1.18 is now available, but the compatibility with Nmap version 4.76.] I had to change the object names to be compatible with the new version, but it works like a champ. Example results look like this: rogueapdetect.pl v0.001 - ( paul@pauldotcom.com ) -------------------------------------------------- |
| PaulDotCom Security Weekly - Episode 128 Part II - October 31, 2008 [PaulDotCom] Posted: 06 Nov 2008 01:47 PM CST We are still working on the sound quality problems and have yet even more equipment to replace, so next episode we should have it all worked out (I hope).
 Hosts: Larry "HaxorTheMatrix" Pesce, Paul "PaulDotCom" Asadoorian Email: psw@pauldotcom.com |
| Credit Card Security at Point of Sale [The IT Security Guy] Posted: 06 Nov 2008 01:44 PM CST This is an interesting article in CSO about Point of Sale (POS) security for credit cards. Credit card security is regulated by the well-known industry standard, PCI. But PCI covers retailers, merchants, banks and others who either issue or use credit cards in their business. Partly due to tightening of security from PCI, hackers are aiming their sites at payment application systems, like those where people swipe their cards when making purchases. Often the security of these applications, which sit on POS systems, themselves striped down mini-computers, aren't as tenderly secured as full-blown systems and their applications. As a result, the PCI council has another standard for these applications, the Payment Application Data Security Standard (PA-DSS). This article also mentions a type of insider attack, called "under-ringing," where store clerks collude with card thieves. This type of human attack isn't cover by PA-DSS, but the article still makes for good security reading. |
| Has WPA Finally Been Cracked? [The IT Security Guy] Posted: 06 Nov 2008 12:52 PM CST Two security researchers working together have partially cracked Wi-Fi Protected Access (WPA), a wireless encryption technology that had been considered secure. Details are to be unveiled at the PacSec conference in Tokyo next week. The breach is significant, since WPA has been touted as a secure replacement for WEP, which itself had been breached by German researchers back in April 2007. The researchers, Erik Tews and Martin Beck, were able to break the Temporal Key Integrity Protocol (TKIP) in less than 15 minutes by fooling a WPA router into sending them enough packets to crack the encryption key. TKIP is used by WPA for part of the encryption process. They didn't use a dictionary attack, where heavy computing power is used to guess at keys, a type of attack of which TKIP is susceptible. The researchers still haven't been able to decrypt data that goes from the PC to the router, so they haven't completely broken in the castle yet. Wireless users could upgrade their access points and routers to WPA2, the next generation of WPA, which can't be hacked yet by the TKIP compromise. But that may not be easy for the many enterprises who have adopted WPA to replace leaky WEP encryption. |
| Expanding the reach [ImperViews] Posted: 06 Nov 2008 10:19 AM CST I was reminded by my fellow bloggers that I have been remiss on my blogging responsibilities and have not written about our recent announcements of a new mid-market edition WAF and PartnerSphere program. We started our partner program, OpenSphere, a few years ago and have been fortunate to attract a good number of partners; in fact, many are currently adding considerable value to our customer base. Our partner program is divided into two components: 1. technology partners (under the OpenSphere umbrella) and 2. our channel partners, which we are calling our PartnerSphere. Yes, there is a pattern here... What is the goal of this new push? Simple: to expand the overall reach of our solutions to segments of the market that are looking to solve security and compliance problems, but have previously been out of reach of our direct sales force or do not require extremely high-performance solutions. Yes, there is another world out there... |
| SC World Congress - New York City [Matt Flynn's Identity Management Blog] Posted: 06 Nov 2008 09:18 AM CST Want to get the latest info on Information Security, Compliance/Audit, Risk Management and Policy? The SC World Congress will happen Dec. 9-10 at the Jacob Javits Center in NYC. New York is a great place to visit in December - let me know if you plan to be there. Maybe we can meet for a drink. Also, NetVision will be there as a sponsor. Stop at the booth - we'd love to talk to you about our latest accomplishments. I'll also be blogging about the event as part of the Security Bloggers Network. The SBN is pleased to offer our readers a 35% discount on conference rates. It could be just what you need to get approval to attend the event. To take advantage of the discount, just use the promotional code BLOG1 (for one day pass) or BLOG2 (for two day pass). For more info, go to the SC World Congress site. |
| Recording & Stream Notice - Episode 129 [PaulDotCom] Posted: 06 Nov 2008 08:09 AM CST The live stream should be active about 6:30 EDT, Thursday, October 30th. We should begin recording the live show at about 7:00 EDT. Please keep in mind that these times are all estimates, but we will try to do the best that we can. This week our featured guest is Bill Brenner from CSO Magazine to talk to us about selling penetration tests and security to upper management.
When active, the live stream(s) can be found at: Ustream: http://ustream.tv/channel/pauldotcom-security-weekly Icecast: http://radio.oshean.org:8000 Please join us, and thanks for listening! - Larry & Paul  |
| "Unix Terrorist" in trouble over TJX ? [extern blog SensePost;] Posted: 06 Nov 2008 04:32 AM CST Anyone who was around for Defcon-10 will have an opinion on the infamous Gobbles-Silvio-UnixTerrorist talk in which mail spools where published and everyone was slammed [1] According to mumble on the Interwebs (and a comment from RiskyBusiness) it appears as if the Stephen Watt who allegedly "modified and provided a "sniffer" program used by the conspirators to monitor and capture the data crossing corporate computer networks" == Unix Terrorist.. It's not clear the extent of Watts involvment with the breakin, but it does send a cold shiver down the spine of anyone who puts out tools / software.. /mh [1.] for me it just hurt seeing Silvio trying to make a real point while UT was trying to make a few jokes.. |
| Interesting Information Security Bits for 11/05/2008 [Infosec Ramblings] Posted: 05 Nov 2008 03:30 PM CST Good afternoon everybody! I hope your day is going well. Here are today’s Interesting Information Security Bits from around the web.
That’s it for today. Have fun! Subscribe to my RSS Feed if you enjoy these daily Interesting Bits posts. Kevin Posted in Interesting Bits |
| Posted: 05 Nov 2008 03:26 PM CST |
| Historic Election, Historic Traffic? [Last In - First Out] Posted: 05 Nov 2008 01:33 PM CST
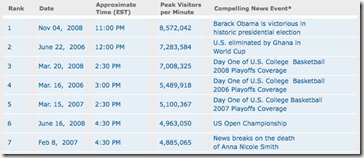
The Akamai Net Usage Index[1] hit a record last night, claiming 8 million odd visitors per minute to Akamai hosted news sites. Pretty cool, eh? The world tuned in to the election and traffic records were set. Maybe. One analysis is that Internet traffic reached 'historic highs'[2] during the historic election. The other possibility is that Internet traffic from Akamai hosted news sites reached historic highs. My guess is that there is a difference. Just for grins – take a look at the runners up to the 'record'.
Let see – as runners up to the election, we've got Ghana-US soccer from 2006; A bunch of playoff games for sporting events that most of the world doesn't even know exist, and the death of a failed gold-digging actress turned pathetic celebrity. No mention of the Olympics, World Cup Soccer Finals, earthquakes, famine, hurricanes, typhoons or wars. Somehow a mere 20% difference in traffic between this election and the second and third place events doesn't sound right, and the absence of what one would think were major world wide events is even more suspicious. I'm guessing that either the entire world is badly obsessed with irrelevant American celebrities and sporting events, or that the numbers are somehow skewed.
I sure hope it's the latter. 1Akamai Net Usage Index |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |


 Rogue Wireless Access Points on an Enterprise Network", which can be found in the OS Detection Chapter. Now, there is an example Nmap command in the book, but I came up with the following Nmap command on my own to do this on my home network:
Rogue Wireless Access Points on an Enterprise Network", which can be found in the OS Detection Chapter. Now, there is an example Nmap command in the book, but I came up with the following Nmap command on my own to do this on my home network: Nmap Parser was also featured in PaulDotCom Security Weekly
Nmap Parser was also featured in PaulDotCom Security Weekly 





No comments:
Post a Comment