Spliced feed for Security Bloggers Network |
| Commtouch Honored with Deloitte Technology Fast 50 [Commtouch Café] Posted: 03 Nov 2008 02:00 AM CST Commtouch is pleased to have been selected as #7 in the 2008 Deloitte Israel Technology Fast 50, a ranking of the 50 fastest growing technology companies in Israel. To determine the fastest growing companies, Deloitte reviewed fiscal year revenues over five years (2003-2007), calculated the revenue growth percentage over five years, and compared [...] |
| SecViz now has a Twitter feed [SOURCE Conference Blog] Posted: 03 Nov 2008 12:29 AM CST |
| HITB 2008 Malaysia Presentations [Infosec Events] Posted: 02 Nov 2008 10:42 PM CST The presentations from Hack in the Box Malaysia are now online and available to download on the HITBSecConf2008 Malaysia Conference page. All the presentations are in one directory, so it is easy download them all with something like wget or httrack. But for those that like direct links from this site, here they are: Keynotes
Track 1
Track 2
Track 3
|
| OpenBSD 4.4 Released [CGISecurity - Website and Application Security News] Posted: 02 Nov 2008 04:33 PM CST "Nov 1, 2008. We are pleased to announce the official release of OpenBSD 4.4.This is our 24th release on CD-ROM (and 25th via FTP). We remainproud of OpenBSD's record of more than ten years with only two remoteholes in the default install.As in our previous releases, 4.4 provides significant improvements,including new... |
| It was twenty years ago today [Emergent Chaos] Posted: 02 Nov 2008 11:57 AM CST It was twenty years ago today Sgt. Morris taught the worms to play They've been going in and out of style But they're guaranteed to last a while So may I introduce to you... the bug you've known for all these years Sgt. Morris Lonely worm club band We're Sgt. Morris' lonely worm club band, It's wonderful to be here I don't really want to stop the show and Sgt. Morris Lonely worm club band! |
| Is your refrigerator running? [StillSecure, After All These Years] Posted: 02 Nov 2008 11:17 AM CST Maybe you should go catch it. Most of you have played some sort of iteration on this one over the phone when you were a kid. But a couple of radio DJs from Montreal actually managed to dupe Sarah Palin herself evidently. C/Net reports that the duo known as the "Masked Avengers" actually convinced Mrs Palin and her team that they were French President, Nicolas Sarkozy. Even when the supposed Sarkozy acts just a bit too goofy, Governor Palin doesn't pick up on it. I don't necessarily approve of this kind of thing, but I question her people not checking on this before putting her on the phone and I question her for not catching on to this. Another incident of social engineering being successful way too easily! I guess you can't see France from her doorsteps. Anyway, here is the audio on this one: Related articles by Zemanta
This posting includes an audio/video/photo media file: Download Now |
| Google Provides Details on how it Determines [Sunnet Beskerming Security Advisories] Posted: 02 Nov 2008 05:18 AM CST A recent post at the Google Online Security Blog provides some background on how Google generates the "This site may harm your computer" warnings that appear from time to time in Google searches. It all boils down to automated scanners detecting the presence of malicious content. The article identifies that at least some of the scanners have been created by Google staff, though it is possible that commercial and freely available tools are also in use to generate the results. Although the results are defined as "accurate" there is no information about what level of false positives or false negatives manage to slip through the net. There are enough problems with similar available toolsets to suggest that Google's own approach is not the panacea that it might appear to the uninitiated. If you think that your site has been misidentified as having malicious content from the Google scanners, then they have provided a straight forward link to go to and check on exactly what it was that triggered the initial labelling. The basic site is http://www.google.com/safebrowsing/diagnostic, and it can be made site specific by adding ?site=site_name at the end of the link. For example, the result for Sûnnet Beskerming is this. Google's Webmaster Tools will also provide added information about what was scanned and found, though not the complete list of URLs that have been identified as problematic. Once whatever problem that was discovered has been rectified, there are procedures available to request a review for your site from Google (Overview page in the Webmaster Tools part of the site). Since the review process is effectively the same as the original automated scan (i.e. it is another automated scan), the complete process to remove the unsafe indication should only take a few hours, a day at most. On the other hand, if you have found that your site has completely disappeared from the Google results, it may be due to it being a "spammy website", in which case a Request for reconsideration is the appropriate action to take. |
| 20th Anniversary for Poorly Written Network Worms [Sunnet Beskerming Security Advisories] Posted: 02 Nov 2008 05:15 AM CST 20 years of poorly written havoc-causing network worms will come to pass on November 2, as it marks the 20th anniversary of the Morris Worm, considered the first major network attack on the Internet. Despite only reaching an estimated 6,000 systems, it still represents 10% of the available systems on the Internet at that time. There is some argument over the exact number of systems compromised and the overall percentage of Internet hosts affected, but the widespread impact of the worm is the most significant outcome. Not only was it one of the earliest examples of an automated denial of service attack (which came about because the detection routine to tell if another copy of the worm was present had a bug in it), but it also led to the creation of the CERT Coordination Center (CERT/CC), which preceded US-CERT by several years and is meant to be one of the key management centres for Internet related attacks and problems. Robert Morris, the worm's creator, was convicted under the Computer Fraud and Abuse Act and was eventually sentenced to probation (3 years), community service (400 hours) and a fine ($10,000). For Morris, he has now entered the academic staff as an Associate Professor at the institution he used to launch the attack, MIT, despite being at Cornell when the worm was originally released. Whether or not the worm was designed for malicious use, or, as Morris has claimed, to map the Internet, the fact remains that it ended up acting as a malicious worm. The use of vulnerabilities in sendmail, finger, rsh, weak passwords, and the attempt to hide the source of the attack (using a system at MIT rather than at Cornell where Morris was) would nowadays suggest motives that weren't completely pure. A problem with this line of thought is that it is extremely difficult to identify an outcome from the worm which could be considered beneficial for a malicious attacker. The mid 80s were an interesting time for Information Security. The first viruses and trojan horses appeared in 1986, so there was a lot of advancement in malicious activity taking place in a very short period of time and next year marks the 20th anniversary of ransomware - the particularly nasty type of malware that encrypts a victim's content and then demanding payment for a decryption key that will decrypt the content back to its original state. |
| Information Security Events in November [Infosec Events] Posted: 01 Nov 2008 11:16 AM CDT The number of information security events in North America is finally slowing down. This month there are only two events going on:
But there are a ton of other information security events around the world going on:
|
| index.asp Server Error [Digital Soapbox - Security, Risk & Data Protection Blog] Posted: 01 Nov 2008 09:19 AM CDT |
| JavaScript engines comparison [Robert Penz Blog] Posted: 01 Nov 2008 04:55 AM CDT A friend of mine has done a comparison of different browsers on a state of the art system. The System runs under Windows XP SP3 on a Core 2 Quad Core CPU (Q9450, 2,66GHz) with 3,5 GB RAM. He did use following test. Smaller bars are better, as the browser was able to process the data faster. The x-axis shows the seconds a browser took for the test. 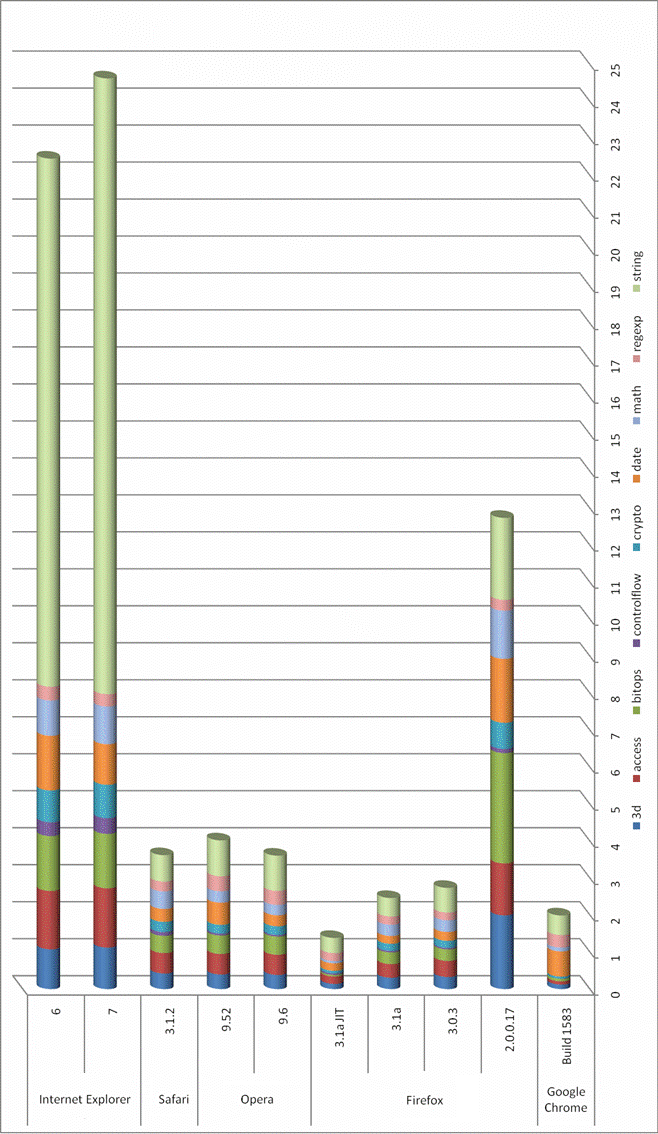 As you can see there are quite some differences which you should be able to “feel” also on current AJAX driven sites. Specially the new JIT (only in beta and not activated by default currently) for Firefox should make it the performance leader. |
| Kubuntu 8.10 Intrepid additional packages install script [Robert Penz Blog] Posted: 01 Nov 2008 04:28 AM CDT This script is for my friends, who most know the previous versions already. It installs additional packages for kubuntu 8.10 Intrepid. I use it for the initial setup of a desktop system. First install Kubuntu from CD and than use this script to get the system which, has all codecs and commonly used programs (be it free or non free software) installed. So this blog entry is for my own reference and for my friends. Basically after running this script you'll have a system which is ready for usage by a standard user. |
| Amusing log messages [Last In - First Out] Posted: 31 Oct 2008 06:09 PM CDT I give Cisco credit for fully documenting firewall log messages. In theory this gives users the ability to set up a system for catching interesting log messages and ignoring uninteresting messages. More vendors should be so bold as to actually acknowledge that their products log messages, and that those messages need to be documented. This level of disclosure has an interesting side effect. I'm not sure what I'd do if one of our ASA's logged this error: Or this error:Error Message %ASA-2-716515:internal error in: function: OCCAM failed to allocate memory for AK47 instanceExplanation The OCCAM failed to allocate memory for the AK47 instance. Error Message %ASA-2-716508: internal error in: function: Fiber scheduler is scheduling rotten fiber. Cannot continuing terminatingExplanation The fiber scheduler is scheduling rotten fiber, so it cannot continue terminating. Fiber rot? An AK47 instance? No doubt those messages mean something to someone at the TAC. For the rest of us, they are mostly just amusing. |
| NIST SeeksNew Hash Algorithm [Articles by MIKE FRATTO] Posted: 31 Oct 2008 02:36 PM CDT |
| Pitchforks in sheds [IT Security: The view from here] Posted: 31 Oct 2008 02:02 PM CDT I once heard someone describe network tools as 'pitchforks in sheds' - the basic premise being that although the tools themselves were all incredibly useful, without someone to use them, they are essentially useless. I've looked at a lot of security tools in my time, and have seen some great ones. HP recently showed me WebInspect, which looks like a great hacking tool on its own, and an awesome development and QA tool in conjunction with other pieces of software in the family. They obviously know this, because they invited me to a dinner which I sadly couldn't make. I always think that when a company is confident enough to invite critics for a dinner, the tool is probably a market leader which wants to stay in that position. If it's just a presentation, then it's probably a start up. Just a thing I've noticed over the years... anyway, back to the point. There are a great many tools out there which are very useful for networks, security focused or otherwise. However, without someone to roll-out, manage, and insert into processes - i.e. to get them used now and in the future - you may as well make a big pile of company cash in the car park and have bonfire night early. |
| Skein Hash Function [CGISecurity - Website and Application Security News] Posted: 31 Oct 2008 01:19 PM CDT "Executive Summary Skein is a new family of cryptographic hash functions. Its design combines speed, security, simplicity, and a great deal of flexibility in a modular package that is easy to analyze. Skein is fast. Skein-512 -- our primary proposal -- hashes data at 6.1 clock cycles per byte on a... |
| Win a free pass to CSI2008 in DC! [Branden Williams' Security Convergence Blog] Posted: 31 Oct 2008 01:16 PM CDT Thanks to the Security Blogger's Network, I am pleased to offer one free pass to CSI 2008 in DC! You will need to put some thought into your entry as this is not just some easy give away. To enter into this contest, all you need to do is email me your favorite security related story. Something that you saw that was clearly a huge security problem. Like if you saw a metal detector in a building that was maybe turned off, or maybe a NEXT box running an e-commerce web server in the last year. Here are the rules:
Since there are only a few of you out there that read this, the odds are pretty good of winning! If you don't want to enter and just want to get 25% off your registration, enter the code 'BLOG25' during the registration process! |
| Experience and Decision Making [Emergent Chaos] Posted: 31 Oct 2008 11:03 AM CDT Following on our satirical endorsement of McCain-Palin yesterday, I'd like to talk a little about the experience argument, that is, that Obama lacks the experience to be President. This may well be true. I'd prefer someone with extensive executive experience, ideally running a state, experience matters in one very specific way: it may help you make better decisions. Having a wealth of experience may lead to the wisdom of age, or being a grouchy old person. I see two key decisions that each candidate has had to make since the convention. One with time for reflection and consideration, and one snap decision. The first, of course, is their Vice President, and the second, how to react to the emergent financial crisis. Let's look at McCain's decisions: Palin, and suspend the campaign. In each case, a honed political calculus was the experience McCain applied. Palin is a great candidate: appealing to both the radical right and disaffected Hillary voters. A great speaker. The leader of America's most socialist state, where each citizen gets $3,200 from the state, just for breathing. And she is so not qualified to be President, she's a drag on the ticket. It was a great political gamble, and an awful one for a 72 year old cancer survivor to apply to the Presidency of the United States. Contrast with Obama, who chose an experienced foreign policy expert who had already run for President. The choice to suspend the campaign was also brilliant politics. McCain, suffering from a self-imposed inability to raise funds, needed a dramatic response to the crisis. But he has no background in finance. No long experience regulating it. No seats on the relevant committees. And rather than letting the professionals do their jobs, McCain decided to grandstand. Contrast with Obama, who said "My strong feeling was that this situation was of such seriousness that it was important not to chase the cameras." So experience matters because it helps you make decisions in the framework of what's important to you. It seems that winning, not governing, is what's important to John McCain. On the other hand, Obama does lack experience. But it seems to me that he makes decisions well, and will continue to do so. |
| Posted: 31 Oct 2008 05:19 AM CDT  Image via Wikipedia Looks like McAfee is going to need a new addition to the ePO uber-suite. They need something to plug the back door of their own marketing machine! It seems a product marketing manager at the security firm and her husband steered about 3.8 million dollars to firms that they had a financial interest in. They were arrested and charged according to this article. I guess the (in)famous Total Protection Suite didn't have an anti-marketing rip off module or maybe it just wasn't up to date ;-) Seriously it just goes to show that you can have all of the security technology and safeguards you want. People are still the greatest threat! |
| The Security Bloggers Network and CSI conference [StillSecure, After All These Years] Posted: 31 Oct 2008 04:59 AM CDT  Image via Wikipedia The Security Bloggers Network (SBN) is pleased to announce that the Computer Security Institute (CSI) and the SBN will be promoting and participating in this years annual CSI conference, Nov 15-21 at the Gaylord National in the Washington, DC area. The CSI show is always one of the biggest security events of the year with a full program of sessions and large exhibit. The SBN with over 185 member blogs, is the largest aggregated feed of security blogs in the world. The folks at CSI recognizing the power and influence of blogs in the media have asked us to help promote the event and invited SBN members to attend as press. Additionally the good folks of CSI have allowed us to make available some benefits to our readers as well: 1. If you would like to attend the conference you can receive a 25% discount by using our special code: BLOG25 2. I have one full boat conference pass. That is right for the entire conference including sessions! This is over a 2,000 dollar value. I will be awarding it to the person who comments on this post with the best and most interesting story on how attending security conferences such as CSI have helped you in your security related job. Just leave a comment with your award, but be sure to leave an email for me to contact you. I will pick one person by next Wed.. Good luck! It is good to see the SBN getting this kind of coverage. I am looking forward to attending CSI this year and hope to see you there!
|
| Google Hacking and the Dangers of Search Engines [ImperViews] Posted: 31 Oct 2008 03:02 AM CDT My main concerns with respect to these threats are: -Lack of awareness (and hence the lack of proper mitigation tools). -Search engine operators, while trying to mitigate some of the issues, do not distinguish between application owners and potential attackers. For example, there is a limit to the search rate based on source IP address. While true attackers are hardly affected by this, site owners are denied the possibility of automated, proactive mitigation. Together with SQL Injection rennaisance, I think that search engine related threads are a growing trend in web application threats. - Amichai |
| Happy (Belated) First Birthday! [Security Thoughts] Posted: 31 Oct 2008 02:27 AM CDT .... to my ADSL application. Last year in October a salesperson at Telkom phoned to let me know that my phone exchange supports ADSL and do I want to upgrade my line to have ADSL? I did the maths and worked out that it would be cheaper for me to have ADSL and have the benefit of all-time-on access to the Internet. So, I applied and a few days later my application was processed and I had an application number. It all got to the point where I had the modem connected and ready when a technical person at the exchange noticed that "no, the exchange is potentially ready for ADSL but was not, in fact, ready." "But, good news, there is a project to upgrade the exchange to be ADSL capable. It should be done by latest end of December 2007." That became end of January, end of February, end of April... then it jumped to end of June. Now it is scheduled to be completed by the end of April 2009. The way things are looking - I'll probably be celebrating the second birthday of my ADSL application this time next year... many happy returns. |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |
 Follow SecViz on the brand new twitter feed:
Follow SecViz on the brand new twitter feed: ![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=bfc733c7-8fa7-4d0b-830f-3843bbc40216)


![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=4219609d-c293-4d5b-ab02-1b8c3671ef94)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=e4dce0ef-2a62-43ee-855d-fb39c4bd4957)

No comments:
Post a Comment