Spliced feed for Security Bloggers Network |
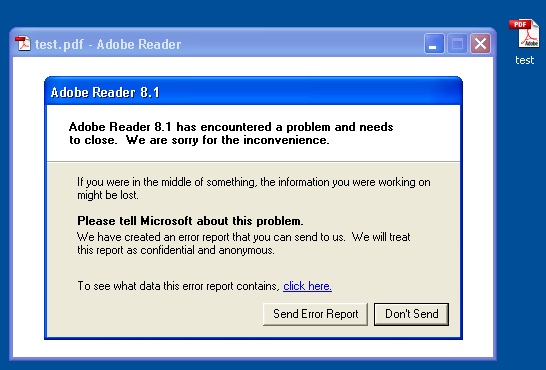
| Creating PDF Test-Files [Didier Stevens] [Belgian Security Blognetwork] Posted: 09 Nov 2008 06:56 AM CST As promised, I’m releasing a couple of my PDF tools as a warm-up to my ISSA Belgium and OWASP Belgium talk. After having manually created some PDF test-files (just using a text editor), I stepped up to the next level and wrote a quick-and-dirty Python module to generate PDF documents by assembling fundamental PDF elements. My mPDF.py module contains a class with methods to create headers, indirect objects, stream objects, trailers and XREFs. One of the programs I wrote based on this module is make-pdf-javascript.py. This Python program allows me to create a simple PDF document with embedded JavaScript that will execute upon opening of the PDF document. Program details and download here. An example: to create a PDF document exploiting the util.printf Adobe Reader vulnerability in its simplest form (e.g. no shellcode and no heap spray), issue the following command:
Here it crashes Adobe Reader 8.1.2 on Windows XP SP2:
 |
| Cisco IOS Router Security mind map [Francois Ropert weblog] Posted: 09 Nov 2008 05:58 AM CST I just created a mind map about securing a Cisco IOS router. The map gives you information about how securing services and how to secure the device itself from attacks. It's like a cheat sheet but a graphic's one and very compact compared to hundreds of pages in various security best-practices guides. |
| Cloud Computing: Invented By Criminals, Secured By ??? [Rational Survivability] Posted: 09 Nov 2008 02:02 AM CST I was reading Reuven Cohen's "Elastic Vapor: Life In the Cloud Blog" yesterday and he wrote an interesting piece on what is being coined "Fraud as a Service." Basically, Reuven describes the rise of botnets as the origin of "cloud" based service utilities as chronicled from Uri Rivner's talk at RSA Europe: I hate to tell you this, it wasn't Amazon, IBM or even Sun who invented cloud computing. It was criminal technologists, mostly from eastern Europe who did. Looking back to the late 90's and the use of decentralized "warez" darknets. These original private "clouds" are the first true cloud computing infrastructures seen in the wild. Even way back then the criminal syndicates had developed "service oriented architectures" and federated id systems including advanced encryption. It has taken more then 10 years before we actually started to see this type of sophisticated decentralization to start being adopted by traditional enterprises.
In this new world order, cloud computing will not just be a requirement for scaling your data center but also protecting it.
One of the obvious benefits of cloud computing is the distribution of applications, services and information. The natural by-product of this is additional resiliency from operational downtime caused by error or malicious activity. This benefit is a also a forcing function; it will require new security methodologies and technology to allow the security (policies) to travel with the applications and data as well as enforce it. I wrote about this concept back in 2007 as part of my predictions for 2008 and highlighted it again in a post titled: "Thinning the Herd and Chlorinating the Malware Gene Pool" based on some posts by Andy Jaquith:
This basically means that we should distribute the sampling, detection and prevention functions across the entire networked ecosystem, not just to dedicated security appliances; each of the end nodes should communicate using a standard signaling and telemetry protocol so that common threat, vulnerability and effective disposition can be communicated up and downstream to one another and one or more management facilities. It will be interesting to watch companies, established and emerging, grapple with this new world. /Hoff |
| Picture Puzzle [Didier Stevens] [Belgian Security Blognetwork] Posted: 09 Nov 2008 01:41 AM CST As I announced via Twitter, here’s a new puzzle. Find the message I’ve hidden in this picture. First one to post a comment with the correct answer can get a sticker. For those who don’t know, comments are moderated.
 |
| Gone Fishing! Taking the Weekend Off [Infosecurity.US] Posted: 08 Nov 2008 11:43 AM CST |
| Stiennon's first law of analyst blogging: Blog's abhor a vacum [StillSecure, After All These Years] Posted: 08 Nov 2008 11:14 AM CST
I heard that Richard was not going to re-launch ThreatChaos because he was about to take an executive position with a NAC company, but that NAC company went out of business. Too bad, I would have liked to see Richard hawking NAC. Just kidding. In any event and in all seriousness I actually like Richard and despite our many blog slugfests, have a lot of respect for him. I wish him well in this old/new endeavor and I am sure he will have lots to say now that the handcuffs are off. Look for the new Threat Chaos in the Security Bloggers Network feed soon. |
| Educational Software Don’t Care For Security! [/dev/random] [Belgian Security Blognetwork] Posted: 08 Nov 2008 10:30 AM CST
I’m pissed off! Educational softwares don’t care for security at all! I have two daughters and, like all children, they like to play on the computer. As they cannot use my own systems (of course!), they have access to a laptop where games and educational softwares are installed. They have their own accounts and no administrative rights! So, when they receive a new CD/DVDROM, it must be installed by myself, I’ve no problem with this but… Often, the software requires administrative rights (it try to write files in a forbidden directory), files are only available to the administrator (no shortcut nor menu are created) or even does not start at all! It just like back to the eighties when only one application can run at a time! Dear developers, could you please take core of security when you write applications? Even more for children! |
| domainregistrars that have dubious addresses [belsec] [Belgian Security Blognetwork] Posted: 08 Nov 2008 09:25 AM CST June 10, 2008As part of our ongoing effort to ensure compliance and improve responsibility on the part of Internet stakeholders KnujOn is posting the results of recent investigation of the public disclosure of the locations of registrar companies. We have found 70 registrars listed on the Internic registrar directory missing street addresses and/or phone numbers. More serious are the following registrars that do not even have the country of location listed: EvoPlus Ltd., Hecta Media, Inc., Hostgator.com LLC, OnlineNIC, Inc., Thought Convergence, Inc., and Verelink, Inc. |
| Deborah Ostrega has a lucky sex story to tell [belsec] [Belgian Security Blognetwork] Posted: 08 Nov 2008 08:46 AM CST She made some phonecam films while having sex with her boyfriend but....she lost the phone one day. In fact it was stolen and the thief wanted to sell the phone with the films to a magazine (Story). Luckily the chief editor of the magazine showed some interest but only to get the address of the thief. Once he got the address he told him to give him the phone and that he may be lucky that he didn't inform the police. Deborah was already afraid that the films would have been posted on the internet. They seem to have been very explicit. She says that "everybody does it". But I doubt everybody would have been so careless with their phone with that kind of stuff on it. She has learned her lesson now, she will keep the phonecam with the pix on her table next to her bed, in case anybody is visiting here. ..... :) Britney spears is maybe her inspiration.
my tip : destroy them or print them out before, anything digital will travel one day |
| steroids spam : how to know if your site is infected [belsec] [Belgian Security Blognetwork] Posted: 08 Nov 2008 08:32 AM CST They mostly come with links in your forum or other interactive functions. I am sure that you don't really need those functions in most of the cases and that they are filled with spam, porn and bullshit. The few people that will have left a message could have sent you an email anyway and you could have republished those. In Google you type site:mijnsite.be of com of ..... followed by steroids, pharmacy, sex, porn or whatever and than you can decide to just close it down or clean it up and keep it clean there are hundreds of sites in the .be domain that are infected with foruminfecting spamlinks of all kinds - even big sites and governmental sites. |
| Its Husker Time [BumpInTheWire.com] Posted: 08 Nov 2008 08:09 AM CST |
| Humo pix we have to disable the link [belsec] [Belgian Security Blognetwork] Posted: 08 Nov 2008 07:40 AM CST Humo has published in a kind of satirical (but stupid and banal) way some pseudo porn pix in which they had changed the heads by those of our national chief of police and his two secretaries. It seemed that they had been promoted to a function that was better paid but that they couldn't get normally and there was a lot of commotion around that. Some people suggested that they were having an affair. The police chief and one of the secretaries went to the court to ask that the Humo with those pix were retired from all the shops around the country at once. The judge seemed to agree and so was done. In appeal the same judge went now even a bit further and said that any distribution in any kind of way of these pix was illegal. This makes us vulnerable to a claim for damages for pix that we didn't make and even don't like at all because they are so stupid and childless that it ain't worth any breath, let alone a penny. I even don't something humorous about that. There are a thousand ways in which you can laugh with the situation and those pix show that you lack the quality and the artists to do it in a better way. I don't agree with the way in which the judge decided to make such judgements without hearing all the parties involved, but I do agree that you can't as a major weekly publish such garbage and call it satire. There is nothing satire about the pix. And this ain't the fight for the freedom of the press. There are other fights for more freedom of the press and a more investigative approach by the press that are much more worthless because they advance the debate and the control by the fourth pillar of our democracy. This is the reason that we have censored the link to the pix. If you are a bit web knowable you should be able to find the older posting and the link. |
| Free for today professional calendarmaker [belsec] [Belgian Security Blognetwork] Posted: 08 Nov 2008 07:28 AM CST The easiest way to create professional calendars in seconds. Posted: 08 Nov 2008 02:00 AM CST This calendar maker allows you to create customized photo calendars using your own photographs or sample built in photographs. Share photos of your loved ones and children easily, use the customized calendars as great gifts! Save time and money creating calendars yourself, plus show you care with calendars for birthdays and holidays! |
| Nieuw nederlandstalig weekoverzicht [belsec] [Belgian Security Blognetwork] Posted: 08 Nov 2008 07:26 AM CST http://www.netties.be/extra/belsec_081106.htm Gepubliceerd bij http://www.netties.be in het kader van onze samenwerking. Voor zij die er niet in slagen om ons te blijven volgen maar toch willen zeker zijn dat ze niets belangrijks gemist hebben. De 4 weekoverzichten van oktober vind je trouwens op netties.be |
| countering spam with a vengeance. [Domdingelom on security, fun and life] Posted: 07 Nov 2008 06:11 PM CST You know them, heartwarming stories that try to tear you up about kids, sick people, adoptions gone awry ... whatever. It never seems to stop, until I received this one. In 1986, Peter Davies was on holiday in Kenya after graduating from Northwestern University . On a hike through the bush, he came across a young bull elephant standing with one leg raised in the air. The elephant seemed distressed, so Peter approached it very carefully. He got down on one knee, inspected the elephants foot, and found a large piece of wood deeply embedded in it. As carefully and as gently as he could, Peter worked the wood out with his knife, after which the elephant gingerly put down its foot. The elephant turned to face the man, and with a rather curious look on its face, stared at him for several tense moments. Peter stood frozen, thinking of nothing else but being trampled. Eventually the elephant trumpeted loudly, turned, and walked away. Peter never forgot that elephant or the events of that day. Twenty years later, Peter was walking through the Chicago Zoo with his teenaged son. As they approached the elephant enclosure, one of the creatures turned and walked over to near where Peter and his son Cameron were standing. The large bull elephant stared at Peter, lifted its front foot off the ground, then put it down. The elephant did that several times then trumpeted loudly, all the while staring at the man. Remembering the encounter in 1986, Peter could not help wondering if this was the same elephant. Peter summoned up his courage, climbed over the railing, and made his way into the enclosure. He walked right up to the elephant and stared back in wonder. The elephant trumpeted again, wrapped its trunk around one of Peter legs and slammed him against the railing, killing him instantly. Probably wasn't the same fucking elephant. This is for everyone who sends me those heart-warming bullshit stories. |
| iPhone - Linux VPN [/dev/random] [Belgian Security Blognetwork] Posted: 07 Nov 2008 02:19 PM CST
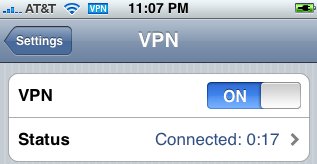
The iPhone 3G firmware is really open to the world via 3G or Wi-Fi. Compared to Wi-Fi, mobile networks are quite secure. Warning, I never said that they are bullet-proof, but tapping a mobile network requires much more resources than Wi-Fi! Wireless network are widely available, which make them a good target for hackers! On the iPhone, common applications can be secured (HTTPS in Safari and the mail client support SSL encryption) but the remote server must offer SSL services! Fortunately, the iPhone supports VPN! Three types of VPN are available: IPSEC, L2TP and PPTP. In this case, to protect our personal information, why not encrypt all the traffic through a VPN session established with a remote server? Let’s go! Warning: Some firewall or access points may not forward GRE packets! PPTP Server SetupMy Linux runs a stock Debian distribution. To install the PPTP server, just install the package: # apt-get install pptpd If needed, fix your firewall to accept incoming traffic on port TCP/1723 and GRE protocol # /sbin/iptables -A INPUT -i eth0 -p tcp --dport 1723 -j ACCEPT # /sbin/iptables -A INPUT -i eth0 -p 47 -j ACCEPT The PPTP server relies on a single configuration file “/etc/pptpd.conf“. The default settings should work out of the box. The only thing to care of is the IP address attribution (which cannot conflict with your existing IP networks). Fix them to match your network: localip 192.168.0.1 remoteip 192.168.0.234-238,192.168.0.245 As pptpd spawns a ppp process. The following modules must be available: # lsmod | grep ^ppp ppp_async 6496 0 ppp_generic 13556 1 ppp_async ppp_mppe 5643 0 Normally they are installed in a standard kernel distribution. Mine is a bit exotic (Debian running on a Cobalt server). VPN Users SetupNow, create your VPN users. Authentication is performed by PPP. Add users accounts with the following command: # echo "<username> pptpd <password> *" >>/etc/ppp/chap-secrets Be sure to set safe access right to this file! If you have a lot of users, consider using another authentication method such as RADIUS. Setup Routing and NATWe need to enable IPv4 forwarding and NAT on the PPTP server. All packets coming from the iPhone will be translated to the server IP address to access the Internet. # echo 1 >/proc/sys/net/ipv4/ip_forward # iptables -t nat -A POSTROUTING -o eth0 -s 192.168.0.0/24 \ -j SNAT --to <serverip> Customize the commands above according to your environment and put them in your init scripts to survive to a reboot. iPhone ConfigurationTap on “Settings”, “VPN” and “Add VPN Configuration”. Select “PPTP” as VPN type, and fill all the required fields:
Save and slide the VPN switch to “On”. Your iPhone will setup the VPN. Once successfully done, use your applications as usual. Everything will be encrypted up to your Linux server! Here is a successful connection as seen from the Linux side in debug mode: pptpd[27539]: MGR: Launching /usr/sbin/pptpctrl to handle client pptpd[27539]: CTRL: local address = 192.168.0.1 pptpd[27539]: CTRL: remote address = 192.168.0.234 pptpd[27539]: CTRL: pppd options file = /etc/ppp/pptpd-options pptpd[27539]: CTRL: Client 81.169.73.7 control connection started pptpd[27539]: CTRL: Received PPTP Control Message (type: 1) pptpd[27539]: CTRL: Made a START CTRL CONN RPLY packet pptpd[27539]: CTRL: I wrote 156 bytes to the client. pptpd[27539]: CTRL: Sent packet to client pptpd[27539]: CTRL: Received PPTP Control Message (type: 7) pptpd[27539]: CTRL: Set parameters to 100000000 maxbps, 64 window size pptpd[27539]: CTRL: Made a OUT CALL RPLY packet pptpd[27539]: CTRL: Starting call (launching pppd, opening GRE) pptpd[27539]: CTRL: pty_fd = 6 pptpd[27539]: CTRL: tty_fd = 7 pptpd[27540]: CTRL (PPPD Launcher): program binary = /usr/sbin/pppd pptpd[27540]: CTRL (PPPD Launcher): local address = 192.168.0.1 pptpd[27540]: CTRL (PPPD Launcher): remote address = 192.168.0.234 pppd[27540]: Plugin /usr/lib/pptpd/pptpd-logwtmp.so loaded. pptpd[27539]: CTRL: I wrote 32 bytes to the client. pptpd[27539]: CTRL: Sent packet to client pppd[27540]: pppd 2.4.4 started by root, uid 0 pppd[27540]: Using interface ppp0 pppd[27540]: Connect: ppp0 <--> /dev/pts/3 pptpd[27539]: GRE: Bad checksum from pppd. pptpd[27539]: GRE: Bad checksum from pppd. pptpd[27539]: CTRL: Received PPTP Control Message (type: 15) pptpd[27539]: CTRL: Got a SET LINK INFO packet with standard ACCMs pptpd[27539]: GRE: buffering packet #1 (expecting #0, lost or reordered) pptpd[27539]: GRE: buffering packet #2 (expecting #0, lost or reordered) pptpd[27539]: GRE: timeout waiting for 1 packets pptpd[27539]: GRE: accepting #1 from queue pptpd[27539]: GRE: accepting #2 from queue pptpd[27539]: GRE: accepting packet #3 pptpd[27539]: GRE: accepting packet #4 pptpd[27539]: GRE: accepting packet #5 pptpd[27539]: GRE: accepting packet #6 pppd[27540]: kernel does not support PPP filtering pptpd[27539]: GRE: accepting packet #7 pptpd[27539]: GRE: accepting packet #8 pptpd[27539]: GRE: accepting packet #9 pptpd[27539]: GRE: accepting packet #10 pptpd[27539]: GRE: accepting packet #11 pptpd[27539]: GRE: accepting packet #12 pptpd[27539]: GRE: accepting packet #13 pppd[27540]: Cannot determine ethernet address for proxy ARP pppd[27540]: local IP address 192.168.0.1 pppd[27540]: remote IP address 192.168.0.234 pptpd[27539]: GRE: accepting packet #14 pptpd[27539]: GRE: accepting packet #15 pptpd[27539]: GRE: accepting packet #16 pptpd[27539]: GRE: accepting packet #17 pptpd[27539]: GRE: accepting packet #18 pptpd[27539]: GRE: accepting packet #19 pppd[27540]: LCP terminated by peer (User request) pppd[27540]: Connect time 0.3 minutes. pppd[27540]: Sent 0 bytes, received 1450 bytes. pptpd[27539]: CTRL: EOF or bad error reading ctrl packet length. pptpd[27539]: CTRL: couldn't read packet header (exit) pptpd[27539]: CTRL: CTRL read failed pptpd[27539]: CTRL: Reaping child PPP[27540] pppd[27540]: Modem hangup pppd[27540]: Connection terminated. pppd[27540]: Exit. pptpd[27539]: CTRL: Client 81.169.73.7 control connection finished pptpd[27539]: CTRL: Exiting now pptpd[31956]: MGR: Reaped child 27539 |
| 2600 Meetings [HiR Information Report] Posted: 07 Nov 2008 11:18 AM CST It's that time again - The first Friday of the month! The Kansas City 2600 meeting will take place tonight at 5:00 PM (although I might be running a little late) at Oak Park Mall in the food court. Check the 2600 Meetings page to find one near you! |
| Detecting Rogue Access Points Using Nmap [/dev/random] [Belgian Security Blognetwork] Posted: 07 Nov 2008 08:49 AM CST
Rogue Wi-Fi access points are a pain for network administrators! A rogue access point is an unofficial device installed by somebody in a secure environment without authorization. Often, a rogue access point is installed not to perform malicious activities but is connected on the corporate network by a employer to use Wi-Fi inside the company. It’s very easy to do, even my 7-years daughter could do the installation! Unfortunately, it brakes the security policy and can be disastrous for the corporate assets: A rogue access point is usually badly or, worste, not configured at all (factory settings). It becomes easy for remote attackers to access confidential data or resources using this “backdoor”. Commercial products, like the Aruba mobility controllers, provide rogue access points detection mechanisms. Helas, they are not “free” and cost $$$. Paul Asadoorian, from pauldotcom.com, released in an excellent article: Discovering Rogue Access Points With Nmap. Using the OS fingerprint feature of Nmap and some Perl code, Paul wrote a script which does perfectly the job! |
| Economic Uncertainty? Maybe it’s a Good Thing… [TriGeoSphere] Posted: 06 Nov 2008 08:53 PM CST
During the discussion I told them all, we’re “doubling down.” While everyone else in our space is cutting back (even Symantec is laying off nearly 5% of its workforce) TriGeo is hiring in almost every department and investing even more into our marketing and channel efforts. We have no intention of ducking for cover - we’re forging ahead and expanding. I see this economic downturn as an incredible opportunity for TriGeo. We’re in the best position out of all our competitors to weather this storm. TriGeo is profitable, cash flow positive, has a huge cash reserve and is debt free. I’m certain you won’t find any other private SIEM vendor who can say the same. It’s likely that the downturn will lead to the disappearance of many of the marginal SIEM and log management products on the market – a bit of ‘Natural Selection’ in action. This is the best possible news for consumers. They’ll get better products for better prices. Yep, I do think this cloud has a silver lining. |
| New Audio Podcast on my Trip to Madrid [Got the NAC] Posted: 06 Nov 2008 05:31 PM CST I recently returned from ISSE 2008 in Madrid, Spain. The conference highlighted some key differences between U.S. and European information security. Tune into this podcast and you’ll get some food for thought: lessons that you may be able to apply in your own work. Tags: General, ISSE, madrid, spain This posting includes an audio/video/photo media file: Download Now |
| Posted: 06 Nov 2008 04:47 PM CST  Well, it's patching time again, especially for the workstations! From US-CERT: Adobe has released a Security Bulletin to address multiple vulnerabilities in Flash Player. These vulnerabilities may allow an attacker to bypass security restrictions or obtain sensitive information.Why is this urgent? There are already active Social engineering and Phishing attacks against it in the form of United states Presidential Elections Emails. Have a look at this F-secure blogpost for examples and screenshots. I did the updates and checked with Secunia Online software Inspector to see if I missed something. I seemed my Skype was also out of date which I actually never use but I updated it just in case. It still sounds like a broken record: Adobe Reader, Flash, Firefox/IE7, Realplayer, Quicktime etc.... rinse and repeat (more often then should be needed). By the way, be warned because Office patches are scheduled for next week (Zero Day). Was any of the Adobe patches a zero day? What was happening behind the scenes? I found the following information on the "Ma petite parcelle d'Internet" blog (in French). It seemed that this Acrobat Reader vulnerability was first discovered by the Zero Day Initiative on the 21th of January 2008!!! This means it took 9 months to fix this stack overflow. This time allowed also Secunia and Core to discover this vulnerability !! All put together in one timeline this gives us:
Anyway, this will be an interesting topic to discuss at the next ISSA-BE and OWASP-BE Chapter meeting on the 17th of November in case you didn't check our security calendar (on the right side of this blog). Topics of the event: Risky pdf and .NET rootkits. I will be sitting front seat for this one with some questions! ;-) (UPDATE 7/11/2008): SANS ISC reported that there are pdf attacks in the wild. And indeed – at the time of writing this article, according to VirusTotal 0 (yes – ZERO) AV products detected this malicious PDF. Very, very bad.(Photo under creative commongs from Poppyseed Bandits' photostream) |
| My Twitter 15 minutes of fame [Security4all] [Belgian Security Blognetwork] Posted: 06 Nov 2008 03:42 PM CST  What the secret formula behind Twitter grader is, is unknown. The results vary from time to time. A review of it was also mentioned on the BVLG blog. Related posts:
|
| CPISM and CPISA certified individuals [PCI Blog - Compliance Demystified] Posted: 06 Nov 2008 02:33 PM CST
There are over a hundred people already CPISM certified (and one special individual), but tomorrow is the first public offering of the CPISA exam meaning they will be some of the first individuals certified under the CPISA. Good luck to all those who take the exam tomorrow. For more information on these certifications check out the SPSP website. |
| S4 Preview: Estimating # of 0days in Control Systems [Digital Bond] Posted: 06 Nov 2008 01:45 PM CST I will be previewing one S4 2009 paper each week. Digital Bond’s SCADA Security Scientific Symposium is Jan 21-22 in Miami Beach with an advanced control system security course on Jan 20th. Estimation and Observation of 0Day Vulnerabilities and Control Systems We have another strong S4 paper on control system security metrics from Miles McQueen and the team at INL - - this time with May Robin Chaffin. How many vulnerabilities for a device, OS or application are known by someone that have not been disclosed? Well the authors of this paper have an approach that analyzes the lifespan of 491 0day vulnerabilities and does a more in depth analysis of 15 of those 0days to come up with an estimation algorithm for the general IT space. But as is pointed out ad infinitum, control systems are different. In an 0day analysis context there is a much smaller set of security researchers, access to hardware and software is more difficult, and lack of public reporting is minimal. May and Miles take these and other factors into account and estimate the number of 0days in control system applications. Yet another important data point in helping to quantify and qualify risk. Other S4 Previews |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |






No comments:
Post a Comment