Spliced feed for Security Bloggers Network |
| Crimping Twisted-Pair Ethernet (and Crossover) [HiR Information Report] Posted: 06 Nov 2008 12:16 PM CST In the Geek 100, I said that every geek should be able to Terminate category 5 cable with RJ-45 plugs and make a crossover cable. While home networking isn't nearly as daunting as it used to be with ubiquitous WiFi routers, I stand by my assertion that no geek has a valid excuse for being unable to crimp some cables. It's a useful skill to have and it's quite easy to learn. All you need (aside from some Twisted-Pair ethernet cable that has bad ends or no ends) are some crimp-on RJ-45 plugs, a knife and a crimping tool. The plugs are less than $1 each at Radio Shack and cents each in bulk, knives are commodity and crimping tools like the one shown (I've had it for probably 15 years) are available for $20 or less. If your crimping tool doesn't come with a wire cutter, a pair of diagonal pliers might be useful as well. There are some much nicer crimping tools available that get really expensive, but the entry-level ones are probably just fine for the geek who only needs to run wires occasionally.  Take your knife and cut the sheath off about 3/4" of the end of the cable. Inside, there are four pairs: Blue, Orange, Green and Brown. Due to carryover from ye-olde telecom days, the pairs are divided into "Tip" (color striped with white) and "Ring" (solid color). Many cable manufacturers put a nylon strand, string, or tuft inside the sheath as well. This makes stripping a long length of sheath easy, but you can safely cut away whatever of it is exposed without harm. Arrange the wires in either of the two configurations shown below. We'll get to putting the RJ-45 plugs on in a moment. For the time being, focus on the order of the wires. 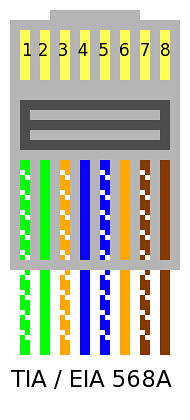 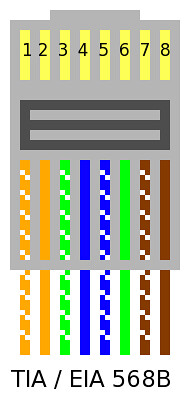 These days, 568-A is kind of "the standard" but when I was learning, the industry was hell-bent on using 568-B. Honestly, as long as you use the same 568 scheme on both ends of the cable and you crimp the RJ-45 plug properly, it really doesn't make a bit of difference at all. The wires are ordered this way to reduce crosstalk and interference, so I advise you stick with one of the two diagrams above. I have the wires ordered 568-B below. The tips (white-striped wires) are hard to determine in the photo, and sometimes they'll be tricky to identify in real life. You may wish to do this under an eye loop or a workbench magnifying lens if your eyesight is sub-par.  Use a wire cutter or a diagonal plier to cut the wires to the same length. It's important to keep the wires held flat and in the right order as shown above.  Slide the RJ-45 plug onto the cable end. Make sure the wires are still even and in the right order.  I stole this crimping "action shot" from the Loopback tester tutorial. Crimping the plug should be pretty straightforward. Make sure to give it a few good squeezes to ensure a good connection.  Make sure you wire both ends the same, and make sure the plugs are both installed facing the proper direction (with the metal pins pointed toward you and up). Here's another diagram I found on Wikipedia:  To make a crossover cable that can be used to connect two hubs/switches or two computers together (Without a hub or switch), simply wire one end as 568A and the other as 568B. |
| PTK Local Command Execution Vulnerability demonstration [Security Circus] Posted: 06 Nov 2008 05:12 AM CST |
| A reminder of why antiforensics is not an overblown threat [Security Circus] Posted: 06 Nov 2008 05:10 AM CST A recently discovered vulnerability (kudos as usual to ikki) in a forensic toolkit just hours after its release, reminds us of why antiforensics is an important threat which should not be dismissed lightly (and it should also remind authors that they should evaluate the security threat model a bit deeper than this). If you wish to understand better what is the problem and just how much impact it can have, have a look at the video I reposted above. My perception is that, as we will see an increase in the use of transient or definitive antiforensic techniques from now on, finding new ways to deal with antiforensics techniques of various kind is one of the research issues at hand in computer forensics research. |
| "Unix Terrorist" in trouble over TJX ? [extern blog SensePost;] Posted: 06 Nov 2008 04:32 AM CST Anyone who was around for Defcon-10 will have an opinion on the infamous Gobbles-Silvio-UnixTerrorist talk in which mail spools where published and everyone was slammed [1] According to mumble on the Interwebs (and a comment from RiskyBusiness) it appears as if the Stephen Watt who allegedly "modified and provided a "sniffer" program used by the conspirators to monitor and capture the data crossing corporate computer networks" == Unix Terrorist.. It's not clear the extent of Watts involvment with the breakin, but it does send a cold shiver down the spine of anyone who puts out tools / software.. /mh [1.] for me it just hurt seeing Silvio trying to make a real point while UT was trying to make a few jokes.. |
| A phishing way to hack an election [Security Circus] Posted: 06 Nov 2008 04:26 AM CST |
| OSS Security vs. COTS Security [Writing Secure Software] Posted: 06 Nov 2008 01:10 AM CST Just finished attending the Security Day hosted by the Sardenia(Italy) Research Park where I was the keynote speaker and invited to present on the topic of Open source projects for Web Application Security and to moderate a round table on the topic of security of OSS vs. COTS with participation of Italian information security managers from Microsoft, IBM ISS and consultants from Engineering and Ablativ consulting. The sub-themes stimulated at the round table were the following: 1) Did OSS adoption in EU (since 2004 directive) produced an increased security because of the diversity of systems/platforms being used? Answer: the point is that managing different platforms and systems can be very difficult while the uniformity of the platforms being used actually help more the secure configuration management effort (i.e. patching). The real objective is to have a secure environment/infrastructure and have a patch management process in place for all type of systems and applications 2) Some COTS advocate that their systems are more secured because is close. Security experts advocate the contrary since security by obscurity is not a good reason for keeping systems close (e.g. Kirckoff's second law principle). Answer: You need a security assessment process to validate the security of software that you acquire from OSS community or COTS vendors. Access to the source code is required for the evaluation and scrutiny of vulnerabilities. The source code scrutiny from "more eye balls" helps review software for vulnerabilities before adoption/release. Keeping the software closed (security by obscurity) is not a good reason for security as might be advocated by some COTS vendors. 3) Some source code analysis vendors (e.g. Fortify) advocate that OSS is not secure because it is not scanned for security bugs. Is this a call for vendors and companies to ask them to source code analyze OSS before adoption/integration? Answer: Again we need a process to security validate the libraries and systems we use/integrate independently being from OSS or COTS. Some customers of IBM asked for a certification process to provide evidence that the software has been security reviewed. Such certification could also be a way to provide legal guarantees to OSS and COTS users and could also be required by compliance with a new normative/regulation. 4) The time to patch is critical for the security of both OSS and COTS. There have been cases where Mozilla was recommended over IE by CERT (2004) based upon the fact that took MS 9 months to patch it. The same happens to OSS, it took more then one year to Debian to discover and patch OpenSSL. The point here is who takes liability of the risk of un-patched vulnerabilities and how we can require both OSS and COTS to timely patch. Answer: Ideally you need to establish a process to work with the software vendor before the zero day vulnerabilities are disclosed. This is what Microsoft is doing with MSVR for example. Time to release a patch is important but some data (e.g. IBM) show that actually system admins still leave systems unpatched even if patches have been available for a while. This seems to be a bigger problem then timely release of patches for 0 day vulnerabilities. 5) OSS is free but it is not maintenance free. Based upon the fact that fixing via catch and patch is expensive and that the cost is on the OSS integrator for the testing and deployment of the patches. Both OSS and COTS would rather continue to transfer the cost to the end user instead of bearing the cost themselves. This is despite the fact that would be much cheaper for OSS and COTS developers fixing their software bugs during the development cycle. Answer: Indeed we need a process to require vendors to fix the vulnerabilities in software before acquiring it and have the adopters patching them at their expense. The cost associated with developing patches can be a good reason for promoting secure software development in the SDLC. Microsoft proved increased security (e.g. reduced number of bulletins and costs (e.g. average cost of one bulletin is 100,000 $ according to MS) for example by comparing Windows 2003 server with Windows 2000 that did not adopt the SDL (Security Development LifeCycle.) The conference was very well organized and the location was just wonderful place to visit, hope to come back on vacation during the summer. |
| Windows Crash at O'Hair Airport Terminal [Digital Soapbox - Security, Risk & Data Protection Blog] Posted: 06 Nov 2008 12:14 AM CST  In my travels I go through a lot of airports, and every once in a while I run into something that gets my attention and I have to pull out my cell phone camera and snap a picture. Coming home from Detroit tonight... I just had to have this for my "Priceless" collection. I know, it's not necessarily a "security issue"... but it's a chuckle in a very tough week so bear with me. You'll notice that the offending driver is sysaudio.sys, which is strange because this terminal doesn't actually play any sound... ever that I've heard/seen when it was working. We really are "Greening" the City of Chicago... wait, what? Such a waste of a beautiful touch-screen display. |
| Phishing 2.0: Botnet based attacks and possible countermeasures [Writing Secure Software] Posted: 05 Nov 2008 10:15 PM CST Back in the early 2000 phishing was a matter to clone a web page of a target site, register a near legal looking domain and social engineer a victim with a phishing mail. Then phishers got little smarter, instead to clone it and do all this work why not point to a web proxy and act as man in the middle? This way phishing did not require fraudster to reverse engineer anything and sucessfully break into multi factor authentication. This was back in 2006 so most banks in US deployed strong authentication besides MFA controls also in response to FFIEC compliance on authentication guidelines. Since then phishing has evolved (the fradusters do not sleep) for example by exploiting man in the browser vulnerabilities to inject code that can executed by the browser or simply XSS vulnerabilites to execute malicious scripts to run keylogger pointing to the malicious sites. More recently the threat of phishing has evolved with the use of botnets. In 2008 more then 50% of phishing attacks are delivered with RBN (Russian Business Network) designed botnets such as Mpack, Storm, Asprox and RockPhish just to mention the more popular. These are tools for the trade to be used by professional fraudsters not script kiddies. They cost in the thousands and the sale generates a business of millions of $$ for the underground economy. The sophistication of these botnets used for phishing is that can be very stealth to IDS and difficult to tear down by IP because of fast flux techniques such as round robin DNS with a short TTL constantly changing the IP mapped to a domain. More information on fast flux and how is used in botnets such as ASPROX can be found here: Spear (targeted) phishing is also targeting banks by close branding to the original site using Rockphish as a botnet. So this is all bad. If you threat metrics did not show the threat coming to you already you should be seriously consider to adopt new countermeasures proactively. It means first of all raise the bar and reduce your attack surface. For example, consider more security for the users of your web site, require them to use browsers with anti-phishing plug-ins enabled with extended validation certificate support. A sandboxed browser such as the ones provided by Trustee and SafeCentral could mitigate malware and keylogger and provide some useful forensics information you can use when your customers become victim of botnet attacks. On the application site, strong authentication is required to mitigate MiTM attacks, for example using one time passwords and tokens that are delivered completely out of band such as via SMS and other channels. As a bare minimum you need to mitigate all common web application vulnerabilities such as OWASP T10. In particular you need to focus on web application vulnerabilities that can be exploited for phishing that deliver attack vectors for malware and spyware by injecting code in the browser by exploiting input validation flaws, typically XSS (stored and reflected) and XFS. Session management flaws such as CSRF (or session riding) can also be used for phishing. Sometimes your application might have design flaws are the most easy exploitable with targeted attacks. Such attacks might rely on attack tools can be tuned to exploit information disclosure, authorization and authentication control flaws. For example an attacker can try to harvest both web site credentials and bank account and credit card information to use to commit fraud via different channels. When you become a victim of botnet attacks, your capability to profile the attacks and alert on the intrusions is very critical for mitigation at the application level. An IDS that is build into the web application such as OWASP ESAPI or in the web server such as a WAF (Web Application Firewall) can log and monitor suspicious activity and trigger alerts for potential fraud attempts. Using honeypots to learn and simulate botnet attacks to your site can be very useful to learn how to build in defenses. Threat analysis is also important: attack tree can be used to identify possible attack scenarios, the channels used and the vulnerabilities that can be exploited. Take the attack tree as reference to derive the right countermeasures for the most likely attack scenarios such as the ones that the frauster might use because of the path of minimum resistance and effort. For example, consider that credit card and account data can be purchased from cyber criminal organizations selling their serviceson line. If such attack is cheaper than to break authentication probably that's the one that a frauster will use. If your site has easily exploitable information disclosure vulnerabilities probably will attack your site instead. Most importantly, never assume the adoption of a anti phishing security technology will solve your problem. You need to consider mitigations wisely. Consider that when you rely on the law enforcement to drive countermeasures is a little too late and this can be very painful in terms of financial losses. Before you become a victim, do a thoughtful review of potential threat scenarios for all your service delivery channels for example both web, ATM, IVR and other channels you might have. You need to consider these channels as your attack surface. Remember that you are NOT on top of the threat if you DO NOT own your attack surface and the attack scenarios: you NEED to simulate potential botnet based/phishing attack scenarios and validate the effectiveness of your countermeasures. |
| Google treats Yahoo like the girl you met at 3am [StillSecure, After All These Years] Posted: 05 Nov 2008 09:49 PM CST When I was in college some of the "cool dudes" used to have a contest. If you did not meet anyone at a bar or club by the time it got late, say 2 or 3am, you had the ugly girl contest. The thinking was you were not going to meet anyone great at that late hour, so you might as well go for something that you could laugh about tomorrow. Of course you would never call that girl again after that night. She was a 3am'er. Me, I was lucky to meet anyone I could, so wasn't cool enough to play that game, but heard about it plenty. Hearing the story about how Google pulled out of the joint advertising deal with Yahoo reminds of that story. When Microsoft was trying its best to pick up Yahoo, Google treated Yahoo like she was the prettiest girl on the block. They were willing to do just about anything to keep Yahoo out of Microsoft's hands. Jerry Yang and the team was only too happy to point to its Google deal as a poison pill that Microsoft would not swallow. Of course the Microsoft-Yahoo deal never happened and the Google partnership was a big reason why. Now that the Microsoft-Yahoo deal is off the table, Google dropped the Yahoo partnership as soon as the water got a little rough. I think Google was only too happy not to go through with the deal. Yahoo is after all a competitor still. They dropped Yahoo like the girl they met at 3am the night before. In the cold, light of day they could laugh about it, but they would be damned before they continued hanging out with them. Google got what they wanted by keeping Yahoo out of Microsoft's hands. When they were done they threw away Yahoo like a cheap date. Shame on Yahoo for being used and abused like that. I could understand why a Yahoo shareholder would be upset with this. Related articles by Zemanta |
| Episode 14 Recording Tonight! [SecuraBit] Posted: 05 Nov 2008 06:05 PM CST |
| Managed Resnet & NAC [CTO Chronicles] Posted: 05 Nov 2008 06:01 PM CST I've written about the link between NAC and MSP before, and the success of NAC in the higher education market is certainly no secret. More and more of our higher ed customers have been talking lately about outsourcing their residential networks. This seems to make sense on a number of levels, provided that the schools can work out a structure for the support as well as engineering and maintenance of the residential network. Certainly, it makes sense to have NAC as an integral part of the managed resnet service, but it also has the potential to go much farther than that, including services like voice and on-demand video in addition to data. A company based here in Austin, Apogee has managed residential services as their primary business function and seems to be making a go of it (except for the domain name, seriously..). Despite the macro economic conditions (and perhaps because of them), I think this has real growth potential. Having what amounts to a specialized MSP provided authenticated, well-governed network access to residential halls, freeing on-campus network staff to focus more on backbone services, and providing school administrators with a predictable cost structure that can be baked into the cost of the dorm room seems to make sense for everyone. Just don't forget the "authenticated, well-governed" part. |
| Xorg.conf for OpenBSD MacBook / Parallels [HiR Information Report] Posted: 05 Nov 2008 03:07 PM CST  On a lot of hardware, X.org just works. OpenBSD is no exception. At certain resolutions and in particular on notebooks, X.org is not happy and getting it configured properly when that happens is usually a time-draining adventure. On a lot of hardware, X.org just works. OpenBSD is no exception. At certain resolutions and in particular on notebooks, X.org is not happy and getting it configured properly when that happens is usually a time-draining adventure.This configuration file (xorg.conf) works great on OpenBSD 4.4 under Parallels Desktop on a MacBook and gives you full 1280x800 resolution at 24bpp color. It should also work for FreeBSD under Parallels as well, but I haven't taken it for a spin yet. So far, I'm really digging OpenBSD 4.4. It might not be as easy to configure as Ubuntu or its Linux brethren, but it's rock-solid and I still prefer the BSD port and package systems to RPM or Debian-style package management. |
| Tips for starting a security career [Network Security Blog] Posted: 05 Nov 2008 02:54 PM CST I know I’m not the only security professional who get’s the question “How do I get started in Information Security?” It’s not a simple question to answer; you don’t simply go get a degree in security then get a job. Every one I know has taken their own, unique path to get into information security and the number of folks who are like me and actually have a degree in IT are few. And even I’d been working in IT for several years before I decided to take my career to the next step and pursue my Bachelor Degree. Security Catalyst Kees Leune regularly teaches aspiring security professionals and probably hears this question more than the most of us do. And being a blogger he’s written a short guide on steps you can take towards becoming a security professional. I have to warn you, there’s a good chance you’ve heard many of the suggestions before. But that’s because he’s listing out what it really takes to become a security pro; there is no silver bullet, no degree or certification that makes you a security professional. It’s a career path, not a destination. You have to be prepared to spend a lifetime learning and have a passion for security if you’re going to be successful. Being cynical and paranoid helps too, but those are skills that can be acquired. His final point, Plan, can’t be overstated. Know why you want to be in security and what you want to be doing in 5 or 10 years then trace back the steps that it’ll take to get there. The path you take probably won’t resemble your plan in any but the vaguest outline, but the only way to reach your goal is to have one in the first place. Saying to yourself “I want to be a security professional” is a good start though. |
| Its the generational thing, stupid [StillSecure, After All These Years] Posted: 05 Nov 2008 12:08 PM CST  Image via Wikipedia Just one more post today on the tumultuous events of yesterdays election. Too many of us, including me have focused on Obama's race being such a defining aspect of this achievement. However, the more I think about it, I realize it is not the color of Barak Obama's skin. It is his age and the true "passing of the torch to a new generation". Obama is just a few months from my own age. For the first time we have a contemporary of mine running the country. Someone who grew up at the end of the crazy 60's. Lived through the ups and downs of the 70's. The drugs, the disco, the ugly hair and clothes. He probably watched Happy Days and Mork and Mindy. Our next President is someone who went to school during the 80's. Saw first hand what the Regan revolution did and didn't do for our country. Has watched us fall behind in many ways that we would have never expected in this country. That is what is exciting about this new President. Looking at the world's new problems through a new generation. A new age President for a new age world. I don't remember when Kennedy was elected, but this is more similar to that I bet than anything else. I am excited about our generation stepping up and taking our place in history. Recalling a poster I had in my room as a little boy, I think we can make the world safe for children, plants and other living things. |
| And the winner is . . . [StillSecure, After All These Years] Posted: 05 Nov 2008 10:10 AM CST
|
| Check It Out! FAIR Public Training December 10-12 [RiskAnalys.is] Posted: 05 Nov 2008 09:32 AM CST There’s been quite a few people talking about what sorts of strategies make sense for security and security departments in a downturn. And they’re all very good - but there’s one thing that I’d like to add. One easy, inexpensive way to actually increase your effectiveness in 2009 is to, right now, make a quick review your risk management processes. As you take a look at how you’re using risk in your organization, I’d ask you to make sure that those processes are providing value for the energy you’re spending. If they’re not - if you’re not successfully using risk within security and with the other lines of business that you serve - then I’d like to invite you to come take advantage of RMI’s public training session for 2008, held in Columbus, Ohio on December 10-12. >A brochure is here<. For three days and $1,995 - you’ll get real answers to many of the commonly voiced frustrations RMI hears concerning risk & risk management. Answers around measurement, application, communicating risk to other lines of business, heck, basic answers as to what risk is and how to get consistent, defensible values that actually mean something. Not to mention - Strengthening your Risk Management processes increases your ability to manage risk, which reduces the amount of risk you actually face. NEW TO THE PUBLIC STUFF! I’m personally excited because this is the first time that our public training will feature measurement “calibration” exercises and include excel tools to take home and use for quantitative FAIR analysis. These are benefits we’ve only previously reserved for private client workshops. I know that FAIR can help you and your organization, but as the sales guys always say, “don’t take my word for it”. Here’s something we recently received (unsolicited) from the CSO of one of the 10 largest banks in the US, who has had several of his analysts receive this same basic training:
More information can be found on RMI’s website here: http://www.riskmanagementinsight.com/12_2008_training.html Thanks. Oh and tomorrow, we’ll talk a little bit about quantitative and qualitative risk. |
| Posted: 05 Nov 2008 07:52 AM CST In just a few short years the move from dial up to broadband in our homes is complete. Do any of you know anyone who still uses dial up for Internet access anymore? The US is actually behind much of the rest of the world in broadband access as well. Many other countries have cheaper, faster access than we do. All of this fast access has also transformed what we access. Can you imagine what YouTube would be like on dial up? Could NetFlix deliver video via the web? Could any video, graphic or other big file in the cloud type of application work without broadband? All of these great applications are built on a platform of ubiquitous and cheap bandwidth. Much like our whole economy was built on cheap, ubiquitous energy. The broadband revolution was built on getting the fattest pipe possible into the house. The idea was with a fat pipe, the applications to fill those pipes would follow, and follow they did. Now the ISPs are rethinking this position. ATT is the latest to join the group who want to charge based upon how much you download and upload to your computers. So now paying for a fat pipe is not enough. If you are going to use that fat pipe you are going to pay for how much you put in there. Some say that this is only fair. If you use more than the next person you should pay for that extra use. I say no. I think this is a change in the rules tin mid-stream. We have an ecosystem built upon one model of broadband and now we are being slipped another. What effect will this have on YouTube, NetFlix, cloud computing, etc.? I don't know, but this could be the fly in the ointment of our broadband future. Related articles by Zemanta |
| [Insert Memorable Election Buzzword Here] [BumpInTheWire.com] Posted: 04 Nov 2008 11:09 PM CST The shoe is on the other foot now. Put aside the political aspect of tonight’s events just for a moment. Just long enough to acknowledge the significance of what happened today across this nation. It is nothing short of remarkable. I have not been more proud to be an American since the way the nation came together after 9/11. If you are unable to put aside the political aspect long enough to recognize the significance of what happened today…well, that’s just unfortunate. Many years from now when my daughter tells me something is impossible I will point her to November 4th, 2008. Anything is possible. |
| Barack Obama, the 44th President of the United States. [Vincent Arnold] Posted: 04 Nov 2008 10:52 PM CST |
| TSA strikes again [Andy, ITGuy] Posted: 04 Nov 2008 03:50 PM CST I left Atlanta this morning to fly to Chicago for ISD. Last night as I was packing my bag and going through my laptop backpack to ensure that I didn't have any "contraband" that would raise the ire of a TSA agent. I had a Leatherman that I took out. Removed a USB drive that had a pen knife in it. Made sure not to pack my Cross Fountain Pen because there is no way in the world that I would throw it away if they told me I couldn't take it on the plane. I was careful to pack on liquids that were less than 3 ounces and packed them all in one 1 quart clear plastic bag. As I went through security at the Atlanta airport all went well as my bags passed through the x-ray scanner and I walked through the metal detector. I grabbed my bag and other stuff and put it all back where it belongs and went on my merry way to the gate. The flight went well and I arrived in Chicago on time. As I was riding the train from the airport to the hotel all of a sudden I remembered that I had another knife in my laptop bag that I didn't remember taking out. It's a Buck 3" straight blade boot knife (don't ask why I carry it). I opened up the compartment that I keep it in and sure enough there it was. How the TSA missed it I'm not really sure. Now I'm faced with the delima of what to do with it. Do I take the chance that I can get it on the flight back to Atlanta? If they catch it what happens then? Do they just give me the option to give it up and go on my merry way or do the strip search me and put my name on the no fly list? Not real sure I'm willing to take that chance. Maybe I'll mail it to myself before I leave here. |
| Speech of the Politecnico di Milano rector for the opening of the 146th year [Security Circus] Posted: 04 Nov 2008 03:00 PM CST |
| "I once was talking with a small business owner who was reading through the Se..." [Security Circus] Posted: 04 Nov 2008 02:54 PM CST I once was talking with a small business owner who was reading through the Self-Assessment Questionnaire (SAQ) and stopped at the first question, which basically said, Do you have a properly configured firewall? The business owner called into the back room and asked the store manager, "Hey, do we have a firewall?" The store manager replied that he thought they had a fire extinguisher which was up to date. I then watched as the store manger checked the "In Place" box on the form stating they had a properly configured firewall in place. –PCI Blog - Compliance Demystified |
| Optical scan machines, not just DREs, giving voters troubles today [Security Provoked] Posted: 04 Nov 2008 02:26 PM CST If voters do not even have confidence in the voting machines recommended by the Verified Voting Foundation, what hope have we in any voting system in use today? Luckily none of the technical problems thusfar experienced by voters have been called “systemic,” but rather are isolated incidents. Nonetheless, it was no doubt frustrating and perhaps shocking to some citizens, when after waiting in line for hours at their local polling places, they were told that the optical scan voting machines were malfunctioning; voters were given the option of waiting for the machines to be repaired or filling out the paper ballot and relying on poll workers to scan the paper ballot when the scanning machines were once again fully functional. Optical scanning machines are preferred by the non-profit organization, Verified Voting, because they automatically provide a paper trail, unlike most direct recording electronic machines (DREs, which are most often thought of in discussions about e-voting.) Optical scan machines basically work like those ScanTron machines you might have used when taking tests back in high school. You’re given a paper ballot, you fill in some boxes or circles with your choices. You then personally insert the paper ballot into the machine, which scans your answers, adds them to the tally, and then drops the paper into a secured box. So in the event of a recount (or in the event that the polling station was randomly selected for a mandatory audit), the machine’s tally could be compared against a manual count of the paper ballots filled out and confirmed by each voter themself. Yet some troubles have been reported with these optical scan machines today, including quite a low-tech problem–after heavy rain yesterday, the paper ballots at one Virginia polling station were damp, and were getting stuck in the scanning machine. This morning Tom Brokaw, current moderator of “Meet the Press” and the moderator of one of the presidential debates, said that regardless of who wins, the nation needs to fix the problems with the voting system. It would be difficult to make a convincing counter-argument. Some of the swing states being given the most attention by analysts and candidates today are Ohio, Florida, Colorado and Virginia. Florida has the most rigorous policy, requiring both a voter-verified paper trail and a manual audit of randomly selected polling places–some of these paper ballots, however are still the infamous “butterfly” ballots that had the country hanging in an uncomfortable suspense during the 2000 election. Colorado also requires a VVPR and manual audits, but according to Verified Voting, Colorado is “shown as having a VVPR requirement because they have enacted VVPR legislation, but these states’ requirements will not be fully implemented until after 2008.” Ohio has a VVPR requirement, but no audit requirement, and Virginia requires neither the paper trail nor the audit. See the requirements for other states here. |
| Preflighting Application Error (0xE800000*) on iPhones [extern blog SensePost;] Posted: 04 Nov 2008 02:20 PM CST For those writing apps for the iPhone, you have a good chance of bumping into the highly annoying preflighting application error: Ralf Rottmann of [24100.net] has a [pretty comprehensive post on how to fix this] (the problem resides in xcode not corerctly tagging the applications BundleID) |
| HITB08 Slides available.. [extern blog SensePost;] Posted: 04 Nov 2008 02:09 PM CST Slides from the latest Hack in the Box conference [are available] [SensePost slides are listed as owing / not there yet] SensePosters can grab a local copy [here] |
| Posted: 04 Nov 2008 10:49 AM CST |
| "Employ simplicity as a tool used to keep your systems running securely and ef..." [Security Circus] Posted: 04 Nov 2008 10:39 AM CST Employ simplicity as a tool used to keep your systems running securely and efficiently. Simplicity helps eliminate network clutter, performance issues, cost, and reduces risk. Give yourself the space to step back, analyze and test carefully to ensure all your systems and networks meet a secure standard. Streamlining processes greatly enhances uptime and quality of service, as well as aiding in secure systems. –holisticinfosec.org - Simplicity |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |

![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=88266454-1530-49eb-bef6-397bd7ee9490)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=5ef9d848-11d2-4a19-95dc-af027c813fcb)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=6cdc1457-ca4c-4d5d-9f91-74e0bf12eccb)

1 comment:
Its a very great post thanks for sharing us.
Good night Sms
Post a Comment