Spliced feed for Security Bloggers Network |
| Gmail as a spam engine [Network Security Blog] Posted: 10 May 2008 10:56 PM CDT This is not good. Researchers from INSERT found a vulnerability in the Gmail engine that could allow spammers to forward mail through Google, thereby bypassing blacklists and being accepted by whitelists. It works by using the same forwarding features that allow users, myself included, to forward their email through Gmail. The worst part of this is that it also bypasses Gmails 500 recipient limit for any email, though that part should be easy to fix. I hope. INSERT has been courteous enough to omit a fair amount of the details of the vulnerability, but I think there’s enough general information in the notification that spammers will be able to figure it out soon if Google doesn’t act even faster than the bad guys. Given Google’s track record and the sneaking suspicion that Google was given advance warning of the vulnerability, I’m hoping Gmail can be made secure fairly quickly. I’ll be interested to see what we hear on this over the next couple of weeks on the Full Disclosure/No Disclosure argument. Did INSERT give Google some warning or did they post this as soon as it was written up? How did Google react? Did Google take the Micorosoft stance of quietly taking the research and fixing the hole before anyone notices? Or did they take the Apple/Cisco approach and threaten to sue INSERT into non-existance? I’m hoping for the former. Just goes to show you, even the best built, least offensive features in software can be subverted if you put enough brain power into solving the problem. | ||
| Swingtown - This ain't your mother's CBS [StillSecure, After All These Years] Posted: 10 May 2008 10:52 PM CDT I was reading a review in the NY Times today about a new summer time show coming to CBS. It is called Swingtown and I was originally attracted to it because it is a look back at the mid 70's. That was the age of my adolescence, so it naturally attracted me. Well this show is about the mid-70's OK, but the wilder side. It is set in a suburb of Chicago and is about wife swapping, partying and other hedonistic activity that is supposed to sum up the era. And on CBS yet! That's right, the folks who give us 60 Minutes, Murder She Wrote and Touched by an Angel, now bring us the swingers of the 70's. I grew up in a suburb in the 70's and while I do remember our parents hanging out drinking Harvey Wallbangers and some of them getting divorced, I don't think they were the type to pass around Quaaludes and engage in orgies, like depicted in this show. But hey, maybe I am just naive. This certainly sounds more like an HBO series to me, but I have to admit I will watch and see it what it is about. Just the 70's clothes and hairstyles should be entertaining for me. I am You Tubing the official trailer:
If you like this trailer, here is a link to a longer video showing more highlights. Let me warn you that this one is a bit racy! | ||
| Maltego v2 is out and its friggin awesome [Carnal0wnage Blog] Posted: 10 May 2008 10:50 PM CDT I did a previous blog post using Maltego v1 and will be talking a bit about maltego at ChicagoCon but Maltego v2 is out and its a very nice upgrade. from the site: Version 2 of Maltego has been completely rewritten - it's a complete new code base.
I'm trying to tidy up slides for next week but expect a maltego post or article after chicagocon.  | ||
| TJX Breach Write-Up [Carnal0wnage Blog] Posted: 10 May 2008 10:37 PM CDT Interesting write up on the beginning of the TJX breach: http://blog.tizor.com/data_auditing_blog/tabid/8146/bid/4793/default.aspx of course they didnt answer the big question of how the attackers gained access to the RTS Servers "(2) After breaching the TJX wireless system, the attacker was able to gain administrative privileges to the RTS servers located at the TJX corporate headquarters in Framingham, MA. The RTS servers hold all cardholder data that is processed centrally for most TJX stores." because cracking a WEP key gets you on the network but doesnt give you the ability to log into anywhere on the network. | ||
| Call me crazy? [Emergent Chaos] Posted: 10 May 2008 02:01 PM CDT There's an article in the New York Times, "‘Mad Pride’ Fights a Stigma" “It used to be you were labeled with your diagnosis and that was it; you were marginalized,” said Molly Sprengelmeyer, an organizer for the Asheville Radical Mental Health Collective, a mad pride group in North Carolina. “If people found out, it was a death sentence, professionally and socially.”Call me crazy, but I think these folks might be onto something. Learning about coping strategies from one another? Testing what works and what doesn't, and reporting on it? Maybe "we were broken into" isn't the most embarrassing thing you can say in public. | ||
| Links for 2008-05-09 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 10 May 2008 12:00 AM CDT | ||
| (ISC)2 exams [Security Balance] Posted: 09 May 2008 11:24 PM CDT This week I’m participating on a (ISC)2 Workshop for item writing and review for the ISSAP certification. This opportunity brought to me a very good view on how the exams are created and managed. Honestly, what I have seen until now completely changed the way that I see these certifications. The process is thorough and the questions pass through a review by several very good professionals. I know that passing a test, even one with good questions, is not a proof of professional competency, but it’s a good way to assess the basic knowledge of a candidate. Congratulations to (ISC)2! | ||
| Now, Somebody Please Tell Me This is A Spoof ... [Anton Chuvakin Blog - "Security Warrior"] Posted: 09 May 2008 07:23 PM CDT ... NOW!!! "Hackers recently bombarded the Epilepsy Foundation's Web site with hundreds of pictures and links to pages with rapidly flashing images. The breach triggered severe migraines and near-seizure reactions in some site visitors who viewed the images. People with photosensitive epilepsy can get seizures when they're exposed to flickering images, a response also caused by some video games and cartoons." | ||
| Expect the Blog to be a Little Quiet [.:Computer Defense:.] Posted: 09 May 2008 07:00 PM CDT Hey All, Time for a personal post... The next two weeks I probably won't be blogging much (or necessarily even acknowledging the blog exists).... then again maybe I will. Either way, I'm getting married on May 17th (back home in Sault Ste. Marie). Shortly after the wedding we'll be going on a brief honeymoon to Chicago and then it's back here to Toronto. Anyways... Just wanted to share. | ||
| ChicagoCon "Con" portion 16 & 17 May 2008 [Carnal0wnage Blog] Posted: 09 May 2008 06:34 PM CDT  I'll be speaking at The "Con"portion of ChicagoCon on "New School Information Gathering". http://www.chicagocon.com/content/view/38/46/ if you are in the chicago area its only 100 bucks for a ticket and EthicalHacker.net Don always has tons of stuff to give away, so it gonna be worth the money. The link has the schedule but of interest is the two keynotes. One by the Tiger Team guys on The Art of Espionage (Tactics, Defense, and your Corporation) TruTV's Luke McOmie, CISSP, NSA-IAM, NSA-IEM & and one from Intelguardian Matt Carpenter (@tlas) Windows Command-Line NinjitsuMatthew Carpenter, SANS, Intelguardians all the other talks look good to me as well, so it should be a good time. see you there! | ||
| Fun Reading on Security - 2 [Anton Chuvakin Blog - "Security Warrior"] Posted: 09 May 2008 02:20 PM CDT Instead of my usual "blogging frenzy" machine gun blast of short posts, I will just combine them into my new blog series "Fun Reading on Security." Here is an issue #2, dated May 8, 2008. So my next iteration of fun reading on security, logging and other topics.
On that happy note - see you next time! :-) | ||
| Credit Bureaus and Outsourcing [Emergent Chaos] Posted: 09 May 2008 11:03 AM CDT The "I've Been Mugged" blog has a great three part series on outsourcing by credit bureaus: "Is It Wise For Credit Bureaus To Outsource To Foreign Call Center Firms? (Part 1)," "part 2" and "part 3." He digs deep into how extensively TransUnion outsources, and where. I went looking, and was surprised to see that their privacy policy is at least honest. They make no claim that they care about your privacy, nor any that they apply the highest standards of security to your information. | ||
| 802.1X-REV: Ya' Heard it Here First! [Security Uncorked] Posted: 09 May 2008 09:59 AM CDT Well, you’re not necessarily hearing it hear first, but it’s likely… unless you read IEEEdocs religiously (as I do) or read Paul Congdon’s standards updates at the ProCurve Networking site. If you have no clue what 802.1X is, read my recent technology primer first. If you’re already familiar with 1X, you’ve probably heard about some of the 802.1X additions- the 802.1AE (MACSec) and possibly 802.1af (the key agreement for MACSec)… but that’s just the tip of the iceberg, and what’s hiding underneath will knock your socks off! We’re currently at the 802.1X-2004 edition, with the group working on the REV and hoping for an early-2009 release. When IEEE makes additions (such as AE and af) they’re just afterthoughts and changes tacked on to the end of the standard. But when they do a revision , as they are now, they’re opening up the whole can of worms and all parts of the standard are opened for evaluation and modification. Yee-haw! So, what’s in this new revision and what can we expect from 802.1X-REV? That’s what I wanted to know, and I’m sure you’re curious too. I was lucky enough to catch a quick call with Paul Condon earlier this week and get some of the inside scoop. Paul is ProCurve Networking’s CTO, but more importantly for our purposes today, he’s the Vice -Chair of the IEEE 802.1 working group and is intimately involved in 1X and a variety of other networking, security and authentication standards. 1) Encryption & Key Exchange : The first goal in updating 802.1X was to add security with encryption, specifically on switch-to-switch links. Of course, with encryption comes the need for fast, secure key exchange, so we ended up with 802.1AE and 802.1af as answers to the first set of goals. The encryption will require hardware refreshes, and vendors are already gearing up for that. The benefits of encryption are pretty obvious, so I won’t bore you with that. There are some fun little gems hidden in the AE/af set though. Even without using the encryption piece, we’ll be able to use the key exchange as a means of quickly (in ~4-5 packets) authenticating (or re-authenticating) switches to one another after a reboot. It will be a critical piece for maintaining availability and integrity in the network. And w e can do this piece without a hardware upgrade, which is pretty nifty. 2) Same-Port Multiuser Support: Here’s where the 1X-REV sauce starts tasting really good. The new revision is leveraging some of its security updates to support multi-user modes on a single port. And no, not by using multi-tagged VLANs, this is way cooler than that. In theory, multiple PCs, phones or other connected devices can connect through a single port, which would essentially be running multiple instances of 802.1X, letting each communicate securely. It’ll be similar in practice to how wireless APs segregate and encrypt traffic between the AP and the endpoint. I’m sure at first we’ll see software-based endpoint encryption support and of course, move towards hardware encryption and see NICs with the capability baked in. That’s still down the road, but the road is getting shorter. 3) Network Advertisement/Selection : Now the 1X-REV sauce is the best you’ve ever had- you’re gonna want to put this stuff on everything ! :) The 3rd goal of the revision is to add support for network advertisements on the wired side- which would be a similar experience to selecting the wireless SSID from a list of ones available on your laptop. But, it’s happening on your wired switch. Wild, right? They’re going to leverage the EAPOL types here to communicate from client to network. Imagine the possibilities… All these new functions and features give 802.1X numerous new use cases. I think you’ll see parts of these technologies leveraged in various parts of critical networks everywhere. Sponsor ballots come at the end of the year, and they’re hoping to see something solid and released in early 2009. You can see why I’m excited. The 802.1X-REV may be the evil stepchild for a while, but it’s coming. When it does, it’s going to rock our little network worlds and flip our thinking about wired security and network segregation upside down. Of course, you’ll be seeing more on this from me, so hang in there! # # # | ||
| Norton on my Tivo [Network Security Blog] Posted: 09 May 2008 08:01 AM CDT I love my DirecTivo, my DirecTV receiver with the Tivo built in. Without it I couldn’t find the time to watch half the television shows I do, and I’d have to actually, you know, *watch* the commercials. The DirecTivo is about four years old and I’m dreading the day something in the box dies, which I know can’t be too far off. One of the features of the DirecTivo is a little advertisement that’s part of the main screen, usually a 3-5 minute infomercial. I often ignore it, but last night something caught my eye; the headline for the advertisement read “Crucial Wifi Security tips”. This was definitely something I had to take a few moments to check out, otherwise what kind of security professional would I be. It turns out that its an advertisement for Symantec Norton 2008, but I have to give the guys at Symantec some credit, it’s also a pretty good primer on the dangers of using wireless hotspots. The video quality isn’t the highest quality, but that may be intentional (or it may be a factor of budget). It starts off by giving some general advice about security, or lack there of, at hotspots and explains in simple terms that the average user might not want to do any sensitive activities while using these hotspots. I was impressed that Symantec decided to only explain two terms in the video and explained them in simple yet accurate language. The first term was ‘packet sniffing’ and the video explained in a few seconds how another curious patron or maybe a hacker could be sitting in the booth next to you capturing your passwords as they fly through the air. I immediately thought of Robert Graham and the grief he sometimes gives David Maynor concerning wireless. The second term was ‘wi-phishing’. I’d never heard the term before, but I guess its easier to remember than man-in-the-middle or evil twin hotspot. The video explained that malicious attackers could set up hotspts that looked just like real hotspots but were just created to capture passwords and other account information or infect systems with malware. From that point on the video was an explanation of how Symantec Norton could protect users from these dangers as well as a host of others, but I’d heard most of this marketing before at RSA. The video was only three minutes long and did a good job of explaining a few of the dangers of public wifi in the first two minutes. I’m actually pretty impressed with the content of the video and if I could get just the first part to use for educational purposes, I’d take it. This video would make a good starting point for a brown bag lunch or other short format awareness campaign at work. There are a couple more videos from Symantec waiting to be watched on the DirecTivo, which I might get to this weekend to see what they offer. Or maybe not; my tolerance for commercials has been greatly reduced over the last four years. | ||
| Links for 2008-05-08 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 09 May 2008 12:00 AM CDT | ||
| OMG, This is Sooo "Kid in A Candy Store" :-) [Anton Chuvakin Blog - "Security Warrior"] Posted: 08 May 2008 04:22 PM CDT "First USENIX Workshop on the Analysis of System Logs (WASL '08) December 7, 2008 San Diego, CA, USA" CFP here. | ||
| QSA Employee Lookup [PCI Blog - Compliance Demystified] Posted: 08 May 2008 03:56 PM CDT Are you working with a Qualified Security Assessor (QSA) and want to make sure they are legitimate? The PCI SSC just launched “a tool to verify the certification status of representatives from PCI SSC Qualified Security Assessor (QSAs) Companies.” Lookup your QSA’s employees to verify they are properly qualified. | ||
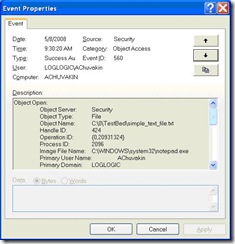
| Posted: 08 May 2008 03:37 PM CDT Following the new "tradition" of posting a security tip of the week (mentioned here, here ; SANS jumped in as well), I decided to follow along and join the initiative. One of the bloggers called it "pay it forward" to the community. So, Anton Security Tip of the Day #15: Fear and Loathing in Event 567 This tip digs into a seemingly simple, but really VERY esoteric subject: monitoring file access and modification via a Windows event log. Now, some people - who never studied this subject - tend to have a very simplistic view of this: just enable Object Access auditing, then right-click on a file or directory, click Security->Advanced->Auditing and then pick what types of events will be logged and by what accessing entities (i.e. users or computers). OK, so this will produce some logs, that is for sure. But are they useful? First, why are we doing this? We typically need to know the following when we audit file access in Windows (or any other OS for that matter) for security (monitoring and investigation) or compliance:
Can we get this from the above logs? No. What? No!?! Really? Yes, really. We can get some of the above, some of the time, not all of the above, all of the time. Here is an example, we are looking at event ID 560 (picture) and then at an extract from its description field. Event: Description (selected field): Object Server: Security Object Type: File Object Name: C:\0\TestBed\simple_text_file.txt Image File Name: C:\WINDOWS\system32\notepad.exe Primary User Name: Anton Primary Domain: XXXXXX Accesses: READ_CONTROL SYNCHRONIZE ReadData (or ListDirectory) WriteData (or AddFile) AppendData (or AddSubdirectory or CreatePipeInstance) ReadEA WriteEA ReadAttributes WriteAttributes
WTH is that? Well, we know that the user 'Anton' has successfully read? wrote? changed attributes? did something? with a file named "C:\0\TestBed\simple_text_file.txt" using a program named "C:\WINDOWS\system32\notepad.exe." That's the best we can get, in this case! We may try to look at event IDs 562 and 567, but this missing information (i.e. the exact action performed) will not be added. BTW, there will be a few more dozen (sometime hundreds!) of the 560s, 562s and 567s produced - all from just opening the text file in a notepad. The above event is notable for having BOTH "notepad" and "simple_text_file.txt" in the same event; others will have either of the two. Anything else gets in the way? Yes, lots! MS Office will write to all files, even just opened for reading (with no user modifications to the content whatsoever), which will screw up your log monitoring efforts. If the file is on a share, more information will be missing (e.g. username might be). So, how to use Windows event logs for file access tracking?
Overall, this is still very useful for file access monitoring, but the process is paaaaaainful. BTW, I am tagging all the tips on my del.icio.us feed. Here is the link: All Security Tips of the Day.
| ||
| All I can say is ‘Wow’ [.:Computer Defense:.] Posted: 08 May 2008 02:57 PM CDT I read this today on a local news site and the only thought that went through my head was "wow"... Essentially a malicious individual hacked the Epilepsy Foundation's website and posted hundreds of rapidly flashing images. While I don't condone it... I can understand why people think they should target websites for profit or pride... but this? It's just plain mean... It makes me wonder what the world is coming to. Update: Apparently this is old news and I'm a little slow finding out about it. | ||
| Another Old Presentation: Log Baselining [Anton Chuvakin Blog - "Security Warrior"] Posted: 08 May 2008 02:12 PM CDT As I did in the past, I am releasing another one of my old presentations. This one is about baselining logs and was given at SANS a few years ago as SANS @ Night. It mostly a subset of my "Log Mining" preso, but with some things added and clarified. Keep in mind, this is circa 2006 or so :-) I dug out a few more fun ones, that go as far back as 2002. I will release them here in a few days. | ||
| Need Proof That I am Popular in UK! :-) [Anton Chuvakin Blog - "Security Warrior"] Posted: 08 May 2008 02:05 PM CDT | ||
| Why [Some] Smart People Hate Logs? [Anton Chuvakin Blog - "Security Warrior"] Posted: 08 May 2008 01:20 PM CDT WARNING! "Ph." in "Ph.D." at work (play?) here :-) This is one of them darn philosophical posts... Now, some people hate logging, because logs are too hard to deal with (enable, collect, store and especially understand and interpret). However, there is a whole other group of fairly intelligent people who "hate logs:" the organizers of some well-known technical security conferences. The experience of many of my colleagues (and competitors!) and myself proves that a log-related talk will NOT be accepted to ANY technical security conference nowadays. Now, some were generous enough to explain why. Others were not (screw them and no link :-)). But let me rant about this one a bit. First, it is always a possibility that they dislike me not logs:-) - this is easily disproved, however, since some of my colleagues had the same exact experience. Do they dislike vendors talking about logs? Nah, this isn't it either - most of my conference presentations had nothing to do with LogLogic, even though they are about logs. Some of my friends (and this blog readers) tried to suggest that an audience of such events "knows everything there is to know about logs." This is not true since - gasp!- nobody knows everything there is to know about logs: they hide way too many mysteries (with useful answers!) to discount them like that. Another one I've heard is that "real hackers don't get logged -> logs are useless", which is also silly: this is true only if you take a very narrow view of logs (e.g. NIDS alerts),; clearly, everybody is logged by the firewalls, servers, apps, etc. The challenge is not a lack of data, but too much data and not enough time and tools. But we are about to "hit paydirt" with this question... Tool? Did I just mention tools? This opens the last and final, deeply evil reason for such "log-hate": one of the conference organizers mentioned that, in his opinion, there is nothing new in the field of log analysis since regex-match-based alerting (and regex-based parsing into database tables). And you know what? Drum roll.... He was actually somewhat right. Indexing did come in the world of logging, but, personally, I don't find it to be a huge feat of human ingenuity (even though it is definitely useful). I also think we are not doing enough with index data (and I definitely intend to change that...) In addition, there was A LOT of academic research on the subject, from the SRI EMERALD in the 80s (and even earlier) to today, but many of the papers I've seen sit on the "hilarious side of useless"... So, I need a campaign "Making Logs Sexy Again!" (and some impressive research results to boot) - will it work? Let's try and find out! | ||
| Russian translation of PCI DSS and SAP [PCI Blog - Compliance Demystified] Posted: 08 May 2008 01:05 PM CDT Maxim Emm from Infosec in Russia has translated the PCI DSS, PCI Security Audit Procedures, and Navigating the PCI DSS into Russian. This is an unofficial copy of these documents but could be helpful to people who would like this resource. If none of these links work due to your browser not supporting Cyrillic characters, click the page link. All official copies of the PCI DSS and Security Audit Procedures (SAP) are accessible from the PCI SSC website where they are offered in multiple languages. | ||
| The Daily Incite - May 8, 2008 [Security Incite Rants] Posted: 08 May 2008 10:13 AM CDT  May 8, 2008 - Volume 3, #44 Good Morning:
Top Security News NAC is dead! Long live NAC!
Top Blog Postings New boss is same as the old boss | ||
| Comments on Core Security’s Wonderware advisory [.:Computer Defense:.] Posted: 08 May 2008 09:04 AM CDT There were a couple of random things that I wanted to comment on. The first was a post by Dave Lewis of Liquidmatrix. The post in question is a discussion of a Wonderware advisory released by Core Security and the level of detail that they provided. Dave doesn't agree with the level of detail provided... as they had details on how to exploit the vulnerability and even showed the assembly from the vulnerable function. He also comments that this isn't responsible disclosure. I'm <sarcasm>really glad to see this debate is coming up again</sarcasm>... but really where's the lack of responsible disclosure? Core reported the vulnerability to the vendor (repeatedly) and went out of their way to ensure the vendor was aware, this is more than a lot of people / companies do. They then continually pushed their advisory release date to accommodate the company. These details are being released after the patch as well. There's absolutely nothing wrong with this... it's really no different from the level of detail provided by other security vendors that release advisories. Once the patch is out there isn't much to stop malicious individuals from obtaining the assembly to the vulnerable function... a copy of IDA Pro and BinDiff is really all they need. Outside of the assembly... the level of detail provided is really the same as most other security vendors that release advisories. I've seen them include some sort of binary analysis in the past... and most of them contain a text write-up... here's an example with enough text to more than locate the vulnerability from TippingPoint / ZDI: The specific flaw exists in the oninit.exe process that listens by default on TCP port 1526. During authentication, the process does not validate the length of the supplied user password. An attacker can provide a overly long password and overflow a stack based buffer resulting in arbitrary code execution. Part of the problem with the InfoSec battle is that the bad guys have essentially unlimited time, where as IS employees have families and lives and work a set schedule. The Core advisory has set internal security teams on their way to developing their own exploits should they need to, without it they'd have had a lot more work to do and it would have taken them more time. Core did everything short of release the related Python and you can't really blame them, since then they'd be giving away their product for free. In the end, what they did was, in my opinion, beneficial to all. It's one thing to simply release details, but as soon as someone works with the vendor you can't really cry foul when they publish the details. At least not on the 'responsible disclosure' front... because they've followed responsible disclosure and in this case Core Security hasn't done anything different then a number of vendors. Microsoft Tuesday is coming up and watch the mailing lists, each vendor that has reported a vuln usually sends out some sort of advisory and these range from brief overviews to full binary analysis and specific details on exploiting the vulnerability. We've seen it before and we'll see it again... but the patch is out, so they aren't helping the malicious individuals... just the good guys who have time constraints. |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |


 Basically for me, movies are about escaping. Not that my life is bad, quite the contrary, but every so often taking a few hours to go into the land of someone else's imagination is very useful for me. I do my best not to get into the dogma of reality vs. unreality. Plot lines that don't make sense just roll off my psyche, and I spend very little time trying to understand the "true" meaning of any of these movies.
Basically for me, movies are about escaping. Not that my life is bad, quite the contrary, but every so often taking a few hours to go into the land of someone else's imagination is very useful for me. I do my best not to get into the dogma of reality vs. unreality. Plot lines that don't make sense just roll off my psyche, and I spend very little time trying to understand the "true" meaning of any of these movies. 

No comments:
Post a Comment