Spliced feed for Security Bloggers Network |
| Why making health records public is not a great idea [StillSecure, After All These Years] Posted: 20 May 2008 07:21 AM CDT Fred Wilson has an interesting blog up regarding the new Google Health service. Fred filled out his personal medical information and was disappointed that he was not able to publish this data and make it public. Fred would like to have a sidebar widget for his blog with his health profile. Many people wrote to Fred telling him why Google does not do this. Many of them centered on the fact that insurance companies would use this information against you to deny or limit your coverage. Some took shots at Fred's socio-economic status saying that he didn't care if the insurance companies used it against him because he could afford to pay whatever he had to. Fred replies that he thinks withholding or being less than open about health issues to insurance companies, investors, etc. is problematic and in a perfect world insurance companies should not be able to use this against us. In fact Fred says:
I don't believe Fred feels this way because of his socio-economic status. I think Fred thinks like this because he is I assume in good health. I wonder if Fred were suffering from some medical condition, if his views on this would change. This reminds me of the "nothing to hide" argument that some use to justify the government trampling on our privacy rights. If you have nothing to hide, what do you care. I care because it is wrong. I care about not making health records public because it is wrong. We don't live in a perfect world. Even taking Hillary or Obama's health plans into account, we live in a world where insurance companies can discriminate against those with pre-existing conditions for the foreseeable future. Think about if only healthy people published their records, what would that say about people who did not publish their records? Fred's point about searching for others with the same condition is fine, if they wanted to be found. It is inherently a persons right not to be found. In fact today if you want to share with a person who shares a medical condition with you, you can search and usually find a group and on line community of people. What is nice is some of these people can share in these groups without revealing their identity. It is this ability to remain anonymous that I think make these types of communities successful. Fred recognizes that not everyone would want to share their records. I say once we start dividing society by those who do and don't we really already have imposed a penalty on those who cherish their privacy. |
| Posted: 20 May 2008 06:50 AM CDT I was at a meeting for a potentially large customer engagement for vulnerability assessment and compliance testing last week. The requirements for this customer were not unusual. They wanted to test for conventional CVE type vulnerabilities. Additionally, they also wanted to test for configuration compliance. Hotfixes, patch level, AV, etc. This direction is where a lot of the traditional vulnerability management solutions have been heading. Whether adding a separate compliance module or audit and local check capability, most of the traditional vulnerability scanning solutions offer some coverage in this area. However, in speaking to this potential customer and in thinking about their needs, an inherent problem with this solution is that it is only as good as the devices that are available on the network when the scan takes place. In traditional vulnerability scanning, when the scan takes place was not as much of an issue. Usually you are scanning servers and other devices that are on the network 24/7. In fact doing the scans during off hours was usually preferred. Too many of the network based vulnerability scanners took up too much bandwidth and other resources to accomplish during the prime time hours of the day. In compliance scanning though, you need the status of laptops, desktops and other devices that may not be connected to the network 24/7. Therefore it is important to reach and test these devices when they are on the network. That is the rub. How do you really make sure the devices connecting to your network are compliant if you are only testing them at a point in time that usually they would not be on at? This problem reminded me of the Clinton-Obama flap over who answers the phone at the White House at 3am. That is an important question for who is president, but for compliance, nswering the phone when someone is there to talk to is more important. I think this is where NAC provides an advantage. By utilizing NAC to detect devices coming on the network and than using a low impact NAC/compliance test as well as traditional vulnerability scanning, you get a picture of vulnerability posture and compliance status as of the last time they accessed the network. You can still do follow on tests at any time you desire, but at least when a device is logging on you are sure of a test. Will NAC supplement vulnerability testing in this manner? I think so. Many customers we have spoken to about this like the idea of "scan on connect" and we have already enabled our own NAC product Safe Access and vulnerability management platform VAM to do this. What do you think? |
| Tomorrow’s Malware [GNUCITIZEN Media Portfolio] Posted: 20 May 2008 05:37 AM CDT My favorite tech quote is from Giorgio Maone. It goes like this:  Part of my job at GNUCITIZEN is to spot trends. There is nothing magical in this line of work but I believe that some people are more suited for it then others. This is my opinion and it is based entirely on my experience and knowledge which has been accumulating for the past 7 years. A trend which I saw emerging several years ago has already started to shape up. I am talking about Web2.0. The Web is the single most important and most critical platform we have ever build. Some of you may argue that it is not the Web, it is the Internet in general. To an extend I agree but I find the Web mission critical for most people. While it may be OK to turn off certain Internet protocols, HTTP is often let go free. It just makes the business sense. This is the reasoning I applied when doing my Web2.0 hacking research, the XSS and CSRF stuff I’ve been toying with, the Social Networking experiments and most of the things behind the GNUCITIZEN umbrella. If you haven’t noticed yet, everything is pushed into the cloud, not only your social life but your personal data and now even your health records thanks to Google. Hacking into your box is not valuable anymore unless attackers are building a botnet. But hacking into your box is hardly scalable if your data is what attackers are after. The cloud is what matters today and will matter tomorrow. |
| CONFidence 2008 [GNUCITIZEN Media Portfolio] Posted: 20 May 2008 04:03 AM CDT CONFidence was great! We would like to thank to Andrzej, Anna and everybody else in the CONFidence team for making this event one of the greatest experiences of a lifetime. Thanks again. We are looking forward for the next event. :)  There were many interesting presentations. We’ve tried to attend all of them although it was really hard to do so when the weather in Krakow was so nice (very different from the weather conditions in cloudy/rainy London). As usual, Adrian and I presented our Anyway, the client-side security slides can be downloaded from here. The embedded devices cracking slides can be downloaded from here. And of course, if you want to see some of the pictures from the event, you can visit House of Hackers and check the CONFidence 2008 album. I am sure that everybody enjoyed the event as much as we did. |
| Quickpost: eicar.pdf [Didier Stevens] [Belgian Security Blognetwork] Posted: 20 May 2008 03:54 AM CDT I like to embed the EICAR Anti-Virus test file in usual formats and less usual formats. Today, I’m publishing a PDF document with an embedded EICAR test file (eicar.txt). This PDF document has also an annotation with a JavaScript action linked to it. Clicking the annotation will export the embedded eicar.txt file to a temporary folder and launch the default editor for .txt files. This doesn’t work with Foxit Reader, because Foxit doesn’t support the JavaScript method I’m using to export eicar.txt (exportDataObject). But you can still export the file manually if you use Foxit Reader. eicar.pdf contains only ASCII characters, so you can use Notepad to see what I did. And I had do to something special, can you guess what? Post your comments! Quickpost info  |
| Posted: 20 May 2008 01:47 AM CDT |
| Rant: Why My ISP Sucks [The Falcon's View] Posted: 20 May 2008 12:17 AM CDT |
| Mail Problems, Busy Week [The Falcon's View] Posted: 19 May 2008 08:24 PM CDT |
| how Belgium loses track of 250.000 cars [belsec] [Belgian Security Blognetwork] Posted: 19 May 2008 06:58 PM CDT You just bring back your license plate and that's it nobody tracks your car anymore You can do whatever you want with it. Export it, demolish it, use it to blow yourself up or attack a bank. There will be a new system in a few years time, but shouldn't it be much simpler to keep the licenseplate with the car instead of with a person. |
| The Two Laws Of Rootkits [securosis.com] Posted: 19 May 2008 06:42 PM CDT I loved Mike Rothman’s title to his take on the Cisco IOS rootkit (original article here).
Okay, technically a rootkit isn’t a vulnerability, but we’ll forgive Mike since I know he knows the difference, and he writes his Daily Incite first thing in the morning. To simplify, here are the Two Laws of Rootkits:
(If you don’t get the sarcasm, I can’t help you). |
| Posted: 19 May 2008 06:12 PM CDT Some say that their university wasn't really much involved in what has been written and that the KUL has been the most important University in the writing of the texts. Now some in the KUL are saying that they didn't really write all the stuff that is in the report and that the Administration of the Interior was behind some things that were added to the report and they didn't count on writing in the first place (but it is difficult to say no the person who pays) Is it intox, are people just leaving the ship, fleeing responsability ? It is clear that some things are moving behind, around and about these University Reports that will become the centerstage of the first of a series of hearings about electronic voting in the belgian parliament starting wednesday. The first thing the parliament should know is which part if any of the report is research and which part is politics added by the Administration and why. They should ask for the drafts, speak to the researchers themselves and have access to the notules of the meetings. Stay tuned. This may become interesting.... Keep the info coming. thanx. |
| Belgium escapes another terrorist campaign [belsec] [Belgian Security Blognetwork] Posted: 19 May 2008 05:25 PM CDT We must be protected by some angel (if you are a religious person) or just some stupid luck. No one has any idea how many times the anti terrorist services will stay ahead of the terrorist groups or loners (very difficult). Belgium has escaped another series of attacks as another Belgo-maroccan terrornetwork was arrested last week. They were starting to plan attacks on the Buildings of the European Community and on the Sheraton Hotel. I never understood why so many traffic and people could pass so easily so near those so important buildings. Or after 11 09 we should never disclaim the impossible. This should be a reminder for any firm in Belgium that the official terror alert is not a bible. You should be prepared for the fact that anytime somewhere a bomb can or will explode and it is better to be prepared than to be in plain chaos at that moment. Especially if you are near a critical public infrastructure or an international center of interest. Things like Business Continuity and Disaster Recovery are important, but also personal guards, evacuation training and a healthy dose of paranoia. The 2 main organisers of these terror networks can be found here http://www.map.ma/fr/sections/boite_annonce/deux_individus_reche1397/view |
| Call for Papers Hack.lu 2008 [Security4all] [Belgian Security Blognetwork] Posted: 19 May 2008 05:13 PM CDT |
| Quote of the day [Security4all] [Belgian Security Blognetwork] Posted: 19 May 2008 04:47 PM CDT |
| Posted: 19 May 2008 01:59 PM CDT |
| New Whitepapr: Best Practices For DLP Content Discovery [securosis.com] Posted: 19 May 2008 01:10 PM CDT One of the most under-appreciated aspects of DLP solutions is content discovery- scanning stored data to identify sensitive content, classify information, and (in some cases) even protect the data. Major DLP tools have long evolved past just scanning network traffic for credit card and Social Security Numbers. Today I’m releasing a new whitepaper on the topic: DLP Content Discovery: Best Practices for Stored Data Discovery and Protection. The paper covers features, best practices for deployment, and example use cases to give you an idea of how it works. It’s my usual independent content, much of which started here as blog posts. Thanks to Symantec (Vontu) for Sponsoring and Chris Pepper for editing. |
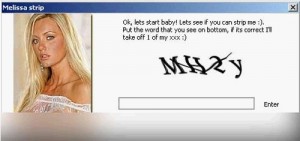
| CAPTCHA Me if You Can! [/dev/random] [Belgian Security Blognetwork] Posted: 19 May 2008 12:46 PM CDT
“CAPTCHA” ? What’s this? Everybody already used CAPTCHA (or “Completely Automated Turing Test To Tell Computers and Humans Apart“). You know those pictures made of deformed letters that you need to understand and type in a specific field to perform some operations like creating some accounts, authenticating, etc. Almost all well-known service providers or applications use them: Google, Yahoo!, PayPal, phpBB. Their goal is easy: forbid bots (computers) to waste resources. The problem is that computers can now “read” them… Most of the CAPTCHA have been hacked! (even the Yahoo! one has been hacked). On sites like captchakiller.com (free!) , even API are available to automatically decode CAPTCHA! They say that the service is provided to help blind people to access resources protected by CAPTCHA on the Internet but how to prevent misusage of this service? Google recently introduced audio CAPTCHA. Check this audio example. It is a step further but audio can also be converted to text (speed recognition). The sound can be distorded, background noise can be added but new algorithms will always be found to circumvent the CAPTCHA! In July 2006 (is this blog so old? ;), I already posted an article about another way to distinguish humans and bots: The goal was to select the three “hot” girls between nine random pictures (the project was called HotCaptcha). Microsoft announced a new solution, more “ethical”, called the Asirra project. Assira means “Animal Species Image Recognition for Restricting Access“). It’s easy: Pictures of animal are displayed and you just have to select all cat pictures! How much time this method will resist? Nobody knows but for sure it will be broken! And even if not broken, some bad guys use the manual way to bypass CAPTCHA. Instead of letting the computer do the job, real humans do it and… they are paid for this business! All combinations of CAPTCHA are stored in databases and ready to be used! Finally, why loose time to decode CAPTCHA when simple users make it for you? End of 2007, a new worm was spread accross the Internet: Trojan.Captchar.A It displayed a nice girl and asked you to decode CAPTCHA to strip her. Decoded strings were recorded and sent to a central server. Quick and efficient! Another solution would be to create CAPTCHA based on high-level questions related to the website or forum content. Why not some tests like this one during the creation of a new account on a forum about mathematics? |
| AMEX password policy - "a daily WTF" [Digital Soapbox - Security, Risk & Data Protection Blog] Posted: 19 May 2008 11:57 AM CDT This, as my good buddy Russ points out - belongs on the daily WTF. I was registering my account on the AMEX (American Express) site and came across this mind-boggling "feature". Apparently, AMEX has a policy, as follows, for their login and password that I would whole-heartedly disagree with. To be fair, there are many schools of thought that would dictate that password policy is irrelevant on a website, and that security shouldn't be based on password strength alone - but I don't necessarily think that this means that you should forgo logic on password policy either. With that being said - here's a lovely screen-shot, complete with auto-pop-up from AmericanExpress.com.  I would absolutely LOVE to hear the community's feedback to this. Am I nuts to think this is a little low on the security totem? User ID Policy:
Hey - wait a minute, what about PCI Compliance you ask? Well, the PCI DSS says the following about password(s) and password strength:
Proof positive folks, compliance does not equal security. Just because you're "PCI Compliant" doesn't mean you even begin to comprehend security policy creation and security strategy in general. Obviously... Yikes. Shame on AmEx. |
| "The Black Hat Tax?" Show me the money [Emergent Chaos] Posted: 19 May 2008 11:25 AM CDT A number of people have sent me links to "Black Hat Tariffs – The Black Hat Taxes on consumer Internet companies are on the rise:" In May 2006, I made mention of the Black Hat Tax, in which most consumer Internet sites have an inherent time, resource, and mindshare tax of roughly 25% due to scamming, phishing, hacking, and government requests. And this drainage has gotten worse two years later which is extremely troubling.So I'm curious: what's the sample size? How does that 40% break out? Who's spending all that time, and what are they doing? Are there things that could be outsourced? (Seems like a possibly huge business opportunity.) Are there design flaws that are being paid for? What size companies are in the set? I don't know Auren. Reading his blog, he seems like a smart guy. I'm just looking for more on where the 40% number comes from, where it's happening, and where it goes. |
| the newest Addition to My Family [An Information Security Place] Posted: 19 May 2008 10:18 AM CDT OK, I know I started a personal blog so I could keep this place security centric, but I really just don’t like doing that. As Alan would say, this is my blog, and I will post what I want. So I have decided to start putting personal stuff over here again. That being said, here’s a personal post. Meet Lizzie: She is a German Shepard / Rottweiler mix that we adopted from the SPCA. We really went in there looking for a smaller dog, but she (corny alert) captured our heart before we really had a chance to look (I’ve heard the dogs picks the family, not the other way around, and I believe it now). She is three months old, and she is already showing me she is one of the smartest dogs I have ever met. And the family loves her already, even though the kids have felt the wrath of sharp puppy teeth from playing with her. By the way, she is named after Elizabeth Bennet from Jane Austen’s Pride and Prejudice, even though I am pretty sure Austen spelled her nickname "Lizzy". Austen is a favorite author of my wife and me. Vet |
| Attendees to be tracked with RFID at The Last HOPE [spylogic.net] Posted: 19 May 2008 10:10 AM CDT  According to 2600 News, 1,500 attendees of this years Last HOPE (Hackers On Planet Earth) hacker conference will be tracked via RFID in a large social experiment which will include games focused on RFID technology. From the press release: "Players will seek ways to protect their privacy, find vulnerabilities in the tracking system, employ data mining techniques to learn more about other participants, and choose how much personal information they will disclose in order to play." Cool stuff...if you are into being tracked via RFID! It should be interesting to see some of the results of this experiment from the conference attendees and to see some cool hacks to gather RFID data and ways to protect your privacy. I did an article on RFID awhile back talking about ways to protect your identity using credit card "shields". The Last HOPE takes place July 18 to July 20, 2008 at the Hotel Pennsylvania in New York City. |
| Conferences... [Liquid Information] Posted: 19 May 2008 09:48 AM CDT I have been thinking of what trainings or conferences I could attend this year. BlackHat Vegas + Defcon sounds like a fun thing to experience again, but the current state of possible laptop search at the airports doesn't sound very inviting to me. Too bad I missed Blackhat Amsterdam, it would have been a lot closer without all the fuzz. Have to keep that one in mind next year. A Finnish conference is the T2'08 conference, it has been good every time I've been there. There is also a swedish conference, Sec-t, which would not be that far away. Both of them are still in the planning phase so there is no agenda to see yet. Even though the networking part of conferences is maybe the most best part, it would still be important to me to have good content to go listen to. Else it would be badly spent money if you have nothing to take with you. I haven't really been looking at any trainings lately. If I would, it might not be directly security-related, but more of learning a technology better. What conferences are you planning on going to, or have already been to? What has been your criteria on participating in those? Did you get anything out of them? |
| securitycomix 1 the first week [belsec] [Belgian Security Blognetwork] Posted: 19 May 2008 09:43 AM CDT |
| security projects and project creep [www.remes-it.be] [Belgian Security Blognetwork] Posted: 19 May 2008 08:02 AM CDT I can not stress it enough but apparently of all types of projects Security Projects are most vulnerable to project creep. More than once I've been called out to save projects that were near dead. The main reason I see there is that goals were not set forward early in the projects, milestones were not defined and/or acceptance scenario's were not adhered to. A few quick tips : - Know what you want to do and why you are doing it. |
| New updated interesting freeware [belsec] [Belgian Security Blognetwork] Posted: 19 May 2008 03:18 AM CDT |
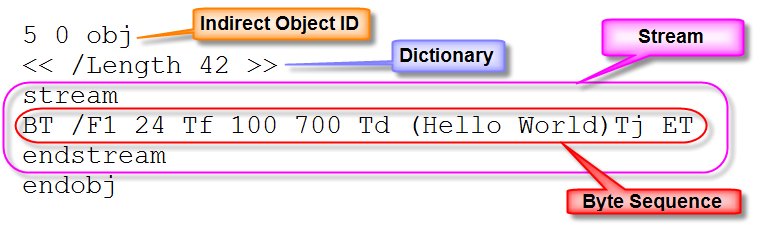
| PDF Stream Objects [Didier Stevens] [Belgian Security Blognetwork] Posted: 19 May 2008 01:09 AM CDT A PDF stream object is a sequence of bytes. There is a virtually unlimited number of ways to represent the same byte sequence. After Names and Strings obfuscation, let’s take a look at streams. A PDF stream object is composed of a dictionary (<< >>), the keyword stream, a sequence of bytes and the keyword endstream. All streams must be indirect objects. Here is an example:
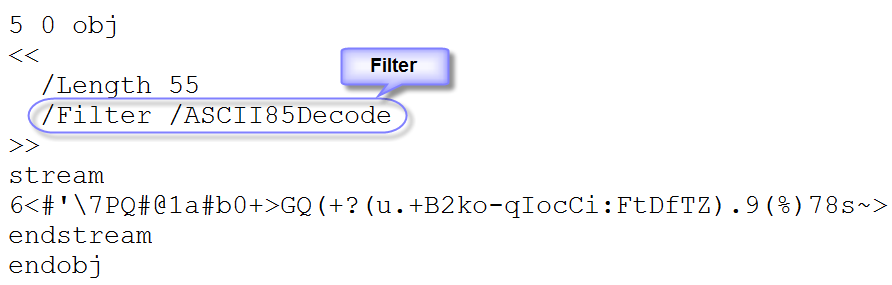
This stream is indirect object 5 version 0. The stream dictionary must have a /Length entry, to document the length of the (encoded) byte sequence. The stream and endstream keywords are terminated with the EOL character(s). In this example, the byte sequence is a set of instructions for the PDF reader to render the string Hello World with a given font at a precise position. It’s precisely 42 bytes long. In this example, the byte sequence is represented literally, but it’s possible (and usual) to encode the byte sequence. This is done with a stream filter. A stream filter specifies how the sequence of bytes has to be decoded. Let’s take the same example, but with an ASCII85 encoding:
The /Filter entry instructs the PDF reader how to decode the byte sequence (/ASCII85Decode). Notice the change of the length value. There are many encoding schemes (ASCII filters and decompression filters), here is a list:
This list is not so long, so why do I claim an almost limitless number of ways to encode a stream? I have 2 reasons:
Here is our example, where the stream is encoded twice, first with ASCII85 and then with plain HEX (I know, this is rather pointless, but it yields simple and readable examples):
Cascading filters also inspired me to create a couple of test PDF documents. For example, I’ve created a 2642 bytes small PDF document that contains a 1GB large stream (a ZIP bomb of sorts). Some PDF readers will choke on this document.  |
| Using twitter to guard your house [Security4all] [Belgian Security Blognetwork] Posted: 18 May 2008 07:27 PM CDT |
| Another example of Black PR [Security4all] [Belgian Security Blognetwork] Posted: 18 May 2008 06:44 PM CDT |
| Using images to support your speech [Security4all] [Belgian Security Blognetwork] Posted: 18 May 2008 06:18 PM CDT |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |




No comments:
Post a Comment