Spliced feed for Security Bloggers Network |
| Evoting : antwerp professor breaks the silence [Belgian Security Blognetwork] Posted: 29 May 2008 06:53 AM CDT As the new evoting proposal was being developed by a consortium of different universities, we thought that nobody would have the guts in these universities to speak out and at least pose some questions. But we were wrong and happy about it. A professor ICT in Antwerp finds that the proposed model doesn't respond to the norms about accesability and usability and can have an influence on the votes of certain groups in the population. He also has some questions about the way the system will control mistakes and changes. We applaud the interview of the professor as a starting point, but would invite him to base his case on the conclusions and propositions in the report itself. It may be that this is his opinion, but it would be too easy to discount this opinion if he doesn't proof his case with references to the report with which he doesn't agree. This is the best method to go forward and have an open and technological discussion about why the present study has some faults that should be taken into consideration and could lead to the radical rethinking of the way we organize our elections. Out of the response of Bruno Seghers (ex Microsoft) we can make up that the EID is a critical part of this system and should have all the attention and investment needed to make it work as it should work. If we vote on paper or not. |
| IED : I am a men now and a woman online [Belgian Security Blognetwork] Posted: 29 May 2008 06:40 AM CDT source datanews Because of a programming error a few hundred Belgians have an electronic ID that present them as the opposite sex if they would use their EID online. Men became women and women became men. The dream of everyone, no ? Only it is only virtual. It is a men's world ..... and women wear the pants..... That is equality :) joke serious : quality control ? |
| Chinese hackers target Sharon Stone [The Dark Visitor] Posted: 29 May 2008 06:27 AM CDT The first calls are starting to make the rounds on Chinese hacker sites to attack the Sharon Stone website. The actress recently started a firestorm in China after she gave an interview suggesting that the earthquake in Sichuan was the result of bad karma. I guessed it would be just a matter of time before Chinese hackers targeted her online and have been monitoring the boards. One site has posted a bit of initial reconnaissance of the website: There was also a post asking to have the unofficial website of Sharon Stone hacked: Tried going to the website for a contact address but found the, “This site may harm your computer” posting. Maybe Jumper will have the time to check it out later. |
| The fraudulent Escrow servers abuse e free domainsystem [Belgian Security Blognetwork] Posted: 29 May 2008 05:49 AM CDT Which other sites are on this server ? http://onsamehost.com/213.239.203.47/ a whole list of subdomains for de.vu ch.vu de.pn dk.tp mx.tp co.uk.tp at.tt es.tt nl.tt us.tt it.tc jp.pn net.tc uk.tc eu.tf de.ms de.gg at.tf page.cx at.lv More information here http://www.nic.de.be/ that says you can get a totally free (sub)domainname here. I hope they have some sort of security-patrol to get rid of bad sites before they get blocked all together....
|
| Flash, AGAIN [The Security Mentor] Posted: 29 May 2008 02:35 AM CDT Youtube videos, and a lot of those annoying flashing ads, come to you courtesy of a third-party plugin ("Flash") in your browser. Sometimes it has security vulnerabilities that let the files it shows take over your computer. It's got one now, and last I heard there was no patch available. Meantime bad guys are taking over legitimate web sites and using them to send you hostile Flash files. You're fairly well protected if you're a Firefox user and have the NoScript extension installed. If you run Internet Explorer, you can either temporarily disable or uninstall Flash. I recommend uninstalling it and then, if you want, reinstalling it later after there's a fix for the current problem. Here are instructions for uninstalling the Flash plugin. Youtube, a number of games, and a lot of annoying ads will stop working until you reinstall. |
| Belgian national egov portal name typosquatted with number [Belgian Security Blognetwork] Posted: 29 May 2008 01:46 AM CDT |
| Schools Battle Proxies [Jon's Network] Posted: 29 May 2008 12:49 AM CDT Stan Trevena, IT director for Modesto City Schools, penned The Internet Filtering Battlefield and describes the constant struggle to keep student and faculty behavior inline with the acceptable use policy. This is important to keep students safe and to keep the district out of legal trouble. It is a great article that explains exactly how users have been bypassing filters over the years. I wanted to disagree on the part about encrypted proxies however:
There is enough processing power to proxy SSL sessions. Blue Coat, Secure Computing and Palo Alto all do it. (Palo Alto does it fastest.) It can be a pain though. Some of the vendors make it easier to manage than others by maintaining your list of certificates for you and letting you control which types of sites you proxy for, e.g. you can ignore banking and shopping traffic but proxy other SSL traffic. If you deem the risk large enough to warrant the hassle of pushing your own cert to the browsers and pointing them to the proxy, then there is ample processing power to do this. What I think is more effective than URL filtering is just straight monitoring of all internet use (not just the blocked sites) and reporting on activity by username to hold users accountable. Stan mentions this at the end of the article. Most filters offer the type of reporting that HR departments require. I also recommend Vericept to schools that want to augment their filter and increase their visibility into user behavior. |
| Chinese Female Hacker Group [The Dark Visitor] Posted: 29 May 2008 12:20 AM CDT In the male dominated world of Chinese hackers, females find it difficult to be accepted as equals. Their technical skills are often viewed as inferior to their male counterparts. As far as I am aware, the first group of female Chinese hackers to break this mold were the Six Golden Flowers. The Golden Flowers have since broken up and gone their separate ways, but a new and larger group has taken their place, the Cn (China) Girl Security Team. The website for the China Girl Security Team was registered on 12 Mar 2007 and currently has 2,217 members. The leader of the group Xiao Tian, is only 19 years old: One of Xiao Tian’s chief lieutenants, who goes by the online name of Clever Without Equal (that’s close anyway), is dialed into just about every major Chinese hacker site on her blog: Also linked through Clever’s blog is Evbs: She seems to be getting the hang of this hacking thing: |
| Pushing Virtual Buttons... [Rational Survivability] Posted: 28 May 2008 11:46 PM CDT My last couple of VirtSec posts have caused quite a stir in certain circles. The "debate" between who "owns" VirtSec that originated as part of my response to Simon Crosby of Citrix regarding the same has been picked up and amplified on multiple fronts. Greg Ness from BlueLane wrote a piece referencing it that was cross-posted on virtualization.com and that even made its way up to VC/investment blogs such as seekingalpha.com (Citrix vs. Chris Hoff ;) and has had my mobile ringing/vibrating itself off my desk over the last week or so. It's hard to believe sometimes just how many people -- and who -- reads my steaming pile of blogginess. The second post of interest was in regard to the provenance of VMware's VMsafe and my reflection on prior art (Livewire) by VMware's Rosenblum & Garfinkel which seems as though it could be the progenitor of the upcoming technology. The very tail-end update of that post referenced another piece of research produced by Komoku based upon similar work focused on rootkit defense. As I pointed out, Komoku was recently acquired by Microsoft. I added those comments deliberately as a parenthetical -- almost like a bookmark -- because what I intended to do next was directly compare and contrast the technology architectures and approaches of VMware, Citrix and Microsoft as it relates to security integration. It seems a bunch of really bright folks caught onto that because a slew of links (such as this one) followed -- driven mostly by Alessandro's (virtualization.info) post titled "Is Microsoft Working On VMsafe-like Framework" I think that's an excellent question ;) It's pretty clear where Citrix's CTO stands on the matter -- as flawed as I see his shortsighted market approach (note I didn't say *technical approach*) -- but Microsoft stands to gain an interesting foothold in regards to security should they play this game correctly. I found it interesting that others are starting to recognize that the virtualization battle isn't going to be won by a shoot-out and the hypervisor-version of the OK corral. It's the effectiveness of the ecosystem and the ability for the channel to serve it up and the customers to implement it. People are sick of sweeping up the decaying corpses of good technical solutions that suck in terms of integration, implementation, operationalization and accountable support -- especially when they have to keep paying for it. Ah the "best-in-breed" versus "good-enough" debate again? Not to further pick on Citrix (or Xen specifically) but here's a great post from Schley Andrew Kutz from the searchservervirtualization.com blog titled "Xen: An endangered species in the virtualization ecosystem?": While Citrix Systems' Xen's ubiquity may help the technology earn a legacy as the invisible hypervisor, it may also prove the most challenging next step for IT administrators and developers who want to find or develop software that leverages, supports or extends the Xen hypervisor. Amen to that. Take heed, Citrix. I maintain your CTO is blinded by what can only be described as a denial of market realities and an undying (arrogant) allegiance to what some might consider to be an architecturally superior product on some fronts, but a lacking solution on many others. Securing the hypervisor is definitely important. However, securing both the hypervisor and the assets that sit on top of it by providing the most extensible, effective and manageable means of doing so is really what's important to customers. Sometimes, it has to be about more than where you came from. Sometimes it's about where you're going. I'll be finishing up my post on where I think Microsoft ought to go shortly. /Hoff |
| Can the Internet help bring peace to the Middle East? [StillSecure, After All These Years] Posted: 28 May 2008 11:22 PM CDT For a long time I have believed that the Internet could be the single biggest tool for world peace ever. By bringing people together and allowing them to share common experiences and interact in a person to person environment, the Internet is a great equalizer. This view was reinforced for me today when I read the story of G.hos.st in the NY Times. G.hos.st is a free web based virtual computer that gives you storage, email and applications available anywhere. I have just signed up for an account, so will have to tell you about how it works later. |
| Does VMware want to own the virtual ecosystem? [StillSecure, After All These Years] Posted: 28 May 2008 11:05 PM CDT VMware has obviously staked out the clear dominant position in the virtual machine market. However, owning the hypervisor alone may not be enough. VMware announced the acquisition of B-hive Networks, a California and Israeli based company that developed application performance management for virtual applications. According to this article in ComputerWorld, the news is comes as bad news for several start ups that were were trying to establish themselves. With VMware themselves including virtual application performance management, a 3rd party competitor is going to be at an extreme disadvantage to the built in VMware solution. It clearly signals a move by VMware that they want not only to provide the environment for virtual machines, but many of the |
| What to make of "Hacker Eliminator" [Digital Soapbox - Security, Risk & Data Protection Blog] Posted: 28 May 2008 10:20 PM CDT Greetings - I've been traveling a significant amount lately so it's harder and harder to find time to sit down and write something more than meandering thoughts - but I've been putting this together in my head for a while and now it's time to write it down and hit the Publish Post button. As many of you may already have figured out I tend to be hard on companies that are, how shall I put it, fraudulent in their "security" services. "Hacker Eliminator" quickly rises to the top of this list like spoiled milk in my latte... quite obvious, yet still oddly intriguing. A little digging revealed the following: Company Name: LockDown Corp. Product Name: "Hacker Eliminator" Product Motto: "Picks up where antivirus programs and firewalls leave off" Home Page: http://hacker-eliminator.com/ Current verion: 1.2 First off, allow me to say that *anyone* who puts the following on their site/product invites people to outright make fun of you... "Hacker Proof Guarantee: You will not become infected with a remote access Trojan without getting a warning. This is why" Impressive! They offer 3 layers of protection - scanning files, detecting startup methods, and detection of Internet servers/processes. Again, very impressive... I think every virus scanner on the planet does this... in 2001. Below is a quick paste of the quote from "LockDown Corp."... wow - they have 6 years of experience! That's almost as many as I have they must be good! About LockDown Corp.Anyway... I just had to click on the "Buy Now" page, which by the way is some 3rd party payment company called "Onesecond-128.bitencryption.net". From their SSL certificate they installed the cert in June of 2003, and set it to not expire - a great security (I mean, usability) feature. The issuer, obviously a trustworthy company, is as follows: E = system@lockdowncorp.comYIKES. Something else interesting on this page, where you'd "buy" the Hacker Eliminator product - notice some of the other awesome products for purchase? Also, look at the bottom of the page, interesting enough the Copyright date and browser compatibility as here: Copyright 2002 One Second Online Services: Email:sales@lockdowncorp.comSo let's recap, so far everything looks and smells like Fisherman's Warf on a sunny morning... It gets better folks, it just gets better. Check this page out. They're using SubSeven 2.1.4 (how old is that again?) and NT 4.0 as the screen shots - are you kidding me?! Wow - I'm convinced, sign me up, where do I send my check? At least let's look at LockDown Corp's crack team of researchers and see what sorts of things they've uncovered lately. Click here, and here, but be prepared for some serious 0-day stuff. Be careful of those "Hacker Tricks"... Hopefully their privacy policy is at least responsible.... oops! Alrighty, so by now you're asking yourself - "Self, is this even a real company? Are they for real?" I'm thinking that myself, and while I download and dissect their EXEs I offer you the chance to decide for your own damn self. Oh, and in case you want to look them up, their DnB number is #15-483-9976 and their Tax ID # is 02-0509165 (right off their pages). Oh, one last thing... They're running Apache 1.3.27, which is from back in... oh, 2002 I think? EDIT: So I went back to the "Wayback Machine" and dug up their site, wow... their last update was Aug. 18, 2007 and since 2002 when the site first went up the site has been changed a whopping 13 times. Go Hacker-Eliminator and LockDown Corp! |
| Mixed Mode URL filtering [Jon's Network] Posted: 28 May 2008 06:54 PM CDT I’m working with a midsize business looking to ditch their Surfcontrol/ISA setup. They want an inline filtering appliance and have already looked at Barracuda and 8e6 Technologies. The problem is they want most of the users filtered transparently (bridge mode proxy) and some using an explicit proxy. Barracuda needs two boxes to do this (one for each mode). 8e6 can’t function as a proxy at all so they would need to set up a proxy that then sends the traffic to 8e6. This problem is easily solved using St. Bernard’s iPrism. St. Bernard offers “mixed mode” filtering which means they can be a transparent proxy and explicit proxy at the same time for different users, machines or protocols. It can be quite handy for organizations with mixed authentication or machine environments or that want granular reporting on web use by terminal server users. Here is the KB article: iPrism Mixed-Mode Traffic Filtering. In this case, it looks like iPrism is the best fit. |
| XHR, CSRF and bypassing the same origin policy [Writing Secure Software] Posted: 28 May 2008 06:50 PM CDT I did a presentation on CSRF on behalf of the local chapter and an interesting question come out about CSRF and XMLHttpRequests (these are very popular wih Ajax nowdays..) CSRF vulnerabilities exploits the trust that the web application has on the browser. In the case of an authenticated session, the browser does not bother to resend the SessionID to the application as a proof that each HTTP request is authenticated. That's a problem and that's the root cause of CSRF or session riding (I like this term better actually because you are really riding an authenticated session..). If I social engineer a victim forcing to select a form (via webmial for example) that has a malicious HTML tag such as iframe with embedded a GET request and such request get issue at the same time I have an open session with another application and it does not get re-authenticated then an authenticated request will be issued by the browser. Attack of this nature can eventually force a business transaction such as bank transfer, denial of service via forced logout, modification of shopping cart credentials to force a purchase as a price and address at the choice of a malicious user. One of the root causes of CSRF on the client is the lack of enforcement of the same origin policy. Such policy prevent two different documents loaded on the browser to access each other via javascript for example because the policy will check that comes from two different sources. The problem is that does not work for HTML tags so that I can embed URL in two different document and have all invoking an authenticated session. In the case of XmlHttpRequest such policy is enforced on the browser and in-theory a CSRF attack will be mitigated by the browser control. The reality is that if malware is present on the client (such as with XSS exploit for example), then you can potentially override this control, simply because XHR rely on client javascript. In other cases if the control is invoked via a flash the same origin policy can be actually disabled to this vulnerability as a configuration management issue. Here are the facts in the details : 1) XMLHttpRequest has a same origin policy enforced in both IE and Mozilla 2) Because of the same origin policy you cannot access, a document/script loaded from one site of origin from a site from a different origin 3) XMLHttpRequest rely on javascript to issue POSTs such as: var post_data = 'name=value'; var xmlhttp=new ActiveXObject("Microsoft.XMLHTTP"); xmlhttp.open("POST", 'http://url/path/file.ext', true); xmlhttp.onreadystatechange = function () { if (xmlhttp.readyState == 4) { alert(xmlhttp.responseText); } }; xmlhttp.send(post_data); 4)Since XHR rely on javascript, you can have malware (like Samy webworm that rely both on XSS and CSRF) installed on the client that can overwrite the javascript function by overriding the constructor XMLHttpRequest() { } By doing you are bypassing the call and disabling the same origin functionality of XHR 5)The same origin policy can also be bypassed with a flash Adobe/Macromedia Flash to issue XHR because cross domain is permitted because of a rule in "crossdomain.xml" file present in the root of the target webserver. So basically like everything in security there is no 100% mitigation of the risk. In the case of XHR CSRF browser controls can also be bypassed despite the same origin policy. The golden rule for security is to rely on multi layer security, XHR with same origin policy but also unique token for each URL and tied to the user session like you can so using OWASP Guard so every request is authenticated. References http://taossa.com/index.php/2007/02/08/same-origin-policy/ http://www.cgisecurity.com/articles/csrf-faq.shtml http://jeremiahgrossman.blogspot.com/2007/01/preventing-csrf-when-vulnerable-to-xss.html http://taossa.com/index.php/2007/02/08/same-origin-policy/ |
| Hack of the day politiebeersel.be [Belgian Security Blognetwork] Posted: 28 May 2008 05:13 PM CDT |
| There was control but also too much trust (Societe General) [Belgian Security Blognetwork] Posted: 28 May 2008 04:50 PM CDT When the biggest french trader/speculator scandal broke, everybody asked why the controls didn't work. Everybody was thinking logically that if such a fact was discovered by the internal auditsystems, that the hierarchy would have been responsable enough to intervene immediately. They didn't. They said they knew that there were alerts by the internal controls and audits, but that they trusted their supertrader. A healthy dose of paranoia - as I said before - is sometimes a necessary evil. |
| Posted: 28 May 2008 04:11 PM CDT |
| The BlackHat 2008 USA Twitter page [Belgian Security Blognetwork] Posted: 28 May 2008 03:29 PM CDT |
| Who’s the Weakness? [Belgian Security Blognetwork] Posted: 28 May 2008 02:20 PM CDT
The Canadian Minister of Foreign Affaires, Maxime Bernier was forced to resign due to a scandal in his country: Sensitive information were disclosed. The problem was the Minister himself! He forgot documents classified “secret defense” in his girlfriend apartment. This is a big mistake but, unluckily for him, his girlfriend was linked with two guys in relation with a well-known bikers gang… She also has a weird past. Funny touch, she’s president of a security company! Once again, this proves that, even with the best technologies deployed to protect your assets, humans stay the weakest link! Read the story here. |
| Quote of the day [Belgian Security Blognetwork] Posted: 28 May 2008 02:10 PM CDT |
| Moving, Moved, On the Move [The Falcon's View] Posted: 28 May 2008 12:14 PM CDT |
| Posted: 28 May 2008 11:29 AM CDT PAC, as in personal access control. Getting unauthorized access to a company's assets is often child's play, security pro's know that. Guys like Steve Stasiukonis, CEO of Secure Network and Ira Winkler, CEO of ISAG can regale you with stories of literally walking into supposedly high secure buildings like they walk into the grocery store. The underlying flaw is often people and these two gentlemen look like nice guys, and they are. But if Steve and Ira were morally challenged, they could the steal the shirt off your back. |
| RIM speaks out on BB security [Emergent Chaos] Posted: 28 May 2008 07:57 AM CDT  El Reg writes that the India Times writes that RIM has "blackballed" (El Reg's words) the Indian Government's requests to get BB keys, saying what we suspected, that there are no keys to give. The India times says: BlackBerry vendor Research-In-Motion (RIM) said it cannot hand over the message encryption key to the government as its security structure does not allow any 'third party' or even the company to read the information transferred over its network. The full RIM letter to its customers says:
My major grumble remaining is that while RIM has been very good at some assessments (FIPS 140 and CAPS are worth something, CC is not), Those of us in the real world haven't seen the BlackBerry architecture. I still hear people say, "Oh, you can't trust that because the French government banned them," which is also FUD, but absent an open attitude about public review, is going to keep happening. My response to that FUD is to counter-FUD by pointing out that there's no better way to spy on someone than to FUD their existing security system. It's worth something to know that Charlie Miller hasn't broken the BlackBerry, but it would be better to have more to go on. Thank you for the discussing rather than ignoring this, RIM. Please, may we have another? |
| Your iPhone has a Good Memory! [Belgian Security Blognetwork] Posted: 28 May 2008 04:39 AM CDT
I don’t have a iPhone yet. I’m waiting for the version “2″ which should support 3G networks. Take care if you sell your beloved iPhone to an untrusted person: Your phone (as any other PDA or mobile phone) knows everything about you: emails, calls, SMS, visited websites. When the owner of an electronic device changes, it’s a good (read: “mandatory”) practice to perform a full cleanup before sending the device to the new owner. But it seems that the reset feature available on the iPhone (using iTunes) does not really remove the data! Jonathan Zdziarski wrote a book “iPhone Forensics Manual for Law Enforcement” (check his live demo) about this topic. He was able to recover deleted files on an iPhone! Take care! |
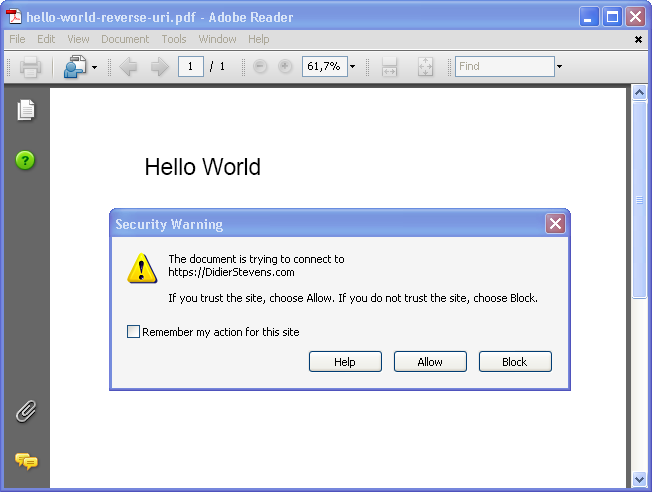
| I Still Use Foxit Reader [Belgian Security Blognetwork] Posted: 28 May 2008 03:38 AM CDT Foxit Reader has been my default PDF reader for more than a year now, as an alternative to the Adobe Acrobat Reader that stalled too often when starting up. While playing with the PDF file format, I created several PDF files that uncovered potential security issues with Foxit Reader. A PDF file with an OpenAction triggering an URI action causes Adobe Acrobat to prompt the user for approval, before accessing the URI: But Foxit Reader opens Internet Explorer and visits the site without confirmation prompt. I submitted a feature request to Foxit Software for this. Another example is a JavaScript inside a PDF file that switches the reader to full screen mode. Adobe Acrobat Reader will warn you for spoofing attacks and ask for your permission to switch to full screen, while Foxit Reader does this immediately. Of course, these warnings will only help a user that is aware of the potential risks. But in a corporate environment, you can also set the appropriate registry keys to block all these actions by default. It was also trivial to assemble some simple malformed PDF files that cause problems for Foxit Reader, but not for Adobe Reader. I submitted these files to Foxit Software. Adobe Acrobat Reader allows you to disable JavaScript. Until recently, Foxit Reader required a JavaScript plugin for JavaScript support. Omitting the plugin was a simple way to disable JavaScript. But since version 2.2, JavaScript is embedded in the main executable and there is no configuration switch to disable it. Many Foxit Reader users have requested this feature. If you absolutely want to disable JavaScript in Foxit Reader 2.3, there’s a quick and dirty trick. Search for the ASCII string JavaScript (preceded and terminated by byte 00) in the Foxit Reader executable (you should find only one occurrence), and replace it with javascript, for example. Actually, this patch will not disable the JavaScript interpreter for Foxit Reader, but it will prevent Foxit Reader from recognizing the /JavaScript name in a PDF document, effectively making it to ignore JavaScript instructions (names are case-sensitive). You can make this patch permanently by editing the Foxit Reader executable with an hex editor, or do it temporarily by patching in memory with my bpmtk utility. The command to achieve this is: search-and-write module:. hex:004A61766153637269707400 hex:006A Of course, this is not a serious risk analysis of Foxit Reader. I started to use Foxit Reader as a solution to the Adobe Acrobat Reader performance problems, not for security reasons. And now that I’ve delved into the PDF file format, I did some random tests with Foxit Reader and Adobe Acrobat Reader. This gave me the impression that Adobe has more experience with security risks and vulnerabilities, than Foxit Software, and that this experience is reflected in the design of their products. I’ll still be using Foxit Reader as my main PDF reader, and I’ll still analyze suspect PDF files in a controlled environment.  |
| Tibetan writer’s online ID hijacked [The Dark Visitor] Posted: 28 May 2008 12:07 AM CDT Ordinarily, I’d try to obfuscate text on this subject but since we’re already GFW’d, who cares… A couple of sites are reporting that the well-known Tibet independence writer Woeser has had all or many of her online accounts hijacked and her website defaced with an anti-splittist message. The Honkers Union of China has taken responsibility. The honkers have used her Skype account to attempt to contact her associates. No word if the contact list has been abused to send malware. Interesting snippet from the article:
The website is still defaced at the time of this writing.
|
| Security and Privacy Day @ Stony Brook [Writing Secure Software] Posted: 27 May 2008 05:52 PM CDT Stony Brook University is hosting a Security and Privacy Day next Friday May 30th http://web.crypto.cs.sunysb.edu/spday/. The topics being covered are pretty interesting such as language based security, security and outsourcing, network security, trusted hardware and privacy: Use of Links programming language to enforce security policies http://www.cs.umd.edu/projects/PL/selinks/ from Dr Michael Hicks of Univ of Maryland Languages for tracking information flows and in particular security metadata (e.g. CIA attributes) from Dr Marco Pistoia of IBM Database as a Service (DAS) for secure and efficient query evaluation over encrypted databases from Dr Wendy Hui Wang of Stevens Security as A Service models (SaaS) from Suresh Sari also from IBM Research An other interesting papers.. May 25 is the deadline to register. The organizers also plan a nice sightseeing program with wine tasting and boating trips around the Long Island Beach area. I plan to attend the conference also to meet Dr Radu Sion for which I had some previous paper email exchanges (Financial Cryptography Conference in Mexico last January that I did not attend) and connect with some academics in light of my future publishing endeavors (a book I intend to write on Software Security Frameworks) Most importantly to take Suzanne (my wife) with me and celebrate together our 4th wedding anniversary with a nice visit/lunch at one of the local wineries on Saturday. Security and Wine Tasting is really appealing...+ car racing event would be elecrifying...I refrain myself would not take the wine-car talk spin topic on this blog... Cheers :) |
| Will Finally IPv6 Arise? [Belgian Security Blognetwork] Posted: 27 May 2008 03:56 PM CDT
The Organization for Economic Co-operation and Development (OECD) published a document to warn goverments and business about the near-future IPv4 addresses shortage. Actually 85% of the IPv4 address space of already assigned (total space is 2^32 == 4,294,967,296) and should be fully assigned by 2011! Of course, a lot of big networks are already NATed (hidden) behind a few public addresses but there are still a lot of wasted addresses. The IPv6 protocol is stable and available for a few years now. I remember when I was playing with the 6bone nine years ago: person: Xavier Mertens address: Lozenberg, 22 1932 Zaventem Belgium phone: +32 2 717 17 00 e-mail: xavier@euro.net nic-hdl: XM1-6BONE remarks: First registration remarks: This object is automatically converted from the RIPE181 registry notify: xavier@euro.net changed: xavier@euro.net 19990701 changed: auto-dbm@whois.6bone.net 20010117 source: 6BONE IPv6 offers many new interesting features compared to the version “4″:
Check here for a full list of IPv6 specs. But the IPv6 protocol was never massively deployed. Why? IMHO, due to its relative complexity. IPv6 is still difficult to deploy natively on a network. Most of the time, you have to encapsulate IPv6 into IPv4 to reach your IPv6 backbone. Not much ISP already provide IPv6 connectivity and , AFAIK, none in Belgium except Belnet (see here) Implementing IPv6 on a network is a long and difficult project (with huge costs). All devices and applications must be IPv6 ready. Security, as usual, is a key point (are your firewalls IPv6 ready?) . It’s impossible to switch from IPv4 to IPv6 in “one click”. It means a lot of work for IT teams in the future! |
| Beware. A wide scale attack on Adobe Flash Player (updated) [Belgian Security Blognetwork] Posted: 27 May 2008 12:40 PM CDT |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |

















No comments:
Post a Comment