Spliced feed for Security Bloggers Network |
| Posted: 18 May 2008 01:04 AM CDT In name only, but NASA will be sending a database of names to the moon on the forthcoming Lunar Reconnaissance Orbiter. You can add yours.  |
| Poetic Weekly Security Review [Rational Survivability] Posted: 17 May 2008 08:44 PM CDT I do these every once in a while. Enjoy -- The Air Force , it seems,
Fear not my good lemmings
New PCI - deadline's coming, And finally, |
| Firefox 3 Release Candidate 1 Now Available [Liquidmatrix Security Digest] Posted: 17 May 2008 09:15 AM CDT  Well, in an unceremonious move the Mozilla folks have released the latest incarnation of Firefox. I thought thet might have some fanfare around the launch but, nope. You can download the one for your respective language via the following link. Download page: Firefox 3 rc1 Enjoy. |
| Did Someone Forget To Lock The Digital Back Door? [Liquidmatrix Security Digest] Posted: 16 May 2008 05:27 PM CDT  It seems that more and more stories about fake Cisco gear are popping up. And, shocker, most of the gear originated in China. This has led to the inevitable thrust and parry of the media’s lust for anything scandalous. “If it bleeds it leads” my old editor used to tell me. Which is funny when you consider I was on the entertainment desk back then. But, is there something to this? Or are folks hunting rabbits out of season? Or is this just a story of contractor greed that has spiraled out of control? Robert O’Harrow Jr. has a nice summary piece that wraps up some of the angles in this story. From the Washington Post:
In one part of the piece O’Harrow points to an article written by Joab Jackson at GCN. He touches on the aspect that it could be the GSA (General Services Administration) that is responsible for this mess. The GSA is a little vague with respects to policies and practices. Just look at per diems for gov employees and contractors. They hand you a chunk of money for the day for food and such. But, you don’t have to show any receipts (at least that was the case several years ago). Not a bad deal for the employee. There is apparently even more ambiguous language concerning sub-contracting. The back door may have been left open. But, rather than the spectre of Chinese hackers planting backdoors in faux equipment (albeit possible), it seems that there may be bigger threat is in the room. Plain old greed. |
| The SecurID Killer [Matt Flynn's Identity Management Blog] Posted: 16 May 2008 05:02 PM CDT I'm a fan of RSA's SecurID product. It's got a highly secure approach, nearly indestructible hardware form factor, lots of form factor options, tons of partners and coverage for apps, servers and devices, and a flawless track record. But the competition has been creeping up. Some try a similar approach to RSA with key fobs displaying numbers or other hardware tokens: ActivIdentity Aladdin Knowledge Systems EnTrust CryptoCard MyPW SecureComputing Vasco Others have a software only approach: AdmitOne (formerly BioPassword) - uses keystroke dynamics Arcot - uses PKI PassFaces - uses user's ability to remember human faces PhoneFactor - uses mobile phone as the device Some are biometric: DigitalPersona L-1 And they all have redeeming qualities. But many are susceptible to keystroke logger attacks (which are getting more and more sophisticated). Others are cheaply made hardware. Some just lack partnerships and market penetration. But there's a new kid on the block. And it seems to be a very cool solution that may quickly become a force to be reckoned with. It's a very small form factor, seemingly very secure, extremely easy to use, requires no client software, inexpensive, and works on any platform. Welcome YubiKey to the arena. I'll let you figure out the details for yourself. It won't allow you to converge a single credential for physical and logical access and it won't work across multiple systems (unless it's used with OpenID or something like that) and it won't serve as a single form factor for multiple uses (like signed email and remote VPN). But, it's a pretty cool new entrant to this arena. And that's a feat in itself. Let me know if I missed your company and you'd like to be added to the list. |
| Apparently The State Department Didn't Learn From Regular Passports [Emergent Chaos] Posted: 16 May 2008 04:30 PM CDT
About the size of a credit card, the electronic-passport card displays a photo of the user and a radio frequency identification (RFID) chip containing data about the user. The State Department announced recently that it will begin producing the cards next month and issue the first ones in July. That's right RFID just like booklet style passports. Only it won't be encrypted and it won't be shielded. It will even be "vicinity" aka long range RFID, so the very intent is to read them from a distance. While the card isn't supposed to have any personal information on it, it will link back to a database that does contain personal information. I for one don't have a lot of confidence that that database can be kept properly secure.
And if that wasn't bad enough only about 10% of border sites will actually have readers: Kelly Klundt, a spokeswoman for U.S. Customs and Border Protection, said the deployment of passport card readers to the largest and busiest 39 border-entry points was intended to expedite travel. The more than 300 remaining points of entry without passport card scanners are in remote locations, and officials will visually inspect passport cards at those entry points, she said. Joel Lisker, a former FBI agent who spent 18 years countering credit-card fraud at MasterCard, said the new cards pose a serious threat to U.S. security. "There really is no security with these cards," he said. So there you have it. Once again the government is engagins in security theater rather than actual security. [Image from: http://www.uspasscard.com/] |
| Jane’s Launches Terrorism Events Map [Liquidmatrix Security Digest] Posted: 16 May 2008 11:46 AM CDT If you are at all involved in physical security as a portion of your portfolio no doubt you have considered terrorism in your risk assessments. The grand dame of mil space security information, Jane’s, announced a new service for tracking terrorism and insurgent activities around the globe.  From the press release:
OK, this is quite a cool offering. Although too rich for this scribbler’s pocket book it looks to be a significant resource for global operators. Here is a screen cap from the demo. 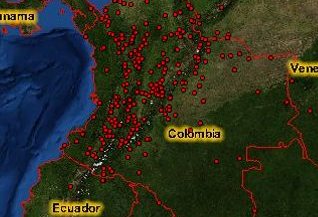 You can view the demo of the new offering here: JTIC Demo |
| Adam on "Silver Bullet Security" Podcast [Emergent Chaos] Posted: 16 May 2008 11:06 AM CDT The 26th episode of The Silver Bullet Security Podcast features Adam Shostack, a security expert on Microsoft’s Secure Development Lifecycle team who has also worked for Zero Knowledge and Reflective. Gary and Adam discuss how Adam got started in computer security, how art/literature informs Adam’s current work, and the main ideas behind Adam’s new book The New School of Information Security. They go on to chat about Adam’s aversion to the term “best practices,” the role IEEE Security & Privacy magazine plays in bringing the science of security to a practical level, and whether the biggest problem of the CardSystems breach was the following the letter, rather than the spirit, of PCI. Also on the agenda, duck-billed platypuses, Kandinski, and books by Pynchon.Show 026 - An Interview with Adam Shostack. The one thing I'd like to add is that we mentioned Frank Abagnale's Catch Me If You Can. It was a fun interview. |
| Clearing up [IT Security: The view from here] Posted: 16 May 2008 11:05 AM CDT I had a mail yesterday after my DLP post expressing concern that I was endorsing Orchestria. It wasn't from any of the Vontu crowd, nor Vericept, nor any of the others in this space, just to be clear. I'm not going to say who it was as they wouldn't thank me for making it public, but just for the record, I was deliberately not endorsing them. I think it's hard to tell in print, but it was supposed to be slightly tongue in cheek. I was told a lot of impressive stuff by the CTO, and without any proof. I have no idea if they are any good or just have a big marketing budget. Personally I would be surprised if it was all true, as they wouldn't need any advertising budget if it was, it would sell itself - and they seem to have blown a huge wedge on getting out into the media. I am still surprised by the suddenness with which they appeared on the scene, even though they had been around for 5/6 years previously working in the compliance space. I've just come out of the compliance space myself, and never saw them there. I was slightly mystified by the claim that they do 'more than just DLP', and then described what they do, which was... erm, DLP. If they DO do DLP to the extent they say, then they still just do DLP I'm afraid, not super-DLP, not DLP-extreme, or even DLP-with-knobs-on, just plain old DLP. They may be doing it super well (or well-extreme, or even well-with-knobs-on), but DLP doesn't break down into subsets, it's already an all encompassing term. This makes me think that they might be a little confused about what they are selling. This often seems to happen when a company has to make a swingeing turnaround from their original product marketing direction. I've worked for a couple of companies (again, no names) where the original idea has been technically sound, but completely unsellable, and changing the message serves to confuse not only the customers, but the internal staff. I wasn't at Ingrian when the focus changed from SSL to data security, but I was selling their kit in the UK. People loved the SSL device, I still do, they are still used in the UK deployments I performed. People didn't understand the data security device, and a complete change of architecture really stalled the company for a short while. They recovered of course to be purchased recently by the marvelous SafeNet (it really doesn't work in print does it?), but it was a tough time. I've been through that twice with other companies, and changing the marketing message can be as time consuming as changing the product direction, sales model, or any other part of the organisation. Something I will say for Orchestria though is that they have the right attitude towards this to succeed - complete self-confidence in the face of adversity, and seemingly infinite marketing dollars. What I can't yet do is endorse them, I hope this is all clear now! |
| Data isn’t ‘private’ if you put it on a social networking site [Network Security Blog] Posted: 16 May 2008 08:55 AM CDT Private: confined to particular persons or groups or providing privacy; “a private place”; “private discussions”; “private lessons”; “a private club” … i.e. something a social network isn’t. I get annoyed with people who use the word ‘privacy’ when talking about their information on a social networking site; by definition, anything put on a Facebook or MySpace is there for sharing and is no longer private. If you want to keep your information private, don’t put it somewhere that’s specifically designed around the concept of blasting your info to as many people as possible in the first place! We’ve got mashables and all the other technologies that are designed to share our information, or data portability as it’s called. People want to be able take their information from one application to another as easily and transparently as possible. That’s great, it’s wonderful for sharing information. It’s also about as far away from ‘privacy’ as you can get. There’s a big hubbub in the blogosphere because Facebook is blocking or limiting the amount of information other sites, like Google’s Friend Connect, can collect from the Facebook API. Facebook claims it’s about privacy; they believe users should have the right to control where their information goes and how it’s being used. I agree with that statement, but if someone is putting their personal information on Facebook, then they’ve made the choice of giving up that control, since any screen scraper or search engine can be used to pull down the information with very little effort. While I hate agreeing with Michael Arrington, he’s right; Facebook’s decision to limit what other social networks can pull from the FB API is about protecting Facebook’s business model and has nothing at all to do with their user’s privacy. Facebook wants to squeeze every possible cent from the value of your information before they let anyone else have it. I don’t blame them, I just don’t have to give them anything to work with. Robert Scoble is wrong, privacy isn’t dead; people are just willing to give up privacy for the convenience of being part of a social network. If someone wants their data to be private, they shouldn’t be putting it online. Privacy isn’t dead, but you’ve made a decision to give up your privacy when you put it online. You have to weigh the value of having that social interaction versus what your information is worth to you. Most people make that decision without any conscious thought, which isn’t Facebook’s fault. Not everyone is a professional paranoid who spend a large amount of their time thinking about these issues, but everyone should at least be aware of what they’re putting online. The Internet, and especially a social network, is designed around the concept of information sharing. Privacy is about controlling your information and controlling who has access to your information. If you put that information on Facebook, you’ve ceded that control to them, and even they don’t have that much control over who can access it. You can control where and when you put your information online, but once it’s there, privacy isn’t applicable. You’ve chosen to put it in a public forum, therefore your information obviously wasn’t something you wanted to keep private in the first place. |
| Security Briefing: May 16th [Liquidmatrix Security Digest] Posted: 16 May 2008 08:19 AM CDT  OK, first day jitters are starting to kick in. The funny thing is that my first day doesn’t start until this Tuesday. Breathe. And now, the news…
Click here to subscribe to Liquidmatrix Security Digest! Tags: News, Daily Links, Security Blog, Information Security, Security News |
| Fawcett Forgives Woman Who Leaked Medical Info [Liquidmatrix Security Digest] Posted: 16 May 2008 07:55 AM CDT  Always one for grabbing the spotlight (inexplicably at times) Farrah Fawcett has forgiven the hospital staffer that leaked her personal info. From Starpulse:
Pawn or not it still doesn’t excuse the behaviour of this staffer. Medical records are not open season. |
| Last Hope To Track Visitors [Liquidmatrix Security Digest] Posted: 16 May 2008 07:43 AM CDT  As I was reducing my email inbox down to zero (miracle of miracles) I noticed that the Last Hope mailing list had an interesting gem. From the email:
I find it a little creepy that they will be able to track my movements at the show. Then again I can tell you exactly my movements. 1) get coffee You get the idea. The first 1500 pre registered attendees will get one of these passes. I’ll be sure to upload some pics as soon as I get it in my hands. For more of this check out the Last Hope website. |
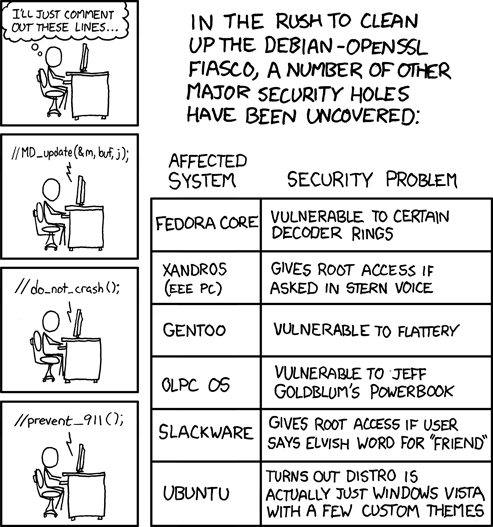
| xkcd on the Debian issue [Emergent Chaos] Posted: 16 May 2008 04:40 AM CDT |
| xkcd: Security Holes [Network Security Blog] Posted: 15 May 2008 11:19 PM CDT Not to be outdone by Dilbert, xkcd has it’s own Debian related humor today. Who ever thought that the words “encryption” and “humor” would apply to the same blog post. |
| Yahoo Search Security Beta Draws Ire [Liquidmatrix Security Digest] Posted: 15 May 2008 10:46 PM CDT Ah the growing pains of a new product. Imagine that, it labeled Google as a malicious site. From eWeek:
Could have been worse. Could have been anti competitive behaviour. heh. |
| Let's not ask the experts? [Emergent Chaos] Posted: 15 May 2008 09:51 PM CDT Can Sips at Home Prevent Binges? is a fascinating article in the New York Times. It turns out there's very solid evidence about this: “The best evidence shows that teaching kids to drink responsibly is better than shutting them off entirely from it,” he told me. “You want to introduce your kids to it, and get across the point that that this is to be enjoyed but not abused.”Ironically, the Times decided to ask their readers: "Do you think teenagers drinking wine with their parents at home encourages reckless drinking or more responsible habits with alcohol later in life?" See the sidebar. Without any disrespect to people reading the Times, why would we care what they think about this? We have evidence of what really happens. Why not ask "Why do you think we can't fix a broken law?" or "Would you vote for a candidate who promised to fix these laws?" Relatedly, Adam Barr wrote: I saw an article today about how the Smart ForTwo (that tiny car you see around) had earned top marks in safety tests conducted by the Insurance Institute for Highway Safety. Despite this, the Institute decided to disqualify the car from potentially earning its "Top Safety Pick" designation because it is just too dang small. "All things being equal in safety, bigger and heavier is always better," says the president of the Institute. ("Things that Everybody Knows.")Experts are experts because they have data and the tools to analyze them. That's why we listen to them. When did we become so resistant to science? |
| Uncle Harold and Open Source [Emergent Chaos] Posted: 15 May 2008 08:46 PM CDT  Uncle Harold (not his real name, not our real relationship, and I never even called him "Uncle") was a cool guy who always fixed his own cars. Most of my life, Uncle Harold has been complaining. It used to be you could actually fix a car. You could put things in, take them out, adjust them, tune them, and so on. As time has gone on, cars got electronics in them, then computers, and nowadays an auto mechanic is as much a computer tech with grease under his nails as a mechanic. I never was much into mechanics as a kid. My father wasn't, either, and discouraged me from ever being a mechanic. If he were to read this, he'd deny discouraging me, but he did. All he did was point out that some bit of automotive fluff that caught my eye would literally be high-maintenance, and either you do that yourself or you pay someone else. I eventually did buy a pre-1968 bit of automotive loveliness as part of a quarter-life (okay, third-life) adjustment. The 1968 date is important because that's when the US started requiring pollution controls, safety equipment, and so on that caused the transit of the gloria of Uncle Harold's mundi. For a technologist, a pre-'68 car is utterly amazing because of sublime lack of technology in it. It needs petrol to burn, water to cool, oil to lubricate, and enough electricity to drive the spark plugs. That's it. The first time I tuned a pair of SU carbs, it was amazing fun. I could really understand Uncle Harold's irritation. The tenth time it was far less fun, partially because I'd gotten good at it. It was just a chore. I could really understand my father's point of view even better. Eventually, the antique bit of fluff got sold and I got a modern fun car that has computers that run everything from engine to brakes. It's really sort of sad that I can't tune the carbs (which of course I don't have; it's all fuel-injected). It's even amusing that if you pull the power from the car, the computers lose their state and they they have to re-tune the ignition system, over the next few miles you drive -- in a wtf sort of way. I mean, haven't these people heard of flash? How much space does it take to store ignition settings and radio presets? (Yes, Uncle Harold, a real radio stores its presets mechanically. Thanks.) But it's really wonderful that I don't have to tune the carbs. There are reasons why those wonderful old systems were replaced. The new ones really are better. Uncle Harold thinks the world has gone to hell in a hand basket. I see the merit in what he says, but when it comes right down to it, I prefer my present hell to Uncle Harold's heaven. The brilliant Ivan Krstić has recently written about the transit of his own personal gloria, the OLPC project. In part of his essay, he shows clearly about how some open source people, in particular RMS, have become Uncle Harold, insisting that if you can't tune those metaphorical carbs, it's like forcing people to be crack addicts. (And this is paraphrasing, not misquoting RMS.) Krstić also talks about the same Haroldisms. He says:
I know exactly what he means. Once, long ago, I'd fire up my GosMacs session in the morning and close it down when I'd go home. I and my colleagues had so customized our editors (which we lived in) the we said that using someone else's emacs was like using someone else's toothbrush. It's just not done. When the Story of Mel came out, one of my coding buddies read it and it really creeped her out. She sent out an email to all of us that said, "Oh, my God, that's my *DAD*!" I once patched a running CVAX just to watch it fly. I admit that I did it because of the smart remark in Dungeon. And I've changed my unices so many times I don't know what I look like. Like me, Ivan's stopped being Uncle Harold with computers. I like being able to get grungy, but I also hate having to. The last remnant of my Uncle Haroldism is my main server that's running FreeBSD. I am especially glad this week that I listened to Ben and didn't put Ubuntu on it. I'm even chafing at that system and asking myself why I don't just outsource the whole damned thing. I'd tell you, but then you'd see my tinfoil hat. (Oh, all right. If you run your own mail server, they can't NSL your sysadmin. I know what you're going to say. I've said it myself. Hush.) Nonetheless, the Uncle Harolds of the world have a point. It's nice to be able to change your kernel. It's nice to be able to recompile everything. It's just a drag to have to. When Open Source realizes that, it will make great strides to getting back people as non-technical as Ivan. And yeah, Ubuntu's getting close, I know that. I actually do love puttering around, but another prop has occupied my time. Photo courtesy of Light Collector. |
| Difficult exploits [Liquid Information] Posted: 15 May 2008 03:52 PM CDT Dave Aitel has some comments on academic research, focusing mainly on the paper on automatic patch-based exploit generation (APEG) and about the differences how academic researchers versus security researchers (might) think. Dave is right that exploiting things has gotten more difficult, a year or so ago I tried to test exploiting a very simple stack-based buffer overflow vulnerability in Linux but due to protections it didn't turn out so well. |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |


No comments:
Post a Comment