Spliced feed for Security Bloggers Network |
| On braces, baseball and Fathers Day [StillSecure, After All These Years] Posted: 14 Jun 2008 10:08 PM CDT  Image via Wikipedia So it is quite an exciting Fathers Day weekend here at the Shimel house. On Friday my oldest son Landon, 8, had braces put on his top teeth. I know that 8 is early for braces, but evidently today they do this as a "Phase 1", so that hopefully he won't need them as long later on. Seeing my little boy come out of the room with braces was quite a sight. Unlike the trauma that kids had about braces when I was younger, he thought it was awesome. The picture to the left are not his braces. Landon's are black and gold, Steeler braces. In 6 weeks they will change them to Yankee blue and white. Braces have certainly come a long way since I was a kid. But my son Landon has come a long way too. Looking at him with his braces and talking to the office staff I realized that the little, fuzzy red headed baby we brought home from the hospital almost 9 years ago now has grown into quite a boy. Where is the little toddler that I would toss a sponge ball to underhand and tell him to use two hands to catch? Could this kid with the catchers mitt catching everything I throw at him and firing it back to me be that baby? Saturday is a day filled with both boys. I am taking Landon and Bradley to breakfast and than off to Baseball City to practice our hitting and pitching. Then Bradley has a birthday party he is invited to and Landon and I will go swimming. Sunday Landon has a travel baseball team game at 10am. Landon was selected for the team because of the great season he had in Little League and is now in tournaments for the next few weeks. Than we are all going to visit my Uncle and Aunt for Fathers Day at the house near the water with a pool. I could not think of a better way to spend my Fathers Day weekend. My mother-in-law always used to say that she was the richest woman in the world because of the treasure that were her children. When I was younger I laughed but would have taken the cash. As I have grown older and have had a chance to watch my boys grow up and have come to understand what it truly is to be a Father, I know that she was right. There is nothing like the love of a child and watching, helping and sharing in their adventure that is life. To all of you celebrating Fathers Day this year whether as a Dad with your own kids or with your own Dad, congratulations and savor every minute of it. Happy Fathers Day! |
| More Preggie Pics Posted [The Falcon's View] Posted: 14 Jun 2008 06:14 PM CDT |
| Compliance abuse [IT Security: The view from here] Posted: 14 Jun 2008 05:06 PM CDT Vendors talk about PCI so much that the reality gets skewed, walking around RSA or InfoSec this year, you could have been forgiven for thinking that PCI was a problem that could be fixed with software. Certainly some software may be able to help with a couple of point of PCI, but there are a couple of issues I have with this vendor approach. Firstly, presenting PCI as a problem, along with other FUD. FUD is so 90s, so Chicken Little. Security has got stuck in a rut in the 00s because we've spent so long saying the sky's going to fall in. When it didn't, no-one believed us any more, and had to try and make up their own minds. Now the people who stand out are the ones who say the opposite - who say that they can actually aid your business, help it to make money. In fact, that's always been a way to make money from software, it's just that using compliance as part of FUD has detracted from the overall value of both security and compliance. Used properly, compliance will make your business run smoothly, without you having to recruit too many specialists. Security will help you achieve that, but here's the second problem. Whereas I have been firmly on the vendor side of the fence for many years now, I can't repeat enough that security isn't all about software. Without decent policies and education security software is near useless. My friends over at the SPSP (Society of Payment Security Professionals) have recently developed the CPISM (Certified Payment-Card Industry Security Manager). It strikes me that this is something long overdue. Developed by Mike Dahn and Heather Mark, two of the biggest names in PCI that I can think of, and with Walt Conway on the advisory board, it's sure to be comprehensive and more importantly, relevant and useful. I can't wait until RSA next year when all the newly qualified CPISMs start asking the questions that Walt and Mike did this year. I'm going to suggest to Mike that he makes this part of the course! |
| Non-Fiction: Steve Martin's Born Standing Up [The Falcon's View] Posted: 14 Jun 2008 04:55 PM CDT |
| Missed This Friday: Tim Russert Dies [The Falcon's View] Posted: 14 Jun 2008 04:21 PM CDT |
| University of Washington Study - Tracking the Trackers [Infosecurity.US] Posted: 14 Jun 2008 01:50 PM CDT Ars Technica reports on an interesting paper by University of Washington Researchers Arvind Krishnamurthy, Michael Piatek and Tadayoshi Kohno examining indirect detection of potential DMCA targets. Utilizing their techniques, they were able to prove their study hypothesis, that indirect detection of P2P targets, can lead enforcements systems to atypical devices not generally associated with storage [...] |
| Boss Conference [Random Thoughts from Joel's World] Posted: 14 Jun 2008 08:26 AM CDT Sourcefire has announced the first BOSS (Best of Open Source Security) Conference. This event will be held in Las Vegas, in February 2009. I'm excited about this conference as it would be fun to work at and see alot of the other people in the Open Source community. I have a few plans for the event, so we'll see. We have an open call for speakers to take part in the conference. For more information on the conference or to submit a speaker application visit: www.bossconference.com |
| Top Posts of the Week [Random Thoughts from Joel's World] Posted: 14 Jun 2008 08:09 AM CDT |
| Links for 2008-06-13 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 14 Jun 2008 12:00 AM CDT |
| One of the Best [BumpInTheWire.com] Posted: 13 Jun 2008 09:24 PM CDT |
| “Loving Customers” [BumpInTheWire.com] Posted: 13 Jun 2008 09:17 PM CDT I don’t know what it is but Alan’s post of “Loving customers frustrate security firms too” just doesn’t sit well with me. Talk about biting the hand that feeds you? Wow. Its this exact reason that I have a real problem with 90% of all “sales” people. 1. The guys who picked the product leave and the new guy comes in and doesn’t have a clue. Are you kidding me? You don’t care. Your sale is made and commision is collected. I really don’t know how this can frustrate a vendor. Its not the company’s fault if a person leaves or gets promoted to different position. If this “frustrates” a vendor than I say “tough titty said the kitty.” That’s part of the game, don’t bitch about it. 2. Buying the product and then “other priorities” delay implementation. Really? You don’t care. If you do care its only because you have resources commited to the implementation and that may hamper future scheduling. I wish I could schedule every task I had to do. That’s not the real world. You’re not in the trenches. We take 20 “grenades” a day. Everybody has their own emergency that prevents us working on what really needs to be worked on. I wish I could plan to be on-site for three days and then walk away. 3. Using the product in unintended ways. This one I might buy. Although I have to think that Alan’s example has to be somewhat rare. Maybe I am niave but I’ve worked for several companies and never has this been done or even considered for any product. It just seems odd to me to complain about customers in one post and then as a ”customer” complain about a vendor in another. |
| New video podcast posted [Got the NAC] Posted: 13 Jun 2008 06:43 PM CDT Tawnee Kendall and I sat down and recorded this video on the future of network security. Check it out! Tags: General, general, network security |
| Verizon 500 breach report [Errata Security] Posted: 13 Jun 2008 04:22 PM CDT Verizon has published a study of 500 investigations over the last 4 years. There are some obvious flaws (pie charts are never a good sign), but it's got a lot of useful content. The industry is full of misconceptions because people don't pay attention to what's really going on out there. This report has data the answers a lot of questions. Misconception: "the standard way to take control of someone else's computer is by exploiting a vulnerability in a software program on it" Verizon data: Only 15% of breeches where from hacking software vulnerabilities. Misconception: Hackers target their victims. Verizon data: 85% of attacks were "opportunistic", the hackers didn't know who their victims were until after they broke in. Misconception: Certified anti-virus products detect over 99% of all viruses. Verizon data: 25% of viruses/malware were customized to their victims and undetectable with standard anti-virus. Misconception: Hackers are smart, clever, geniuses, wizards, etc. Verizon data: 55% where of attacks required essentially no skills, the level of "script kiddies" running automated tools. Only 17% required "advanced" skills. Misconception: It's the insider threat. No, wait, it's outsiders. No, I mean, it's the partners. Verizon data: 73% external, 18% internal, 39% partners. However, external breaches tended to be minor, whereas internal and partner breeches were major. Their numbers show that all three are important threats and that it's hard to measure which one is worse. Misconception: Numbers are definitive. Verizon data: These numbers are bit subjective. For example, they notice that "physical breaches" were rare, but that's because Verizon wouldn't be called in to investigate a physical breach. Question: What are hackers after? Verizon data: Credit Card data (84%), Personal identity (32%), Username/passwords (15%) Question: How old are the vulnerability exploits hackers use? Verizon data: 71% older than 1-year, another 19% older than 6 months. |
| Variable Bitrate Compression Flawed [Voice of VOIPSA] Posted: 13 Jun 2008 03:14 PM CDT Some researchers over at Johns Hopkins University have discovered that due to the way Variable Bitrate Compression does it’s thing, even if the audio stream is encrypted it is still possible to determine entire words and phrases based on the lengths of the packets with a high degree of accuracy. According to the article referenced above it appears that the proof of concept tool is fairly limited, but given a little time and additional effort it’s capabilities could be greatly expanded, potentially to the point of transcribing entire conversations. The researchers’ paper was presented at the 2008 IEEE Symposium on Security and Privacy a few weeks ago. |
| My Monster Name [The Falcon's View] Posted: 13 Jun 2008 02:39 PM CDT |
| Security Briefing: June 13th [Liquidmatrix Security Digest] Posted: 13 Jun 2008 12:38 PM CDT  Friday the 13th. Well, it was apparently worse than I thought at Infosecurity Canada. I spoke with eight people that attended and all of them gave it a unanimous thumbs down. Too bad. I guess if they were better organized it wouldn’t have sucked that badly. Click here to subscribe to Liquidmatrix Security Digest!. And now, the news… (better late than never)
Tags: News, Daily Links, Security Blog, Information Security, Security News |
| Maltego Community Edition Released [Liquidmatrix Security Digest] Posted: 13 Jun 2008 10:05 AM CDT 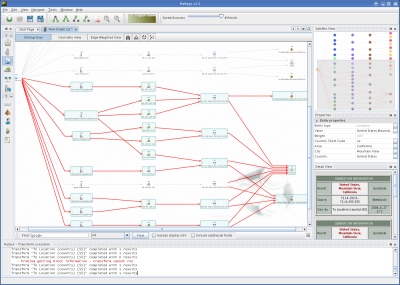 From Paterva dot com: The Community Edition is limited in the following ways: * A 15second nag screen http://www.paterva.com/maltego/community-edition/ |
| E-crime Unit On Track, Says Police Chief [Liquidmatrix Security Digest] Posted: 13 Jun 2008 09:51 AM CDT The Policing Central e-Crime Unit (PCEU) is apparently full steam ahead but, the author of this next article points out one minor detail. Where’s the funding? From Silicon dot com:
Read on. |
| You are subscribed to email updates from Black Hat Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Black Hat Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |

No comments:
Post a Comment