Spliced feed for Security Bloggers Network |
| PGP Source Code Book on eBay [Infosecurity.US] Posted: 18 Jun 2008 07:44 AM CDT A small, yet powerful piece of encryption history is being auctioned off on eBay, an original set of exported source code of Phil Zimmerman’s PGP 5.0. As of this post, the eBay auction is now at 18 bids, for a high bid of $102.50 USD. For those that are unfamiliar with the history of these books, [...] |
| Microsoft: June Security Bulletin Released [Infosecurity.US] Posted: 18 Jun 2008 07:42 AM CDT |
| Sei un professionista di sicurezza se... [varie // eventuali // sicurezza informatica] Posted: 18 Jun 2008 07:26 AM CDT InfoWorld: Are you a computer security professional ? Ehm, si, lo sono. Ho il cellulare con la password, il mio firewall blocca molte applicazioni genuine, non mi allontano dal PC se non l'ho bloccato, correggo i libri di sicurezza, mi preoccupo delle vulnerabilitá del mio GPS, non installo nulla di nuovissimo, ho il privacy screen che quello accanto non vede il mio schermo, preferisco usare la mia chiavetta USB. |
| TS/SCI security is first [StillSecure, After All These Years] Posted: 18 Jun 2008 07:09 AM CDT ts/sci security blog is the first SBN member out of the blocks to blog on our Black Hat Security Bloggers Network topic of interest and it is a great one! Thanks to dre! I was afraid none of our bloggers would pick up on this but am looking forward to seeing more on virtualization and Hoff's discussion at Black Hat. |
| The security sales conundrum [StillSecure, After All These Years] Posted: 18 Jun 2008 07:01 AM CDT I spent this week on a tour of StillSecure customers speaking to them about security, their jobs and what would make their lives easier. One thing that I heard consistently from them was that they are overwhelmed with security vendors barraging them. Be email, phone or postal mail it just doesn't stop. They don't answer their phones and don't even know where these vendors get their names. Mr Bump in a recent comment on my blog about the used car salesman of NAC says this is another example of why he is just fed up with sales people. I hear all of this loud and clear and will be sure to pass this along to our on sales and marketing teams. However, it begs the question of how are security vendors supposed to contact and sell their products? Should security vendors just sit their and wait for the phone to ring with questions or orders? Would you prefer that all sales people are highly technical and just talk bits and bytes with you? How will you find out about new products and services? For all of the bellyaching and moaning about sales and marketing overload, it would seem that if it was not successful, vendors would not do it. I would like to hear from you. How would you like to see vendors contact you? What do you think the sales process should look like? I don't think sales people want to be a pain in the butt and for the most part don't want to blow smoke up anyones butt. What do you think? Leave a comment and be heard. The time you save dealing with annoying sales tactics may be your own. |
| WikiScanner - Find Interesting Anonymous Edits on Wikipedia [Darknet - The Darkside] Posted: 18 Jun 2008 01:18 AM CDT Now this isn’t a new tool, and it’s not quite up to date as the author hasn’t updated it for a while - but it’s still exceedingly cool! As you know most IP addresses are registered to companies or organizations in blocks, so you can identify which network an edit is coming from as Wikipedia logs [...]SHARETHIS.addEntry({... Read the full post at darknet.org.uk |
| Google secrecy - a bad thing? [Roer.Com Information Security - Your source of Information Security] Posted: 18 Jun 2008 12:57 AM CDT I came by this comment over at The Register today, by Ashlee Vance. Ashlee is asking why Google keeps it's power saving tweaks a secrecy on one hand, and promote itself as an environmental friendly company on the other hand.
"If Google is actually successful at lowering power consumption, then the secrecy makes sense." Ashlee writes. Before rambling on about how Google (and Intel too) should share it's secrets with everyone else so we could save power and make a greener world. And yea, I agree that in a perfect world, that would be nice. But this is not a perfect world, this is a competitive and commercial world where money speaks. And in my head that means that if you have made some tweaks that increases your productivity without increasing the power consumption, you would keep those to yourself as long as you possibly can. That is how it stays a competitive advantage. If you share it, then it no longer is an advantage. What impresses me with Google is the fact that their engineers (at all levels) seems to share a very high level of security awareness, particularly when it comes to value of information. Of course, information is the core value of Google, but how often do you meet a company where the culture and knowledge about what to share and what not to share - even accidently - is so evident? I am impressed. I think that what Ashlee and the rest of us should do is learn from Google. Learn how to define the core values, and the core information, in the company, and then keep them to yourself! --- Before you shoot your green arrows at me, I do care about the environment. I just do not see why buzzwords like the environment should be mixed up and used as an excuse to force companies to give up their core information. Stick to your point - or leave it be. Hmm...How many Penguins did I just kill? And bummer, I did not make any money either... |
| Black Hat Bloggers Network topic of interest [StillSecure, After All These Years] Posted: 18 Jun 2008 12:11 AM CDT
Our first topic comes to us from an SBN member who will be presenting at Black Hat. It is one of our resident big brains, Chris Hoff talking about virtualization and security. I asked Chris to give me a quick write up on what he is presenting and here it is: Despite shiny new stickers on the boxes of our favorite security vendors' products that advertise "virtualization ready!" or the hordes of new startups emerging from stealth decrying the second coming of security, there exists the gritty failed reality of attempting to replicate complex network and security topologies in virtualized environments. This talk will clearly demonstrate that unless we radically rethink our approach, the virtualization security apocalypse is nigh! We will focus on both securing virtualization as well as virtualizing security; from virtualization-enabled chipsets to the hypervisor to the VM's, we'll explore the real issues that exist today as well as those that are coming that aren't being discussed or planned for:
You can read more on this at Chris's blog here. So bloggers here is the deal. You have what Hoff thinks, what do you think. Wrap your heads around virtualization and security and lets hear what you have to say. We will all be reading! ON YOUR MARK, GET SET, BLOG!
|
| Pink Slip Virus 2008 [securosis.com] Posted: 18 Jun 2008 12:00 AM CDT This is a very scary thing. I wrote a blog post last year about this type of thing in response to Rich’s post on lax wireless security. I was trying to think up scenarios where this would be a problem, and the best example I thought of is what I am going to call the “Pink Slip Virus 2008″. Consider a virus that does the following: Once installed, the code would periodically download pornography onto the computer, encrypt it, and then store it on the disk. Not too much, and not too often, just a few pictures or small videos. After several weeks of doing this, it would un-encrypt the data, move it to “My Documents” or some subdirectory, and then uninstall itself. It could be programmed to remove signs that it was present, such as scrubbing log files to further hide from detection. The computer could be infected randomly through a hostile web site or it could be targeted through an injection attack via some insecure service. It could even be targeted by a co-worker who installed this on your machine when you were at lunch, or loaned you an infected memory stick. A virus of this type could be subtle, and use so minimal CPU, network, and disk resources so as to go unnoticed both by the owner of the computer and the IT department. Now what you have is presumed guilt. If the downloads are discovered by IT, or someone like the malicious co-worker were to proactively mention to HR “I saw something that looked like …” on or after the date the virus uninstalled itself, a subsequent search would reveal pornography on the machine. Odds are the employee would be fired. It would be tough to convince anyone that it was anything other than the employee doing what they should not have been doing, and “innocent until proven guilty” is a legal doctrine that is not applied to corporate hiring/firing decisions. I was discussing this scenario with our former Director of Marketing at IPLocks, Tom Yates, and he raised a good point. We routinely use Occam’s Razor in our reasoning. This principle states that the simplest explanation is usually the correct one. And the simple explanation would be that you were performing unauthorized browsing with your computer, which could have negative legal consequences for the company, and is almost always a ‘fire-able’ offense. How could you prove otherwise? Who is going to bring in a forensic specialist to prove you are innocent? How could you account for the files? I have had a home computer infected with a BitTorrent-like virus storing such files on a home computer in 2003, so I know the virus part is quite feasible. I know that remote sessions can be used to instigate activity from a specific machine as well. It is a problem to assume the person and the computer are one and the same. We often assume that you are responsible for specific activity because it was your IP address, or your MAC address, or your account, or your computer that was involved. Your computer is not always under your control, passwords are usually easy to guess, and so it is a dangerous assumption that the official user is responsible for all activity on a computer. Almost every piece of software I have ever downloaded onto my machine takes some action without my consent. So how would you prove it was some guy looking at porn and not spammers, hackers and/or the malicious co-worker? |
| Links for 2008-06-17 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 18 Jun 2008 12:00 AM CDT
|
| Another brick in the wall to limit blogging [StillSecure, After All These Years] Posted: 17 Jun 2008 11:43 PM CDT
I think that it is a really short sighted move by the AP. First of all it shows they really don't understand blogging. Blogging is about taking an idea which often comes from another source and putting the bloggers own spin and ideas behind it. In this way topics are built on one blog at a time with each blogger adding a bit more to the conversation. Each additional blog on topic enriches those blogs and articles that preceded it. As I said in the Channel Web article, it is like a jazz musician playing a riff on top of a line already laid down. In real terms blogging on the AP content will only generate more views and interest in the AP content. AP is just a dinosaur with this type of view and will soon go the way of dinosaurs if they try to enforce this. In the meantime bloggers can talk about an AP article, but don't link to it and don't excerpt from it. I suspect that the next thing is we will have a replay of the inbound links litigation we had 8 years ago. In the meantime blogging will continue to march on with AP or not. |
| Posted: 17 Jun 2008 09:55 PM CDT The Federal Bureau of Investigation released an announcement detailing the sentencing, today of Parthasarathy Sudarshan, the principal of an electronics enterprise, in the D.C. court, to 35 months in prison for conspiracy to illegally export controlled electronic components to the Indian Government. The Indian government agencies specified in the original complaint directly engage in [...] |
| Network Security Podcast, Episode 108 [Network Security Blog] Posted: 17 Jun 2008 09:03 PM CDT Back to just Rich and I this week. We’re both running around like chickens with out heads cut off, so we were lucky to be able to get a show in this week. Coordinating with a guest would have been more than we could handle. I’m sure we’ll be back to a more normal schedule next week. More ‘hoping’ than ’sure’, but only one way to find out. Show Notes:
Network Security Podcast, Episode 108, June 17, 2008 Time: 30:49 This posting includes an audio/video/photo media file: Download Now |
| Interactive map: what a botnet looks like [Security4all] [Belgian Security Blognetwork] Posted: 17 Jun 2008 07:37 PM CDT |
| Where oh where has my little blogger gone? [Branden Williams' Security Convergence Blog] Posted: 17 Jun 2008 07:23 PM CDT I haven't written, called, emailed, faxed, or even sent you guys anything via carrier pidgeon. For that, I grovel at your feet and request my penance (tee hee, I love the occasional translation error, especially when it reminds me of the most beautiful thing I have ever seen). What have I been up to? Last week was fun. Boston & Cincinnati in two days. Was great seeing many of you out there! Especially when a coworker and I started eating at the wrong party! This week, so far, I have met with the Visa CISP and Incident Response teams over two days, and I am headed home to fly out to Atlanta for a couple of customer meetings. If you are in town, drop me a line! Some PCI News for you... The PCI Security Standards Council has announced their community meetings for 2008. We will be there! They have also announced training dates for PA-DSS assessors. I'm off to DFW! |
| “My Tax Returns Were on There!” - Woman Sues for $54 Million [IceLock Blog] Posted: 17 Jun 2008 07:01 PM CDT Here’s an interesting story that shows another way that targeted encryption systems, like IceLock, (as opposed to Full Disk Encryption) can really be useful. Here’s the background: A woman sent in her laptop for servicing to Best Buy. They lose her computer, and after making her jump through some irritating hurdles, the offer her a gift certificate to partially defray the cost of replacing the hardware. She then sues Best Buy for $54 million simoleons on the basis of their failure to notify her that her personal information had been compromised. Best Buy’s customer service shenanigans aside, this points out an interesting potential application of encryption systems. If she had a secure partition on her system, she could have saved her sensitive documents, including her tax returns, in the encrypted partition, and had perfect peace of mind that her confidential personal information would stay confidential. If she were using IceLock, she could also perform a secure, audited delete when the system next connected to the Internet. Here’s another idea: what if service operations like Best Buy’s required confidential information on systems to be encrypted before taking them in for servicing? Here’s a point to ponder: If she were using a Full Disk Encryption, like PGP, BitLocker, TrueCrypt or the like, she would have had to give up her password to get the system serviced. The machine is at that point out of her control, and compromised. And she has no way to effect a clean wipe remotely. |
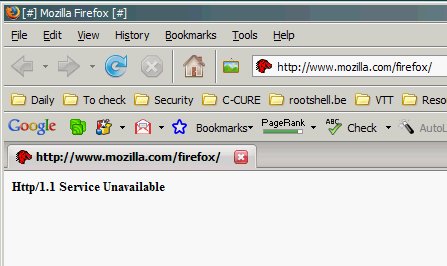
| Firefox 3 goes live and suffers some small downtime [Security4all] [Belgian Security Blognetwork] Posted: 17 Jun 2008 06:43 PM CDT |
| The highest form of flattery. [NP-Incomplete] Posted: 17 Jun 2008 04:58 PM CDT Juan Caballero, Theocharis Kampouris, Dawn Song, and Jia Wang published some interesting extensions at this year's NDSS of the work presented by Harish Sethu and me at CCS '04. Both papers examine the software diversity problem, which states that networks of systems would be more secure if they minimized the number of possible common mode faults by running different software and operating systems, by relating it to the graph coloring problem. The thesis of both papers is that software diversity can be improved by using graph coloring algorithms to maximize diverse software allocation. This title of this post's implication is only in jest, as I am incredibly happy to see our idea extended by the research community. |
| Doing my part to help Mozilla [Network Security Blog] Posted: 17 Jun 2008 02:45 PM CDT I’m doing my part to help Mozilla and I’m downloading Firefox 3.0 onto all of my systems at home today. I haven’t installed it yet, but I’m downloading it. Are you helping Mozilla make it into the Guinness Book of World records for greatest number of downloads in one day? |
| Fun Reading on Security - 4 [Anton Chuvakin Blog - "Security Warrior"] Posted: 17 Jun 2008 01:36 PM CDT Instead of my usual "blogging frenzy" machine gun blast of short posts, I will just combine them into my new blog series "Fun Reading on Security." Here is an issue #4, dated June 17, 2008. So my next iteration of fun reading on security, logging and other topics.
|
| Allo Mozilla? [/dev/random] [Belgian Security Blognetwork] Posted: 17 Jun 2008 01:14 PM CDT
Firefox 3 is out! It seems that the World Record of downloads in 24 hours will be difficult to accomplish… |
| Who Still Remember Usenet? [/dev/random] [Belgian Security Blognetwork] Posted: 17 Jun 2008 01:07 PM CDT
A page of the Internet history will maybe be turned off soon. Three major ISPs in the United States (Verizon, Sprint and Time Warner Cable) announced they will stop access to Usenet! (or access will be limited to the Big-8). The youngest of us have probably never used a “newsreader” to access Usenet via the NNTP protocol (already available before the World Wide Web). A few years ago, it was still a classic way to find help over thousands of topics (from IT issues to fishing or cooking). Today, Usenet (the newsgroups) are accessed via Google Groups or online tools. But Usenet is still used by the “underground”. On Usenet, you can find almost all movies, MP3 albums or application via the well-known “alt.binaries.*” branch. Even more, it’s a method of file sharing which is unknown by most of the young surfers. Less known, discreet, fast… a perfect way to exchange illegal material. That’s why Usenet is at risk at the moment. Maintaining a Usenet feed is also very expansive in bandwidth and storage for an Internet provider: 400 GBytes of data per day! |
| Do you know what a Host Protected Area (HPA) is? [Robert Penz Blog] Posted: 17 Jun 2008 01:02 PM CDT It is sometimes also called Hidden Protected Area and it is an area of your hard disk which is normally not visible for the operating system and therefore the applications. It was first introduced in the ATA-4 standard and is defined in ATA-5 as optional feature which is supported by most modern hard disks. The normal use case of this is for system recovery and the backup of important configuration data. So why is this security relevant? For law enforcement agencies and forensic experts it is important to detect HPAs and recovery data from it. For one someone could hide some sensitive data in it or there could be evidence or traces if the owner does not know about the HPA. But it is also important for any business and home user, e.g. if you want to fully override your hard disk you need to make sure you also override the HPA. If you’re a user of a current Linux kernel you’re lucky - the kernel will deactivate (temporary) the HPA during booting and so can override everything without problems. Here are some links which will help you do detect / remove the HPA from your hard disk:
|
| How much work is writing a book? [Emergent Chaos] Posted: 17 Jun 2008 12:14 PM CDT There's a great (long) post by Baron Schwartz, "What is it like to write a technical book?" by the lead author of "High Performance MySQL." There's a lot of great content about the process and all the but I wanted to respond to this one bit: I can’t tell you how many times I asked people at O’Reilly to help me understand what would be involved in writing this book. (This is why I’m writing this for you now — in case no one will tell you, either). You would have thought these folks had never helped anyone write a book and had no idea themselves what it entailed. As a result, I had no way to know what was realistic, and of course the schedule was a death march. The deadlines slipped, and slipped and slipped. To November, then December, then February — and ultimately far beyond. Each time the editor told me he thought we were on track to make the schedule. Remember, I didn’t know whether to believe this or not. The amount of work involved shocked me time after time — I thought I saw the light at the end of the tunnel and then discovered it was much farther away than I thought.I think this is somewhat unfair to the O'Reilly folks, and wanted to comment. Baron obviously put a huge amount of effort into the work, but O'Reilly has no way of knowing that will happen. They run a gamut in second editions from "update the references and commands to the latest revision of the software" to "complete re-write." Both are legitimate ways to approach it. It could take three months, it could take a few years. O'Reilly can't know in advance. (Our publisher has told me horror stories about books and what it's taken to get them out.) So O'Reilly probably figures that there's a law of diminishing returns, and pushes an insane schedule as a way of forcing their authors to write what matters and ignore the rest. So it's not like a baby that's gonna take 9 months. Andrew and I opened the New School of Information Security with a quote from Mark Twain which I think is very relevant: "I didn't have time to write you a short letter, so I wrote you a long one instead." We took our time to write a short book, and Jessica and Karen at Addison-Wesley were great. We went through 2 job changes, a cross-country move, and a whole lot of other stuff in the process. Because we were not technology specific, we had the luxury of time until about December 1st, when Jessica said "hey, if you guys want to be ready for RSA, we need to finish." From there, it was a little crazy, although not so crazy that we couldn't hit the deadlines. The biggest pain was our copy-edit. We'd taken the time to copy-edit, and there were too many changes to review them all. If we'd had more time, I would have pushed back and said "reject all, and do it again." So there's no way a publisher can know how long a book will take a new set of authors, because a great deal of the work that Baron Schwartz and co-authors did was their choice. |
| Code Development and Security [securosis.com] Posted: 17 Jun 2008 12:00 PM CDT How do we know our code is bug free? What makes us believe that our application is always going to work? Ultimately, we don’t. We test as best we can. Software vendors spend a significant percentage of their development budget on Quality Assurance. Over the years we have gotten better at it. We test more, we test earlier, and we test at module, component, and system levels. We write scripts, we buy tools, we help mentor our peers on better approaches. We do white box testing, we do black box testing. We have developers write some tests. We have QA write and run tests. We have 3rd party testing assistance. We perform auto-builds and automated tests. We may even have partners, beta customers, and resellers test so that our code is as high quality as possible. We have learned that the earlier in the process we find issues, the less money we spend fixing them (see Deming, Kaizen, Six Sigma, etc.). We have even altered the basic development processes from waterfall to things like extreme and agile methodologies to better assist with quality efforts. We have taken better advantage of object oriented programming to reuse trusted code, as well as distill and simplify code to ease maintenance issues. This did not happen overnight, but has been a gradual process every year I have been part of the industry. We continually strive to get a little better every release, and we have generally gotten better, and done so with fewer resources. None of these strategies were typical 20 years ago when developers were still testing their own code. We have come a very long way. So what, you say? I say software security is no different. We are on the cusp of several large changes in the security industry and this is one of them. Security will come to the “common man” programmer. I was discussing this with Andre Gironda from ts/sci at the SunSec gathering a couple of weeks ago, and how process has positively affected quality as well as how it is starting to positively affect security, along with some of the challenges in setting up suitable security test cases at the component and module levels. Andre put up a nice post on “What Web Application Security Really Is” the other day and he touches on several of these points. Better security needs to come from wholesale and systemic changes. Hackers spend most of their time thinking about how to abuse systems, and your programming team should too. Do we do this well today? Obviously the answer is ‘no’. Will we get better in 10 years, or even 2 years from now? I am certain we will. Mapping security issues into the QA processes, as a sub-component of quality if you will, would certainly help. The infrastructure and process is already present in the development organization to account for it. The set of reports and statistics that we gather to ‘measure’ software quality would be similar in type to those for security … meaning they would both suck, but we’ll use them anyway because we do not have anything better. We are seriously shy on education and training. It has taken a long time for security problems, security education, and security awareness to even percolate into the developer community at large. This has been getting a lot of attention in the last couple of years with the mind-boggling number of data breaches that have been going on, and the huge amount of buzz lately with security practitioners with PCI 6.6 requiring code reviews. There is a spotlight on the problem and the net result will be a slow trend toward considering security in the software design and implementation phases. It will work its way into the process, the tools, the educational programs, and the minds of typical programmers. Not overnight. Like with quality in general, in slow evolutionary steps. |
| Bonehead Information Technology Practices [Infosecurity.US] Posted: 17 Jun 2008 10:11 AM CDT |
| Reuters: Nuclear Secrets Found on Swiss Smugglers’ Computers [Infosecurity.US] Posted: 17 Jun 2008 09:58 AM CDT |
| Major influencers [Network Security Blog] Posted: 17 Jun 2008 09:44 AM CDT I’ve only met Jack Daniel face to face a couple of times, but I must have left an impression to elicit the sort of nice stuff he says in his latest post. “…he’s Martin. Which is pretty cool.” You can’t buy compliments like that. He brings up a good meme though: who’ve you learned a lot from in your career or as a blogger? One of the first people who come to my mind is Richard Bejtlich, partially because Richard was the first security blogger I met face to face. Richard is constantly contributing to the community as a blogger and a teacher and he’s one of the nicest people I’ve ever had the chance to meet. Chris Hoff is on my list as well as Jacks. Chris gives me an idea of what it takes to reach the top tiers of our profession. And a taste of what you can get away with once you’re there. Michael Santarcangelo I see as a true community leader and creator, as well as being a decent co-host for a podcast. And speaking of co-hosts, I can’t forget Rich Mogull, who influences my thinking on a weekly basis. That’s just the short list; I could come up with a dozen more names to add to it in short order. I try to learn from these people and many more on a daily basis. Who has been a major influencer in your career? What are you learning from them? Write a post and link back to Jack. I’m interested in seeing who people have been learning from. |
| Anonymouse proxy now blocked in PRC [The Dark Visitor] Posted: 17 Jun 2008 08:37 AM CDT The well-known (to our regular readers) Chinese media site Danwei linked to a Shanghaiist article that the Anonymouse proxy servers have been blocked in the PRC (along with comedycentral.com apparently). From the article:
Commenters noted that the Hack520 program is the same as the well-known Ultrasurf/Ultrareach system and that although the client program works to anonymously proxy surfing, one needs to use another proxy to get to the download site to get the client to begin with. One of the best client anonymizers out there is TOR, which also still works in the PRC. Interestingly enough, there are many TOR exit nodes inside the PRC, which leads me to wonder: Why would anyone who uses TOR (political dissidents, journalists, pr0n surfers) want to be proxied into a country that most people are trying to get proxied out of? |
| Go ahead, be a Tiger [StillSecure, After All These Years] Posted: 17 Jun 2008 08:25 AM CDT  Image via Wikipedia I stink at golf. I don't play often enough to get better and I wasn't good to begin with. But regardless of whether you are a good golf player or not, you can appreciate greatness. We were in the presence of greatness this weekend and yesterday watching Tiger Woods storm to his latest US Open victory. Of course Tiger has won these before, but this one may have been his greatest yet. Coming off of knee surgery, limping up and down the course, Tiger made so many amazing shots that you almost expect him to make the impossible. Coming back on the 18th hole on Sunday to tie it, then a nail biter 18 hole playoff today, only to win it in an extra death 19th hole Tiger Woods has once again confirmed that he may be the best money player of his generation, if not of all time. But Rocco Mediate played for all of us over 40-somethings, that you can still play with the big boys and give them a run for their money. Good for Rocco too! It is about time someone gave Tiger a run. At the end of the day though we should all realize how special it is that we get to watch Tiger week in and out. Much like watching Babe Ruth or Mickey Mantle, we may not truly appreciate how luck we are being able to watch Tiger, until we can't watch him anymore. So like the commercial says, "Go on, be a Tiger"! |
| You are subscribed to email updates from Black Hat Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Black Hat Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |

 This post is intended to member of the Black Hat Bloggers Network and others who blog on security. When we announced our affiliation with the Black Hat folks, we said that between now and the show in August we would pick topics of interest tied to presentations at Black Hat for us to "shine a light on". With over 150 blogs in the network, if even a small percentage of us write on one particular topic that should be quite a concentration. I am looking forward to see the many different tangents our members will take these topics.
This post is intended to member of the Black Hat Bloggers Network and others who blog on security. When we announced our affiliation with the Black Hat folks, we said that between now and the show in August we would pick topics of interest tied to presentations at Black Hat for us to "shine a light on". With over 150 blogs in the network, if even a small percentage of us write on one particular topic that should be quite a concentration. I am looking forward to see the many different tangents our members will take these topics. 





No comments:
Post a Comment