Spliced feed for Security Bloggers Network |
| Freeware of the day WinSCP [belsec] [Belgian Security Blognetwork] Posted: 11 Aug 2008 07:00 AM CDT WinSCP is a SFTP client and FTP client for Windows. Its main function is the secure file transfer between a local and a remote computer. It uses Secure Shell (SSH) and supports, in addition to Secure FTP, also legacy SCP protocol. Development Status : 5 - Production/Stable Intended Audience : Developers, End Users/Desktop, System Administrators License : GNU General Public License (GPL) Operating System : 32-bit MS Windows (95/98), 32-bit MS Windows (NT/2000/XP), All 32-bit MS Windows (95/98/NT/2000/XP), Win2K, WinXP Programming Language : C++ Topic : Communications, File Transfer Protocol (FTP), Cryptography Translations : Catalan, Czech, Dutch, English, Finnish, French, German, Hungarian, Indonesian, Italian, Japanese, Malay, Polish, Portuguese, Russian, Spanish, Swedish | |
| Posted: 11 Aug 2008 06:52 AM CDT This is the description of the vulnerability of your DNS BIND server if you don't put the patch - even if this won't defend you against persistant targeted attacks - especially if you are still recursive DNS - which is just STUPID - if I may say so. "Look. We were looking at an attack before the patch that took ten seconds and was relatively invisible. " Test your DNS server, just go there and if they are still vulnerable, give that stupid admin a mail or someone else if he is on holiday source http://www.doxpara.com/ https://www.dns-oarc.net/oarc/services/dnsentropy I think we will be blacklisting poisoned or non-patched dns servers soon - especially if they are recursive. The risks are too high. | |
| Surf Jacking [un-excogitate.org] Posted: 11 Aug 2008 06:11 AM CDT Just finished reading about Surf Jacking from Ronald van den Heetkamp (and Sandro Gauci and Mike Perry), the demonstration movie that Sandro published really set in stone how interesting this vulnerability is. Sandro’s whitepaper describes the attack in detail, the primary attack scenario being the following:
The first thing I did after reading this paper was to check my online banking, and I was relieved to see that the session cookies sent by the server were set to “Encrypted Only”. | |
| Patch Now - What Does it Mean? [Last In - First Out] Posted: 11 Aug 2008 06:03 AM CDT When security researchers/bloggers announce to the world 'patch now', are they are implying that the world should 'patch now without consideration for testing, QA, performance or availability'? Or are they advising an accelerated patch schedule, but in a change managed, tested, QA'd rollout of a patch that considers security and availability? And when they complain about others not patching fast enough, are they assuming that the foot draggers are incompetent? Or are they ignoring the operational realities of making untested changes to critical infrastructure? Consider that:
But when security people push recommendations out to the world without consideration for availability and/or performance, their recommendations remove value from the Internet community. Security Researchers add value when
In that context, when I hear 'patch now' advice, You can bet that I will filter the advice through the prism of availability, performance and operational reality.
The bottom line is that unless the people who give the world advice to 'patch now no matter what' are also going to write my e-mail's and presentations explaining why my systems failed, unless they will absorb the inevitable backlash from customers, senior management, governing boards and will stand up in front of representatives from my internal business units and get grilled, castigated, chewed up and spit out for my decision, I don't need them to complain that I am not 'patching now'. I've been in the 7pm vendor conference call with vendor VP and development supervisor, where our CIO came to the meeting with his/her letter of resignation, to be turned in to our CEO should the vendor fail to deliver performance fixes for the business critical application by 7am the next day. It was not a fun meeting. 'Patch now' advice must be filtered through the prism of availability, performance and operational reality. | |
| Posted: 11 Aug 2008 06:02 AM CDT They do not seem to be updated for the moment, but I think they are doing everything they can to keep them online and back. I presume the updates will follow once they think they have everything more or less under control (MIRROR MIRROR MIRROR - If you can mirror those sites contact the Georgian embassy in your country or just download them and set up your own mirrors) You can post the sites where they are mirrored here under if you like) http://www.president.gov.ge/?l=E&m=0&sm=0 the president http://www.mfa.gov.ge/ the Ministery of Foreign affairs the rest is still down or time-outs or whatever - please help them - these are some buttons if you need for your website or blog. Georgia proofs what it is to live as a democratic country next to the Russian bear and not be protected by a democratic shield. I think every young democratic Eastern European or Ex USSR state is now looking what will happen and thinking about what to do next and if they will be next. What westeuropeans sometimes think and say is for them so bizarre and proRussian that it is normal that they look more towards Washington and I understand that.
| |
| Georgian hackers start attacking Russian websites [belsec] [Belgian Security Blognetwork] Posted: 11 Aug 2008 05:48 AM CDT | |
| .be hack of the day corneliusfeesten.be [belsec] [Belgian Security Blognetwork] Posted: 11 Aug 2008 05:44 AM CDT | |
| Posted: 11 Aug 2008 05:22 AM CDT | |
| Posted: 10 Aug 2008 11:49 PM CDT Russia is moving in to Georgia. Is the Big Bear securing it's oil reserves? Are they trying to close the West's access to the Caspian sea? Where will Putin head after Georgia? Is Putin the new Stalin? These and many other questions have surfaced around the world for a while now. To many of us, Georgia is far away, thus the news are easily downgraded on our scale of importance. And this might very well be Putin's exact calculations - that Russia can go out and grab Georgia with little or no reactions from the international communities. I hope that reactions will come. That the international community will raise it's voice and tell Russia and Putin that theft is not acceptable. That Georgia will receive support and help on their path to independence and democracy. In our globalized market, we are all interdependent. That should also mean that we are equally responsible for each other, that we should care and that we need to voice our concerns. Larko opened my eyes - by pointing my radar to the incident. Thus, I changed the filter mode in my brain, and interesting bits of information started to appear. Some of them are listed below. I encourage you to spend a few seconds (as a minimum) to consider the questions I pose above. By spending that little investment of your time, you may find that you need to do something more. If you do, please go ahead! Thanks!
| |
| Dispatches from Blackhat/Defcon: PayPal Token [NP-Incomplete] Posted: 10 Aug 2008 11:10 PM CDT Paypal placed this item in everyone's BlackHat backpack. This second-factor authentication token, which really should be far more common for consumer websites, has to be the best piece of swag I have ever received in the conference fun bag. | |
| Blogging Defcon [Digital Bond] Posted: 10 Aug 2008 10:46 PM CDT There wasn’t a whole lot to report from the last few days of Defcon, as most of the presentations there don’t directly relate control systems or SCADA. But there were a few standouts in regard to network security in a more general sense. Errata’s presentation on using the iPhone was an interesting idea, and seems like it was well executed. For control systems this kind of attack serves as a good reminder that security within the perimeter (physical not network) is just as important. An open wireless access point in the middle of a large secured area could be compromised by a device mailed in. Essentially this boils down to the same arguments against using telnet and other clear text protocols internally. They do provide some convenience but probably aren’t worth the risk. Ian Angel, Professor of Information Systems at the London School of Economics, did a fantastic presentation, essentially a repeat of the day one keynote for Blackhat, and I can’t say enough about how good it was. A description won’t do it justice, and your time will be well worth it to watch the videos when they’re posted up. Lots of humor, lots of attacks on statistics and those who prepare them, and overall a very good contradictory voice in the academic community that often is a bit of the mark from the real world. Ben Feinstein gave a great presentation on Snort plugins, and shed some light on an area that isn’t exactly unknown, but where documentation has been lacking for quite a few years. Great example code, and may spur some more low level development, custom rule writing has been very popular for years and a number of companies have it as a significant part of their business model, but custom preprocessors and plugins are all too often uncharted territory. As Dale already mentioned many in the Modbus presentation were unimpressed. No real need to go into further details, most of the information could have come from open sources and no new breakthroughs were presented. There was a small amount of drama, which always tends to occur along with security conferences on the fringe, and reporters and pundits on all sides are already chiming in. Apparently a group of MIT students were set to give a presentation of weaknesses common in the fare collection system of subway systems, but were given a court order not to. However the presentation materials were already present on the CDs given out with registration to the conference. I’ve read over the presentation, and it's interesting, the systems they examined used very insecure methods of tracking fare and lot of other things. Good research, but seems like they really left the Boston subway operators no choice when looking at that kind of financial loss. I’m betting there will be more on this in the next few days. I also spent a good bit of time in the “hardware hacking village”, and for the first year they had it was a big success. The room was cramped people learning to create circuits and use soldering irons and multimeters for the first time. I even won a FPGA circuit design kit from a research group at the University of Delaware that was in attendance. If anyone is ever asking trivia questions about old Apple systems, the answer 50% of the time is “Lisa.” | |
| Black Hat/Defcon 16 Recap from Vegas [spylogic.net] Posted: 10 Aug 2008 09:39 PM CDT I am on my way back from Black Hat and Defcon 16 in Las Vegas with a three hour delayed flight so this is probably a good time to talk about Black Hat and Defcon 16. To start off...this was one busy and eventful week! I met so many people this week it was crazy. I am officially overflowed with business cards! I got lots of opportunities to not only meet some of the people that I admire in the security industry but also had a chance to network with a great many others that I just met. There were some really good parties (umm..networking opportunities) at both Black Hat and Defcon. Some worth mentioning that I was at were Mozilla, Core Impact, Ethical Hacker, and I-Hacked. I also attended a Security Twits meetup on Friday night at Sushi Roku and got to meet many of the Security Twits in person which was really cool. Thanks to @quine for organizing this event! I attended several talks at both Black Hat and Defcon. I was able to attend everything that I wanted at Black Hat and even attempted to "live tweet" the Dan Kaminsky talk. You can see my updates through TweetScan or other Twitter search tools by searching for #blackhat and #defcon on my Twitter ID (agent0x0). Most of my time at Defcon was spent watching my wife win the Guitar Hero 3 Medium contest...(first woman to win this contest at Defcon) and improving my lock picking skills in the lock picking village. I have to say that I focused a lot of my time at Defcon just enjoying the contests and meeting new friends. I absolutely love Defcon. It's the greatest meetup of the good, bad, and everyone in between. One talk that was a highlight for me was Jay Beale's talk on "Owning the users with the Middler". I interviewed Jay on the Security Justice podcast about a week ago where he talked about the tool. Jay's talk was packed! Standing room only (goons were sent in to crowd control). He did a good job even though he couldn't finish his talk because time ran out. If you get an opportunity to see Jay speak, I highly recommend it! Speaking of goons...I have to hand it to the Defcon goons this year for doing a great job with crowd control! I overheard one goon say that he was doing crowd control for a "f***ton" of people! Oh, and the badges were pretty cool as well...once I waited in a long line for mine on day 2. The badge is actually a "tv-b-gone"...I could turn the TV on and off in my hotel room with the badge. Neat! Speaking of podcasts...I was fortunate to participate in the live podcast at Defcon 16 right before the I-Hacked party in one of the Sky Boxes. I podcasted with Chris and Jay from Securabit, Larry from PaulDotCom, Matt from SploitCast and Martin McKeay from the Network Security Podcast. Rob Fuller (@mubix) coordinated and hosted the event. Hopefully some of you were able to tune into the live video and audio and chat via IRC. Not sure if the recording will be released or not. I'll post a link if it is. Finally, lots of pictures were taken!! I will be posting mine to both my personal and the Security Justice podcast web site Flickr account soon. It looks like my plane just arrived...I hope to post more stuff on Black Hat/Defcon in the coming days. | |
| PuttyHijack V1.0 - Hijack SSH/PuTTY Connections on Windows [Darknet - The Darkside] Posted: 10 Aug 2008 08:13 PM CDT PuttyHijack is a POC tool that injects a dll into the PuTTY process to hijack an existing, or soon to be created, connection. This can be useful during penetration tests when a windows box that has been compromised is used to SSH/Telnet into other servers. The injected DLL installs some hooks and creates a socket for [...] ShareThis Read the full post at darknet.org.uk | |
| Chinese hackers eating Chinese hackers…with a side of government [The Dark Visitor] Posted: 10 Aug 2008 06:48 PM CDT This is the official Chinese government website for Longgang Emergency Management: This is also the official Longgang Emergency Management website, when you add xiaozi.html: You would think, with the recent earthquake in Sichuan and the ongoing Olympics, that government websites dealing with emergency management would be inspected rather thoroughly. Not so much. Google spiders crawling the internet, show that the website has been hacked since at least 31 July 08. Is it unusual for a Chinese hacker to attack their own government’s website? The first-generation of Chinese hackers had very strict rules about not hacking inside China but the current crop doesn’t seem to adhere to the same code. Doing a pull on Zone-h.com.cn, gives 1,952 known Chinese government websites that have been hacked. A fairly large number of those attacks appear to be carried out by Chinese hackers. So, from the URL extension on the hacked page of the Longgang Emergency Management website, who or what is a xiaozi? It is a who, or to be more precise, a him. Meet Network Boy (Wanglu Xiaozi): Blog name: Network boy’s BLog Hacker Not to get in a battle over Zodiac signs but isn’t someone born on 13 December a Sagittarius? Maybe something to do with the Chinese Lunar Calendar but trying to figure it out hurts my head about as much as International Date Line conversion. I have Chinese friends I give birthday gifts to five times a year just to be on the safe side. Moving on. Going through Netboy’s website reveals that government websites are not his only target, he also has an affinity for fellow hacker websites as well. 1) First target, zgmuma.com (China’s Trojan Base): According to Netboy, he was bored and went to his favorite hacker site (hackol.com) to study but the website was down. He did notice a link toward the bottom of the page that connected to zgmuma.com and for reasons unmentioned decided to see if he could break into the site. Zgmuma.com is another Chinese hacker website that boasts the largest collection of online game trojans around. It also provides hacker training. I have to give Netboy credit, he provides a step-by-step account of his exploits, to include screen shots and the tools used to perform reconnaissance on the intended victim. With this one he was able to find a fatal flaw in the server to crack. While Netboy was breaking into zgmuma, his buddy, who goes by the name of Ice Sugar, contacted him to say that he had gained access to cnhacker.com and posted a hacked page: Ice Sugar passed over the info on cnhacker.com to Netboy, who said he also posted a hacked page on the site. 2) Second target, an81.cn (The Dark Hacker Group): Netboy was able to gain access to this website because they were using Dvbbs8.1. He was thankful that it was not 8.2, because then he would not have been able to gain access to the backstage shell. Using Thunder (unclear) he was able to discover the site admin’s password, 6423987, after making several manual guesses. He also used an ASP trojan during the process but I couldn’t begin to tell you what he was talking about; didn’t understand much of the technical jargon. 3) Third target, www.163???.com (Hacker) Netboy really liked the design of this website and consider it difficult to break but still managed. Once again, he takes you through his very methodical system of cracking the website and I wish I was able to translate it but can’t. Some of you people who are more on the tech side might be able to gather what he did even better than me by the screen shots. For whatever reason, he decided to hide the target’s URL but it only took about a minute to find the site, www.163xjs.com. Wasn’t able to access the site due to a “directory listing denied” message. However, Google’s cache was not so particular about who peeked: Even though the imagery is absent, it is clearly the same website. 4) Fourth target, hacker98.cn Lot of stuff on this hack too but I’m getting bored and you get the point. He hacks other Chinese hacker websites. Conclusion: At the end of each of these attacks, Netboy posts an invitation for other skilled people to join his group. So, this all may be just to gain recruits by proving he is better than the other groups out there. | |
| The Cat is Out of the Bag - Defcon or not [Last In - First Out] Posted: 10 Aug 2008 05:24 PM CDT Apparently Massachusetts Transit thinks that it is actually possible to retract information from the public once it leaks. They've convinced a judge to issue a restraining order to prevent MIT students from presenting at Defcon. But they missed the fact that the presentation is already downloadable from public sources (MIT's student newspaper), is available on the Defcon CD, and then a "copy of the entire presentation was entered as evidence in publicly available court records". Doh! The source code for the nifty toolkit might be harder to obtain. But because is was once public, odds are that someone grabbed a copy. In any case, the physical security at MBTA was apparently weak enough that many opportunites for mischief were available without going through the trouble of hacking the cards. | |
| Microsoft Security Patches August 2008 Advance Notice [Sunnet Beskerming Security Advisories] Posted: 10 Aug 2008 05:09 PM CDT Microsoft have provided advanced notice of the patches that they intend to release with next week's August Security patch release. In a departure from the trend of the last few months, where only a couple of patches were released, this month Microsoft are intending to release 12 patches. Seven patches will be Critical, and the remaining five as Important. As well as the regular Malicious Software Removal Tool update, there will be non-security, high-priority updates through Microsoft Update, Windows Update, and Windows Server Update Services. From the Advance Notification page, the software to be affected by the Critical updates include Windows, a cumulative Internet Explorer Update, Windows Media Player, and various Office components. Software affected by the Important updates include Windows, Outlook Express, Messenger, and Word. As with each month's security patch releases, Sûnnet Beskerming will be preparing a detailed briefing pack outlining known issues affecting this month's releases. | |
| Twitter Weekly Updates for 2008-08-10 [/dev/random] [Belgian Security Blognetwork] Posted: 10 Aug 2008 04:59 PM CDT | |
| Sampling a Malicious Site [Didier Stevens] [Belgian Security Blognetwork] Posted: 10 Aug 2008 04:59 PM CDT Fake CNN alerts galore! I seize the opportunity to publish a new video (warning: 8 minutes of command-line staring) (hires XviD version here) showing you how to use my tools to retrieve malware samples hosted on a website. If you just visit an infected website with Internet Explorer, you run the risk of infecting your machine. The safe way to retrieve samples is to work in a low-risk environment (e.g. non-root account on a Linux VM) and use tools that are unlikely to be the target of exploits hosted on said website. The following tools are featured in the video:
The file numbering trick (01., 02., 03., …) allows me to document exactly how I obtained the sample. Since I recorded the video, the malware seems to have been removed from the site. But be careful, it’s not uncommon that compromised websites get reinfected.  | |
| Dispatches from Blackhat/Defcon: Facebook/MySpace "Worm" [NP-Incomplete] Posted: 09 Aug 2008 09:15 PM CDT I have been at BlackHat/DefCon since Tuesday, and I have been slightly out of the loop on some recent security events. Coincident with the presentations on social network security and new XSS attacks against MySpace, reports of a worm hitting MySpace and Facebook started trickling in via SMS messages from our team back at the office. My initial concern was that this was a full-blown Samy-style worm hitting both social network sites, and some of my comments were oriented towards this threat. It turns out that the MySpace/Facebook worm was less a worm and more a standard malware-push technique. Rather than having malware infect a system to send spam to other users that enticed them to install the same malware, the authors had the malware hijack MySpace and Facebook profiles on login by the user, spamming their friends with a malware download pitch. Basically this ends up being a hybrid worm, that requires more than just pure browser support, like XSS and CSRF attacks, to propagate. Good show, spammers. The interesting part of this incident is that attackers, the media, end users, and vendors are focusing on this as a social networking story and not a desktop malware story, when it is equal parts of both. It is further evidence to me that desktops are being considered by home users to be nothing more than browser containers, with their activities being almost completely focused around a handful of major (social) web properties. | |
| This Is Not Writing; You Are Not Reading [Emergent Chaos] Posted: 09 Aug 2008 03:57 AM CDT The Paper of Record has a hilarious article, "Literacy Debate: Online, R U Really Reading?" which asks important questions about what Those Darn Kids are doing -- spending their time using a mixture of hot media and cold media delivered to them over the internets. I'll get right to the point before I start ridiculing the ridiculous, and answer the question. No. Of course not. It's not really reading. This is not text. It is not the product of hot lead type lovingly smearing a mix of kerosene and soot over wood pulp. It's a bunch of pixels, and those pixels are whispering directly into your brain. You are not reading, you're hearing my snarky voice directly massaging your neurons. That doesn't happen when you read. People don't see things or hear things when they read. Ask Anne Fadiman if you don't believe me. She knows. Let's look at some of the statements in the article: Few who believe in the potential of the Web deny the value of books. But they argue that it is unrealistic to expect all children to read "To Kill a Mockingbird" or "Pride and Prejudice" for fun. It is unrealistic to expect any children to read Austen. Austen is arguably the second best writer in all of English, but she requires emotional experiences that children do not have. Pride and Prejudice is no more children's reading than 1984 is. Trust me on this, I know. I read 1984 when I was ten, and when I re-read it in college, I was gobsmacked to learn that there is sex in it. Some traditionalists warn that digital reading is the intellectual equivalent of empty calories. Often, they argue, writers on the Internet employ a cryptic argot that vexes teachers and parents. Zigzagging through a cornucopia of words, pictures, video and sounds, they say, distracts more than strengthens readers. They said pretty much the same about Dickens. Until relatively recently, no serious scholar of literature (read college professor) would admit to reading Dickens. Personally, I agree. These days he's considered a classic, and the non-serious scholars won't admit to reading him. Last fall the National Endowment for the Arts issued a sobering report linking flat or declining national reading test scores among teenagers with the slump in the proportion of adolescents who said they read for fun. And of course we can fix this by denigrating what they do read, as opposed to finding things for them worth reading. "Whatever the benefits of newer electronic media," Dana Gioia, the chairman of the N.E.A., wrote in the report's introduction, "they provide no measurable substitute for the intellectual and personal development initiated and sustained by frequent reading." I'll do my part. I resolve to start writing my blog posts, okay? Do you want them in printing or copperplate? [Synopsis: Nadia's mother tries to instill a love of books in Nadia. Nadia does not respond until they get a computer, when Nadia gives up TV for fanfic.] Which the masters of modern literature such as Pynchon and Joyce would never do. Austen never had elliptical plots, they were circular, and she was merely eccentric. Nadia said she wanted to major in English at college and someday hopes to be published. She does not see a problem with reading few books. "No one's ever said you should read more books to get into college," she said. And this is a problem? Reading skills are also valued by employers. A 2006 survey by the Conference Board, which conducts research for business leaders, found that nearly 90 percent of employers rated "reading comprehension" as "very important" for workers with bachelor's degrees. I don't know about you, but I wonder what sort of people the 10+% of employers are who think that reading comprehension is not very important. What sort of Dilbert-refugees are they? I find that "nearly 90%" to be disturbing. Some literacy experts say that reading itself should be redefined. Interpreting videos or pictures, they say, may be as important a skill as analyzing a novel or a poem. Ah, the word "may." I've ranted about it before. It is true that interpreting pictures may be as important as analyzing a novel. It certainly is if you want to appreciate El Greco. But that's not the point. As much as I like sneering at moderns who think Dickens is literature, times change. It may, indeed. Joyce may have written grammatically. Austen may be suitable for children. Reading comprehension may be important for workers with bachelor's degrees. And Shakespeare's works may have been written by another man of the same name. I am disdainful of hot media, but the Web is the rennaissance of cold media. It's an aberration in a slide to hotter and hotter media. Also realize that cold media is relatively recent. Most of human history had its literature in songs and pantomime. Lastly, remember that kids have been no damned good for as long as we've been writing at all. The pinnacle of civilization was when we were in the caves, and it's been a long slow slide into perdition ever since. Every generation is worse than the previous one. It will continue to be that way. These kids are going to sigh with exasperation and not understand why their kids roll their eyes at Sailor Moon. And they just not going to understand the true art form of fanfic and slashfic. Tsk. | |
| Posted: 08 Aug 2008 04:21 PM CDT  HD Moore just posted documentation for Karmetasploit: I just posted the first public documentation on Karmetasploit. This project is a combination of Dino Dai Zovi and Shane Macaulay's KARMA and the Metasploit Framework. The result is an extremely effective way to absorb information and remote shells from the wireless-enabled machines around you. This first version is still a proof-of-concept, but it already has an impressive feature list:Just one piece of advice. Unless you create an IPSEC tunnel or you can use WPA, don't use a wireless network. Too much can go wrong. If you want to know how many attacks are possible on an unprotected wlan connection, just download this video from The Last HOPE from Renderman: How Do I Pwn Thee - Let Me Count The Ways (torrent). Just set up a openVPN server at home (or use ssh tunneling in worst case). Related posts:
| |
| Fake CNN Custom Alert [Didier Stevens] [Belgian Security Blognetwork] Posted: 08 Aug 2008 03:33 AM CDT Here’s a new social engineering trick I hadn’t seen in my spam mail before:
The Shia link actually points to a real CNN article about the olympics & terrorism. So you might be inclined to click on the full story link. Like the CNN Top 10 malware, it has a fake Flash update:
Which happens to be malware.  | |
| Phone Call Strong Authentication [/dev/random] [Belgian Security Blognetwork] Posted: 08 Aug 2008 03:09 AM CDT
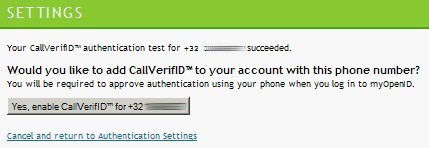
OpenID is a free service which offers strong authentication to websites (already covered by a previous post). Strong authentication is based on a two factors authentication: something you know, something you have or something you are (more details here). Trustbearer offered strong authentication via, as example, the Belgian eID Card. OpenID now propose a new service called CallVerifID: Once you configured a phone number, OpenID will call you to perform the authentication. The phone rings, answer and press “#” to authenticated. A small demo? First login to your OpenID account and enable CallVerifID. You just have to give your number and press the “Test” button. A few seconds later, you receive a call asking you to press the pound key (#). Once done, you are ready to enable your CallVerifID:
Now, let’s perform the final test. We still use our login and password pair but now the phone rings to complete the authentication procedure:
At the moment, this service is available in 30 countries. Unfortunately for me, mobile phones are not (yet) supported in Belgium, only fixed lines. | |
| Keeping abreast of the threat [Emergent Chaos] Posted: 07 Aug 2008 10:15 PM CDT The German Bundespolizei have announced what the BBC are calling a "bullet-proof bra". It may sound like a joke, but this is a serious matter - the policewoman who came up with the idea said normal bras can be dangerous when worn in combination with a bullet-proof vest. Now, I'm sure Frau Kibat's heart is in the right place, and I would certainly not want it to be pierced by either a bullet or a brassiere clasp or underwire fragment, but I have to suggest here that "I always thought" doesn't suggest that the decision to develop this article was made based on empirical data. While I admit it's interesting to see "Polizei" on a brassiere, it'd have been better to ask those that are concerned about the "risk posed by normal bras" to simply buy one that is made entirely of cloth, since they are readily available through non-governmental channels. Photo: Reuters, via Die Welt | |
| Posted: 07 Aug 2008 08:39 PM CDT Dan Kaminsky not only posted his slides but also this cool video he used during his presentation. It's shows DNS servers being patched in fast motion, beginning the 7th of July till the 3rd of August. Red is unpatched, yellow is patched but with NAT issues and green is patched. From doxpara.com: - Too bad it didn't include dramatic music. ;-) UPDATE: Now a version WITH music. ;-) Related posts:
|
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |



















No comments:
Post a Comment