Spliced feed for Security Bloggers Network |
| Links for 2008-08-15 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 16 Aug 2008 12:00 AM CDT
|
| The Cat is Out of the Bag [Andrew Hay] Posted: 15 Aug 2008 07:16 PM CDT
Every now and then a career opportunity comes around that you simply cannot say no to. This job in Bermuda is just that kind of opportunity. My new role will allow me to attend more conferences and influence the development of security policies and training. Hopefully my new role will also allow me to enjoy some of my past accomplishments and provide new and exciting challenges. Oh…and blog more |
| A Few More Words on DLP and Compliance [Anton Chuvakin Blog - "Security Warrior"] Posted: 15 Aug 2008 04:51 PM CDT Today I was thinking about DLP again :-) (yes, I know that "content monitoring and protection" - CMF - is a better description) Specifically, I was thinking about DLP and compliance. At first, it was truly amazing to me that DLP vendors "under-utilize" compliance in their messaging. In other words, they don't push the "C-word" as strongly as many other security companies. Compliance dog doesn't snarl at you from their front pages and it doesn't bite you in you ass when you read the whitepapers, etc. Sure, it is mentioned there, but, seemingly, as an after-thought. For example, Reconnex that was recently absorbed by McAfee, touts "information protection" before compliance. Similarly, my friends from nexTier only mention "compliance" on a few pages. Even newly unveiled DLP resource (DLP In-Depth portal) only contains a little bit of information on how DLP solutions help with various compliance projects. People tout "data protection", " data security", "data governance" (aka "we know big words - bigger than you") or even "data risk management" (aka "we are confused about what we sell") I decide to explore this curious phenomenon. Initially, I thought that it was reverse compliance at work? People not wanting to know what content packs up and leaves their network. Then I thought that maybe DLP vendors just aren't "the bandwagon jumping kind" (yeah, right!) Then I thought that they are "beyond compliance" already :-) But you know what? I actually think that it is something different, much more sinister. It is the ominous checklist mentality (here too)! You know, DLP is newer than most regulations (PCI DSS, HIPAA, FISMA, etc) and - what a shock! - the documentation for these mandates just doesn't mention DLP (or CMF) by name. Sure, they talk about data protection (e.g. PCI DSS Requirements 3 and 4), but mostly in terms of encryption, access control, logging (of course!). Also, PCI DSS directly and explicitly says "get a firewall", "deploy log management", "get scanned", "install and update AV" - but where is DLP? Ain't there... Yes, Virginia, folks who "go by the book" and just "do the minimum" are missing out on the chance to procure DLP while their compliance budgets are still flowing. To me that means that many still don't get the "compliance+" model - buy for compliance -> use for security, operations, having fun, etc. Think what a good DLP solution will do for you in discovering regulated data across the entire organization, blocking those pesky email with SSNs, PHI (hi, HIPAA) and CCs (hi, PCI) as well as solving plenty of other problems ... |
| StillSecure secures an IQ award [StillSecure, After All These Years] Posted: 15 Aug 2008 04:20 PM CDT For those who don't know StillSecure is headquartered in Superior, CO, which right outside of Boulder, CO. Besides being a beautiful, funky college town nestled in the foothills of the Rockies, the Boulder area is a leading tech center. One of the more coveted local recognition awards is the Boulder County Business Report IQ awards. In this case IQ does not stand for how smart you are, but Innovation Quotient. StillSecure was just named the winner in the Computer category. This was just not security, but virtually computer technology. This follows my pal, Rajat Bhargava, StillSecure CEO, winning an entrepreneur of distinction Espirit award from the Boulder Chamber of Commerce as well. |
| Posted: 15 Aug 2008 03:24 PM CDT  Many words were written about the cyberwar between Russia and Georgia. Georgia is accusing the Kremlin, and there were reports that the Georgians experienced cyber-attacks even before the invasion began. If you Google around, you'll get hundreds of related news stories. Many words were written about the cyberwar between Russia and Georgia. Georgia is accusing the Kremlin, and there were reports that the Georgians experienced cyber-attacks even before the invasion began. If you Google around, you'll get hundreds of related news stories. Evgeny Morozov decided to report from a different angle. Probably intrigued by quotes stating that cyberattacks are inexpensive and easy to mount, he decided to join the war. Protected behind the shields of his laptop and far from the dangers of the fights. The Slate brings his story. |
| If security is a circus, who are the clowns? [StillSecure, After All These Years] Posted: 15 Aug 2008 03:09 PM CDT
With the pressure of getting out code on time and on budget, there are just too many vulnerabilities in the products we rely on. Racing to get the next greatest feature in this release or that must have functionality that was promised to the customer, too often pushes security and bullet proof code into the shadows. Then when someone finds the all too often holes in the code, somehow the people finding it are wrong? Yes, it would be much better if the whole disclosure timing thing went away. I don't think that will ever happen. But if we had more quality control around code, perhaps it would not be so acute. So, when talking about the circus, instead of blaming the security people, maybe take a good look at the clowns. |
| Cisco Security Advisory: Cisco WebEx Vulnerability [Infosecurity.US] Posted: 15 Aug 2008 02:07 PM CDT |
| On Idiots and Logs [Anton Chuvakin Blog - "Security Warrior"] Posted: 15 Aug 2008 01:53 PM CDT |
| XKCD: Electronic Voting Machines [Infosecurity.US] Posted: 15 Aug 2008 01:52 PM CDT |
| Applied Security Visualization [Roer.Com Information Security - Your source of Information Security] Posted: 15 Aug 2008 01:34 PM CDT The book Applied Security Visualization, by Raffael Marty (the SecViz) is available. This book is particularly interesting to those of you who are into logging, and struggle to find a meaningful way to present and use your log data. I have put it on my reading-list, as I believe that logs are only as valuable as their presentation. |
| Fortify Hacking Challenge [ISIS Blogs] Posted: 15 Aug 2008 01:03 PM CDT I also did the Fortify [Web] Hacking Challenge last week. Their challenge was refreshingly different, fun, and relaxing compared to the other web hacking challenges I’ve done. I really enjoyed playing in it even if it only lasted a short time. Here’s the official description of the contest:
Fortify RTA had a tight lock on that website! I probably came up with a hundred separate attacks against their website, but they were only looking for a very specific 3. Every so often, I’d come up with what I thought was an impressive attack but it wouldn’t give me any points! Here’s one example:
I took screenshots of all the actual attacks below. You had to recognize that they set an AuthType cookie when you logged in. Changing this cookie to 0 let you view and access a hidden admin panel. Once in the admin panel, RTA triggered on a command injection vulnerability: … and on cross-site-scripting the other admins: The last attack was a SQL injection on the account details page: My biggest problem was that I overthought the attacks they were looking for. Once I calmed down and stopped trying to become a millionaire/root-shell-0wner I realized they were probably looking for the basic web vuln trifecta: command injection, xss, and sqli. All in all, a really fun challenge. Thanks Fortify! |
| Posted: 15 Aug 2008 10:46 AM CDT  "Cybercrime was probably here to stay". Kypros Chrysostomides, Justice Minister, Cyprus "Cybercrime was probably here to stay". Kypros Chrysostomides, Justice Minister, CyprusThis quote is taken from an article in the CyprusMail, delivering the story of an IT consultant breaking into a former client, an international investment and finance services company, which the island's industry is based upon, and stealing customer data. Looks like Cybercrime is everywhere, including the peaceful Mediterranean island. Only several years ago the paper quoted another official stating that "no one in Cyprus has ever been arrested or charged with any sort of cyber crime". But now, it's there to stay. |
| Shimel Returns! [Infosecurity.US] Posted: 15 Aug 2008 09:39 AM CDT
|
| Will Exporting Netflow Impact My Device? [Andrew Hay] Posted: 15 Aug 2008 09:37 AM CDT One question I hear all the time is “If I enable the exporting of Netflow on my router or switch, will it impact performance?” Yes it will, but usually not by enough to discourage you from including Netflow datagrams in your network analysis plans. According to this document, released by Cisco, if you have…
Also, sampled Netflow will significantly decrease CPU utilization to the router. According to Cisco:
That being said, sampling Netflow won’t give you the whole picture, just a tiny piece of the flow puzzle. More information can be found here and here. |
| links for 2008-08-15 [Andrew Hay] Posted: 15 Aug 2008 08:00 AM CDT
|
| Cyberwar or Media Hype? [Andrew Hay] Posted: 15 Aug 2008 07:50 AM CDT Note - I am not taking sides in the Georgia/Russia conflict as I think the governments on both sides are equally acting like children.
The article describes how easy it was for the author to find out how to attack the Internet infrastructure of a foreign nation. (I won’t even touch the topic of someone downloading a webpage and accessing it on their system - that’s another article entirely). From the article:
Now this really made me think. If there is a Cyber War going on in Georgia, how can we be certain that the attacks originate from Russia and not sympathetic expatriates in the Western hemisphere? How can we be sure that the attackers are not opportunistic attackers looking to exploit an attack vector that will be blamed on an entire nation? How can we be sure that the Georgian army isn’t taking their own infrastructure offline in order to draw sympathy to their cause? From the article:
The bottom line is that we can’t be sure of any of these issues without extensive network and system monitoring. I’m not talking about watching the traffic and logs for one or two sites, but rather a city-/region-/country-/nation-wide monitoring infrastructure with centralized consolidation of information for trending and situational awareness. This type of infrastructure allows nations to detect probing of their infrastructure (a.k.a. reconnaissance), help determine the source of the attackers (a.k.a. intelligence), and ultimately help mitigate the attack (a.k.a. digging in). |
| I’ve Been Laughing At This All Morning! [Andrew Hay] Posted: 15 Aug 2008 06:54 AM CDT |
| Difference between InfoSec and Audit (Group Hug)? [RSA Conference - Blog] Posted: 15 Aug 2008 05:07 AM CDT |
| Posted: 14 Aug 2008 10:44 PM CDT The more of these I read, the more I will continue to express my opinion that I shared with an Army gentleman on my way home from Atlanta the other day - the TSA should be fired wholesale, and replaced by competent military personnel. I can confirm, personally, that the TSA's facilities in SFO are horribly bad, as I walked past a screening point in the airport, past a door marked "Transportation Security Administration Staff Only" which was taped open (meaning, there was tape over the door lock)! Another door was propped open with a chair and a oscilating fan placed on it, presumably to cool off the room. Now the above mentioned article indicates that an unencrypted computer for the CLEAR program was stolen and then put back into a locked cabinet... how does this happen? First off, how is it that the TSA and its partners are still not encrypting laptops? How does a laptop go missing from a locked cabinet, then get put back into that same locked cabinet without anyone noticing who took it or put it there. How bad is security at these places? While I understand I may be subjecting myself to some "additional security screening (read: hassle)" I will be starting to take more pictures of the TSA "secure areas" with my trusty travel camera as I travel. Someone needs to expose this crap, and make the TSA accountable - I guess if it has to be me, so be it. While I'm not planning on getting myself into trouble, or taking pictures of anything that's a security breach (obviously, I travel enough to know safety is a concern)... someone has to keep these folks accountable for their absolute lack of knowledge, security, and concern. More to come. |
| VMware CEO Apologetic After Patch SNAFU [Infosecurity.US] Posted: 14 Aug 2008 04:27 PM CDT |
| Air Force Hibernates ‘Cyber Command’ [Infosecurity.US] Posted: 14 Aug 2008 04:11 PM CDT
|
| Clear® CEO Stephen Brill Updates Registered Travelers Via Email [Infosecurity.US] Posted: 14 Aug 2008 11:19 AM CDT
|
| Black Hat 2008: Zen of Xen [Infosecurity.US] Posted: 14 Aug 2008 08:04 AM CDT
|
| On TV Warfare [Anton Chuvakin Blog - "Security Warrior"] Posted: 13 Aug 2008 08:23 PM CDT It is simply amazing that all the countries now "get it" that war happens primarily on TV (this vs this; many other examples are around). It is also amazing that there is NO way to know where "media reporting" ends and "psyops" begin. So, a burning tank with no clear markings that you see on TV might be:
Same applies to the "primary weapon" of a modern TV war: "evidence of atrocities of the opposing side." What's the truth? Who knows... progress brought us "TV wars," is this the first "YouTube war"? But if we cannot believe the media coverage, how can we believe a random video online? Well ... maybe the same way we often believe Wikipedia over Britannica. In any case, if there was a better time to turn off the TV (and tune off the web news...), it would be now. Also, time to get the dust off my copy of Toffler? Rant mode off :-) UPDATE: fun article on that very subject (media vs psyops) - "Debating Domestic Proganda: Part I" UPDATE: "A column of Russian military vehicles, including tanks and armored vehicles, was reported to be moving toward Tbilisi with a journalist from U.S. media giant CNN riding along and reporting live for U.S. television. [...] The fact that Russia now has U.S. journalists embedded with its military to report every move being made is key. " (source) |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |
 After weeks of biting my tongue I can finally let everyone know that I have accepted a security analyst position in Bermuda and am leaving
After weeks of biting my tongue I can finally let everyone know that I have accepted a security analyst position in Bermuda and am leaving ![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_c.png?x-id=3772df74-e821-4714-8e2d-e8d5d317b5ab)
 Linus Torvalds complains to Ellen Messmer
Linus Torvalds complains to Ellen Messmer Cisco
Cisco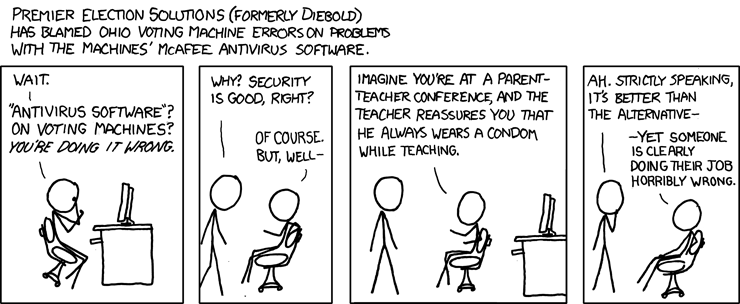




 Alan Shimel (Chief Strategy Officer of
Alan Shimel (Chief Strategy Officer of  In reading this
In reading this 



No comments:
Post a Comment