Spliced feed for Security Bloggers Network |
| VCR taping part II [StillSecure, After All These Years] Posted: 07 Oct 2008 07:41 AM CDT  Image via Wikipedia I thought I was in a time warp reading this article that RealNetworks had pulled their RealDVD copying software pending a judges ruling. It seems several of the major Hollywood studios have asked the courts to stop distribution of the software because it will break or bypass the DRM-copyright protection (pronounced you can't copy it, not copyright) built into DVDs. Two things on this come to my mind. First of all, I am old enough to remember when Hollywood said the same thing about taping movies on VCR tapes. The thought of taping off of the TV or of buying a tape and making copies for all of your friends scared Hollywood to death. We heard all kinds of stories about how this was going to be the death of the movie business. What happened was that the VCR tape business became a huge money maker for the studios. An entire new revenue stream, often bigger than than what a film drew in theatres was born. Despite all of the doom and gloom, VCR tapes was the best thing that ever happened to the movie business. I don't see any reason that DVDs will be any different. Secondly, even if ReadDVD is stopped from selling this software, do you really think they are the only ones? Anyone who is serious about copying DVDs can find software on the Internet to do this. I think the movie industry, like the music industry is shoveling sand against the tide with DRM and anti-copying protection. These industries need to figure out how to capitalize on the viral nature of copying media and monetize it. Picking on RealNetworks about this a whack-a-mole game. As soon as RealNetworks is back in the hole, another one will pop up. Related articles by Zemanta |
| Security Briefing: October 7th [Liquidmatrix Security Digest] Posted: 07 Oct 2008 06:28 AM CDT  Sector.ca sessions start today! Click here to subscribe to Liquidmatrix Security Digest!. And now, the news…
Tags: News, Daily Links, Security Blog, Information Security, Security News |
| SecTor Goodies [.:Computer Defense:.] Posted: 07 Oct 2008 12:53 AM CDT So I spent today in training @ SecTor. I attending HD Moore's metasploit training and rather enjoyed myself... I picked up a couple of things that I'd been previously unaware of. Since I was already onsite, I took advantage of the open registration booth and picked up my SecTor goodies. Instead of the cooler bag (last years very cool SecTor registration goodie), there's a rather nice tote with the SecTor logo on it. Inside the bag was the usual advertising literature, a nice Leed's notebook with a metal (I think) cover, with the SecTor logo, and a pen and BlackBerry screen cleaner. The badges are quite nice... given that the program includes a picture of the DefCon badge, I imagine they were trying to go with something along those lines. Rather than the hard plastic, "corners will cut you when you attempt to touch it" badge of last year, the badge this year is rather cool. There's a usb cable enclosed on the back of the badge and when you connect it, you find that it's a 1GB storage device. Definitely a step up. I took pictures to attach, but I'm getting an error, so I won't be uploading them tonight... I'll try again tomorrow. Now given that it's 2AM and I'm meeting people for breakfast in 5.5 hours, I should probably grab some sleep... but on that note... The program this year doesn't mention a breakfast, so some of us are meeting at Cora's on Spadina (not far from the MTCC) at 7:30 if anyone happens to read this between now and then and wants to join us. |
| Grecs’s Infosec Ramblings for 2008-10-06 [NovaInfosecPortal.com] Posted: 06 Oct 2008 11:59 PM CDT
|
| That’s All I Have To Say About That [BumpInTheWire.com] Posted: 06 Oct 2008 11:09 PM CDT You see what happens when Missouri is good at football? The global markets tank. Remember the “dot com bubble?” A whole lotta people made a whole lotta money. During that time, which according to Wikipedia was from 1995-2001, the Nebraska Cornhuskers went 68-11 in football. In that same seven year span the Missouri Tigers went 34-45. Isn’t it in your economic best interest to have Nebraska good at football?!!! |
| J. Leaves Security Team Zero-Day Exploit [The Dark Visitor] Posted: 06 Oct 2008 10:35 PM CDT New group to keep an eye on: J. Leaves “Security Team” Zero-Day exploit group: http://00day.cn As with most of my posts, I was looking for something else and bumped into this group. It seems they found a crack in a section of the JSP version of eWebEditor (1.4 and older) on August 30th and have just released the code. No, I will not link to the code. The eWebEditor is an HTML editor put out by a Chinese company located in Fuzhou, Fujian. Yes, I did send the company an e-mail: We, at the Dark Visitor, strive to be good citizens of the international community. |
| September SCADApedia Entries [Digital Bond] Posted: 06 Oct 2008 09:59 PM CDT SCADApedia - - all can read - - subscribers can write. New entries in September:
A number of the other pages have been updated as well. You may also want to look at All Pages or the links to Control System Vulnerability Notes or the links to Digital Bond’s Research Projects. |
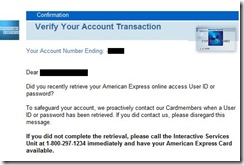
| Trivial Account Reset on American Express Accounts (Updated) [Last In - First Out] Posted: 06 Oct 2008 07:51 PM CDT
2008-10-06 Update: I did eventually get an e-mail notice sent to the e-mail associated with the account about 6 hours after I reset my password. Account claiming is an interesting problem. The tradeoffs necessary to balance ease of use, security and help desk call volume are non-trivial. 2008-10-05 9:59 PM:I'm a bit disappointed how easy it was to recover online access to my American Express account.
"spaces or special characters (e.g., &, >, *, $, @)" That makes choosing a password tough. My normal &mex$uck$ password will not work. But fortunately for me, the help screens on picking a new password contain useful examples: Examples of a valid password are: snowman4, 810main, and year2k." Never mind that whole dictionary thing. Nobody will ever guess a password like 'year2k'. The Amex account is set up to send me an SMS alert for any 'Irregular Account Activity'. I did not get an SMS, even though on line recovery of both userid and password would certainly be worth an SMS in my book.There are better ways of doing this. They could have asked me for some secret number that only exists on my last statement, or information on recent card activity, or perhaps like my health care provider, the account reset could generate a letter with a token, sent to my home address via good old fashioned postal mail. |
| On Black Monday, security vendors are not immune [StillSecure, After All These Years] Posted: 06 Oct 2008 06:05 PM CDT I don't have to tell you what a miserable day it has been on Wall St. It is downright depressing. One thing that has me even more worried is that with the past financial turmoil, IT security has remained solid. The thought that organizations would do without security was just too radical to contemplate. In today's sell off though, information security has not been immune. According to this article in Forbes, all software is down but information security companies are taking more than their full share of the hit. Now that doesn't mean that we are already seeing a slow down of spending on security. But what it does mean is that the people buying stocks, whether they be smart or stupid, are thinking that our economic climate is going to effect the ability of these companies to execute on their plans and that means selling security solutions. This is a problem. I think we are past the time of quick fixes here. We are going to have to take our medicine like it or not. As I have said before though in the long term it may be a good thing for security vendors. |
| Out with TMDA, In with Spam Assassin [The Falcon's View] Posted: 06 Oct 2008 06:00 PM CDT |
| Interesting Information Security Bits for 10/06/2008 [Infosec Ramblings] Posted: 06 Oct 2008 04:51 PM CDT Good afternoon everybody! I hope your day is going well.
That’s it for today. Have fun!  |
| Rethinking stored document encryption: Part 0 [Phillip Hallam-Baker's Web Security Blog] Posted: 06 Oct 2008 04:02 PM CDT Some years ago at the height of the crypto-wars the FBI argued that commercial implementations of PKI would need escrow. Opponents of Freeh's proposals argued against this notion at the time. It was several years after US government restrictions on export of strong cryptography were lifted that key escrow was accepted as a genuine requirement: Nobody wants to tell the CEO that the loss of their private key means that documents they stored on their hard drive are irrecoverable.
|
| Fun With The External Auditors [Liquidmatrix Security Digest] Posted: 06 Oct 2008 02:46 PM CDT  As I sat at a client site recently I was amazed what I overheard a few cubicles away. An auditor was onsite as part of a team to review the same client that I was doing some work for. The part that I chuckling about was their lack of access. Apparently the best laid plans had been all for naught. They couldn’t access their IP phones and VPN. Basically they were flying blind. Then they called the help desk. After three reboots, no really, three of them, they were still no further ahead. I was starting to feel bad that I wasn’t helping but, that washed away quickly when I heard the most amusing thing. “Yes, my username is XXXXXXX and my domain password is XXXXXX. What’s that? Yes, my VPN is the same” WTF? SRSLY? The auditor had just coughed up their username/password for access to the kingdom. I should have been more surprised but, I’m very familiar with said audit shop. Then it continued. “Yes, the VPN IP address that I’m going to is 1.1.1.1″ Obviously that’s not the proper address. I couldn’t be that evil. The root of the problem was that this person was borderline clueless on an epic scale. Scratch that, full on clueless. So, as I had been sitting here churning through my mountain of documentation I had managed to receive access to the network of one of the big audit firms. Time and again I read about data breaches and the media will call out various Hollywood scenarios as possible methods on how the breach may have occurred. Occam’s Razor should be more closely examined. Sometimes the easiest explanation is the correct one. I walked up to the auditor a little while later and introduced myself as Dave from consulting firm X. The point I was trying to hammer home was that I was very much within ear shot. I wanted to gauge their reaction to my proximity. The light was on but, no one was home. Ouch. |
| State of Maine Skipping Vista Too [Security Provoked] Posted: 06 Oct 2008 02:17 PM CDT So Maine’s skipping Vista, and I’m skipping like a broken record. The government of the state of Maine has joined the burgeoning group of organizations planning to side-step Windows Vista and go straight from Windows XP to Windows 7. I continue to say that completely ignoring Vista is a short-sighted decision that may cause both usability and security troubles not too far down the line. I’ve written about this oodles of times, so I shan’t bore you again. If you’re a CSI member, you can see the entire July Alert issue about this here: “Even Security Pros are Rejecting Vista: What happens next? And what’s our wishlist for the next Windows OS?” If you’d like to duke it out with me, the XP devotees, the Linux fan boys, and/or the Vista lovers, you’ll have a golden opportunity to do so at our Fate of the Secure OS Summit next month as part of our CSI 2008: Security Reconsidered conference in D.C. In the meantime, I’ve reopened the survey we asked CSI members to fill out a few months ago. It’s now open to the general public, so go ahead and take the survey here. |
| Vulnerability management and the Blogs [extern blog SensePost;] Posted: 06 Oct 2008 02:08 PM CDT Gegroet just a quick note on VM. Google is now offering Google Blog Search Beta and I thought it interesting to see who is blogging on vulnerability management.Some of the output includes: i) "Vulnerability Management" = 6,330 hits ii) "Vulnerability Management" + Dummies = 314 hits iii) "Vulnerability Management" + ineffective = 16 hits iv) "Vulnerability Management" + effective = 314 Probably 90% of all hits came from vendors and it was also evident that they were punting the "successes" of VM, utilising their products and services. It was also interesting to note how popular the Qualys "Vulnerability Management for Dummies" is, hence my search in that regard: 314 hits. Note corresponding hits for "VM + Effective". What Qualys has done is to punt effective VM without leaning too much towards their own solutions. The reference is however there and without a real contender in this space they obviously have the lead. For infosec guys that need to kick-start a VM process in their companies there is not a lot to lean on apart from product punts and associated solutions. It also requires access to research companies such as Gartner and Burton Group to really get solid information - at a price of course. This obviously leaves a gap for people to post or publish really effective and non-partisan VM research and ideas. Evert. |
| Lessons learned from the gas shortage [Andy, ITGuy] Posted: 06 Oct 2008 01:57 PM CDT Since just before Hurricane Ike hit the Texas coast we have had problems with finding gas in the Atlanta area. When we are able to find it we are paying 20 to 30 cents a gallon above the national average and 50 to 70 cents above some areas. This has forced Atlantans to make changes in the way we live in many cases. We're making fewer trips to places that are unnecessary, combining trips so that we only have to go out once. Taking alternate transportation to work. Things like car pools, buses, trains, bikes, even working from home. Luckily, things are getting a better here now, at least on the supply side. The 1 - 2 hour wait for gas is over but we are still seeing several stations with little or no gas and we are still paying close to $4 a gallon. In my opinion Atlanta needs to reconsider how we do transportation. I'm not talking about how our transit agencies are run or plan their systems. I'm talking about the average Joe and Jane Commuter. Atlantans rely way too much on their cars and way too little on other ways to get around. We tend to think nothing of making 4 trips when everything could be done in one trip. We love to drive. I assume it's so we will have more reason to complain about how bad traffic is. :) So, how does this relate to Information Security or technology in general? I'm glad you asked! Just as Atlantans have had to come up with creative ways to handle the gas shortage we need to review creative ways to protect our networks and data. We need to look at what we have and how we can leverage it instead of buying something new. We need to look at how we are doing things and find ways to maximize our processes instead of just adding more to the pile. We need to think about how everything fits together and how we can make changes to improve security instead of making things more complex by adding additional layers. (I'm not talking about security layers but about layers that are unnecessary and make more problems than they solve). Times are tough all over and that holds true for security programs also. As I'm writing this the Dow Jones is down 760 points for the second time in a week or so. It recovered some of the first loss but it's not getting any prettier out there in the foreseeable future. Companies are tightening belts and spending is going to slow way down and jobs are going to be lost. This is the time to get creative and show your company how you can make things better and save money. Of course creativity means risk and that may not be the best thing at the moment but at least let them know that you are thinking and working on ways to improve security w/o spending lots of money. |
| Congress: A One-Trick Pony [The Falcon's View] Posted: 06 Oct 2008 12:53 PM CDT |
| Posted: 06 Oct 2008 10:50 AM CDT
My friend Mike Rothman always recognized it and was not shy about calling me out on it. Just for giggles I would send him an email now and then that I heard rumors he was going to take a job as a SVP of marketing at a NAC company. He would always write back with something about hell freezing over. Not sure how cold things are down there today, but in a case of truth is stranger than fiction, Mike announced he has taken a job. Well it isn't a NAC company, but a "company redefining security and compliance management", eIQNetworks. I don't know much about eIQ, but I assume the fact that Mike is joining along with Jim Geary, his colleague at SHYM, they have high hopes. I am glad to see Mike coming over to the "darkside" and joining the vendor wars. Mike has done a great job with Security Incite. It is one of my favorite blogs to read and I enjoy interacting with Mike. I am sure that he will continue on with the incite, but now he will have to deal with the "vendor issue" as well. But hey that goes with coming over to the dark side. I am sure Mike will handle it well and still give us interesting takes on what is going on in the security world. Good Luck Mike! Now that you have come to the dark side (in my best Darth Vader voice), do I need to tell you who your father is? |
| TCP DoS, bang or whimper? [Digital Bond] Posted: 06 Oct 2008 10:42 AM CDT There has been a lot of buzz lately about the Denial of Service vulnerability that a Swedish security firm, Outpost24, have discovered. Right now, the details are a bit limited, as the researchers aren’t going to release details until they present at the T2 conference in Helsinki later this month. This is similar to the way the DNS issue was handled earlier this summer by Dan Kaminsky. So being that security research people tend to be a curious sort there has to be rabid speculation about what the problem really is. Some very smart people have weighed in with their thoughts, including Fyodor(of nmap fame), Graham, and Kaminsky has a great post on the meta issue of partial disclosure. From what I can tell this will just be a minor blip for most people, those with services large enough to be DoS’d have largely distributed systems and won’t really be affected by this any differently than a flood from a botnet, only able to be done more efficiently, and in fact it will be easier to mitigate since this type of attack does not allow for spoofed connections. But this may shape up to be one of those issues that affect control systems more than the average system. We’ve already seen that excessive network traffic can cause major problems, but with this form of attack the same problems could manifest themselves with a very limited number of packets from a compromised system, and given the lack of monitoring tools in a lot of those networks that may make it extremely hard to track down, and make for a very rough day for operators. Since the full scope of the vulnerability isn’t public yet (probably) not much more than the usual advice can be offered, separated networks, acls, and monitoring are very good defenses if deployed properly. We’ll keep following this as I’m sure many of you will, problems in underlying protocols like TCP don’t come around every day. |
| fwknop: Single Packet Authorization and Port Knocking [Nicholson Security] Posted: 06 Oct 2008 09:34 AM CDT |
| OWASP Foundation Announces Full Conference Content Release [Infosecurity.US] Posted: 06 Oct 2008 08:08 AM CDT
The OWASP Foundation has announced the soon-to-be full content release of the entire, recent conference. Read the announcement excerpt after the break. From the announcement:” NOTE we will be releasing the FULL CONTENT of the event on www.owasp.tv <–note new domain on October 1st 2008. ALL talks were video taped and will be a full talk, video stream online shortly so you can watch the event or see the content that you missed. Related Posts |
| Day-Con Infosec Conference Event [NovaInfosecPortal.com] Posted: 05 Oct 2008 11:06 PM CDT Mike from The Guerilla CISO let me know of this year’s Day-Con infosec conference event. It a little far - over an 8 hour drive but according to this ZDNet article some of the Security Twits have rented an RV and will be swinging through NoVA to pick up anyone interested in going assuming there’s still room left. If there’s no room left, then I guess caravaning should work at least. According to Mike, pick-up would be in Herndon on Friday the 10th in the morning and drop-off would be on the evening of the 12th. Here are the logistics for the conference:
Although this conference event will not take place in or around NoVA, we included it because it is drivable for an overnight or weekend trip for those living/working in NoVA. View our Calendar for a list of similar infosec events in and around the NoVA area. See Day-Con’s conference site for more information. |
| Economics of PCI DSS and ROI of Education; A new VODCast [PCI Blog - Compliance Demystified] Posted: 05 Oct 2008 11:04 PM CDT The PCI DSS is expensive and challenging. Scarcity, Information Asymmetry, and the Rational Self Actor phenomenon all play a role in keeping prices high and merchants/service providers at a disadvantage when working through the program. A new VODCast discusses some of the economic aspects of the PCI DSS and explain the ROI of PCI related education. Economics of PCI DSS and ROI of Education |
| T-Mobile: Loses 17 Million Consumer Records in 2006 [Infosecurity.US] Posted: 05 Oct 2008 06:07 PM CDT
Sunday brought news of a truly massive dataloss at Deutsche Telekom’s mobile unit - T-Mobile. Evidently, reported to authorities in 2006, this is the first public acknowledgment of the loss…2 plus years from the date of the event. Apparently the loss affects European customers only…
From the news report: ” According to Der Spiegel, the stolen data had already fallen into the hands of criminals. The data includes the private details of several prominent entertainers, TV stars, politicians, businessmen and millionaires, the magazine said, adding that distribution of their data by criminals could pose a safety risk. It’s not the first time Deutsche Telekom has been mired in a scandal regarding data protection. The company is in the midst of a probe after revelations that it hired an outside firm to track hundreds of thousands of phone calls by senior executives and journalists to identify the sources of press leaks.” Directive 2006/24/EC of the European ParliamentRelated Posts
|
| WinZip Announces Vulnerability. Patched. [Infosecurity.US] Posted: 05 Oct 2008 05:17 PM CDT
Winzip has revealed a serious vulnerability when installed on Microsoft (NasdaqGS: MSFT) Windows 2000. Evidently, patched and mitigated on versions WinZip 11.2 SR-1 and WinZip 12. Hat Tip to Heise Security UK! Related Posts |
| Taking Sunday Off! [Infosecurity.US] Posted: 05 Oct 2008 09:51 AM CDT Taking Sunday off to enjoy some autumnal fishing in the Sound, just south of the Narrows Bridge…Great fishing weather, woohoo! Posting resumes on Monday, October 6, 2008.
|
| Embarrassing [BumpInTheWire.com] Posted: 05 Oct 2008 12:01 AM CDT I’ve done my fair share of exploiting emails from El Sidekick so it would only be fair to have a taste of my own medicine. Some of the text messages I sent tonight during the Huskers 52-17 woodshed beating… @ 8:17 PM - Three plays and MU scores. Gonna have to start double fisting it. @ 8:23 PM - Bopo [Bo Pelini] just put another f’n piece of gum in @ 8:24 PM - 7-6! Extra point coming @ 8:34 PM - MU is 17 yds from scoring again @ 8:37 PM - So is NUs. 14-7 (In reference to MU’s weak defense) @ 8:48 PM - NU is driving. I think the over is going to hit. @ 9:07 PM - 17-7. MU is making Pelini look like a clown. @ 9:24 PM - 24-7. Just pulled my flag in. Good news is I’m gonna hit a 4 team parlay thanks to MU. @ 9:31 PM - 31-7. Ganz just threw a pick six. @ 9:36 PM - Fvcking ridiculous. @ 9:47 PM - 31-10 half @ 10:13 PM - Amy went to bed at the end of the 1st. “Well, I can see you are going to drink yourself into oblivion so I’m going to bed” @ 10:31 PM - 38-10. I’ve had one beer for every nebraska point @ 10:47 PM - 45-10. I’m currently trying to decide which wrist would be better to slit @ 10:53 PM - 52-10 @ 11:08 PM - I’ve decided on the wrist. Now looking for a sharp knife. @ 11:25 PM - 52-17 final. Easily could have been 66-10. As Ron Burgandy would say…”Boy, that escalated quickly… I mean, that really got out of hand fast!” |
| Interesting Information Security Bits for 10/04/2008 [Infosec Ramblings] Posted: 04 Oct 2008 07:41 PM CDT Good afternoon everybody! I hope your day is going well.
That’s it for today. Have fun!  |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=3d17c00b-5d30-4938-9e29-33e4df8aa511)




![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_b.png?x-id=95e4018d-e5bf-47b2-a9ec-c9eba97f6333)

![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_b.png?x-id=fbcbe0e7-4285-4e5d-921d-ac21b7ab7b57)

![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_b.png?x-id=3a87d097-a3ec-4c50-9d10-340124458f0e)

No comments:
Post a Comment