Spliced feed for Security Bloggers Network |
| Joomla hacking still goes on and on [belsec] [Belgian Security Blognetwork] Posted: 13 Oct 2008 04:57 AM CDT |
| Nice Hack psychologischebegeleiding.be [belsec] [Belgian Security Blognetwork] Posted: 13 Oct 2008 04:55 AM CDT |
| Posted: 13 Oct 2008 04:50 AM CDT Evaluating the Utility of Anonymized Network Traces for Intrusion Detection We have provided a thorough evaluation of single field anonymization polices upon pcap formatted network traces. This means that to have some utility log anonimization has to keep the IP address and the port. THis poses a problem with dynamic addresses but keeps the possibility to trace attacks back to networks and fixed servers (with some exceptions I know). It also means that Non Disclosure Agreements and privacy guarantees have to be built in for whoever is working with these logs. |
| Security and ITmailinglists : some are spam havens [belsec] [Belgian Security Blognetwork] Posted: 13 Oct 2008 04:01 AM CDT |
| Posted: 13 Oct 2008 03:12 AM CDT |
| Security ideas for your mom revisited [Security For All] Posted: 13 Oct 2008 12:39 AM CDT
While I completely concur with Julie’s sentiments, isn’t everybody aware of the risks of our Web 2.0 lives? Aren’t there plenty of wise and erudite security experts providing all of the information that everyone needs to know about being secure? And what about all the excellent and ubiquitous security suite software packages available? Surely a tech savvy person like Julie has nothing to be concerned about. And clearly if you are a Republican VP candidate the Feds are quick to enforce even the most trivial security breaches at least as long as the Feds are Republicans. Sorry couldn’t resist. Unfortunately all of the preceding rhetorical questions are pure irony. Phillip Hallam-Baker’s Web Security Blog article “Zero Overhead Security” sums it up this way.
A good part of the problem can be laid our door, fellow security professionals. We can certainly build brilliant complex software and our marketing and sales brethren can sell the heck out of it. But there is something very wrong when at the end of the day someone like Julie is left with this anemic solution.
So why do I say this is anemic? Isn’t this exactly what we’ve been telling Julie to do? Hasn’t she hit on every “best practice” point? Enough with the ironic rhetorical questions. How about some concrete ideas that Julie or you can give your mom on security that will make a difference. In three earlier articles here, here and here I attempted to build a framework of ideas that mom should consider when getting a new computer and going online. What’s missing from those articles are specific details. So without further ado: Security Ideas for Mom - Revisited
I’m sure there are other good, and straightforward ideas for securing mom’s computer. I would love to know about them. I would also love to hear about problems with the ideas I’ve put forth here [note - blatant pandering for comments]. Maybe we can make things a bit nicer for Julie and mom. Or convince them that the internet is funny again.  |
| Security Bloggers meeting at Hack.lu 2008 (#hacklu) [Security4all] [Belgian Security Blognetwork] Posted: 12 Oct 2008 07:10 PM CDT  Well, all good thing come threefold. After a recent security bloggers meeting in Belgium, an upcoming one in London, I'm trying to organize one at Hack.lu. So all security bloggers and securitytwits are welcome to join me Wednesday 22.10.2008 at 18u in the bar of Parc Hotel (the location of the Hack.lu conference) and we'll see where we go from there. If you are coming, drop me a note (email or tweet) so I'll more or less have a view on the number of people that will come and I can provide you further updates directly. Previous posts:
|
| Apocalyptic Vulnerability Percentages - FUD 101 [Kees Leune] Posted: 12 Oct 2008 07:06 PM CDT While reading RSnake's latest post, I cannot escape the feeling that he's in a very gloomy mood today. His advice: "The truth is, if you have something interactive connected to the Internet, it's probably exploitable in some way, and really, it's not that terrible of a thought considering it's pretty much always been that way." As gloomy as that may sound, it is something that I run into regularly. Too many people assume that the next new (web) app that is getting deployed 1) is absolutely essential for the continuity of the company and 2) must run on an internet-facing web server. Air-gapping a system is probably not that feasible in this day and age (although I still see self-contained networks with only a dial-out modem that gets unplugged when not in use), but using common sense when deciding on the visibility of a system can never hurt! |
| Security Bloggers Meeting at RSA Europe 2008 [Security4all] [Belgian Security Blognetwork] Posted: 12 Oct 2008 06:33 PM CDT  Kevin Riggins from Infosecramblings proposed a Security Bloggers/Twits meeting during the RSA Europe 2008 conference on Tuesday the 28th of October at 8 PM. The location hasn't been set yet. If you are interested in joining us, drop a message with Kevin (email/twitter) or alternatively with me. If you know a good location to meet, ditto. Updates on the meeting as well as coverage of the event will follow soon. Previous post: (Photo under creative commons from ggee's photostream) |
| Belgian Security Bloggers Meeting 1st Edition [Security4all] [Belgian Security Blognetwork] Posted: 12 Oct 2008 06:18 PM CDT  Last Saturday, the Belgian Security Bloggers organized a small get together. It was really fun and interesting to meet some of the other bloggers in real life. No presentations, no workshops, just something nice to eat with a good Leffe and some interesting conversations. It was a more relaxed atmosphere then a security conference. Although not all of the Belgian bloggers were present, the first edition was a success. Something tells me that there will be another edition in the future. Related posts:
|
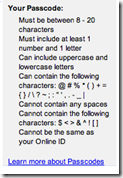
| Bank of America SafePass Authorization [Last In - First Out] Posted: 12 Oct 2008 05:28 PM CDT Unlike American Express, Bank of America seems to have pretty decent account claiming, user id and password requirements. Additionally, BofA allows account holders to set up SMS alerts on various types of account activity. Additionally, BofA automatically uses the SMS based SafePass® for changes to the account, including alerts, e-mail address changes, account claiming etc. You also can set up your account to send SMS alerts on significant account activity and any/all changes to account profiles, including on line charges, charges greater than a specific amount and international charges. The user id and passwords are also allowed to be significantly more complex than American Express, allowing more than 8 characters and permitting various non-alphanumeric characters.
These features, plus the availability of merchant specific temporary credit card numbers (ShopSafe®) makes the banking experience appear to be much closer to what one would think was needed for 21st century banking. |
| 7 Information Security Lessons You Can Learn By Watching The Movie JAWS [Writing Secure Software] Posted: 12 Oct 2008 02:59 PM CDT If your are a security practitioner involved in risk analysis and incident response processes I strongly recommend watching the movie Jaws  since this movie has all the elements to understand how human behaviour and business factors play in information security risk management and incident response decision making. One thing you realize is that risk awareness never comes first. We are humans and as humans we respond to risk in stages such as: (1) denial, (2) awareness, (3) responsibility, (4) action. Risk denial probably comes from the fact that till we (as people or as business) are not impacted directly or till we witnessed that we could be impacted we most likely minimize risks. Awareness is probably driven by the fact that we had experienced a loss directly before that caused to raise our level of attention to new and incoming risks. Responsibility comes from feelings (fear) or by duty (role). As human we feel responsible to react to protect our assets such as people, business, family for example. The action is trigger by the need to react to the risk to prevent further sure loss and damage. If you watch the movie from the perspective of a risk manager you can see all these elements, in particular the major information security lessons that I think can be learn from the movie are: since this movie has all the elements to understand how human behaviour and business factors play in information security risk management and incident response decision making. One thing you realize is that risk awareness never comes first. We are humans and as humans we respond to risk in stages such as: (1) denial, (2) awareness, (3) responsibility, (4) action. Risk denial probably comes from the fact that till we (as people or as business) are not impacted directly or till we witnessed that we could be impacted we most likely minimize risks. Awareness is probably driven by the fact that we had experienced a loss directly before that caused to raise our level of attention to new and incoming risks. Responsibility comes from feelings (fear) or by duty (role). As human we feel responsible to react to protect our assets such as people, business, family for example. The action is trigger by the need to react to the risk to prevent further sure loss and damage. If you watch the movie from the perspective of a risk manager you can see all these elements, in particular the major information security lessons that I think can be learn from the movie are:Lesson #1: The first approach toward risk is to either ignore it or minimize it. For example, the movie jaws is about the risk of being killed by a shark attack. So there is a shark out there in the ocean and has already made a victim (a girl student during a skin-dipping swim after a college party). This is the opening scene of the movie. The police finds the remains of the girl body. The remains are a clear indication of a shark attack. The policeman knows for sure is a shark attack but while filing the report on the incident is advised by the major of the city to not report about the shark as the cause of the incident and rather something else. This is required for not scaring off coming tourists to the town beaches. How this lesson applies to IS risk? A company had a security incident and corporate customer data was compromised as a result. The attack indicates that a fraudster got customer data by breaking into the database through a web application. The business decides to file a defect report that the web site application has some functional defects that need to be fixed. The customers are notified that customer data where compromised but that this was a functional problem that is now under control. Lesson #2: When security vulnerabilities are found and fixed you also gain a false sense of security.The shark attack again and makes another victim: a young kid swimming. The incident cannot be ignored since happens in complete daylight with a lot of witnesses. The mother of the kid is devastated and demands an investigation. In the mean time a shark is caught by fisherman. The shark is shown to the public as proof that the beaches are no-longer at risk of shark attacks. How this applies to IS risk? The company did not fix the web application vulnerability that is the cause of the exploit so we had another attack. Since now the information about the vulnerability is public, the company needs to do something. The company releases information to the public that the publicly disclosed vulnerability has been fixed and customers can come to the site securely business as usual. Lesson #3: When internal security solutions do not mitigate the risks, you most likely ask for help from outside such as by hiring a security expert/consulting company. This might point to solutions that you are hesitant to implement since can be very costly The policeman of the city where the shark attack takes place asks a researcher of the US Oceanic Institute for help. The researcher comes to town and starts the investigation about the shark attack. He soon realizes that this is a case of a white-giant tiger shark attack. The shark that was believed to be the one killing the two swimmers and shown to public is identified not to be the one that made the killings. This is based upon the fact that there are different teeth marks between the jaw of the shark and the ones in the victims body. The researcher explains the results of his analysis to the policemen and recommends an action for fishing the killer tiger shark. After meeting with the policemen and the major it still decided not to. How applies to IS risk? The company declares that knows what the security holes are, a security consulting company is asked to identify the web application vulnerabilities and run some security tests. Security researchers look at the web application scan reports and results of the security tests and conclude that even if some of the identified vulnerabilities can be exploited for the attacks, other potential security flaws can be exploitable too. Fixing these security flaws might actually require to re-engineer the application. The business is still undecided whether to pursuit this recommendations since require very expensive changes. Lesson #4: When the security problem gets bigger and noticed by senior management it cannot be ignored and it is decided to act The shark attacks again and this time even more deadly, the people are now scared and demand prompt action to the major of the city and the policeman to kill the shark. After the major of the city and the policemen hear complains at a public hearing, they decide to finance a mission to kill the shark. How applies to IS risk? Fraudsters break again to the site and this time the losses get noticed by seniot management. The company now decides to put resources and spend money to identify the root cause of these attacks and ask engineering to provide proved risk mitigation solutions. Lesson #5: The first approach to deal with information security attacks from the defensive perspective is to detect the intrusions and pinpoint the threat sources. The policemen, the shark hunter and the researcher use different techniques to locate the shark such as by hooking it with floating devices. For a moment the shark is located and traced and is within reach for being killed. How applies to IS risk? The company installs intrusion detection systems and intrusion prevention systems. Once an alert from the IDS is triggered, it is decided to block the IP address of the source. Lesson #6: If your deal only with the symptoms instead of the root causes the risk is not mitigated.The shark outsmarts the fisherman, the oceanographer and the policeman by breaking the hooks where the floating devices where attached and attacking the boat unnoticed. The shark attacks the boat directly causing it to sink. How applies to IS risk? The fraudster bypasses the IDS with signature evasion techniques and continues the attack undetected, a device that pinpoints the IP address for blocking it does not stop the attack since the attacker uses fast-flux botnet techniques where the source IP is dynamically changed in real time. Lesson #7: By tackling the attack root causes finally the risk is mitigated During the wrestling with the shark, the policemen is able to throw a gas tank on the shark jaw and by shooting it with a rifle finally causes the tank to explode and kills the shark. How applies to IS risk? Finally is is decided to go after the root causes of the attack identified with an attack tree analysis where all probable attack patterns are simulated. By threat modeling the application, the attack surface of the application is identified as well as the entry points. The entry point that is most likely used by fraudster is blocked access and the possible transactions that can be performed through this entry point are disabled. Web application logging and tracing are enabled to detect and trace and correlate possible threat events. These web application changes finally prevents the attack to occur. The logs collected during the attacks are provided to law enforcement. These logs provide enough information to catch the fraudster. |
| IDApython - Sort imported functions by xrefs count [Francois Ropert weblog] Posted: 12 Oct 2008 10:24 AM CDT A good understanding of a binary starts with reconnaissance. The goal of this article is to help the binary reverser during his first analysis. I haven’t found IDA function or script which can tell “the most used imported function is blabla”. That’s why I wrote an IDApython snippet that browse the IAT through the .idata section and sort imported functions by cross-references count. Let’s take an example by running the script over omg.exe. We took a grasp (after auto-analysis) about which imported functions the binary call the most and the least: printf => 15 The analysis inform the reverser that printf, sleep and isdebuggerpresent are the most imported functions used. Lots of printf() and sleep() for user interaction. isDebuggerPresent talk for himself :-) Here’s the IDApython script:
def find_xrefs (name,address): def find_imports (start_address,end_address): while import_ea < end_address: if len(import_name) > 1: occurence = find_xrefs (import_name,import_ea) import_ea += 4 return imports_list seg_start = SegByName(”.idata”) for name,occurence in imported: Copy-Paste then save under “%IDADIR%\python” then execute it with ALT-9. Enjoy! |
| New Features in User Provisioning Products [The IT Security Guy] Posted: 12 Oct 2008 12:19 AM CDT My article on TechTarget's SearchSecurity web site about new features in user provisioning products came out this week. User provisioning is a pretty basic technology but expect advances in the future with the growth of technologies like virtualization and Software as a Service (SaaS). Both of these present challenges to traditional identity and access management systems overall but to user provisioning, in particular. |
| WPA Enterprise made easy with the Napera N24 [Napera Networks] Posted: 11 Oct 2008 07:19 PM CDT Wi-Fi security has been a challenge since the technology first came on the market. In 2001 the WEP protocol was shown to be fatally flawed, and was replaced by WPA in 2003. In 2004 the 802.11i standard for WPA2 became available and WEP was officially laid to rest. With revelations this week of a Russian firm selling a GPU accelerated key cracker for WPA Pre-shared key mode (WPA-PSK, also known as personal mode) Wi-Fi security is in the headlines again. Brute force cracking is not new, but the speed of this attack checking hundreds of millions of passwords per second combined with the typical simplicity of shared WPA-PSK passwords supports the argument that WPA-PSK is now insufficient to protect commercial wireless networks. Results of the Napera Network Test showed nearly half the respondents still relying on weak WEP or WPA-PSK security. Poor wireless security was one of the root causes of the TJX hack which remains the largest security breach in the United States, and wireless flaws are an easy way for hackers to gain access to a target network. An IT manager using WPA-PSK to protect a wireless network would have to be lucky to detect such an intrusion. With our recent 1.2 release for the Napera N24, we’ve enabled IT managers to easily deploy the most robust Wi-Fi security by using WPA Enterprise authentication with their existing Active Directory installation. The advantages of using WPA Enterprise with the Napera N24 are as follows. (i) Wireless users provide their Active Directory username and password to log on to the network. No shared passwords are used, and when a user is removed from Active Directory, their wireless network access is automatically revoked. (ii) Wireless network logins can be tracked to each user, which removes the need for shared passwords common to WPA-PSK. (iii) Guest usernames can be created on the Napera N24 and are automatically granted wireless access to the Internet while protecting the rest of your network. (iv) WPA Enterprise provides far more robust security than WPA-PSK and is not vulnerable to any known attacks or the brute force cracking tools released this week. (v) The Napera N24 uses NAP to check the health of each device when it connects, ensuring vulnerable laptops are current with operating system, antivirus and antispyware updates before connecting to the corporate network. Using the Napera N24 to deploy WPA Enterprise doesn’t require knowledge of RADIUS, EAP, 802.1X or self signed certificates. Previously WPA Enterprise deployments included all of these components plus the need to deploy certificates to end user PC’s. The Napera N24 was designed with a RADIUS server and a valid certificate built in so the pain involved with deploying new servers and home grown certificates can be bypassed entirely. Once your Napera N24 is installed with a static IP and joined to your Active Directory domain, configuring WPA Enterprise is as simple as the following four steps. 1. Plug your wireless access point into a switched Ethernet port on the Napera N24. We’ve successfully deployed Cisco, HP, D-Link, Linksys and Netgear WAP’s with the Napera N24. Any WAP that was Wi-Fi certified after March 2006 will support WPA Enterprise. 2. Login to MyNapera.com and select the Configuration panel. Under the Authentication tab, enable the Wi-Fi RADIUS authentication option and enter a shared secret, which can be a password of your choice.
3. Log into your wireless access point’s administration page and enable WPA Enterprise. Enter the static IP address of the Napera N24, and the shared secret you defined in step 2. Any additional options such as timeouts and port selections can usually be left as the defaults. 4. You are ready to connect! Most operating systems support WPA Enterprise automatically, including Windows XP SP2 or later, all flavors of Vista, and Mac OS X 10.3 or later. The iPhone and BlackBerry also support WPA Enterprise with recent firmware. Anyone connecting to the wireless network will now be prompted for a username and password. Employees with Active Directory credentials will be granted full access to the network. Guest users created on the Napera N24 will automatically be recognized. The MyNapera.com dashboard displays a summary of recent authentications, and provides a full audit trail of users and devices.
Now that WPA-PSK has finally been put out to pasture, WPA Enterprise provides the most robust security for wireless networks. The Napera N24 enables you to deploy WPA Enterprise painlessly with your existing access points, enjoying the best possible security and unmatched visibility across your wireless network. |
| belsec in top 10 most popular skynetblogs [belsec] [Belgian Security Blognetwork] Posted: 11 Oct 2008 06:42 PM CDT |
| Late 2008: ICANN Still Broken [Infosecurity.US] Posted: 11 Oct 2008 03:41 PM CDT |
| GNUCITIZEN - Advanced Clickjacking Explained [Infosecurity.US] Posted: 11 Oct 2008 03:40 PM CDT |
| Security week reading [Francois Ropert weblog] Posted: 11 Oct 2008 03:55 AM CDT This past week I felt the need to learn other stuff than networking related topics. As you may know (or not), I’m not only a TCP/IP fanatic. Too, you can speak me about everything tricky and hacky, reverse engineering, operating systems internals or all sort of stuff including MicroVAX exploits development and shellcodes :-) If I had to made a mix of my week’s reading, here it is: Those books comes from No Starch Press. Not very surprisingly for humans like you, like me :) For the web exploration, Google Chrome helps me building this “classic” list:
Off-topic: - My FON wireless access has been disabled for no signal since three weeks. Since yesterday, beacons are sent over the air. - In past weeks discussions I had with peers, I try to understand SDR Software Defined Radio but I lack fundamentals. |
| Holiday Weekend Off… [Infosecurity.US] Posted: 10 Oct 2008 07:18 PM CDT |
| World Bank Denies Fox News Reports of Multiple Breaches [Infosecurity.US] Posted: 10 Oct 2008 07:17 PM CDT |
| Happy Columbus Day 2008 [Infosecurity.US] Posted: 10 Oct 2008 07:14 PM CDT |
| Maui Vacation 2008 [Jeremiah Grossman] Posted: 10 Oct 2008 07:02 PM CDT  Some people are busy and then some people have my schedule. Typically my time is spent in thirds -- a third public facing (conferences, presentations, writing, media, etc.), a third speaking with customers, and the remaining third performing R&D. Oh, and a whole lot of time in spent in the air, check out the wall of fame. ;) Fortunately now that the whole clickjacking craziness has died down a bit and the quarter is over, time for a much needed break. Starting this weekend I'll be heading back home to Maui for a couple of weeks of R&R. Beach, surfing, BJJ, play with the kids, sleeping, checking out my dad's home built hydrogen powered jeep and whatever else I can fit in. From there I'll be off to Malaysia for a couple of days attending Hack in the Box Malaysia and delivering a keynote speech. Emails and blog comments are unlikely going to be responded to during that time. Unplug and unwind. See you all in November. Some people are busy and then some people have my schedule. Typically my time is spent in thirds -- a third public facing (conferences, presentations, writing, media, etc.), a third speaking with customers, and the remaining third performing R&D. Oh, and a whole lot of time in spent in the air, check out the wall of fame. ;) Fortunately now that the whole clickjacking craziness has died down a bit and the quarter is over, time for a much needed break. Starting this weekend I'll be heading back home to Maui for a couple of weeks of R&R. Beach, surfing, BJJ, play with the kids, sleeping, checking out my dad's home built hydrogen powered jeep and whatever else I can fit in. From there I'll be off to Malaysia for a couple of days attending Hack in the Box Malaysia and delivering a keynote speech. Emails and blog comments are unlikely going to be responded to during that time. Unplug and unwind. See you all in November. |
| A great weekend for Napera at SMB Nation [Napera Networks] Posted: 10 Oct 2008 04:06 PM CDT Last weekend was the annual West Coast conference for SMB Nation. We were excited to get out there and talk to people about the Napera approach to solving security challenges in SMB and SME networks. Our ideas resonated well with SMB Nation attendees, and well known SMB security blogger and speaker Amy Babinchak thought Napera was best of show, which was very gratifying. This was my second SMB Nation, and there was a great mix of people from around the US and around the world. One of the things I love about SMB Nation is that it’s a very friendly show. Pretty much everyone has a down to earth approach to solving IT challenges that you don’t always see at larger conferences. Attendees also appreciate the difference between a product like ours that was designed to work in smaller networks and products from large enterprise vendors that are shoehorned into the SMB and SME market. Thanks to Harry Brelsford and Chris Bangs for a successful conference and thanks to everyone who stopped by the Napera booth. See you next year!
Bryan, Harry and Liz with Dean Wake of Gaeltek Technology Solutions who won our iPod raffle |
| links for 2008-10-10 [Andrew Hay] Posted: 10 Oct 2008 04:02 PM CDT
|
| Happy Thanksgiving To Our Canadian Friends and Relatives [Infosecurity.US] Posted: 10 Oct 2008 03:59 PM CDT |
| Security Provoked (Episode 12) [Security Provoked] Posted: 10 Oct 2008 03:25 PM CDT Part 2 of a conversation with Dr. Peter Tippett of Verizon Business. ….ah, well, seems someone’s reconfigured the blog so that the old approach to embedding isn’t working. While we get that figured out, you can link to the episode here. Gah! |
| World Bank Network Penetrated [Infosecurity.US] Posted: 10 Oct 2008 12:12 PM CDT |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |




 Information security for everyone is a big deal with me. I even have a weblog devoted to that very ideal. So
Information security for everyone is a big deal with me. I even have a weblog devoted to that very ideal. So 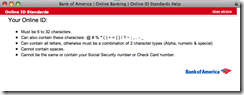


![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=87ba479f-afc8-4f91-bd6f-de9ea24f4479)

No comments:
Post a Comment