Spliced feed for Security Bloggers Network |
| RSA Europe - Day 2 [Infosec Ramblings] Posted: 28 Oct 2008 03:48 AM CDT Hello again people. In a bit of a time pinch, so here is the agenda for the day for those who care
Should be an interesting and busy day. Kevin Posted in Uncategorized |
| DMCA Anniversary - 10 years of FAIL! [Amrit Williams Blog] Posted: 28 Oct 2008 01:07 AM CDT Today is the 10th anniversary of the Digital Millennium Copyright Act (here), which was signed into law by President Bill Clinton on October 28th, 1998. The act essentially criminalizes the production and dissemination of technology, devices, or services intended to circumvent measures (such as DRM) that control access to copyrighted works and it also criminalizes the act of circumventing an access control, whether or not there is actual infringement of copyright itself, it essentially makes DRM hacking, among other things, a crime. The EFF (Electronic Frontier Foundation) noted (here)…
Trying to address the problem through technology is also a losing battle. Sony tried to prevent digital copying of CD's with its Key2Audio technology (here). They spent millions and it was defeated with a $1.35 sharpie marker. Their attempts to install a rootkit were even less successful (here) and the backlash was deafening. Students at Georgia Tech are working on a technology to block the functioning of video cameras in movie theaters (here), and Paris-Based Thomson is working on a technology that inserts "artifacts" into the the frame that are picked up by camcorders (here), essentially the movie could be covered with watermarks such as "you are viewing a pirated film". Unfortunately, those who want to pirate are clever and will find ways to bypass all these laws and mechanisms. Millions, perhaps billions, will be spent trying to stop copyright infringement. Piracy will continue, virtually unimpeded, and there is very little the media industry or the government can do about it. Well except one thing. That is to lower the demand for pirated media. Bollywood does this by releasing DVD's at the same time movies are released in the theater. Wouldn't this lower theater profits you ask? The same thing was said about VHS and video rental stores, but sometimes you really want to see a movie in the theater - anyone stand in line for Batman, Indian Jones, or Star Wars Episode III, even though all of these movies were available on torrent sites prior to release? Hollywood seems to have a lack of understanding for the appetite of the consumer. If they want to be successful at limiting piracy, and all they can do is limit piracy, they have to lower demand. They can lower the demand for pirated media by releasing movies through DVD, cable TV, and the Internet at the same time movies are released in the theater. They can lower pirating of music by taking advantage of innovation around the distribution and licensing of higher quality recordings. They can find unique ways to partner, market, and charge for them. Simply put they either figure out how to leverage the new digital mediums to satisfy the consumers appetite or they lose out on billions of dollars in potential revenue and licensing fees, and trust me if any group can figure out ways to keep the gold plated toilets at 50 cents mansion shiny and the Porsche humming in Lars Ulrich’s 12 car garage, it will be the the MPAA and the RIAA. To learn more: The EFF (Electronic Frontier Foundation) has been tracking the unintended consequences of the DMCA over the last 10 years (here)  |
| Links for 2008-10-27 [del.icio.us] [Anton Chuvakin Blog - "Security Warrior"] Posted: 28 Oct 2008 12:00 AM CDT
|
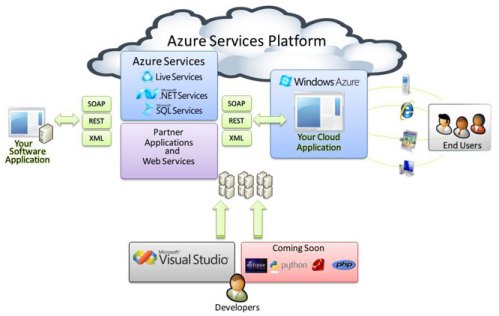
| And on through the Fog of Microsoft’s “Cloud OS” Azure [Amrit Williams Blog] Posted: 27 Oct 2008 05:50 PM CDT Ray Ozzie, Microsoft Chief Software Architect and creator of Lotus Notes, announced Windows Azure today during the Windows PDC (Professional Developers Conference) event in Los Angeles (here). Azure coincidentally sounds an awful lot like du Jour, as in “technology hype du Jour” Windows Azure, previously code name “Red Dog” is a hosted suite of services, including a highly scalable virtualization fabric (a what?), scalable storage, and an automated service management system. It is pretty close to the Amazon web services platform EC2 (Elastic Compute Cloud), except for the whole “Only Microsoft” thing. Hoff was on the ball and posted his thoughts earlier today (here)
You can “experience” Azure here (here) also check out Manuvir Das, Director in the Windows Azure team explain the Windows “Cloud OS” (here) or Steve Marx presentation, Azure for Developers (here) You can read my previous thoughts on cloud-computing (here) and (here)  |
| Into the (data) breach [StillSecure, After All These Years] Posted: 27 Oct 2008 02:28 PM CDT
Well this years survey is here. You can click here and go take the survey. The SC Mag folks will publish the data in January (one month after their initial SC World Congress in NY). So give Illena and crew a hand. Take a moment to take the survey and be sure to see the results in a few months. Thanks! |
| Beat Poet - Chris “Doby Gillis” Hoff [RiskAnalys.is] Posted: 27 Oct 2008 02:04 PM CDT |
| on HITB 2008 Conference [Anton Chuvakin Blog - "Security Warrior"] Posted: 27 Oct 2008 01:10 PM CDT Not to pretend to steal Halvar Flake's glory, but I just got my own "fun" international travel story, which also spells bad news to those who wanted to hear my fun keynote at Hack In The Box 2008 in Kuala Lumpur, Malaysia. To make the short story ... even shorter :-), I got kicked off my flight since my passport is only valid 5.5 months in the future and Malaysia requires that visitors' passports are valid for 6 months from the date of arrival (not that they make it anywhere near clear on their embassy website or anything :-)). What makes it funnier is that I got so used to US dates of month/day/year that I actually was genuinely shocked when they said "you passport is not valid for 6 months" while it clearly said "Expires on 8/4/2009" ... So much for Kuala Lumpur :-( Back to work now. |
| CLOUD COMPUTING - STORMY WEATHER? [RiskAnalys.is] Posted: 27 Oct 2008 10:46 AM CDT Lots being written about the Cloud, most of it quite dark and gloomy. In fact I’m surprised, that Hoff hasn’t got a preso spooled up called “The Toxic Cloud” or something similarly ominous for his next speaking tour.
Let me ask you - if you had to put your money on one of those horses, considering your average profit-preoccupied business, which would it be? I’d put my bottom dollar on the thoroughbred named “Cost Center Reduction”, to place. WHO ARE WE TO STAND IN THE WAY OF “PROGRESS”? I’m always fond of Jack’s rule that the role of information risk management boils down to three deceptively simple premises:
So it would seem antithetical to the charter of the Chief Security Officer to stand in the way of progress as embodied by “cloud computing” (not to mention dangerous to long-term job security). And I think that this presents opportunities to discuss strategies for managing risk, strategies that aren’t too theoretical and have practical application (though actual “cloud” use by enterprises may be rare at this point). ON RISK REDUCTION IN THE CLOUD (or, How To Learn From the Shortcomings of PCI DSS) The good news is, there’s already a well-established model for managing the risk around outsourcing the processing of “confidential” information. The bad news is, that model kinda sucks it. The Payment Card Industry, known as the “PCI” or “meal ticket” to many in the industry, faced a similar problem with the introduction of GLBA. As I see it (and I’m not at all close to the PCI, at all, so this is all just abstract soliloquy) the PCI had one of two choices when faced with the prospect of other people managing their sensitive information:
(Martin, you may recall our Twittering about PCI a while back. This is the crux of my view on the subj.) Now fortunately, the CSO’s of the world are going to be a little more “invested” in protecting the information they are stewards over, and unlike the PCI, will remain primarily responsible for the C, I, & A of the data in the Cloud. The cool thing is, this actually presents a great opportunity to start building a meaningful model for co-management of risk! In fact, we can take the PCI model of contractual risk transference but modify where it goes all wrong, and start working to create something better. And we can start by euthanizing some faulty assumptions. JUST HOW INFORMATIVE IS PCI DSS? What might be the.greatest.mistake of the standards compliance mentality is the assumption of value for the past-state measurement. That is, I believe that the CSO needs more than some “past-state” assurance in order to understand their risk. If you look at the concept of “PCI compliance” it really is an examination of a past state of nature that is assumed to be relevant to current and future states. Many people (myself included) are not at all convinced that this past-state is nearly as informative as those who mandate it’s measurement believe it to be. That’s not to condemn past-state measurements as completely non-informative, they most certainly are useful. It’s just that no self-respecting CSO sleeps well because they were deemed “PCI compliant” 10 months ago. They sleep well because they have good visibility into current-state information and confidence in their strategy concerning future-state (based on that visibility and the outcomes of sound IRM models). MOVING PAST THE VULNERABILITY SCANNER INTO INTELLIGENCE AND WISDOM So realizing this new importance (to me, at least) concerning visibility and IRM models, I’m lead to the conclusion that if we are to manage risk in the Cloud, we’ll have to move beyond “PCI Compliance” or the concept that some regular “audit” of controls in place at the host is all we need to understand our ability to manage risk. No, the CSO must have good information concerning current and probable future states. This is that “visibility” I spoke of above. In fact, we’ll need significant amounts of piercing, transparent visibility. And in order to gain that visibility, our insight into Cloud Risk Management must include significant provisions for understanding a joint ability to Prevent/Detect/Respond as well as provisions for managing the risk that one of the participants won’t provide that visibility or ability via SLA’s and penalties . These SLA’s must be expressed in measurable terms (more visibility), and those metrics must have their roots in the things that help understand how we manage risk (those aforementioned IRM models). THE CLOUD COMPUTING SECURITY SILVER LINING (sorry couldn’t resist) As I mentioned earlier, I do see an opportunity to create insight. The need for visibility and IRM models would allow us to create a “guidance” if you’ll allow me to use the term. Not a standard or a “best practice” to audit by, but simply a reference document that says “if you’re going to put information on somebody else’s systems and still hold some significant responsibility for that information, here’s the considerations, why they are considerations, and how you might go about collaborating on the management of risk”. And I think that if we undertake this journey, there is going to be a lot of growth and risk management innovation along the way. But keen insights into what it means to manage risk will be necessary, and secure and forthright collaboration will be of absolute importance. I say that last bit because, if these pundits are right about the utility of a hosted computing model - the Cloud will happen regardless of the CSO’s ability or desire to manage it. |
| NAISG - Birth of the Atlanta Chapter [Andy, ITGuy] Posted: 27 Oct 2008 08:30 AM CDT It seems that technology is filled with it's share of things to do. From local chapters of national organizations to small meet-ups between friends who all work in technology. Everywhere you look there are conferences on all things technology. The bad thing about these events is that often they are not what you are looking for. If you are a pen tester then an ISACA meeting may not be your cup of tea. If you are a firewall jockey then InfraGard may not be what you are looking for. Then there is the question of value. Is the organization giving you value? Does it help you learn, connect with others, grow your career? Then when it comes to the conferences most of them are out of reach for you unless you either live close enough to not have travel expenses, you get a free pass or your company is willing to pay. A conference can easily run $4k before you know it. Even if you get a a press pass for some events the hotel, travel and per Diem cost alone can break the bank. In Atlanta there are a few different opportunities to get involved with different organizations. There is ISSA, ISACA, InfraGard, and several other local groups that meet weekly, monthly, quarterly or whenever they get around to it. I've not been involved in any of these for a few different reasons. Value, Time, lack of content, etc... Well, for me at least that is about to change. Starting next month Atlanta will be the home of a new chapter of the NAISG (National Information Security Group). I'm supporting it for a few different reasons. (Now comes the full disclosure part) I am on the Advisory Council for the chapter so that does sway my opinion a bit, but not only that but I'm supporting it because I like the mission of the NAISG. It focuses on Information Security. It's not a platform for vendors to hock their wares, it's a good mix of "in the trenches" technology and soft skills that are needed to succeed in some areas of business. I also like it because there is no fees associated with it. I don't want to pay a national chapter, a local chapter, and a registration fee just to join a group that is asking me to give of my time and resources. Anyway, the first meeting will be Wednesday Nov 12, 2008 at 7:00 PM. We will be meeting at 3030 Royal Blvd. South, Suite 220, Alpheretta, GA 30022. We are being hosted by Upgrade IT Consulting Services. There will be pizza and drinks provided. The program will be given by the Founder and President of NAISG, Brad Dinerman. He will be speaking on "Employee Monitoring and Surveillance" You can read more about the meeting at the Atlanta chapter page of the NAISG web site. If you are in the Atlanta area we'd love to have you join us and become an inaugural member of the Atlanta chapter of NAISG. Tell your friends and co-workers to come also. Hope to see you there! |
| Security Briefing - October 27th [Liquidmatrix Security Digest] Posted: 27 Oct 2008 05:59 AM CDT  I hope I have a good Monday. Signed, Click here to subscribe to Liquidmatrix Security Digest!. And now, the news…
Tags: News, Daily Links, Security Blog, Information Security, Security News |
| RSA Europe 2008 starts today… [Infosec Ramblings] Posted: 27 Oct 2008 04:45 AM CDT Good morning everybody or at least those who are in a time zone similar to GMT :) RSA Europe starts today and I am sitting in the press room scheduling out my day. For those interested, my itinerary follows: 10:00 - Keynote - Arthur W. Coviello, Jr. - Executive Vice President EMC 10:40 - Keynote - Panel - Moderator Christopher Kuner - Partner and Head, Hunton & Williams 11:30 - Chris Batten - Managing Director, Acumin 13:15 - Amichai Shulman - Co-Founder & CTO, Imperva 16:00 Neil Costigan - Technical Advisor, BehavioSec - Peder Nordstrom - CTO, BehviorSec There is a reception this evening and of course the exhibition hall is open all day. Should be a busy day. Have a great morning, afternoon or evening as the case may be. Kevin Posted in rsa europe 2008 Tagged: rsa europe 2008 |
| Turkish Police Beat Crypto Key From Suspect? [Liquidmatrix Security Digest] Posted: 26 Oct 2008 08:54 PM CDT  Chris Soghoian has another interesting piece on his CNET blog. Wow, I’m certainly glad that I’ve not had the displeasure of police interrogation. But, to think of one in some countries around the world makes the blood run cold. One such example is apparently, Turkey. From CNET:
Now, comments alleged to have been made by Howard Cox, a US Department of Justice official, shed some light on the possible means in which the Turkish police extracted the password for his encryption software.
Volun…damn. OK, the tongue and cheek imagery of a black and white film gives way to this image.  Guilty or not, this is not the right way to do things. |
| 100 Mile Constitution Free Zone [Emergent Chaos] Posted: 26 Oct 2008 01:00 PM CDT  Government agents should not have the right to stop and question Americans anywhere without suspicion within 100 miles of the border, the American Civil Liberties Union said Wednesday, pointing attention to the little known power of the federal government to set up immigration checkpoints far from the nation's border lines.See Wired, "ACLU Assails 100-Mile Border Zone as 'Constitution-Free'." In closely related news, a Washington Municipal Court in Tacoma (pictured) has ruled that "showing ID to cops not required." I found this map to be pretty shocking on two levels: first, and most importantly, I hadn't realized that it was 100 miles from any border. (And if it really is any border, do the international airports count?) Which brings me to my second point: it was pretty surprising to see not only that two thirds of Americans live within 100 miles of a border, but that there are only a few major cities (Denver, Atlanta) which are not in that zone. I also feel personally invaded to know that every time I use a ferry in Seattle, they scan my license plate and record that travel. The map is a link to the ACLU's page on the issue. |
| Twitter Terrorism? [HiR Information Report] Posted: 26 Oct 2008 08:20 AM CDT Oh REALLY? Could Twitter become terrorists' newest killer app? A draft Army intelligence report, making its way through spy circles, thinks the miniature messaging software could be used as an effective tool for coordinating militant attacks. I've written about Twitter As A Threat before, but this is completely different. The US is still looking for tools the terrorists are using (you know, like the ONE time that someone tried to slip explosives by the security checkpoints in a pair of shoes?) and not finding anything but the dumbest, sloppiest and most ham-fisted terrorists. Check this out, and try to refrain from falling out of your chair in laughter: Scenario 1: Terrorist operative "A" uses Twitter with… a cell phone camera/video function to send back messages, and to receive messages, from the rest of his [group]... Other members of his [group] receive near real time updates (similar to the movement updates that were sent by activists at the RNC) on how, where, and the number of troops that are moving in order to conduct an ambush. Wait! Terrorists are on MySpace and Facebook now, too?! Look, guys. We get it: Terrorists communicate. Terrorists can communicate the same way other people communicate. What's next? "Terrorists might drive cars?" Looks like we'd better beware of anyone found driving a Toyota. Seriously, how much money do we have to waste on reports like this, which state the obvious while putting a sensational movie-plot spin on things? |
| Cloud Computing - The Good, The Bad, and the Cloudy [Amrit Williams Blog] Posted: 26 Oct 2008 12:06 AM CDT And on the second day God said “let there be computing - in the cloud” and he gave unto man cloud computing…on the seventh day man said “hey, uhmm, dude where’s my data?” There has been much talk lately about the “Cloud“. The promise of information stored in massive virtual data centers that exist in the ethereal world of the Internet, then delivered as data or services to any computing device with connectivity to the “Cloud“. Hoff recently ranted poetic on the “Cloud” (here) and asked the question “How does one patch the Cloud” (here) So what the hell is the cloud anyway and how is it different from ASPs (application service providers) and MSPs (managed service providers) of yesteryear, the SaaS/PaaS/CaaS (crap as a Service) “vendors” of today and the telepathic, quantum, metaphysical, neural nets of tomorrow? I am not going to spend any time distinguishing between services offered by, or including the participation of, a 3rd party whether they take the name ASP, SOA, Web services, Web 2.0, SaaS/PaaS, or cloud-computing. For whatever label the ‘topic du jour’ is given, and regardless of the stark differences or subtle nuances between them, the result is the same - an organization acquiesces almost complete visibility and control over some aspect of their information and/or IT infrastructure. There should be no doubt that the confluence of greater computing standardization, an increasing need for service orientation, advances in virtualization technology, and nearly ubiquitous broad-band connectivity enable radical forms of content and service delivery. The benefits could be revolutionary, the fail could be Biblical. Most organizations today can barely answer simple questions, such as how many assets do we own? How many do we actively manage and of these how many adhere to corporate policy? So of course it makes sense to look to a 3rd party to assist in creating a foundation for operational maturity and it is assumed that once we turn over accountability to a 3rd party that we significantly reduce cost, improve service levels and experience wildly efficient processes - this is rarely the case, in fact most organizations will find that the lack of transparency creates more questions than they answer and instill a level of mistrust and resentment within the IT team as they have to ask whether the company has performed something as simple as applying a security patch. The “Cloud” isn’t magic, it isn’t built on advanced alien technology or forged in the fires of Mount Doom in Mordor, no it is built on the same crappy stuff that delivers lolcats (here) and The Official Webpage of the Democratic Peoples Republic of Korea (here), that’s right the same DNS, BGP, click-jacking and Microsoft security badness that plague most everybody - well plague most everybody - so how does an IT organization reliably and repeatably gain visibility into a 3rd parties operational processes and current security state? More importantly when we allow services to be delivered by a third party we lose all control over how they secure and maintain the health of their environment and you simply can’t enforce what you can’t control. In the best case an organization will be able to focus already taxed IT resources on solving tomorrows problems while the problems of today are outsourced, but in the worst case using SaaS or cloud-computing might end up as the digital equivalent of driving drunk through Harlem while wearing a blind fold and waving a confederate flag with $100 bills stapled to it and hoping that “nothing bad happens”. Yes cloud-computing could result in revolutionary benefits or it could result in failures of Biblical proportions, but most likely it will result in incremental improvements to IT service delivery marked by cyclical periods of confusion, pain, disillusionment, and success, just like almost everything else in IT - this is assuming that there is such a thing as the “Cloud“ Update: To answer Hoff’s original question “How do we patch the cloud?” the answer is - no different than we patch anything, unfortunately the problem is in the “if and when does one patch the cloud” - which can result in mistmatched priorities between the cloud owners and the cloud users.  |
| Ridiculing the Ridiculous: Terrorist Tweets [Emergent Chaos] Posted: 25 Oct 2008 09:09 PM CDT A group of soldiers with the US Army's 304th Military Intelligence Battalion have managed to top previous military research on terrorist use of World of Warcraft. Realizing that mentioning the word "terrorist" can allow researchers to acquire funding to play the popular MMOG, they turned attention to the popular, if architecturally unscalable micro-blogging system, Twitter. Surpassing the threat-analysis skill of super-spy Chad Feldheimer from the recent documentary "Burn After Reading," they mention not only the threat of "socialists," "communists," and "anarchists," in using Twitter to "communicate with each other and to send messages to broader audiences," but the wider and more up-to-date threats from "religious communities," "atheists," "political enthusiasts," "human rights groups," "vegetarians," and last but not least, "hacktivists." They notably left out delinquent teenagers, so one presumes they don't use systems like Twitter. The Military Intelligence group also discovered that people can use GPS in phones like the Nokia 6210 and Nokia Maps to know where they are. This could let terrorists who want to illegally cross a border know where that border is, or to know that a certain large triangular stone thing is the Pyramid of Cheops (category: Attraction). The report's cutting edge thinking also discusses how terrorists could use voice-changing software such as AV Voice Changer Diamond to make prank phone calls and effectively hide under an abaya. The full report, marked "For Official Use Only," can be found here. It also redacts with a dark gray splash of ink the email address of sarah.e.womer@ugov.gov, from whom you can get a copy of the report if you do not have access to INTELINK, Cryptome, or the Federation of American Scientists. I think the report speaks for itself. I just can't make this stuff up, apart from the bit about hiding under an abaya. |
| Insecurity Theatre [Emergent Chaos] Posted: 25 Oct 2008 03:56 PM CDT  "It's been in the back of my mind since you first came in: How do you get the missile on the trailer into Manhattan?" federal Judge William Pauley III asked.So reports the New York Post, "Security Lapse Let in Naughty Fake Rocket." I was going to comment, but I think I'll just salute. |
| Where Are They Now: Quentin Stafford-Fraser [HiR Information Report] Posted: 25 Oct 2008 09:46 AM CDT  I've looked up to a lot of people in my day, and sometime in the middle of 1998, I was really looking up to the guys at the Olivetti & Oracle Research Laboratory (ORL for short) because they made something that at the time I considered truly groundbreaking and now, more than a decade later, I can't see living without it. If you've been around a while (or you're paying attention to my coffee mug in the photo) you may have guessed I'm talking about VNC, which now has quite a few forks, most of which surprisingly play very nicely with one another. I've looked up to a lot of people in my day, and sometime in the middle of 1998, I was really looking up to the guys at the Olivetti & Oracle Research Laboratory (ORL for short) because they made something that at the time I considered truly groundbreaking and now, more than a decade later, I can't see living without it. If you've been around a while (or you're paying attention to my coffee mug in the photo) you may have guessed I'm talking about VNC, which now has quite a few forks, most of which surprisingly play very nicely with one another.In 1998, I actually wrote an article about VNC in HiR's old text-zine format. Shortly after that, AT&T Swooped in and bought ORL. I contacted the team to ask if they had any of the cool VNC Mugs I saw on their Windows CE page (Archived here) and I actually was told by the team that "they shouldn't, because they had the old contact information on them" but they shipped me a pair of them anyways. Now, some 9 years later they're still some of my favorite mugs from which to quaff my morning coffee: I've got one at work and one at home. QSF wasn't the sole inventor of VNC, but he put quite a bit of work into it and was one of the authors of the initial VNC whitepaper, first published in IEEE Internet Computing. When poring through mailing lists in my early days of using FreeBSD and OpenBSD on the desktop, I'd often run into QSF's helpful tips when dealing with compiling or troubleshooting issues. QSF's also one of the creators behind first Internet meme I ever experienced (in early '94): the coffee-pot web-cam. A few months ago, Frogman pointed me to Status-Q, QSF's blog (via shared articles in Google Reader) and I must say I've been hooked ever since. His blog content offers little in the way of what he's up to for a living these days (hint: the About Quentin link has those details), but it's full of sage advice, useful quotes, and fascinating observations. I'm happy to have run into him again! The entire team of VNC people were and are, in my opinion, "real hackers" and visionaries. They might not be penetration testers or security researchers. They're certainly anything but cyber-terrorists. The team saw a need, filled it elegantly, and built something extensible and open-source that to this day is relied on by more people than I could count. |
| US Military Wants Packs Of Robots To Hunt Humans [Liquidmatrix Security Digest] Posted: 25 Oct 2008 07:35 AM CDT  Well, to hunt down the bad kind or “uncooperative” ones anyway. This has a weird humour element as it manages to conjure an image of Bender calling to “kill all humans”. From New Scientist:
So, the author is concerned where this tech could end up? The US military wants a droid army. What could possibly go wrong?  Oh, riiight. For the full article read on. |
| Comments on the news, this one's NOT overblown [The Security Mentor] Posted: 24 Oct 2008 11:03 PM CDT Run Windows Update. Microsoft released a "Critical" security patch to fix a problem in which any computer running Windows file sharing can be completely taken over with no action on your part. It's less of a worry if you're running Vista, and normal firewalling will stop the attack. But it's still a big concern. When the news broke, I advised clients that before long there would be automated attack programs that unskilled attackers could use, and that attackers would use the new attack to spread infections after getting a toehold by other means. Both have already happened. There's already a self-reproducing "worm" program taking advantage of the security weakness. It's being introduced behind people's firewalls by the usual sort of trickery, but then once it's on one machine it copies itself to the others on the network. It's a little more complicated than that, but now you have the gist. If you use a laptop on the road, make sure you've got a firewall program running on it and that it's set to block Windows file sharing, or turn off file sharing altogether in the Control Panel. |
| Comments on the news: this is overblown [The Security Mentor] Posted: 24 Oct 2008 10:54 PM CDT The headlines said that wireless networking security is now a thing of the past, due to a clever company finding a way to program graphics cards to crack security codes. In a word, no. What they did was speed up existing password-guessing attacks on one flavor of Wi-Fi security, by a factor of 25-100. If you've chosen a good password in the first place, it's not going to be so close to guessable that it matters if someone can guess 25 times faster. And you can really go to town picking a hard password for your Wi-Fi setup, because you only have to type it in when you're installing things. You can use something long and obscure. You can make it up to 63 characters long! I recommend a passphrase, something with multiple words instead of an incomprehensible set of letters and numbers. Visit http://www.diceware.com for a system that lets you roll dice to pick short words from a big list. As long as you've chosen them randomly, a passphrase with as few as four words will defy any feasible attack. |
| Security Flaw In T-Mobile’s Google Phone [Liquidmatrix Security Digest] Posted: 24 Oct 2008 09:08 PM CDT  Well, that certainly didn’t take very long now did it? From NY Times:
Tricking a user into surfing an infected site? Nevah.
I guess we can safely say that, yes, that would be unpleasant. UPDATE: Well, I posted this just yesterday and now it appears that there are serious problems with T-Mobile’s G1 mobile email service. They are actively working to address the issue. Tags: Google, Android, Google Android, T-Mobile |
| EFF Offers NSA Spoof T-Shirts [Liquidmatrix Security Digest] Posted: 24 Oct 2008 05:03 PM CDT  This is rather funny capper to a long week. The EFF, in a bid to raise donations, has made t-shirts with their spoof of the National Security Agency’s logo on them. Very amusing. From EFF:
This is available for a donation of $65 or more. Very cool shirt and the money helps to fund a great cause. |
| Recession-Induced Network Innovation [ARCHIMEDIUS] Posted: 24 Oct 2008 01:18 PM CDT I just watched Cisco's John Chambers "Can IT Strengthen the Economy?” interview at the recent Gartner conference just released at ZDNet. John clearly sees innovation as the way out. The network is strategic to business productivity. Flexibility, speed and scale are becoming even more important. That means dynamic connectivity and intelligence will become critical to the [...] |
| StillSecure 4 in the Fast 50 [StillSecure, After All These Years] Posted: 24 Oct 2008 11:23 AM CDT
Last night was another such occasion. For the 2nd time, StillSecure was honored as one of the Deloitte Colorado Technology Fast 50. This annual award is in recognition of revenue growth. StillSecure was actually the 4th highest ranked company in Colorado with revenue growth over 5 years of almost 1400%! I accepted the award and spoke on our behalf. It was very gratifying. Also interesting was that the two companies just above us, Accuvant and MX Logic were also security companies. That made 3 of the top 5 being security companies. That is a statement too, I guess! I thought the best speech was from the CEO of Accuvant who said the key to winning was starting off really small. But seriously, we are very grateful for the award and recognition. I can only take little if any credit for it though. All of the hard working people at StillSecure who passionately ply away every day trying to offer the protection our customers are depending on us to provide deserve all of the credit! Related articles by Zemanta |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |




![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=4f699ba8-1086-4fa3-8694-453790f9020b)
No comments:
Post a Comment