Spliced feed for Security Bloggers Network |
| An Information Security Place Podcast - Episode 2 [An Information Security Place] Posted: 05 Aug 2008 07:30 AM CDT Here’s the second installment of the podcast. Joining me is my cohort and cohost, Jim Broome. Some of you may know Jim from his blog. Jim is definitely one of the more technical bloggers out there, serving up all kinds of geek toy and hacking fun. I hope to keep Jim around a long time since he has a whole lot of experience in the security field, and he is in no way shy to talk about it. :) Also, Jim is doing most (if not all) of the mixing and production work on the podcast since he has a lot of cool toys and has experience in the broadcast industry. So thanks Jim! Some show notes:
Stick with us as we get all the bugs worked out. I hope to bring some new perspectives and liveliness to security podcasting. Vet | ||
| Black Hat 2008 Preview: Paranoia and Learning [Security Incite Rants] Posted: 05 Aug 2008 06:51 AM CDT Hard to believe, it's time for another Black Hat conference. This is my third, and as I sit in the airport waiting to head out to Vegas, I'm eagerly anticipating the show. For lots of reasons, but mostly because it's the only show I attend to actually learn something. It's not like RSA or CSI are big on "education." I certainly know that I don't know it all, but Black Hat is a place where I can hang out with guys a lot smarter than me. And that's a good thing. Even if the show has gotten a bit corporate. As others have mentioned, Black Hat/DEFCON are not the places to be careless about your computer security. Now that BH is doing the Wall of Sheep as well, no one is safe. I was at Rob Graham's session last year where he pulled up some poor saps Gmail through his sidejacking attack. That ain't going to be me. So what do I do? WiFi is OFF. Period. Until I get back to ATL on Friday, WiFi is off. I'll just rely on my Verizon card for the few times I'm in my room and connected. I don't carry my laptop at the show, rather relying on good old fashion paper and pen to take notes. I may do a quick post or two from my iPhone (3G, I upgraded over the weekend), but for the most part I'll be mostly disconnected. Speaking of my iPhone, WiFi is off on that as well. I'm also turning off Bluetooth. That means I'll be the silly one with the wired headset. But I'm not sure what new attacks have emerged, so I'll suffer the wired life for a few days. I'm also turning off the GPS. It's not like I'm going to get lost in Vegas, and again although I haven't heard of specific GPS attacks, why risk it? Yes, clearly it's paranoia in full effect. But better to be safe (if a bit disconnected) than sorry. That's for sure. In terms of sessions, a few caught my eye:
I'm sure there are others, or maybe not. I tend to like to keep my schedule pretty fluid at Black Hat. I'll be hitting the party scene as well, so I hope to see at least some of you in Vegas. Safe Travels. | ||
| Fake flash player downloads alert [belsec] [Belgian Security Blognetwork] Posted: 05 Aug 2008 06:41 AM CDT First off, do not download Flash Player from a site other than adobe.com – you can find the link for downloading Flash Player here. This goes for any piece of software (Reader, Windows Media Player, QuickTime, etc.) – if you get a notice to update, it’s not a bad idea to go directly to the site of the software vendor and download the update directly from the source. If the download is from an unfamiliar URL or an IP address, you should be suspicious. Second, all Adobe software for Windows is signed with a digital certificate that is validated by Windows when you install our software. The Publisher will always be ‘Adobe Systems, Incorporated’, and you can verify this when you double-click the installer, or by right-clicking on the installer, selecting ‘Properties’, and going to the ‘Digital Signatures’ tab. For Flash Player in particular, computer users can use this page to verify what version of Flash Player is installed, and what the current version of Flash Player is for your operating system. The most recent version of Flash Player version is 9.0.124.0. http://blogs.zdnet.com/security/?p=1648 | ||
| Surveillance cams are helpless against this [belsec] [Belgian Security Blognetwork] Posted: 05 Aug 2008 06:12 AM CDT | ||
| Should pipelines be published on the internet or not [belsec] [Belgian Security Blognetwork] Posted: 05 Aug 2008 06:00 AM CDT After 9/11 thousands and thousands of information, websites and documents were made to vanish by the US government because it would give too much information to their ennemies who - as the scaremongering went - were ready to strike at any moment with any means against any part of the country. The terrorist alerts stayed high - so when there was a real indication of an alert it went to its highest and the whole media went nuts. We are now nearly 7 years later and most of the US is still standing (if it wasn't for the foreclosures most would be happy also) and even if at one end the outgoing administration is still trying to realise or revive some of its big plans to change the USA in a better controlled state (with ID's and big databases about whatever somebody did or does) at the other end others are trying to get operations or information out of the sphere of paranoia and back where they belong. There is no discussion that scientific information about chemical products needs still to be available for the community and so there is much more technical information that needs to be liberated from the censors (with eventually restricted access). But are pipelines really necessary to be published on the internet. Even if you know that if you blow up one the price of oil will rocket even bigger and its impact will be immediately much bigger than the bomb itself (or even the two airplanes they did crash into the buildings). http://www.eia.doe.gov/pub/oil_gas/natural_gas/analysis_publications/ngpipeline/index.html http://www.npms.phmsa.dot.gov/
| ||
| Different ways of installing surveillance camera's [belsec] [Belgian Security Blognetwork] Posted: 05 Aug 2008 05:46 AM CDT When we were visiting London it was just amazing how many camera's there were and just everywhere. It was only after I came back to Brussels that it struck me. The way that camera surveillance has been set up is for the moment totally different, which explains that the number of cams is so different. If you are in a London Metro you will see that you are being videatracked from the moment you are some yards away to the station untill you have left the station some yards away (and than arrive in another stream of camera's). Once inside the Metro (or tube) every corner, every part of your travel is covered from 1, 2 or 3 angles to be sure that there is nearly no dead (or dark) corner left to hide. It is nearly impossible to do stuff that ain't going to be seen or recorded. They will need some very efficient technology (but it seems they are trying that out at the Olympics) to analyze all those pictures in real time and to extract in real time those pics or movement that can give a hint or an alert. If you are in a public place than the same principle is used. There is no dark corner that hasn't been covered by some cam somewhere watching over you. If you take the tube or metro in Brussels there are some place that are somewhat covered but the coverage is far from complete. In public places you will see some cams but not the total coverage. There are 2 different principles of covering or controlling things. Or you cover each possible angle and position or movement or you just select those where there is or has been a risk and where there is an objective reason to place a cam. | ||
| Posted: 05 Aug 2008 05:32 AM CDT | ||
| The RFID internet of things to come [belsec] [Belgian Security Blognetwork] Posted: 05 Aug 2008 04:43 AM CDT RFID for Jewellery (or blood diamants ?) DAILY RFID ( www.rfid-in-china.com ) recently announced availability of their RFID Jewelry Tag designed to automatic Jewelry tracking to market communities, secured storing and other areas. The cost of each RFID Jewelry Tag is even lower than 1.2USD. RFID Jewelry Tag would help the manufacturers to collect data from hundreds of items in few seconds. Unlike barcode, a complete tray load of jewellery and RFID tags can be inserted into the system and data can be captured from all of them at once, Orizin said in a statement. RFID for cars (rental and fleet for example) DAILY RFID ( www.rfid-in-china.com ) recently announced availability of their RFID Windshield Tag designed to deliver long read range at lower cost for customers automating vehicle which obtains access control to gated communities, secured parking and other areas. The cost of each Windshield Tag is even lower than 1.4USD. RFID for car components, location and repair For document tracking (for example at an office) Still think that in some cases, a notice or warning would be in order. And some of these RFID stuff isn't that safe enough that it couldn't be used against the safety of it. If you are looking for jewellery expensive enough to track and protect it, scan for it. | ||
| July Commenter of the Month Competition Winner! [Darknet - The Darkside] Posted: 05 Aug 2008 04:22 AM CDT Competition time again! As you know we started the Darknet Commenter of the Month Competition on June 1st 2007 and it’s been running since then! We have just finished the fourteenth month of the competition in July and are now in the fifthteenth, starting a few days ago on August 1st - Sponsored by GFI. We’ve successfully... Read the full post at darknet.org.uk | ||
| Apple DNS Patch Problem: No Fix For MAC Clients! [Infosecurity.US] Posted: 05 Aug 2008 12:05 AM CDT
| ||
| US-CERT: Airline E-ticket Email Attack [Infosecurity.US] Posted: 04 Aug 2008 11:31 PM CDT | ||
| Posted: 04 Aug 2008 11:30 PM CDT I would like to continue the discussion I started in my previous post called "Ideal Tool to Solve Real Problems ... of the Near Future?" Specifically, upon outlining some problems with logging, I will now forecast what will happen with them in 18-24 months.
First, let me bet my ass that "Not knowing what to log" problem will be licked in 18-24 months; at least as far as major regulations go, people will have a pretty good idea a) what the auditors want them to log (and review!) b) what they need to log for solving their problems. Now, for esoteric log sources (and custom applications) might still present a challenge from that point of view, but for basic "staples" (firewall, network gear, major OS) the mystery will be over (again, see "Tell me EXACTLY what to log for PCI?" for reference) Next, the problem of "Log volume" will definitely get worse, much worse. One might think that 100,000 each second is a lot of log - but there WILL BE more at many companies! Big application log explosion is coming, fueled by the need to address logging in areas where such motivation was lacking before (basically, custom and vertical applications) as well as harness the power of "uncommon" logs for such tasks as fraud analysis or SOA monitoring. Keep in mind that even though in some areas logging is NOT a preferred way of monitoring and auditing activities (see this discussion on database logs here), application logging will still explode on us... The problem of "Log diversity" (the fact that most logs all look different in format and meaning) will get worse before it will get better - and better it WILL (!!!) get since standards are being developed. We will see people struggling with all sorts bizarro log data in the coming years. Virtualization, web services and SOA, various ERP applications and even cloud services will increase the diversity of logging in the coming years. Similar to the above, a problem of "Bad logs" (ones that are subjective, miss key information, require groping for a crystal ball to understand, turn log analysis into dark voodooistic experience or are useless in some other way) will also follow the pattern of the above log diversity problems - it will get worse before it gets better (via the CEE standard effort that now covers the OpenXDAS effort as well!) I noticed that people started asked me questions about "how to do application logging right?" and "what to tell application developers about logging?" which almost never happened in the past. BTW, watch my blog for some uber-fun info on that! "Getting the logs" has gotten much easier in recent years; agentless collectors like Project Lasso (which, BTW, just got updated) and grabbing files remotely via secure protocols made application log collection easier (syslog-NG with TCP transfer and buffering also helped). Next, Windows 2008 will make it MUCH easier for the whole Windows kingdom due to their use of web services (thanks Eric!). However, in the future it might resurface as we try to collect logs from "weird" places, again, clouds come to mind as well as virtual environments (e.g. how do you get logs off a dormant VM?). What's the next frontier in this area? Log discovery - automatic finding and identifying log files on systems in order to analyze and retain them (Yo, my t-shirt-making colleagues... :-)) All this, however, pales in comparison with my favorite "uber-challenge", "Making sense of logs in an automated fashion" - this baby is definitely not going away in 2-3 years. Much more research is needed to make that "log->conclusion" jump automatically without head-scratching, invoking ancient deities and cursing under ones's breath. Only then we can attempt to reliable handle "proactive logging" (i.e. analyzing various failure or compromise precursors in logs and then predicting the future based on them), another Holy Grail of logging domain. Anything new will emerge? Yes, I think awareness of the "Logging Gap" problem will grow. "Logging gap" happens when you combine "a need to log" with utter "inability to do so." For example, this will happen when people will know that they HAVE TO log, say, for compliance, but will have no way of doing it due to application or platform limitations. This will become one of the challenges and special "logging add-ons" will appear to close the logging gap and create additional logs where activity audit is desperately needed, but native logging is not helping to achieve it. Also, I think people will finally wake up to "Log security" challenges - i.e. producing for use as evidence, compliance attestations, etc. Log security is not getting the attention it deserves, but I think this challenge will finally emerge in full force in the next 2-3 years. My next poll will address that :-) Anything else I missed? Share away! Related posts: | ||
| More on the Oracle Zero Day [Infosecurity.US] Posted: 04 Aug 2008 11:28 PM CDT
| ||
| SAP MaxDB Vulnerability [Infosecurity.US] Posted: 04 Aug 2008 11:20 PM CDT
| ||
| Chinese hacker dancing and defacing = pure awesome! [The Dark Visitor] Posted: 04 Aug 2008 11:19 PM CDT Just going to change the name of the blog to the Xiao Tian Show and call it a day. Even though Chinese hackers are now constantly worrying about the Olympics getting hacked, Xiao Tian has managed to remain in the spotlight. The latest articles making the rounds about Xiao Tian still summarize the interview with the Daily News and Analysis, just with the addition of a defacement: The first reference I can find of this defacement indicates it took place in September of 2006, to protest Prime Minister Koizumi’s visit to the Yasukuni Shrine. Several people posting think it was done by a female hacker due to the signature line that translates to something like, “the girl pissing on the Yasukuni toilet.” The article uses the screen shot to demonstrate how ferocious female Chinese hacker can be and does not attribute it to Xiao Tian. Plus, we know our gal would never use such vulgar language. She saves all that built up nationalist energy for the dance floor: FROM Xiao Tian’s blog: She is on the left in black and says to ignore the other girl in the short skirt. As a matter of fact, Xiao Tian wants you to know she hates that girl. Apparently, the DJ pushed the girl up on the stage so the two could dance together. Xiao Tian doesn’t have kind words for the DJ either. Also, she claims to have been a bit nervous on stage, so these are not her best dance moves. That is why you come here, for the culture. Now, back to your nerdly doings. | ||
| Twitter Updates for 2008-08-04 [.:Computer Defense:.] Posted: 04 Aug 2008 10:59 PM CDT
Powered by Twitter Tools. | ||
| Safe browsing - Websense says fuggetaboutit! [Last In - First Out] Posted: 04 Aug 2008 10:14 PM CDT It would sure be nice if an ordinary mortal could buy a computer, plug it in, and safely surf the web. Websense doesn't think so. I don't either. Apparently neither does CNN. According to Websense:
It's 2008. So now that we have the wonderful world of Web 2.0, Websense says: The danger is that users typically associate the content they are viewing from the URL in the address bar, not the actual content source. The URL is no longer an accurate representation of the source content from the Web page. (Emphasis is mine.)So even the wise old advice of simply making sure that you pay attention to your address bar is of limited value. Your address bar is really just he starting point for the adventure that your Web 2.0 browser will take you on without your knowledge or consent. Obviously it is true that some people, some of the time, can surf the web with a mass produced, default installed operating system and browser. But for the general case, for most users, that's apparently not true. One of my security mantras is 'if it can surf the web, it cannot be secured'. In my opinion, if your security model assumes that desktops and browsers are secure, your security model is broke. You still need to do everything you can to secure your desktops and browsers, but at the end of the day, after you've secured them as best as they can be, you still need to maintain a healthy distrust toward them. Of course when security vendors report on the state of security, we need to put their data into the context of the increase revenue they see when everyone panics and buys their product. (via Zdnet ) | ||
| Following Blackhat & Defcon from home (update) [Security4all] [Belgian Security Blognetwork] Posted: 04 Aug 2008 07:05 PM CDT  For the unfortunate people who won't be at Blackhat or Defcon, here are some ways to follow up on the events. The BlackhatUSA2008 Twitter page The BlackhatUSA20008 RSS Feed People on Blackhat reporing on Blackhat (#Blackhat using Tweetscan) The Defcon Twitter Page The Defcon RSS Feed People on Twitter reporting on Defcon16 (#defcon using Tweetscan) Using hashtag.com might be more accurate then Tweetscan but it's currently not working for #blackhat or @defcon. UPDATE (04/08/08): Microsoft created a virtual Blackhat pressroom to bring Microsoft news from the conference. It's nice to see how they support Blackhat and embrace blogging and are even on twitter!!! Check the link above for more info. (Photo under Creative Commons from Lisa Brewster's Photostream) | ||
| Fake Flash updates being distributed through Twitter [Security4all] [Belgian Security Blognetwork] Posted: 04 Aug 2008 06:54 PM CDT  The Kaspersky weblog warns us of social engineering tactics (in this case beautiful women) being used to spread malware on Twitter. (hat tip: Ryan Naraine) So Twitter as a social network has moved from being misused to spam members to distributing malware.
I didn't know that the PSIRT (Product Security Incident Response Team) of Adobe started a blog which incidentally also confirmed this attack today. They remind us that the official download link for Flash is at http://www.adobe.com/go/getflashplayer/. When being presented with a download link, it's always safe practice to not follow the link and go directly to the vendor's site to search for the update. Additionally, their installer is digitally signed with 'Adobe Systems, Incorporated', and you can verify this by by right-clicking on the installer, selecting 'Properties', and going to the 'Digital Signatures' tab. Finally, there is also an ongoing email campaign, distributing a fake flash component. The email appears to come from CNN.com and lists the Top ten newsstories. When following one of the links, the user is prompted to download the get_flash_update.exe malicious "codec". For a more detailed analysis, visit the malwaredatabase.net website. I wonder if our friends from StormWorm are behind this wave? | ||
| slide:ology: The Blog [Security4all] [Belgian Security Blognetwork] Posted: 04 Aug 2008 06:54 PM CDT  I mentioned Nancy Duarte and her new book Slide:ology in a previous post (Creating powerful presentations: Some advice and an online Webinar) I'm happy to announce that she also started a blog (Slide:ology) with regular tips and useful information. Make sure to subscribe to their feed. | ||
| Presentation skills: Learn to master the stage [Security4all] [Belgian Security Blognetwork] Posted: 04 Aug 2008 05:40 PM CDT  Making good slides is only a small part of a good presentation. You must also be able to communicate it as a good story to your audience. Use some emotion and passion. Don't just ramble of a list of facts (or bulletpoints). A recent comparison Garr Reynolds from PresentationZen made, was that professional stand-up comics and presenters & speakers have much in common. This is why he recommends us to watch 'Comedian' (Amazon), a documentary about Jerry Seinfeld. I loved this documentary and I too highly recommend it. However, it's not for everyone — don't buy it if you just are looking for laughs; it's not a comedy though it's often funny — but if you are a professional speaker or presenter (or any other professional) with a passion for learning and improving your speaking skills, then I think you will enjoy this documentary. (Source: Presentationzen)Of course, there are also some other tricks & tips that can enhance your performance. Just look at this video: Related posts:
| ||
| The Art of Patching [/dev/random] [Belgian Security Blognetwork] Posted: 04 Aug 2008 05:01 PM CDT
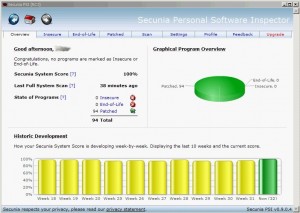
Finally! After weeks of “yellow status” reported by PSI (Personal Software Inspector from Secunia), my profesional notebook finally went “green”! I’m using PSI for a while on my notebook which has plenty of installed applications: productivity, connectivity, security, reporting tools and much more. Since the beginning, I was never able to have a fully patched system! Why? There are multiple reasons:
Being a security professional, it took me time and research to reach the score of 100%! Patching a system is really a pain, nobody does this with fun. What about all home PC users? Read some statistics gathered via PSI:
| ||
| some thoughts about the Belgian eID [remes-it] [Belgian Security Blognetwork] Posted: 04 Aug 2008 04:40 PM CDT I was discussing with some people about the benefits of using the Belgian eID for authentication of users within an application/system and someone came up with the following argument : "If a user would lose his/her card, he/she would be unable to use the system until the card is replaced". Which, imho, is quite a valid argument NOT to opt for eID unless you can take that risk. I'm not sure what the replacement term is for an eID but probability is high here ... and as a business I might not feel like depending on a service without an SLA for my identification needs. | ||
| Interesting Information Security Bits for August 4th, 2008 [Infosec Ramblings] Posted: 04 Aug 2008 03:29 PM CDT Well the start of a new weeks is here, along with a batch of interesting things to take a look at. Only blogs again this time. 360 Security, along with many other folks, points out that the Apple DNS Patch Fails To Randomize. Kurt Dobbins over at Arbor Networks has an interesting post up about the Myths and Realities of the Net Neutrality Debate. Good stuff in there. Bruce Schneier brings to our attention that the U.S. government has published its policy regarding Seizing Laptops at Borders. Basically, we take when we want to and you don’t have any say in the matter. Nifty post up at Neohapsis talking about exploiting hardware vulnerabilities in the Intel CPU. Neat stuff. Kris Kaspersky’s talk “Remote Code Execution Through Intel CPU Bugs” to be given at Hack in the Box was the impetus. Wesley has created his first Metasploit module. It is a nifty tool. You should go take a look if you are interested in pen testing. CG points to a paper and demo for DHCP script injection. Lots of fun to be had there. Ha.ckers.org has a nice little bookmarklet that make is easy to use MSN IP Search to find domains on the same IP address as the web page you are reading. Finally, Gary Warner points us to another story about an insider selling PII. I will be leaving for Vegas on Thursday so there will be light posting here until next week. Kevin Technorati Tags: apple, dns, net neutrality, border, hardware, metasploit, dhcp, risk, pii  | ||
| Is Product integration working? [An Information Security Place] Posted: 04 Aug 2008 02:39 PM CDT I just read a post by Mike Rothman where he is revisiting the "Big is the New Small" post he wrote oh so long ago (is it just me, or does 2 years in the blogging world seem more like 20?). Basically, it was all about the consolidation of the security market, which is still happening, as Mike points out. But the little nugget that Mike points out but really doesn’t give enough time to is the integration issue. Mike says this:
I added the emphasis there because I think that is important. I have seen some of these bigger companies that have a centralized management platform (especially the end-point security companies) that have bought these different products and are still trying to integrate them all into that platform. Their vision is good as far as the concept goes. "Let’s put all of these products into a central management console that can provide all the information in a single spot." It makes their offerings attractive to the client if it worked. I think this is the reason a lot of people are going with some of these "bloated, unresponsive, lumbering vendors." Some of it may be that they don’t want to work with 5 different companies, but I think that happens more often in infrastructure types of products (DLP products, now mostly owned by bigger companies, still often sell as best of breed much of the time because they each have their own strengths). What I see as something of a trend (though not long term because the consolidation will still happen) is that some of these shops will look at best of breed in some areas for a while because the integration they were sold has not been delivered. I really see some of these shops not wanting "good enough" because it isn’t close enough to actually being good enough. These products that should have been integrated and functioning smoothly by now are still struggling to get off the ground, and they are causing more management headaches. I guess we’ll see. Some people may continue to struggle through and wait for the promise. But I see a lot of people getting aggravated, and they are being almost forced to make some changes in order to manage the problems. Vet | ||
| Revisiting the good enough generation [StillSecure, After All These Years] Posted: 04 Aug 2008 02:08 PM CDT Thats right, talkin' 'bout my, my g-g-g-generation. The generation where good enough, is . . . good enough. There is no sense of being the best you can be or going over and above. Just enough to get it done is the way of the world. So with Rothman revisiting Big is the New Small, I thought another look at the good enough generation was in order. It was just over two years ago, that I wrote the original "Is good enough security, good enough" | ||
| BlackHat Picks, Day 2 [Zero in a bit] Posted: 04 Aug 2008 12:48 PM CDT Here’s the rest of my list: 10:00-11:00 FX, Developments in Cisco IOS Forensics. 11:15-12:30 Oliver Friedrichs, Threats to the 2008 Presidential Election (and more). 13:45-15:00 Option 1: Scott Stender, Concurrency Attacks in Web Applications. Option 2: Travis Goodspeed, Side-channel Timing Attacks on MSP430 Microcontroller Firmware. 15:15-16:30 Option 1: Alexander Sotirov and Mark Dowd, How To Impress Girls With Browser Memory Protection Bypasses. Option 2: Karsten Nohl, Mifare - Little Security, Despite Obscurity. This is one of the toughest time slots as you also have McFeters/Carter/Heasman and Grossman/Evans in the lineup. Choices, choices. 16:45-18:00 Option 1: Bruce Dang, Methods for Understanding Targeted Attacks with Office Documents. Option 2: Christopher Tarnovsky, Inducing Momentary Faults Within Secure Smartcards/Microcontrollers. Lots of intriguing hardware talks on Day 2. A lot of it is probably over my head and my first options are more applicable to my day job. There might have to be some room hopping. I fly out to Vegas tonight — see you all there! | ||
| Posted: 04 Aug 2008 12:05 PM CDT ... said the user while his computer was crippled with malware. His answer didn't make sense anyway, because how could he know that he was (never been) infected if no scanner would alert him? He asked for my help because his Internet Explorer browser crashed frequently and his computer was crawling. Although he did get popups as well, he didn't really see this as a problem because he had a good popup blocker. O_o No way malware was causing this (according to him). It was always been like that..... (so you can imagine how long he was infected already...) And yes, I've found malware from years ago: DollarRevenue crap, EliteMedia, leftovers from the Alcan worm, and a recent Zlob Media variant. Time to make him aware that his computer really is infected - so the only way to show the facts is to install an Antivirus... which he did. He was shocked once the scanner started to detect and delete the files. Funny part here was, a HUGE amount of infected files were present in his Limewire shared/complete folder (because of the Alcan Worm, which was luckily already disabled). So it was an extra shock for him since more than 1000 files were already detected and deleted there. After all, we could clean everything and I'm sure he would never uninstall his Antivirus again. :-) A shocktherapy is really needed once in a while.  Recently I've been reading many articles, blogposts, discussions about Antivirus Software and Security Suites. Which one is the best and if it's really needed nowadays since a lot of malware can bypass Security software, or scanners don't even detect it. If I read this, then I'm always wondering what these people actually do online if they are complaining that their Security Software couldn't prevent or detect the infection they are dealing with. Ofcourse you'll get infected if you use 4 different P2P managers and download everything from there. Ofcourse you'll get infected if you visit illegal sites. Ofcourse you'll get infected if you click every link in your mails. Even with the best Security Suite installed, you can get infected if you visit the sources where malware is lurking. So why blaming your Security software? Also, A LOT of people only install an Antivirus after they got infected... in order to remove the malware... and if it fails to remove the malware, then they complain. So YES, an Antivirus / Security Software is really needed, not necessarily to remove the malware, but to PREVENT the malware in the first place. It can prevent/detect/delete a lot of malware, but can't prevent all since a lot of new malware is created everyday. After all, it's still better to prevent 80% of the malware than no detection/prevention at all. | ||
| Ever did some design and wanted blind / dummy text? [Robert Penz Blog] Posted: 04 Aug 2008 11:36 AM CDT I found a very nice and easy homepage which generates that kind of text for you. Take a look at Lorem Ipsum. And here is a text generated by it Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Nullam at erat ac sem aliquam tempus. Vivamus nisl odio, euismod quis, tempus quis, porta eu, ipsum. Vivamus est erat, commodo tempus, interdum et, elementum ac, nulla. Vestibulum pede tortor, eleifend at, mattis eget, dignissim eget, lorem. Mauris eu leo. Cras sodales, enim sed faucibus ultricies, tellus tortor blandit nunc, quis lacinia quam est a felis. Ut ac lorem non nunc consectetuer rhoncus. Aenean erat lacus, mollis nec, aliquam et, laoreet quis, neque. Fusce urna lorem, posuere et, molestie eu, facilisis eget, dolor. Integer erat erat, bibendum et, viverra quis, dapibus at, erat. Vestibulum metus. Ut diam erat, sollicitudin sed, ullamcorper at, commodo luctus, eros. Nulla vitae erat. Cras hendrerit commodo mauris. Aliquam aliquet turpis vitae odio. Etiam luctus orci vitae leo. In et augue eu justo convallis adipiscing. Integer ultricies. Class aptent taciti sociosqu ad litora torquent per conubia nostra, per inceptos himenaeos. Nam ante lacus, pellentesque quis, tempor eget, malesuada eget, dui. Proin nec libero. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Sed scelerisque facilisis justo. Suspendisse semper turpis et pede. Pellentesque erat libero, sodales ac, iaculis sed, commodo non, velit. Donec commodo pellentesque elit. Suspendisse sagittis molestie quam. Cras at dui a magna pharetra ornare. Sed interdum felis quis augue. Maecenas turpis. Suspendisse dui. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Sed vulputate mauris id est. In consectetuer neque nec ipsum. Maecenas consectetuer tellus at pede. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Aenean ante risus, cursus vel, porta ultricies, gravida quis, dolor. Mauris blandit velit ut enim. Pellentesque enim. Praesent vehicula. Maecenas pharetra sollicitudin eros. | ||
| DFN CERT warns about Linux root kits [Robert Penz Blog] Posted: 04 Aug 2008 11:16 AM CDT The CERT of the Germany`s National Research and Education Network (DFN – Deutsches Forschungsnetz) warns about attacks on Linux servers, which hide with a root kit. This root kit hides directories and processes from the administrator. The attack is most likely carried out by stolen SSH keys. Their experts found the directory
tells you the link count and following counts the entries returned by ls:
If the do not match, you should really take a closer look. Of course you should use other directories as well. The second way to find leads on this root kit is to send signals to the hidden processes. If a process id is not in /proc, but responding to signals you should also take a closer look:
On olders systems the task directory is maybe missing, use |
| You are subscribed to email updates from Black Hat Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Black Hat Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |





No comments:
Post a Comment