Spliced feed for Security Bloggers Network |
| Posted: 27 Sep 2008 07:33 AM CDT A couple of months back GNUCITIZEN started House of Hackers, a social network for hackers and other like-minded people. Keep in mind that we use the word hacker in much broader context, i.e. someone who is intellectually challenged by the limitations of a system. Certainly, we do not promote criminal activities. Today the network has expanded to 5500 members. I believe that it will reach 6000 members by the end of the year. It has been a huge success so far. HoH has groups which cover almost every area of the information security field and also some unique ones such as Stock Market Hackers, Urban Explorers, Ronin, Female Hackers, Black PR, etc. So, let’s get to the point. Would you be interested in sponsoring HoH in return for placing your brand in our sponsors page which is also displayed on the front page and the sidebar for every other page? We are open to any other suggestions you may have. If you are interested get in touch with us from our contact page. | ||
| Entrust - as a Vendor should be [Last In - First Out] Posted: 27 Sep 2008 05:58 AM CDT
Entrust gets a gold start next to their name in my vendor contact list. Earlier this week, Entrust called. Not to sell us anything, but rather to advise us that we had a couple of SSL certs that were generated by the non-random Debian SSL package. That's pretty decent of them. But not only did they call, they made sure that we we understood the problem, they sent us a follow up e-mail with the details, and made sure we got the e-mail. Microsoft recently did something similar with all of it's 'Premier' customers. In our case, for one of the nastier Windows vulnerabilities a few years ago, our Microsoft Technical Account manager called us, explained the problem, advised us how to mitigate and patch, and sent follow up e-mails and tracked our patching progress at 6 or 8 hour intervals with e-mails and phone calls until we were patched. I like it when vendors are watching out for customers. Compare that to the Network Solutions/Comcast domain fiasco. Or read Amrit Williams thoughts on trust and responsibility between providers and customers. | ||
| Were entrepreneurs born yesterday? [StillSecure, After All These Years] Posted: 27 Sep 2008 12:04 AM CDT  Image via Wikipedia It is not often that I disagree with my friend Brad Feld. It is not because he is on the Board of Directors at StillSecure, but more that Brad and I generally agree on a lot of topics and where we don't, he makes his position reasonable enough that I can appreciate his point of view. But today I have to disagree with Brad. Brad wrote an article about his annual trip with his family back to the 'hood in the Bronx where his Dad and Uncle grew up in the 40's and 50's. While on the trip Brad's uncle made the comment "if you aren't growing, your dying". I actually agree with the statement. Brad than talks about the world being different today than the world his dad and uncle grew up in. He makes the statement, "Entrepreneurship existed, but it wasn't the mainstream". Therein lies my problem. Brad has quite a record of success as both an entrepreneur and as a VC. But I think Brad is mixing and matching them here. Yes the VC industry may not have been mainstream in the days of his dad and uncle growing up, but entrepreneurs were very much alive, growing and mainstream at the time. In fact the entrepreneurial tradition is a key part of American tradition. In fact some people think this tradition is our greatest export. Just because there may not have been a VC around to help the entrepreneur doesn't mean that there were not mainstream successful entrepreneurs. From Benjamin Franklin himself, who started a bunch of different businesses around his inventions and a successful printing business to Thomas Edison and Alexander Graham Bell, the American tradition of innovation has made many a fortune over the course of our history. From John Rockefeller to JP Morgan, from Andrew Carnegie to Henry Ford, America has a rich tradition of entrepreneurs being successful on Main St, Wall St and every street in between. These men did it the old fashioned way, they boot strapped it! They didn't have the luxury of finding some VCs to give them capital and put them in the Kiretsu. If they took money, they paid an arm and a leg for it (hey, somethings never change). So Brad lets not imagine that entrepreneurs being mainstream was non-existent before the advent of the VC industry or the technology revolution. It was American entrepreneurship that allowed Brad's dad to join the armed forces, go to medical school and establish and grow a successful medical practice. Americans like Brad's dad, Stan have been been building businesses like that since the birth of the nation and even before. Without VCs and without computers, these entrepreneurs were indeed growing or they were dying. But to be so era-centric as to not acknowledge the long and successful tradition of American entrepreneurship is to ignore the facts and insult the long line of business people who have made this country great! Related articles by Zemanta | ||
| Checking for ViewStateUserKey using FxCop [CGISecurity - Website and Application Security News] Posted: 26 Sep 2008 05:41 PM CDT An anonymous user writes "ASP.NET has had a mitigation to prevent against CSRF/One-Click attacks since 1.1 with the use of Page.ViewStateUserKey property. You can now make sure that the property is being used using FxCop." Link: https://blogs.msdn.com/sfaust/archive/2008/09/25/checking-for-viewstateuserkey-using-fxcop.aspx | ||
| (ISC)2 Announces CSSLP Developer Certification [RioSec] Posted: 26 Sep 2008 05:09 PM CDT (ISC)2 has announced a certification for application development security called Certified Secure Software Lifecycle Professional (CSSLP). According to their site, CSSLP seminars will be offered beginning "early 2009" and exams will start June 2009. There will also be an "experience assessment window" starting September 30th in which candidates may submit "Accomplishment Records" for review - accepted qualified applications will get the $650 USD exam fee waived. Similar to the CISSP, the CSSLP requires four years of experience in four or more of the topic areas listed below, endorsement from a current (ISC)2 certified individual, and a commitment to the (ISC)2 Code of Ethics. | ||
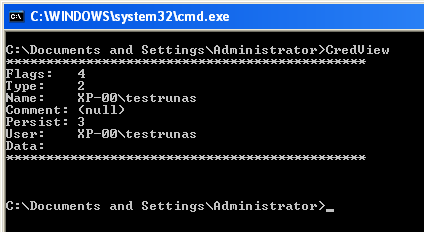
| Quickpost: Stored User Names and Passwords [Didier Stevens] [Belgian Security Blognetwork] Posted: 26 Sep 2008 02:05 PM CDT “Where does Windows store this password?” “Is it safe there?” I regularly get asked these questions, and they frequently appear on forums. Microsoft has developed several technologies to store and protect credentials, and to add to the confusion, Microsoft has renamed some of these technologies over the years… A list: LSA, Protected Storage, Windows Data Protection (DPAPI), Stored User Names and Passwords, … Last question I read was: where does runas /savecred store the password? It gets stored in Stored User Names and Passwords. Before storing the password:
And after:
Nirsoft has a tool (CredView) to dump passwords stored in Stored User Names and Passwords:
The CredRead function (used by CredView) will not retrieve Windows passwords (domain and local) unless it is called from the LSA process. That’s why CredView doesn’t display the testrunas password (data). If you convert CredView to a DLL and inject it in the LSA process, you’ll be able to retrieve the passwords. This is exactly what Cain & Abel does, and why you need admin rights (SeDebugPrivilege to be precise). Quickpost info  | ||
| A fortis reminder for the weekend [belsec] [Belgian Security Blognetwork] Posted: 26 Sep 2008 01:09 PM CDT From doomberg " Sept. 26 (Bloomberg) -- Wachovia Corp. and National City Corp. slumped after negotiations on the government's financial bailout stalled and Washington Mutual Inc. was seized by regulators and sold to JPMorgan Chase & Co. Wachovia dropped $3.84, or 28 percent, to $9.86 at 1:20 p.m. in New York Stock Exchange composite trading, and Cleveland-based National City fell 40 percent, leading banks lower. National City and Charlotte, North Carolina-based Wachovia have plunged more than 80 percent in the past 12 months. ``Washington Mutual showed that one of the big ones can go down, and if you are looking at who else in the top 10 is facing the most pressure, Wachovia is right there,'' said Stan Smith, a banking professor at the University of Central Florida in Orlando. " | ||
| Ex Fortis CEO was once a celebrated figure in Belgium [belsec] [Belgian Security Blognetwork] Posted: 26 Sep 2008 01:04 PM CDT Fortis' Votron is European Business Leader of the Year Jean-Paul Votron, CEO of Belgian-Dutch banking and insurance group Fortis was elected European Business Leader of the Year. The European Business Leader of the Year title rewards the most successful companies and their leaders from the 25 European Union Member States. The jury awarded Votron because of his "extraordinary leadership and exceptional vision, which has led to Fortis's remarkable performance". http://invest.belgium.be/en/news/fortis-votron-european-business-leader-year
| ||
| Catching up on my security reading [StillSecure, After All These Years] Posted: 26 Sep 2008 10:30 AM CDT Anyone who looks at the currently reading and read recently sidebars on my blog knows that I read a decent number of books. I do most of my reading on planes. I like to read either Sci Fi or historical novels, but also a fair amount of current event stuff. Occasionally I will read business related books and even some security related books as well. I have been meaning to get to two books that were given to me by their authors for the last month. I am going to tee them both up and try to get to them in the next two weeks. I will write a review of each in the sidebars of my blog. Here are the two books: This is Michael Santarcangelo's book based upon his philosophy in security. I know Santa has been talking about it a long time. I am looking forward to reading what he has to say.
| ||
| Brits Give Up Passwords For a £5 Gift Voucher [Darknet - The Darkside] Posted: 26 Sep 2008 09:15 AM CDT So it turns out you don’t need any fancy password cracking software like John the Ripper or Cain and Abel you just need a handful of £5 gift vouchers for Marks and Spencers! But we had discussed this in part before, some people will give out their passwords if you just ask, some if you offer [...] Read the full post at darknet.org.uk | ||
| Around The Web For Friday [RiskAnalys.is] Posted: 26 Sep 2008 07:56 AM CDT We’re frequently asked what we’re reading and what we like in blog posts, so here are some interesting things that hit our RSS readers that you may have missed: COBIT rivals ITIL from The IT Skeptic
Interesting stuff that. A detailed mapping might help some folks. Either way, the good news for those keen on understanding risk management is that governance metrics, done right, allow us to understand a part of that “capability to manage risk” we’re always looking for. Assurance, verification and the acquisition and interpretation of knowledge is king. Speaking of which…. How To Tell When “Nothing Happens” by Pete Lindstrom
Good analysis is all about the uncertainty. Speaking of accounting for uncertainty… Assets Good Until Reached For by Gunnar Peterson
And there’s the trick. We might call “abstraction assurance” an analog to “confidence” or “uncertainty” in certain priors (metrics) or posteriors (calculated values based on those metrics). The stronger that abstraction assurance is, the less uncertainty we have in our knowledge and the better our ability to create wisdom from that knowledge (you know, make decisions). Epstein, Snow and Flake: Three Views of Software Security by Adam Shostack Adam’s focus is on software security, but the discussion here can be abstracted out into the broader realm of risk management quite nicely. Two-thirds of firms hit by cybercrime from Security Focus The US DoJ says that in 2005 (there’s some timely data) 2/3 of their surveyed firms detected at least one cybercrime. “Cybercrime” is “classified … into cyber attacks, cyber theft, and other incidents.” Pretty general. Also from the report: “Computer viruses made up more than half of all cyber attacks.” (That sound you hear is me tapping my forehead lightly on large iron object) Lessons Learned from "Personal" Risk Management By: Christopher Daugherty
| ||
| the problems of a bank up against Doomberg thinking [belsec] [Belgian Security Blognetwork] Posted: 26 Sep 2008 07:39 AM CDT I am no financial specialist and not one of these postings should be interpreted this way. I just look upon it from a risk and crisis communication look of way, both of which are very important at this moment. This article is Not for republication, linking or citation under the present circumstances as I don't know what the intention of the rest of your article would be and I don't want to be part of that. First it is not necessary to see long lines of people before a bank to know if people are transferring money. It are the totals of daily transactions that count - including online transactions. Seeing no long lines before a bank doesn't mean people are not transferring money. Secondly you don't need a SMS or a rumor (like the mails about Fortis last week) to get people thinking. People are not that stupid that they act as cattle on a message. For some people the continuing messages of the financial market and its indicators are clear enough to take some precautions. I am not saying they should be doing that. I just say that aside from the rumors which can be prosecuted and so on, Fortis should review its communication policy and also take some - even drastic steps - to restore confidence with the little people who have most to lose. If Fortis wants to diminish the anguish of its little people, it should try to stabilize its shareprice at the market (just as is done with currencies). That would be the strongest message to its little people and the market afterwards. If the little people see that everything calms down and gives their bank some leverage (time that is) the market will also calm down and look for another victim to speculate against. Thirdly it looks like the Fortis crisis is a bit becoming a self-fulfilling prophecy and is in the eye of the storm. It is very hard to break this circle and it will need every support it has and every signal it has at its disposal to stop it. It should not wait for long with these signals. Simple declarations are not enough. Fourth. There is a deadline (what a word in such circumstances). For those old enough to remember the speculation against the currencies, it is the weekend. Responsable people in responsable financial positions won't take a holiday this weekend I presume. Fifth. They should remember the other banks that just as with currencies before the EURO or with US banks that the other European banks are also part of the Domino's and that they at least should stick together for the time being. It could end up costing the other European banks more if one of them fell than to intervene together and support each others stock and creditlines. | ||
| Belgian government acts and reacts on financial crisis [belsec] [Belgian Security Blognetwork] Posted: 26 Sep 2008 07:07 AM CDT The prime minister and the minister of Finance have declared together that * the responsable institutions are following the situation very closely and that all measures have been taken (also on the European level) * the money of the people on the Belgian banks is safe and that there is state guarantee for these disposits (how much) * that no Belgian bank (including Fortis) has a problem of solvability (is the CEPS study wrong than ?) * they will prosecute people who spread rumors (fine they have been identified by name in the newspaper and no one from Fortis to contradict or silence them) would anyone learn them the basics of crisis communication ? Do not answer on some of the questions. Answer them all correctly in full and without any hesitation. It is the only way to respond to Doomberg (bloomberg) | ||
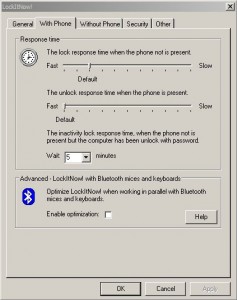
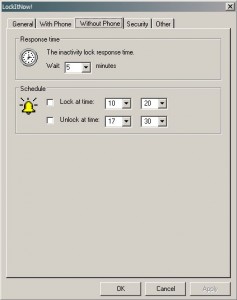
| Workstation (Un)locking Using Bluetooth [/dev/random] [Belgian Security Blognetwork] Posted: 26 Sep 2008 06:59 AM CDT
When you use a workstation (PC, laptop or thin client), it’s important to lock it when you are away for a while or funny things may happen. Usually, the screen is automatically locked after a configurable inactivity period. To unlock it you need to type a password or, on some laptops, scan your finger print. I tested a sympatic application for Microsoft environments called LockItNow!. It replace the standard locking mechanism used in the Microsoft OS by its own system. In the same time, other features are added:
The goal is simple: if the paired device is near the workstation, it’s kept unlocked and way you walk away with the device, it’s locked a few seconds later. You come back (with your coffie There are two methods available to detect the presence of the phone: Bluetooth inquiry (a search) or Bluetooth connect (using a COM port mapped to the paired device). The first method is of course the best one but the application does not support all Bluetooth adapters (and my Dell laptop was not supported). As the iPhone does not provide a serial service via Bluetooth, I was unable to test mine. But it worked perfectly with a old Nokia phone. Even if it’s funny to see your computer locked and unlocked automatically, this tool does not provide enough security. Your mobile can be stolen or your Bluetooth ID can be spoofed! A stronger authentication process is required. (Example: password + phone presence detected) | ||
| Backup Encryption [vandeneynde.net] [Belgian Security Blognetwork] Posted: 26 Sep 2008 06:40 AM CDT Quick Post. I just read that laptops were stolen from one of our Belgian ministries. According to the ministry, the data was safe because it was backed up to a central server. That server was not comprimised and all sensitive data was stored there. I sure hope they also thought about encrypting the laptop hard drives and/or used some kind of DLP system to prevent data to be copied locally on the laptops. If not, the central backup won’t guarantee that no sensitive data was stolen. Availability in the form of backups is just covering one letter of the CIA (Confidentiality, Integrity, Availability) Triad which forms the core of Information Security. | ||
| SecureSphere vs Secure Coding [ImperViews] Posted: 26 Sep 2008 06:34 AM CDT It is becoming more and more common for companies to weigh WAFs vs. secure coding options as they try to determine the best way to protect their web applications. After talking to many developers, one thing I've learned is that many coders are not fully aware of the risks that come with secure coding. And, on a related note, many companies are not fully aware of all the costs that come with secure coding. | ||
| E-land archive : Vragen bij de EID deel 5 [belsec] [Belgian Security Blognetwork] Posted: 26 Sep 2008 05:59 AM CDT | ||
| E-land archive Vragen bij de EID deel 4 [belsec] [Belgian Security Blognetwork] Posted: 26 Sep 2008 05:59 AM CDT Wij houden van normen, standaarden, toezicht en controle tijdens zowel het opstellen, ontwikkelen als het installeren en onderhouden van een ITproject. Met EID zijn wij dan ook niet anders ingesteld dan tegenover elk ander ITproject. Het EID-project zou integendeel zelfs strenger moeten behandeld worden gezien het strategisch belang van dit project voor onze economie en privacy. Men verzekerde ons echter dat er normen en kwaliteitscontroles aanwezig waren en en wie waren wij om daaraan te twijfelen ? Tot dat berichten verschenen in de pers over chips die uit de kaarten vielen en andere vergissingen in de data op de kaarten. Het waren kleine aantallen kaarten die procentueel onbelangrijk leken maar wel een indicator waren dat er een probleem was met de kwaliteitscontrole. Het effect van ons onderzoek was echter dat sommige interne medewerkers ook begonnen te praten en dat zij een boekje opendeden over het gebrek aan kwaliteitscontrole en projectmanagement dat zij zagen. Dit alles moet echter door onafhankelijke ITauditoren worden onderzocht en nadien worden bijgestuurd. En het was dan ook niet aan ons om dit te publiceren, maar wel om beleidsmakers hiervan op de hoogte te brengen. Dit stukje over normen en standaarden kon echter niet worden afgesloten zonder een verwijzing naar de disucssie over normen tussen Microsoft en de aanhangers van EID. Microsoft had zich van in het begin sterk geïnteresseerd in ons EID project. Bill Gates was indertijd zelfs naar België gekomen om er een valse EID te ontvangen. Na deze PR push bleek het allemaal nogal stil te vallen. De nieuwe CEO van Microsoft België gooide echter dit jaar de steen in het kippenhok. Hij stelde dat Microsoft zich enkel zou houden aan internationale kwaliteitsnormen en -standaarden op het vlak van smartcards (wat een EID is) en liet verstaan dat EID daar misschien wel niet aan voldeed. Het leek voor de buitenstaanders een bijzonder moeilijke discussie, maar ze is niet zonder belang. Het is niet echt duidelijk wat de huidige houding is van Microsoft tegenover de EID, maar het lijkt er wel op dat Microsoft de lat wilt hoger leggen dan men oorspronkelijk bij ons met EID van plan was. Misschien speelt hierin het feit dat Microsoft op het vlak van veiligheid doorheen haar hele bedrijf en gamma de kwaliteitslat steeds hoger aan het leggen is. In veiligheid is stilstaan in feite achteruitgaan. Het wordt misschien tijd voor een grote sprong voorwaarts voor de Belgische EID. | ||
| iPhone vs. Android [/dev/random] [Belgian Security Blognetwork] Posted: 26 Sep 2008 01:21 AM CDT | ||
| Posted: 25 Sep 2008 04:36 PM CDT | ||
| Humor: Worldwide SQL Protocol Advisory [CGISecurity - Website and Application Security News] Posted: 25 Sep 2008 04:15 PM CDT The full disclosure mailing list is usually 95% junk but every once in awhile an amusing/informative post gets through. Today an amusing post came through regarding a 'Worldwide SQL Protocol Advisory'. That's not to say this post isn't junk, but I found it amusing :) Here's a peek "II. Problem descriptionThe... | ||
| Chance to Meet: Gartner ITxpo in Orlando, FL [RioSec] Posted: 25 Sep 2008 01:46 PM CDT I am planning on being at the Gartner ITxpo Symposium in Orlando, FL from October 12th-16th for the Security and Risk Management track. If you are going to be at ITxpo or live in the Orlando area, please drop me a note at http://riosec.com/contact so hopefully we can meet up at the event or in the evening. - Christopher | ||
| Insecurities in Privacy Protection Software [Security Coin] Posted: 25 Sep 2008 11:23 AM CDT I recently wrote an article for INSECURE Magazine (awesome mag BTW!) on the lack of protection given to one's sensitive information, ironically, by the very software that claims to protect it in the first place! These security companies seem to be riding on a new wave of PII protection - and the vendors are scurrying to come up with their own versions of a solution, forgetting all about secure software development practices. The importance of writing secure software cannot be stressed upon enough. Security vendors should know that. The article is at http://www.net-security.org/dl/insecure/INSECURE-Mag-18.pdf Or read it online at http://issuu.com/insecure/docs/insecure-18/44?mode=a_p Also - Jeremiah Grossman's nice article on the bitter reality of Web Browser security. While on the topic of vendors - What vendor in his right mind would send something like this to a security contact in a company.. mind you - this vendor has NO NDAs with us - and I have had no prior contact with this guy.  I have no idea if a project like that even exists in the company, but it sounded like an important security project that should definitely be company confidential information. On quizzing the person, he replied that he got that information from his 'inside sales folks'.. riigggght. I asked for names. I haven't heard from him since. | ||
| Interviewed for WNIN radio [Network Security Blog] Posted: 25 Sep 2008 10:51 AM CDT I was interviewed yesterday morning for WNIN 88.3 FM in Evansville to talk about how Sarah Palin’s account got hacked and how it affects the average user. I thought the interview went well and I didn’t sound like too much of an idiot. You can listen for yourself, it’s now been published as part of the third episode of Plugged In, the podcast that accompanies the radio show. | ||
| One more time - HIPAA, not HIPPA [An Information Security Place] Posted: 25 Sep 2008 09:45 AM CDT | ||
| Posted: 25 Sep 2008 09:43 AM CDT In part one we talked about some of the mistakes that companies make when it comes to risk management. In this post we will focus on some of the items that a company can do to improve their risk management programs. What I will lay out are three points/characteristics/aspects that a solid risk management program must have in order to be effective. Point One: A common risk framework must exist throughout the organization, not just within one department. This framework must: · Use a common definition for "risk;" · Support appropriate standards, regulations, guidelines; · Clearly define the key roles, responsibilities, and authority relating to risk management; · Support all of the business units and functions both in the way that these units accomplish their jobs as well as in the performance of their risk responsibilities. Many organizations recognize that risk means "the chance of something going wrong, hazard, statistical odds of danger" to quote the Encarta Dictionary. What they forget is that there are positive aspects to risk. Risk can be seen as the opportunity to create and preserve value. When I think of risk in this way an old saying comes to mind: "When Life gives you Lemons, make Lemonade." In other words you need to create opportunity out of adversity. Business is about risk. There is no way to avoid it so why not simply seek to nullify its effects when you can leverage it to gain an advantage. In my experience, the companies that embrace this concept of managing risk succeed not only in risk management but in the marketplace itself. Point Two: Senior management must have the primary responsibility for the risk management program. This means its design (it must be appropriate for the whole organization), its implementation (it must not favor one unit or function over another), and its ongoing operation. Most importantly senior management must have complete visibility into how the organization (and each of its constituent components/units) manages risk. This means that risk must be coordinated across the entire organization. Risk must be everyone's responsibility; even those people who do not think they have any responsibilities with regard to risk. True implementing technical security controls may be the primary responsibility of the IT department but in order for that implementation to be successful all departments and functions must share the responsibility. IT needs to know if a particular control causes too much interference with the way the business is run so that they can make adjustments or implement alternative controls to reduce interference to a minimum. The other departments and functions must realize that there are valid business reasons that these controls must be implemented. Senior Management needs to send the message that risk is a collective concern. In order to do Senior Management needs to ensure that they communicate clearly and effectively. They need to nurture a culture focused on risk (how to manage it and overcome it for the organizations benefit). They need to institute a rewards program to provide positive reinforcement and they need to institute an effective learning program to educate everyone on what parts they play in the grand scheme of things. Point Three: Risk is an everyday concern and on every agenda not just on certain scheduled meetings. Each business units/function is responsible for the performance of not only their business and the management of risks they take. This is important because it speaks to ownership and accountability. Not everyone is going to like this. Honestly they don't have to but they do have to climb on board and support the effort. It is analogous to having to abide by the covenants in your homeowners association. If you move into a neighborhood with a home owners association, then you agree to abide by the rules that the association agrees upon. If you don't want to do that then there are other homes that are not part of associations just as there are other companies to work in. (Of course there are always rules set forth by the local, state, and a national government that we must abide by – that is part of living in an ordered society. ) Now not all business units or functions have the same scope when it comes to risk. Some departments "own" risk management because they are the profit generating arms of the organization and other departments (such as HR, IT, finance, legal, etc) support these profit generating arms. These supporting functions own the risk that arises out of their own area of responsibility in addition to sharing in the overall responsibility of supporting the overall organization. It is very important (to harken back to Point One) that these functions have well defined articulated roles within the overall risk management program. They must participate in risk discussions even when it is not clear that these discussions are directly related to them. I could go on but this post is getting a bit long already. To sum everything up – risk is everyone's responsibility. Companies trade risk for reward daily so it shouldn't be too large a leap to remind ourselves that the risks we face on a daily basis need not only be seen as a drag on the balance sheet. They can be seen as opportunities to be leveraged. Instituting a risk management program that pays attention to the three points that I have made above will do just that. |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |

![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=c8a0bce4-2617-473c-ac52-1b26f45ceef0)








No comments:
Post a Comment