Spliced feed for Security Bloggers Network |
| GEO Tagging Attacks [SOURCE Conference Blog] Posted: 04 Oct 2008 05:34 AM CDT I am working on a Parser that transforms any kind of ASCII input log file into KML files used in Google Earth/Maps. What does it do? 1. Reads the log Why? Well I was recently analyzing a big set of IDS events with abut 99% of false positives. Most of them originated from partners of the company located in England and France. Only a few of them - the real positives - originated from countries like Iran, Pakistan, Brazil, Russia and China. The picture is an animated GIF. Hope this format comes through. :) I'll provide a download link for the script soon. (the sticking point is the GeoIP database; most of them are commercial ones; currently I use TOR network and a GEO IP web service to determine the LAT and LON parameters. That should not be the final solution, right?!) | |||||||||||||||||||||||||||||||||||||||||||||
| GEO Tagging Attacks [Security Data Visualization] Posted: 04 Oct 2008 05:34 AM CDT I am working on a Parser that transforms any kind of ASCII input log file into KML files used in Google Earth/Maps. What does it do? 1. Reads the log Why? Well I was recently analyzing a big set of IDS events with abut 99% of false positives. Most of them originated from partners of the company located in England and France. Only a few of them - the real positives - originated from countries like Iran, Pakistan, Brazil, Russia and China. The picture is an animated GIF. Hope this format comes through. :) I'll provide a download link for the script soon. (the sticking point is the GeoIP database; most of them are commercial ones; currently I use TOR network and a GEO IP web service to determine the LAT and LON parameters. That should not be the final solution, right?!) | |||||||||||||||||||||||||||||||||||||||||||||
| Humble Pie [BumpInTheWire.com] Posted: 04 Oct 2008 12:42 AM CDT Its late as hell and I’ve been up to my eyeballs in Visio diagrams. Time for my weekly Husker pick. Missouri is a 10.5 point favorite in Lincoln, NE tomorrow night. They have not won there in 30 years but that streak ends in 2008. Give the points. Missouri 44 Nebraska 17 Just typing that gave me a stomach ache! | |||||||||||||||||||||||||||||||||||||||||||||
| Introduction to SIP [/dev/random] [Belgian Security Blognetwork] Posted: 04 Oct 2008 12:20 AM CDT
SIP (or Session Initiation Protocol is a protocol commonly used in VoIP applications. Here is a good introduction of SIP (within a funny context): VoIP Demystified: SIP. | |||||||||||||||||||||||||||||||||||||||||||||
| Grecs’s Infosec Ramblings for 2008-10-03 [NovaInfosecPortal.com] Posted: 03 Oct 2008 11:59 PM CDT
| |||||||||||||||||||||||||||||||||||||||||||||
| Delta steps into big brother role, do they belong there? [StillSecure, After All These Years] Posted: 03 Oct 2008 10:09 PM CDT  Image via Wikipedia I for one was pleased to hear about Delta Airlines plans to start offering wi-fi access on domestic flights. I figured being a platinum medallion member there is a good chance I may even get access for free. I frankly was worried about security while logged on in the air. In a "closed" environment on the plane a malicious individual could play havoc with folks whose security settings may not be up to snuff. But what makes logging in on the plane any different than logging on at the airport? Now comes reports in the Atlanta Journal-Constitution and a follow up in ComputerWorld by Mike Elgan, that Delta will implement some sort of content filtering application to make sure that inappropriate web sites are not accessed while on the plane. This raises several issues in my mind. First of all what makes Delta the judge of what is appropriate or not. Second isn't it a bit imbecilic that they may prevent access to pornographic web sites, but have no problem with people running a porno DVD on their computer. If keeping smut off the plane is the goal, what difference does it make if it is via the web or on a DVD? Lastly, what happens when inevitably the filtering solution blocks a legitimate web site? If I paid for that access and was unable to access what I wanted and it was a legitimate site, is Delta going to refund my fees? It seems to me that when Delta steps into the role of big brother and is going to regulate what I am allowed to see, I am having to conform to their views on what is normal. If I am paying my own hard earned cash, as long as it is legal, Delta should not have the right to filter me. I want to make my own decisions. I also think that this is a case where the market will take care of itself. Peer pressure will stop people from viewing smut on the plane better than Delta's big brother censors. Related articles by Zemanta | |||||||||||||||||||||||||||||||||||||||||||||
| New York Information Security Community [Kees Leune] Posted: 03 Oct 2008 08:19 PM CDT Today was the first meeting of the New York Information Security Community (nyinfosec). nyinfosec provides an information security focus group for Long Island-based practitioners, but attendees from New York City are also welcome. While the number of attendees was a little disappointing, the content of the discussion was great. We covered a great amount of topics, ranging from netflow analysis tools to DMCA infringement notices, via a little sidestep to policy development and incident response. All participants agreed that the initiative adds value, and that the meetings should continue. A new date has not yet been set, but we're shooting for a cycle that has meetings every 2-3 months. If you are a security practitioner on Long Island or in New York City, please let me know and I'll be glad to provide you with more information. | |||||||||||||||||||||||||||||||||||||||||||||
| Tim Callan on TV [Tim Callan's SSL Blog] Posted: 03 Oct 2008 07:03 PM CDT Today I shot a live segment on online security for San Francisco station KGO's afternoon show View on the Bay. I had a great time. I'm not seeing the segment archived on the site, but maybe it's too fresh. I'll look for it and post it if it goes up. In the meantime, feel free to enjoy this segment I shot for Las Vegas TV a couple of weeks ago. | |||||||||||||||||||||||||||||||||||||||||||||
| From Hollywood: Don't Vote (Unless You Care) [The Falcon's View] Posted: 03 Oct 2008 05:22 PM CDT | |||||||||||||||||||||||||||||||||||||||||||||
| Removable media security at work in Japan [Security4all] [Belgian Security Blognetwork] Posted: 03 Oct 2008 05:11 PM CDT  WhatJapanthinks.com has some interesting facts and figures about removable media security at work in Japan. With flash capacity becoming bigger and bigger and more integrated into devices; it's important to be aware of the consequences. For example, secure deletion doesn't work the same as it does for magnetic storage. Have a look at this presentation from CCCamp2007: 'What you always wanted to know about Flash memory - but were afraid it could be true'. Now, I would be interested in similar figures for Belgium. (Photo under creative commons from kaihizzle's photostream) | |||||||||||||||||||||||||||||||||||||||||||||
| Stupidity Prevails: How the Bailout is Like Enterprise Security [The Falcon's View] Posted: 03 Oct 2008 05:02 PM CDT | |||||||||||||||||||||||||||||||||||||||||||||
| Napera @ SMBnation [Napera Networks] Posted: 03 Oct 2008 04:57 PM CDT The Napera team will be at the SMBnation fall conference in downtown Seattle this weekend, talking to folks from around the country. Drop by and say hello! | |||||||||||||||||||||||||||||||||||||||||||||
| Gartner DOES have a sense of humor - sometimes [Amrit Williams Blog] Posted: 03 Oct 2008 04:52 PM CDT Greg Young (here) and John Pescatore (here) have started blogging on the Gartner Blogging network and many of the posts are both enlightening and humorous, such as this post from Greg Young on how to get rich from network security (here) - about time Grumpy and the Bear got a sense of humor
 | |||||||||||||||||||||||||||||||||||||||||||||
| Using Google to Identify Security Trends [Gilbert Verdian - Security Advocate] Posted: 03 Oct 2008 03:55 PM CDT The other day I was thinking about what is the best way to identify current trends on a macro level, to have an overview and understanding of what is currently happening and more importantly where to focus to mitigate against the risks and threats. Currently my RSS feeds bring in over 1000 items a day, which is great on a micro level, but I wanted something with a wider view. So decided to try Google Trends and feed it some security keywords which gave some interesting results. Keyword: 1) Hacking
This show’s Pakistan, India and Indonesia were the top 3 countries who searched for hacking and there’s a small and general increase for the term since 2004. 2) Zero Day Zero day (0 day) was almost non-existent before 2004, the increasing trend seems quite accurate as the previously underground term found itself into in the mainstream media. Surprisingly Finland is on top searching for zero day the most, whereas India who topped “hacking” is now listed as number 8. Another noteworthy entry is Romania, which compliments trends of eastern European countries that have been increasing their activity in this area, especially as organised crime is involved. 3) Phishing Phishing similarly evolved around 2004, with its peak around the middle of 2005. The trend show a slight decline possibly reflecting the increase in user awareness to not click on suspicious links. 4) Botnet 2004 seems to be quite a popular year where botnets also took the stage. The gradual rise in the term searches does reflect the amount of attention in the mainstream about them. The peaks show the main headlines covering stories regarding the popular botnets Storm and Kracken and the law enforcement successes by the FBI and Dutch police. Don’t exactly know why Norway is the top country searching for botnets. The OS Wars 5) Operating Systems (Linux, XP, Vista, Apple) This shows the steady decline of XP and Linux, the rise of Vista and OSX (Mac & Leopard revealed an almost zero result so decided to use the term Apple to be more comparable). 6) Linux Linux searches have surprising been decreasing over the last 4 years. I would have thought with the popularity of ubuntu it will be on the rise. The amount of news stories covering linux in the lower graph seems to be constant. 7) Ubuntu Showing the unsurprising increase of Ubuntu since 2004. One thing that I find interesting is that Italy is number 1 for Ubuntu searches, open source must be quite popular in Italy. Apple has had an expected increase reflective of its increase in market share over the years. The launch of the iPhone has obviously helped with its popularity. 9) BSD A favourite of mine, showing the enormous decline in popularity of the the *BSD family. Still FreeBSD is on top and Russia and Ukraine are the top countries. My favourite, BSDi, has not been around for quite a while. 10) Unix Searching for Solaris, AIX and HPUX reveals and overall steady decline in popularity. Solaris and AIX evening out in 2008 and India, Singapore and Japan being the top countries for Solaris. The Security Vendors 11) McAfee Vs Symantec Both companies have been quite close over the years. The next graph details the activity in 2008. Also the Asian countries seem to be on top searching for Symantec. 12) McAfee Vs Symantec 2008 A closer view show’s McAfee was searched the most and it overtook Symantec for the first time. In Conlusion Google trends doesn’t replace hard metrics, threat reports from industry sources, correlated logs and alerts etc. But it does give you an insight on what people are searching for and from which geographic regions, thus giving you some awareness of what is going on, where to focus your attention on and what to look for to help mitigate threats and risks. If you have some interesting searches please feel free to link back and display your results. | |||||||||||||||||||||||||||||||||||||||||||||
| Published in EDPACS: "Key Management: The Key to Encryption" [The Falcon's View] Posted: 03 Oct 2008 03:40 PM CDT | |||||||||||||||||||||||||||||||||||||||||||||
| Malicious Pop Ups Still Fake Out Users [The IT Security Guy] Posted: 03 Oct 2008 03:21 PM CDT According to recent study, even well-informed users, who should know better, can be caught by malicious pop up windows. The screen shots in the study, conducted by a group of psychologists at North Carolina State University in Raleigh, show some pretty impressive fake pop ups. Now, remember, these aren't phishing sites. They're web sites designed to look like error messages packed in error-sized windows. Clicking on the "x" in the upper right hand corner of the window prevents redirection to a malicious site. Clicking on "OK," as many study participants did, well . . . who knows what evil lurks. | |||||||||||||||||||||||||||||||||||||||||||||
| See You At SecTor (Toronto) and/or DayCon (Dayton) [Rational Survivability] Posted: 03 Oct 2008 02:22 PM CDT
I've spent some serious time talking to users, vendors and analysts regarding some of the research I've been doing on current and future state virtualization technologies and roadmaps. To cap of this year's events, I'll be at SecTor in Toronto on 10/8-9 and DayCon in Dayton from 10/10-12.
Hope to see you in Toronto or Dayton, eh? /Hoff | |||||||||||||||||||||||||||||||||||||||||||||
| Layers 8 and 9 deep inspection? [Emergent Chaos] Posted: 03 Oct 2008 02:04 PM CDT | |||||||||||||||||||||||||||||||||||||||||||||
| The Skype Issue [Emergent Chaos] Posted: 03 Oct 2008 02:03 PM CDT According to The New York Times in, "Surveillance of Skype Messages Found in China," the Chinese provider TOM has software in place that reads Skype text messages, and blocks ones that use naughty words and terms, like "Falun Gong," "Independent Taiwan," and so on. A group of security people and human rights workers not only found out that TOM-Skype is not secure, but found the list of banned words because, as usual, someone didn't set up their servers very well. A report can be found here. Skype president Josh Silverman replied to the issue today in this article. He says that yes, it's happening: It is common knowledge that censorship does exist in China and that the Chinese government has been monitoring communications in and out of the country for many years. This, in fact, is true for all forms of communication such as emails, fixed and mobile phone calls, and instant messaging between people within China and between China and other countries. TOM, like every other communications service provider operating in China, has an obligation to be compliant if they are to be able to operate in China at all. He's right: one of the quandaries of business in China is that you have to put your belief in freedom in a trust when you go there. This is why many of us do not like doing business there. However, he also said: We also learned yesterday about the existence of a security breach that made it possible for people to gain access to those stored messages on TOM's servers. We were very concerned to learn about both issues and after we urgently addressed this situation with TOM, they fixed the security breach. In addition, we are currently addressing the wider issue of the uploading and storage of certain messages with TOM. In other words -- it's bad for the Chinese to spy, and bad for people to catch them at it. Oh, naughty Chinese, and shame on you too, Infowar for dragging this into the daylight. This comes on top of April's flap in which the German and Austrian governments essentially said that they have no trouble listening in to Skype. Skype hasn't commented on that. This is a different issue, as it appears that the surveillance is being done via malware. Despite the fact that we still don't know what goes on inside of Skype, it appears that the software is basically secure -- or at least the voice parts are. Or was at one time. The noted cryptographer Tom Berson did an analysis of Skype and showed that it was reasonably secure. There were also reverse-engineering analyses done on Skype by Philippe Biondi and Fabrice Desclaux, presented at Black Hat in 2006 that showed it was secure, if eccentric in its design. However, despite the security of the voice parts, the text parts are obviously not secure. And we have this uncomfortable set of circumstances:
The problem here is one of labeling, and the market effects. I'm sophisticated enough to know that when Josh Silverman says: ... Allowing the world to communicate for free empowers and links people and communities everywhere. that he is stating that free (as in beer) is important, even if he's unable to do a lot about free (as in speech) in repressive countries and in the face of law enforcement technologies. But Skype has always touted itself as a secure technology. The reason that it became popular for free (as in beer) conversations was that we thought and were assured that it was also free (as in speech). Skype themselves paid for a security analysis. Skype thus became not only the proverbial eight-hundred pound gorilla, but (it seems) the proverbial dog in the manger. Skype's presence has actively hindered other secure-voice technologies. Phil Zimmermann's Zfone, for example, has had to answer the question, "why do we need you when there's Skype?" It seems that he'll be answering that question less. Josh Silverman needs to do something to show us the basic integrity of the system. Presently it appears that he has empowered us to have communities everywhere but China, or Germany, or any place with a sophisticated and powerful government. At the very least, he should protect eBay's investment, because if people conclude that Skype is not secure, eBay may wish they'd invested that $1.6 billion in mortgage-backed instruments instead. | |||||||||||||||||||||||||||||||||||||||||||||
| One Day in the Life of the SANS Internet Storm Center [/dev/random] [Belgian Security Blognetwork] Posted: 03 Oct 2008 12:21 PM CDT
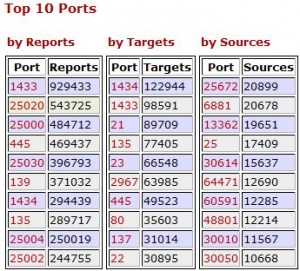
Yesterday, I attended a very interesting session about the SANS “Internet Storm Center” (ISC). This event was organized by the Belgian ISSA Chapter in Brussels. As I’m a daily ISC users for a long time, it was very interesting to have a “back stage” overview of this organization. The Internet Storm Center runs on a 24 x 7 basic and incidents are managed by ~35 handlers. All of them are volunteers and take a shift of 24 hours of duty. There are spread worldwide to cover all timezones. Everybody can participate by sending incident reports or just suspicious activities detected on networks. Based on simple rules, they can decide if the reported information is useful to the community and publish it. The on-duty handler writes one diary. Several updates may be released if new events or updates occurred. Question: how can you participate more actively with the ISC? Check out dshield.org. If you manage a firewall you can submit your logs and statistics will be generated (per IP address or port - source or destination) as the following example: They provide log parsers which can handle almost all type of logs. Check the list: here. Personally, I submit firewall logs since 2003 (with some period of interruption from time to time). Feel free to join! The ISC produces an excellent day to day job and is a must read for all people who deal with Internet or security in their job. | |||||||||||||||||||||||||||||||||||||||||||||
| What's in a name? A Candidate by any other name... [Emergent Chaos] Posted: 03 Oct 2008 10:55 AM CDT  For those who haven't been listening closely to their NPR, it turns out that there are at least eight Barack Obamas running for election in Brazil this year. Yes, you heard that right. Under Brazilian law, it turns out, candidates are allowed to run for office under any name, as long as it's not offensive. So eight aspiring politicos, including a former air conditioner salesman and a man claiming a resemblance to Obama (but not actually bearing one), have officially changed their names in hope that it will bring them victory in October's municipal elections.Sorry to be getting political. We'll try to keep it chaotic, emergent and fun. Via Concurring Opinions. Photo: AP | |||||||||||||||||||||||||||||||||||||||||||||
| Friday News and Notes [Digital Bond] Posted: 03 Oct 2008 10:27 AM CDT
| |||||||||||||||||||||||||||||||||||||||||||||
| Posted: 03 Oct 2008 08:47 AM CDT  Image via Wikipedia OK I admit it. As I wrote earlier I am reading Friedman's book Hot, Flat and Crowded. I am very charged up about the challenges we face and what it is going to take to really change the world. When I read about Google's 4.4 trillion dollar clean energy plan I was intrigued. There was a time when a number like 4 trillion would really peak my interest, but in these times of 700 billion dollar bailouts, what is a measly 4 trillion anyway. Beyond the numbers though, the Google plan is rather simple.
If we can do these three things, we could unlock millions of new jobs and change the world. You can read more directly from the Google folks here. The cost would be about 4.4 trillion and we would have a net return of 1 trillion by 2030. I especially like the smart house idea that like in Friedman's book, gives consumers the ability to use electricity based upon up to the second pricing. This recognizes that there are peak times and non-peak times and prices should be different for each. All of this is well and good, but is this Google's new mission? I know they want to change the world, but I thought it was by cataloging the worlds information. Yeah, they are supposed to be a cool company and all, but should our energy policies and plans be coming from the guys who bring us search? Is Google biting off more than it can chew by plowing cycles into this? They are trying to figure out how to monetize their business beyond search. They have the whole android thing going on, plus countless other projects in beta. Do they have the cycles to spend on the energy plan? If you are a shareholder in Google do you want to see them spending a ton of money on this unless they can show where there will be a return on this investment? Google may in fact be a great company. But if they are spending money on figuring out how to solve the world's energy issues without a way of becoming a major player in that market and making huge profits by it, what are they doing. Is their too much fat in Google's budget? Are they tilting at windmills (and maybe solar panels too)? Related articles by Zemanta
| |||||||||||||||||||||||||||||||||||||||||||||
| IPHONE mailreading : be careful [belsec] [Belgian Security Blognetwork] Posted: 03 Oct 2008 08:41 AM CDT The problem with Apple is that they see functions as absolute dogma's and aren't prepared to think about it. If they think that they are right, there is no way that you are going to convince the 'elite' of the computeruniverse (as they see themselves) that they are in fact very wrong. They have untill now not be able to establish a working relationship with security researchers and have had for this reason several confrontations and also no goodwill at all. Firms need that goodwill - based on past experiences and the belief in the good intentions - to have some complacency when they can't deliver the solution in time for whatever reason. This is what happened to this security researcher "I have disclosed the technical details to Apple few weeks before that post, in a hope to get those security issues fixed as soon as possible. Unfortunately, two and a half months later, and still there is no patch for those vulnerabilities. I've asked Apple several times for a schedule, but they have refused to provide the fix date. Three versions (v2.0.1, v2.02, v2.1) have been released since I provided them with the details, and they are still "working on it". Therefore, I've decided to publicly disclose the technical details." The facts are these - and the things you can do 1. Do not respond to mails asking you to log in as you won't see the link itself when the subdomain is longer than 24 letters. You will not see the full link. For example https://www.securitycontrolcenter-logonrenewel.facebook.com.myrewards.com/.......... 2. If you read your mails with your iphone all images (or things that look like images because of their extensions) will be automatically downloaded. This is plain stupid. So if you wanna mess up someone's iphone you can send him a mail with links to a very huge image or an imagebomb (images opening links to other images that each open images to other images that each open images to other images.....) | |||||||||||||||||||||||||||||||||||||||||||||
| RFID skimming illegal in California [belsec] [Belgian Security Blognetwork] Posted: 03 Oct 2008 08:24 AM CDT RFID Journal reports that anyone skimming an RFID tag issued by a government agency, health insurance company, employer or library could find themselves in prison for up to a year, or facing a $1,500 fine, though you're OK if you read it by accident, for a medical emergency or if you're a law-enforcement official. http://www.theregister.co.uk/2008/10/02/rfid_skimming_ban/ And so the RFID industry will be very pleased to know that security researchers have also no exception and that vulnerabilities will so be less publicised and that they can continue to try to convince the public that all is safe and well and that there is nothing to worry about - because they aren't told anything else. | |||||||||||||||||||||||||||||||||||||||||||||
| SKYPE : an example of a SKYPE policy in networks [belsec] [Belgian Security Blognetwork] Posted: 03 Oct 2008 08:04 AM CDT Instances of Skype on the University network have been found to be the highest users of network resources. This is likely because the software can act as a Supernode. From the Skype privacy policy: "A Supernode is a computer running Skype Software that has been automatically elevated to act as a hub. Supernodes may assist in helping other users to communicate or use the Skype Software efficiently. This may include the ability for your computer to help anonymously and securely facilitate communications between other users of the Skype software who, due to network and firewall constraints, cannot establish direct connections." Therefore, running Skype means your system can (and probably will) participate in providing Voice over IP (VoIP - internet phone calls) services outside of your direction and control. You are also agreeing to provide services to Skype for resources owned by the University. Individual users are not empowered to give such consent. Because of these potential risks, other options are to use a different VoIP service or limit how you used Skype. Before using Skype or another similar product, please communicate with your IT staff, and be sure to configure the software so that your computer and the University network will remain secure. There are other free VoIP services (such as Free World Dialup ) that are relatively easy to use and have clients for Windows, OS X, and Linux. This does not represent an official recommendation by the University for this service. To control how Skype works:
Having Skype active only when in use will prevent it from becoming a supernode, and routing other phone calls and using excessive network resources. | |||||||||||||||||||||||||||||||||||||||||||||
| Skype espionage how does it work ? [belsec] [Belgian Security Blognetwork] Posted: 03 Oct 2008 07:58 AM CDT The installer creates two files in c:\Program Files\Skpye\Phone, "Skype.exe" and the cleverly named "ContentFilter.exe". The Description field for ContentFilter.exe says "TOM Word Review". It appears to be written in Delphi. http://www.metafilter.com/51004/Skype-working-with-China-Censor) ps can you change the contents of the file ? | |||||||||||||||||||||||||||||||||||||||||||||
| SKYPE is not SAFE in China, but is it safe an sich [belsec] [Belgian Security Blognetwork] Posted: 03 Oct 2008 07:54 AM CDT The findings unearthed and documented by NartVilleneuve in Here we have a major software tool used to make telephone calls and send instant messages over the Internet, advertising secure end-to-end encryption, and widely touted by activists and dissidents as a safe way to communicate sensitive information, logging sensitive keywords and uploading entire transcripts of conversations to servers in China, which themselves are insecure. How insecure? Villeneuve was able to view, download, and archive millions of private communications, ranging from business transactions to political correspondence, along with their identifying personal information. Although some have mooted that Skype is equipped with a backdoor for intelligence, and that TOM-Skype in particular contained a Trojan Horse for the Chinese government, the company publicly denied these suspicions. Villeneuve’s research definitively shows these denials are untrue. Although Villeneuve’s trail runs cold at the doorstep of eight TOM-Skype servers in China, the underlying purpose of such widespread and systematic surveillance seems obvious. Dissidents and ordinary citizens are being systematically monitored and tracked. comment : And elsewhere ? What about Russia, Algeria and other democracies that have also such controls on the internet ? Or even the Patriot Act in the US ? And if he can hack into the servers, why not any other cyberwarrior. Leave skype dead if you want to have privacy and security. Because if you can't trust them there, where and when can you trust them ? Trust is not something that you can split. You trust or you don't. And that you have to earn, every day, anywhere anyhow whenever.
| |||||||||||||||||||||||||||||||||||||||||||||
| TC/IP flaws some last thoughts for today [belsec] [Belgian Security Blognetwork] Posted: 03 Oct 2008 07:34 AM CDT From this excellent blogposting I remember this "this is about the best vulnerability we could request. If you're vulnerable, and you're attacked, you'll notice." (that is if you an avaibility or uptimemonitor working) A solution I remember from this excellent blogposting : "The trick is to create billions of connections, with special tools like this, then verify that once everything is gone, that you indeed have gone back to zero resources. " And at the end after reading tens of articles and seeing hundreds of comments I think I am only a bit wiser. If I would resume it It would come down to this * crimegangs and script kiddies are made aware that they could ddos something with very little resources and it wouldn't surprise me if we would see more ddos attacks. If we are talking about cyberwar situations than every machine in country A is capable with this attack of blocking out a server or router in country B. Now you would need thouands of patriotic PC's to contribute to your ddos attack * I still do think that the whole matter has been handled quite stupidly and we will have to wait the conference. Or it is hype and ain't working in the real world (like their tool it seems) or the producers are just again very irresponsable. * I see a lot of discussion about the issue, but not many people looking for solutions, workarounds. Even if you don't have all the details, you can more or less have an idea about what the methodology and effects will be. The ISP's should began thinking about 'clean pipe' offers. | |||||||||||||||||||||||||||||||||||||||||||||
| IAPP 2008 Privacy Academy [The Security Catalyst] Posted: 03 Oct 2008 05:41 AM CDT Hi Everyone, I just got back from the IAPP 2008 Privacy Academy and it was a great opportunity to meet other privacy individuals from all over the world. As many of you know, the IAPP is one of the premier not-for profit organizations for legal, security, and IT professionals. It was a three-day event for industry leaders to come together and learn about the challenges that organizations are facing in their industry. I sat in on many sessions related to these issues and I wanted to share some of what I learned with you. In these difficult economic times, one of the challenges to protecting information and setting up a privacy compliance program is getting the necessary funding from management. It is often difficult to get support without convincing the CFO that creating and complying with privacy mandates is a business saving endeavor. The panels spoke at length that in their case, they had experienced a data-breach of one of their clients and this was the impetus for change. Unfortunately, this is often the case in many businesses. The key is to take preventative measures to avoid this from happening. However, this can’t be done unless management realizes the dangers of non-compliance and the possibility of FTC sanctions. Another excellent session was given by Jay Cline titled "50 Best Metrics for data Privacy and Security Status." He outlined the specific metrics to perform a privacy audit on an organization and present to management clear steps where improvement is needed. The session gave us an overview of GAPP: General Accepted Privacy Principles. The audience went through it and how to apply it to a hypothetical organization. The primary objective of the IAPP is to network with our fellow privacy members and learn from what others are doing. Aside from the actual sessions, the most important part of the IAPP is to meet with people in our industry and have sit-downs on how our counter-parts are taking on new regulations and laws in their industry. I am definitely going to attend the next IAPP Academy which is being held in Washington, DC. If anyone else out there is interested in attending, please do not hesistate to contact me and we can meet up in March. |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |

![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=4d42742e-e050-4f1e-95c2-10a1cc8304d3)














![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=c2f66203-b74d-4cea-b5fb-7ddcb7750a9e)
1 comment:
Know why you want to be in security and what you want to be doing in 5 or 10 years then trace back the steps that it’ll take to get there. The path you take probably won’t resemble your plan in any but the vaguest outline, but the only way to reach your goal is to have one in the first place. Saying to yourself “I want to be a security professional” is a good start though.
-------------------
Angelinjones
Interactive marketing
Post a Comment