Spliced feed for Security Bloggers Network |
| The most insecure banking/sales terminal [Security x.0] Posted: 14 Jul 2008 05:51 AM CDT Can you imagine an ATM running Windows XP Home Edition and being connected to the Internet or a Point of Sale terminal running Tetris? – Unlikely! Why then is allowing a customer to use any computer on the Internet to connect to the banking system, and transfer much more money than you can take out of a cash machine, a good idea? Why did arguably the most conservative organisations in the world – the banks – agree to lower their defenses so low that they practically invited the criminals in? The answer is simple – the same reasons why even risk-averse investors were chasing after every Internet company in the late 90s – the attractiveness of the global scale and reduced costs of e-channels. Over the years, payments and savings have always been a subject of the most advanced protection:
These are all very sensible measures that work (to one degree or another) to protect customers' and banks' money. Today, however, there is a huge imbalance between the value of electronically accessible funds and their security. This is being very effectively exploited by criminals and the banks are looking for a solution. Personal computers are not tamper proof sales terminals, therefore it is unfeasible to rely on the customer to keep them 100% secure. No one can take away online banking but banks can deploy new security measures, and solving this problem requires a new innovative approach that can equally address security, ease of use, and cost. At Cronto, we identified this imbalance years ago. We also correctly predicted that the only solution to address this problem is transaction authentication (where the customer confirms each banking instruction). We then developed an innovative visual transaction signing solution. Based on our unique Visual Cryptogram, the Cronto solution supports multiple end user options allowing the bank to choose what is right for their customers whilst maintaining consistency in their backend systems. |
| FWAuto v1.1 - Firewall Auditing & Ruleset Analyzer Tool [Darknet - The Darkside] Posted: 14 Jul 2008 01:48 AM CDT FWAuto (Firewall Rulebase Automation) is a Perl script and should work on any system with Perl installed. Provide the running config of a PIX firewall to fwauto. It will analyze and give you a list of weak rules in your rule base and store the result in multiple output files. Maybe there have been times when [...]SHARETHIS.addEntry({ title:... Read the full post at darknet.org.uk |
| Another Apple Security Update: XCode 3.1 [Infosecurity.US] Posted: 13 Jul 2008 09:44 PM CDT
|
| links for 2008-07-14 [Raffy's Computer Security Blog] Posted: 13 Jul 2008 09:30 PM CDT |
| I took the plunge for an iPhone 3G [StillSecure, After All These Years] Posted: 13 Jul 2008 08:56 PM CDT When the original iPhone came out I thought it was pretty cool, but at the end of the day it did not do for me what my Windows Mobile Smartphone did. Namely gave me 3G access speed and Exchange integration. Those two things alone were enough to keep me a Windows smarthphone user. As I wrote earlier July 4th my phone got wet in my backpack and though I have blown dried it often since than, it has just never come back. I can make a call now and than and use, but you never know when it is going to whig out and I have to reboot (actually it was like that before it got wet, but it is much worse now). So having had this phone over a year, it really was time for a new phone. I was not totally sold on the iPhone and it was not my only choice. I wanted no part of the lines and crowds, so I waited until Saturday to go to the ATT store and see what my options were. Frankly, I didn't have many options. The upgrade for my current phone is the HTC Tilt. Nice phone and I would consider it, but not at the $450 dollars that they wanted to charge me. After that, there was the Blackjack, not interesting. A few others and than Blackberries. I need the Exchange integration. So when it came down to it, you could not beat the $199 price for the iPhone. The 2 year contract didn't scare me, as I am at ATT wireless user for about 10 years already. The only bad part is that they did not have any in stock and I had to order mine. It should come within 5 to 7 days, but all set up for me to just plug in to iTunes and away I go! So a few more days of this water logged brick and than on to joining the "mod squad". |
| Presumed Hostile - Your Application is Out to Get You [Last In - First Out] Posted: 13 Jul 2008 08:08 PM CDT
OR:
Or maybe:
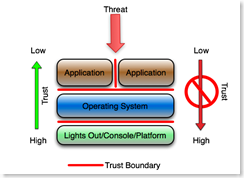
The Intent:The intent of this post is not to break new ground, but rather to describe a concept in a simple framework that can be committed to memory and become part of the 'assumed knowledge' of an organization. The Rules:#1 - In general, the closer a system or component is to the outside world or the more exposed the system is to the outside world (the user, the Internet or the parking lot) the less trusted it is assumed to be. #2 - The closer a system or component is to the data (database), the higher the level of trust that must be assumed. #3 - Any traffic or data that flows from low trust to high trust is presumed hostile. Any data flowing in that direction is assumed tainted. Any systems that are of higher trust assume that the lower trust systems are hostile. (a red arrow). #4 - Traffic from high trust to low trust is presumed trusted. Any traffic flowing in that direction is presumed safe or trusted. (a green arrow). This one is arguable. #5 - In between components that are of different trust levels are trust boundaries. Trust boundaries presumably are enforced by some form of access control, firewall or similar device or process. The boundaries are also assumed to be 'default deny', so that the only data or traffic that crosses the boundary is defined by and required for the application. All other data or traffic is blocked. The boundaries are also assumed to have audit logs of some kind that indicate all cases were the boundary was crossed. (a red line). An example:Start with a simple example. Pretend that threat is at the top of the drawing, the applications are directly exposed to the threat, and the applications are hosted on an operating system that is hosted on a platform of some kind (hardware).
Applications co-located on the same operating system must implicitly distrust each other (the vertical red line). Presumably they run as different userids, they do not have write privileges in the same file space, and they assume that any data that passes between them is somehow tainted and scrub it accordingly. The operating system administrator assumes that the applications hosted on the operating system are hostile, and designs, configures, monitors and audits the operating system according. File system and process rights are configured to least bit minimized privileges, the userids used by the application are minimally privileged, and process accounting or similar logging is used to monitor attempts to break out of the garden. The operating system also enforces application isolation in cases where the operating system hosts more than one application. Chroot jails or Solaris sparse zones are examples of application isolation. This of course is the basic operating system hardening concept or process that has evolved over the past decade and a half. The platform (the hardware, the keyboard, the physical ports, the Lights Out console, serial console, system controller, etc.) assumes that the operating system that booted from the platform is hostile. The operating system, when assumed to be hostile, has to be prevented from access it's own console, its own lights out interfaces, or the interface that allows firmware, BIOS or boot parameters to be modified. This presumes that access to the console automatically invalidates any security on the operating system or any layer above the OS. This also encompasses physical security. The underlying assumption is that if the platform is compromised, everything above the platform is automatically presumed to be compromised, and if the operating system is compromised, the applications are automatically presumed to be compromised.
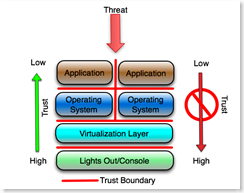
With Virtualization:Adding virtualization doesn't change any of the concepts. It simply adds a layer that must be configured to protect itself against the presumed hostile virtual machines that it hosts (and of course the hostile applications on those virtual hosts).
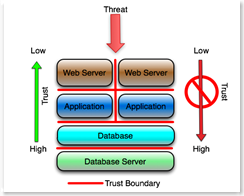
This has implications on how VM's get secured and managed. The operating system that is hosted by the virtualization layer should not, under any circumstances, have access to its own virtualization layer, or any management or other interface on that layer. Of course there are lots of articles, papers and blogs on how to make that happen, or on whether that can happen at all. As in the first example, the platform must assume that the virtualization layer is hostile and must be configured to protect itself from that layer and all layers above it, and of course if the platform is compromised, everything above the platform is automatically presumed to be compromised. For the Application Folks:The third example conceptualizes the application layer only, specifically for those who work exclusively at the application layer. The red lines again are trust boundaries, and presumably are enforced by some form of access control, firewall or similar device or process. The concept is essentially the same as the prior examples.
The application server administrator assumes that the web server is hostile and designs, configures and monitors the app server according. The application server administrator and the administrator of the application running on the server implicitly distrust the web server. The presumption is that any traffic from the web server has been tainted. The DBA assumes that the application running on the app servers is hostile and designs, configures, monitors and audits the database accordingly. This means that among other things, the accounts provisioned in the database for the application are minimally privileged (least bit, not database owner or DBA) and carefully monitored by the DBA, and that 'features' like the ability to execute operating system shells and access critical database information are severely restricted. This is fundamental to deterring SQL injection and similar application layer attacks. The database server administrator assumes that the database instance is hostile, and designs, configures and monitors the server operating system accordingly. For example the database userids do not have significant privileges on the server operating system, the file systems are configured with minimal privileges (least bit, not '777' or 'Full Control'), and the ability to shell out of the database to the operating system is restricted. The server administrator assumes that neither the application, the application servers or the database are trusted and protects the server against those assumptions. (A simple example - the database server administrator does not permit interactive logins, remote shells or RPC from the assumed hostile application or web servers.) Conclusion:The concept is really simple. Keep it in mind when you are at the whiteboard. I can't be the only blogger in the universe who isn't mentioning the iPhone this weekend, so here goes. Apparently from what I read, accessing the platform (the hardware/firmware/console) pretty much invalidates all of the iPhone security at the operating system and application layer. That lines up pretty well with the concepts in this article. |
| Liquor is quicker but… [The Dark Visitor] Posted: 13 Jul 2008 08:01 PM CDT |
| Chinese hacker Withered Rose returns [The Dark Visitor] Posted: 13 Jul 2008 07:41 PM CDT
UPDATE: Dominic reminds me that some people might not be as Chinese hacker obsessed as myself and suggests I give some links as to why Withered Rose is important. Whoops on my part! For some background on rose, read here and here. As mentioned yesterday and updated today, Withered Rose (Tan Dailin) is back to his old haunts; both mghacker.com and ncph.net websites are up and running again. Just a couple of observations: 1) Rose has done some scrubbing of his personal blog mghacker.com. Had to go to the wayback machine to make sure but you can tell a number of posts have been deleted for some reason by comparing the wayback machine to what is listed on the current blog’s archive. Rose has wiped out everything prior to March of 2007 and selectively edited the months still showing. 2) Not sure why but at least four of the new post on ncph.net are old posts from the mghacker.com blog: a. Mghacker 再现社会工程学 (29 Mar 2007) b. Mghacker 3389密码的嗅探 (29 Mar 2007) Ncph 3389密码的嗅探 (11 May 2008) c. Mghacker Rainbow Table 分析 (10 Apr 2007) Ncph Rainbow Table 分析 (11 May 2008) d. Mghacker 获取cuteftp中的ssh密码 (16 May 2007) Ncph 获取cuteftp中的ssh密码 (11 May 2008) 3) Whois data shows that NCPH.net administrative contact as: Administrative Contact: Sichuan Ligong Xueyuan is the Sichuan University of Science and Engineering. Rose founded NCPH while a student at the university. A Chinese hacker going by the name of Rodag, who was also a member of NCPH lists the university as a contact on his blog. The contact number 86.13154663992, was noted by Jumper in an IRC log:
My guess is the at the two of them are old college buddies. 4) What does this random sampling of information mean? Not much. Just wanted people to be aware that Mr. Rose is back in business and on the internet. |
| ADMP: A Policy Driven Example [securosis.com] Posted: 13 Jul 2008 07:00 PM CDT A friend of mine and I were working on a project recently to feed the results of a vulnerability assessment or discovery scans into a behavioral monitoring tool. He was working on a series of policies that would scan database tables for specific metadata signatures and content signatures that had a high probability of being personally identifiable information. The goal was to scan databases for content types, and send back a list of objects that looked important or had a high probability of being sensitive information. I was working on a generalized policy format for the assessment. My goal was not only to include the text and report information on what the policy had found and possible remediation steps, but more importantly, a set of instructions that could be sent out as a result of the policy scan. Not for a workflow system, but rather instruction on how another security application should react if a policy scan found sensitive data. As an example, let’s say we wrote a query to scan databases for social security numbers. If we ran the policy and found a 9 digit field, verifying the contents were all numbers, or an 11 character field with numbers and dashes, we would characterize that as a high probability that we had discovered a social security number. And when you have a few sizable SAP installations around, with some 40K tables, casual checking does not cut it. As I have found a tendency for QA people to push production data into test servers, this has been a handy tool for basic security and detection of rogue data and database installations. The part I was working on was the reactive portion. Rather than just generating the report/trouble ticket for someone in IT or Security to review the database column to determine if it was in fact sensitive information, I would automatically instruct the DAM tools to instantiate a policy that records all activity against that column. Obviously issues about previously scanned and accepted tables, “white lists”, and such needed to be worked out. Still, the prototype was basically working, and I wanted to begin addressing a long-standing critisicm of DAM- that knowing what to monitor can take quite a bit of research and development, or a lot of money in professional services. This is one of the reasons why I have a vision of ADMP being a top-down policy-driven aggregation of exsting security solutions. Where I am driving with this is that I should be able to manage a number of security applications through policies. Say I write a PCI-DSS policy regarding the security of credit card numbers. That generic policy would have specific components that are enforced at different locations within the organization. The policy could propagate a subset of instructions down to the assessment tool to check for the security settings around credit card information and access control settings. It could simultaneously seed the discovery application so that it is checking for credit card numbers in unregistered locations. It could simultaneously instruct DAM applications to automatically track the use of these database fields. I instruct the WAF to block anything that references triggering objects directly. And so on. The enforcement of the rules is performed by the application best suited for it, and at the location that is most suitable for responding. I have hinted at this in the past, but never really discussed fully what I meant. The policy becomes the link. Use the business policy to wrap specific actions in a specific set of actionable rules for disparate applications. The policy represents the business driver, and it is mapped down to specific applications or components to enforce individual rules that constitute the policy. A simple policy management interface can now control and maintain corporate standards, and individual stakeholders can have a say in the implementation and realization of those policies “behind the scenes”, if you will. Add or subtract security widgets as you wish, and add a rule onto the policy to direct said widgets how to behave. My examples are solely around the interaction between the assessment/discovery phase, and the database activity monitoring software. However, much more is possible if you link WAF, web app assessment, DLP, DAM, and other products into the fold. Clearly there are a lot of people thinking along these lines, if not exactly this scenario, and many are reaching to the database to help secure it. We are seeing SIM/SEM products do more with databases, albeit usually with logs. The database vendors are moving into the security space as well and are beginning to leverage content inspection and multi-application support. We are seeing the DLP vendors do more with databases, as evidenced by the recent Symantec press release, which I think is a very cool addition to their functionality. The DLP providers tend to be truly content aware. We are even seeing the UTM vendors reach for the database, but the jury is still out on how well this will be leveraged. I don’t think it is a stretch to say we will be seeing more and more of these services linked together. Who adopts a policy driven model will be interesting to see, but I have heard of a couple firms that approach the problem this way. You can probably tell I like the policy angle as the glue for security applications. It does not require too much change to any given product. Mostly an API and some form of trust validation for the cooperating applications. I started to research the policy formats like OVAL, AVDL, and others to see if I could leverage them as a communication medium. There has been a lot of work done in this area by the assessment vendors, but while they were based on XML and probably inherently extensible, I did not see anything I was confident in, and was thinking I would have to define a different template to take advatage of this model. Food for thought, anyway. -Adrian |
| “Transparent end-to-end encryption for the Internets” is not the solution [Robert Penz Blog] Posted: 13 Jul 2008 04:28 PM CDT Last week the guys behind the popular torrent site The Pirate Bay went public with their project of an opportunistic encryption of all traffic from an computer. The project is called "Transparent end-to-end encryption for the Internets" (IPETEE) but it is not the first time something like this is tried. Due to the pressure by the media industry it has more success chances than the last tries but I think we should target something else. So what should be our target? To build an overlay network with allows anonymous, encrypted and censor resident communication for unchanged IP based protocols over the internet. From the user perspective the software creates a virtual network adapter like OpenVPN does and every traffic that goes into that device is send via this overlay network. The overlay network does not send the traffic to the other peer directly (in this case the communication would not be anonymous) but via other peers taking part in that network. The more security you need to more peers it takes, but it will also get slower. This enables the usage of the network by different user groups. This would be a real solution and not a half one like the idea from The Pirate Bay guys. Ah, before I forget it, following are non-goals.
What do you think about it? |
| AppleTV Security Updates Announced [Infosecurity.US] Posted: 13 Jul 2008 01:55 PM CDT
|
| Zombies winning? I disagree. [Commtouch Café] Posted: 13 Jul 2008 11:10 AM CDT |
| Withered Rose, NCPH.net active again? [The Dark Visitor] Posted: 12 Jul 2008 10:58 PM CDT UPDATE 13 JULY 08: Still doing some research but at this point it is kind of a moot question… CHINESE HACKER WITHERED ROSE HAS RETURNED! Why I don’t do things the simple way is one of those questions that may never be answered. Did you checked his blog site? Yep, Withered Rose reopened it on 2 July 08. The only explanation given for the long absence was that he was busy but his new job allows him time to blog. More later. Jumper and I are in the process of looking through the posts at NCPH.net (it became active again on 14 April 08), a site previously run by Withered Rose, to determine if it is indeed the same organization. The site went down after it received a bit of notoriety from a Time’s article titled Enemies at The Firewall. There are at least two articles that detail hacks of Taiwanese websites but it is uncertain if it is still run by Rose. Hopefully, more to follow. |
| Apple iPhone 2.0: Multiple Security Updates [Infosecurity.US] Posted: 12 Jul 2008 08:00 PM CDT
|
| MustRead: Aviv Raff - Apple Commentary [Infosecurity.US] Posted: 12 Jul 2008 07:49 PM CDT
|
| Kpartx: a tool for mounting partitions within an image file [Robert Penz Blog] Posted: 12 Jul 2008 01:32 PM CDT Kpartx can be used to set up device mappings for the partitions of any partitioned block device. It is part of the Linux multipath-tools. With There are packages for Debian and Ubuntu. |
| Information Security Poll on the DNS Patch [Andy, ITGuy] Posted: 12 Jul 2008 07:07 AM CDT I haven't done a poll in a while and decided that the DNS issue was a good time to bring back the poll. I have a simple question "Have You Patched Your DNS Server?" The reason that I'm asking is because I want to know just how quickly everyone has reacted and whether or not some of you think that it's not a big deal. Also, if you have internal DNS servers that don't get updates from the internet I'm curious as to whether you still patched due to potential insider threat issues. |
| EU Member States Data Retention Transposition Measures [Robert Penz Blog] Posted: 12 Jul 2008 04:51 AM CDT I got my hand on this list which is out of a PDF from the European commission, and I though it maybe also interests others. It shows the status of data retentions laws in the EU member states. So here is the list. (The list is sorted by the native names of the nations and not the English ones I used here, e.g. Deutschland vs Germany)  . |
| Another Patch Cycle [Last In - First Out] Posted: 11 Jul 2008 09:50 PM CDT Here we go again. Review vendor patch release information cryptic enough to be only slightly useful. Check blogs & forums, see what others think as if they know more than you do. Connect with dozens of vendors tech support staff & web portals to review supported & unsupported patches in the unlikely event that they'll actually support a system fully patched to the current patch cycle . Wait for vendors to approve patches, or go ahead and patch without application vendor approval. Wait forever or listen to vendor tech support lecture you on how you've voided your support agreement by securing their product. Decide how to handle 'appliances', those things that vendors claim are hands off, fully hardened and don't need security patches, but in reality are dammed near full copies of COTS operating systems with minimal hardening and no patch strategy whatsoever. As if the tape library vendor will ever admit that the things 'firmware' is ordinary Linux/OpenSSH & needs routine patching. Test & QA all patches, with full regression testing as if you actually have the ability to regression test anything. Or roll the patch kit out to a few test/dev servers that nobody uses anyway. Schedule outages for non-redundant apps, or anything that is supposedly redundant but still doesn't support rolling patches, which is pretty much all of your redundant, clustered HA systems. Or go ahead and run the HA pair or cluster out of sync, and risk god knows what, because god (the vendor) never tested and will not talk about rolling upgrades. Or, worst of all, get stuck having to apply an Oracle CPU, the patch kit from hell. The one that from what I can tell introduces at least as many new bugs as it fixes, and seemingly breaks some existing functionality every patch cycle. But that's OK, nobody applies CPU's anyway. |
| links for 2008-07-12 [Raffy's Computer Security Blog] Posted: 11 Jul 2008 09:32 PM CDT |
| I have an iPhone, the MotoQ is dead [Network Security Blog] Posted: 11 Jul 2008 07:18 PM CDT I’ve never liked my MotoQ, other than maybe a couple of hours when I first got it. The battery life has always sucked and I was never happy with the form factor. I hoarded all the money family sent me for my recent birthday, waited about 1.25 hours between line and activation, now I’m home with my very own 8 gig iPhone. I just started syncing it up with my iTunes, played with the GPS a little on the way home and plan to get it hooked into my home wireless system as soon as possible. Happy Birthday me. Even if the iPhone hadn’t come out, the MotoQ had to go. After 16 months, the extended battery took a dump. I hope the iPhone batteries last more than 16 months, I know my iPod has so far. |
| NIST releases three new security guidelines [Security Karma] Posted: 11 Jul 2008 04:52 PM CDT  Government Computer News (GCN) reported that the National Institute of Standards and Technology (NIST) recently released three draft guides for public comment before their official publication. From the article: Government Computer News (GCN) reported that the National Institute of Standards and Technology (NIST) recently released three draft guides for public comment before their official publication. From the article:SP 800-107, titled "Recommendation for Applications Using Approved Hash Algorithms," is in its second draft release. It provides guidelines for achieving the appropriate level of security when using approved hash functions. Draft SP 800-121, titled "Guide to Bluetooth Security," describes the security capabilities of Bluetooth technologies and gives recommendations on securing them effectively. Draft SP 800-41 Revision 1, titled "Guidelines on Firewalls and Firewall Policy," updates the original publication released in 2002. It provides recommendations on developing firewall policies and selecting, configuring, testing, deploying and managing firewalls. The publication covers a number of firewall technologies, including packet filtering, stateful inspection, application-proxy gateways, host-based and personal firewalls.I have begun reading and intend on commenting on the Firewall draft. From my first peek inside it seems very thorough and covers not only firewall policies and requirements but also architecture, rule selection, and life-cycle management. |
| Posted: 11 Jul 2008 02:26 PM CDT Blah blah, slight lack of posts here, etc etc. However, I come bearing gifts of weirdness. So that's cool, right? First up, scumbags install a legit screensaver and use it to hide a malware install. Sneaky. Second - as the title says, Homer gets his very own Turkish Botnet. Anyone with Chunkylover53 on their AIM buddylist will have noticed a steady stream of infection links being pushed via "Away" status messages the last couple of days. The links claim to be for "new, web only episodes of the Simpsons". In reality, you'll get a Rootkit, some malware related to Chinese hijacks and be plonked into a Botnet. What significance does "Chunkylover53" hold for Simpsons fans, you ask? Well, "Chunkylover53@aol.com" was revealed to be Homers email address in an old episode. A lot of people ran off and added "Chunkylover53" to their AIM buddy list, and now here's Homer, poppin dem' hijack links. What's interesting is that the Username doesn't necessarily have any relation to the email address (in fact, add the EMail address and you don't see ANY infection links - you only see them if you add the Username minus the "@aol.com" part). However, people added the Username, and infection links are now the order of the day. Doh. |
| Should bloggers be held to ethical standards? [The Security Catalyst] Posted: 11 Jul 2008 02:02 PM CDT This is a question that has been kicked around quietly, and now it is the focus of the August Security Roundtable. We are recording on Tuesday (pondering using a live-feed) and I want your feedback. Show Prep Outline Blurring the lines: blogging, ethics and journalistic integrity The impact of social media on how ideas and information are shared, and the responsibility of those who create it. I’m driving at a few things: 1 - social media is here, and it has changed the game (ask the newspapers) 2 - used to be “if it is printed, it must be true;” seems to have migrated to “if it is on the internet, it must be true” 3- journalists have (supposedly) integrity and editors. What about bloggers? 4 - are sites with editors better? 5 - what are the lines, and does the “system” have a way of repressing the bad and sifting the good to the top? As the popularity and quality of a blogging/social media outlet improves, do the requirements change? Should superstars be role models? What about bloggers with a following? So whether you blog, podcast/netcast or read blogs - what do you expect from your bloggers? Got a comment? Idea? Question? Send it me michael [@ SHIFT-2] securitycatalyst [period] com. Call and leave me a message or join the conversation in the security catalyst community: Note: Joining the Catalyst Community Your participation is your currency (means no charge to join) - the more you contribute the more you learn and the more valuable the community becomes to everyone (so dive in and share). If you have not yet registered, please remember to use firstname.lastname as the standard. |
| Security Catalyst Community: Discussion Forum Activity (11 July 2008) [The Security Catalyst] Posted: 11 Jul 2008 12:52 PM CDT It’s been a brisk week in the forums, and here are some hot topics: Join the in the Discussion! Your participation is your currency (means no charge to join) - the more you contribute the more you learn and the more valuable the community becomes to everyone (so dive in and share). If you have not yet registered, please remember to use firstname.lastname as the standard. PS: I’ll be updating the blogroll this weekend. If you have a blog, podcast or write for a blog (for example, I welcome guest writers), drop me a note and I’ll add you to the list. |
| Hoff Waxes Poetic… [Infosecurity.US] Posted: 11 Jul 2008 12:41 PM CDT
|
| Oracle July 2008 Critical Patch Update Announced [Infosecurity.US] Posted: 11 Jul 2008 12:36 PM CDT |
| PCI DSS 2.2.1: Single Function Servers [Infosecurity.US] Posted: 11 Jul 2008 11:55 AM CDT
As usual, much of the PCI DSS is open for interpretation. Rather than the utilization of specificity, the PCI Council has permitted enough wiggle room to potentially allow for so much variation to make the standard ludicrous. |
| Friday News and Notes [Digital Bond] Posted: 11 Jul 2008 08:45 AM CDT
|
| You are subscribed to email updates from Black Hat Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Black Hat Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |
 Symantec
Symantec


 Apple Inc
Apple Inc
 SecurityFix
SecurityFix This weekend’s MustRead is a superb post by
This weekend’s MustRead is a superb post by 
 Just In: Oracle’s (NasdaqGS:
Just In: Oracle’s (NasdaqGS: 
No comments:
Post a Comment