Spliced feed for Security Bloggers Network |
| Security Briefing: July 29th [Liquidmatrix Security Digest] Posted: 29 Jul 2008 07:52 AM CDT  My jaw is sore from the dentist yesterday. Ugh. At least today is starting off on a good note (jaw notwithstanding). Click here to subscribe to Liquidmatrix Security Digest!. And now, the news…
Tags: News, Daily Links, Security Blog, Information Security, Security News |
| Ex-Manager at Siemens Is Convicted in Bribe Case [Liquidmatrix Security Digest] Posted: 29 Jul 2008 07:37 AM CDT From NY Times:
For the full article read on. |
| New Online Security Screening For Travel [Liquidmatrix Security Digest] Posted: 29 Jul 2008 07:33 AM CDT From Minneapolis Star Tribune:
So, why is it that I have an uneasy feeling about this program? Sure travelers would also have to provide all of their other info and fingerprints (mmm, Gummi) but, with this higher level of “automation” will this make it easier to breach the battlements? It appears that they’re moving ever closer to a screening process that removes the element of human intervention. Mind you I could be seeing this in a much darker light than is intended. Hmm. |
| NIST Revises Several Security Guidelines [Liquidmatrix Security Digest] Posted: 29 Jul 2008 07:22 AM CDT NIST has updated several of its guideline documents. From GCN:
For the full article read on. |
| Symantec takes a fling it on the wall approach to NAC [StillSecure, After All These Years] Posted: 29 Jul 2008 06:49 AM CDT I was reading Tim Greene's column this morning about Symantec's new on demand web log in for guests as part of their SNAC appliance offering. I have to admit that even I who follows the NAC market and competition pretty closely, get pretty confused with all of the different offerings Symantec has come out with around NAC. Symantec seems to be following a fling stuff on the wall and see what sticks strategy when it comes to NAC. The problem is separating the keepers from the rest of it when evaluating their offering. This latest offering appears to sure up a hole that was called out in the recent CRN review of their product in a bake off against Sophos and StillSecure's Safe Access. In that review Symantec's drop off in functionality between agent and agentless was called out. So within just a few days comes this announcement addressing the issue. Very timely indeed. This comes on the heels of Symantec's peer-to-peer approach to NAC, which came on the heels of their Endpoint Security product version 11 which had NAC included (and which I understand has already been patched/upgraded several times since its release). At this point you have Symantec NAC with their endpoint suite which is a throw in but has no guest access option on its own. Than you have the Symantec NAC appliance which can do enforcement of managed devices beyond what just endpoint suite gives you. Now you also have on demand/dissolvable agents available with the Symantec NAC server (but I guess not with the endpoint suite). You also have the Symantec peer-to-peer stuff, which I think also requires the SNAC server. Starting to get confusing? I guess this is what happens when your NAC offering is made up of an amalgamation of several different products lumped together. Not to worry though, I am sure Big Yellow will still sell plenty of all flavors of their NAC offering. At the end of the day some of this stuff is bound to stick. |
| Monday merger-mania in security [StillSecure, After All These Years] Posted: 28 Jul 2008 09:54 PM CDT Not sure if it is because of the slumping market and economy or in spite of it, but there pace of merger activity has been picking up lately and the security industry has not been immune to it. Today saw two meaningful deals announced that could have an impact on the security landscape: 1. Sophos buys Utimaco - Saw this one when I woke up today, as it is a European deal. UK based Sophos is buying German based Utimaco, makers of the SafeGuard line of data encryption/protection/DLP product line. Sophos is paying cash $340 million US for in this deal. This means they are substantially dipping into the credit market, as this is far more than they reported cash on hand. So like the Brocade/Foundry deal, the acquiring company feels strong enough about the acquisition to mortgage the house to get it. In this case, I think Sophos is making a smart deal. They clearly say that to compete with Symantec, McAfee and Microsoft they are going to need a full endpoint security suite. AV alone is not just going to cut it. This gives Sophos a real play in DLP and data storage space. Yes they could have just done a partner deal for this type of technology, but I applaud them for going out and buying the technology. I wondered if they would use this as a reverse merger entry to the public markets but it doesn't look like that. In any event it looks like Sophos is making the play and spending the bucks to be a player in the endpoint security suite game. 2. Motorola buys AirDefense - Well one of the air brothers finally found a taker. I always thought that for all of the press AirDefense, AirTight and AirMagnet receive, the revenue just didn't match the hype. Stand alone wireless security was a tweener. Would traditional security cover wireless or would traditional wireless cover wireless security. In any event a stand along wireless security play is a tough road. So with this answer Motorola says wireless handles wireless security. My question is what does the future hold for Motorola. They are reportedly getting out of the cell phone business. Is their wireless business, even a secure one enough to support this giant? I don't know but there is a bit of "dead man walking" over there if you ask me. I think the play is clear though that wireless providers are going to snap up wireless security companies. The real issue is at what prices. If anyone hears a price on this one, let me know. |
| Podcaster's Meetup @ DEFCON 16 Update 2 [Room362.com] Posted: 28 Jul 2008 03:54 PM CDT It’s almost that time. DefCon is right around the corner and things are coming together nicely. Here is where we stand and a rough schedule of events:
We’ll see you there! mubix |
| Posted: 28 Jul 2008 03:13 PM CDT Just read the eWeek summary for the new book Blown to Bits... (btw, what's up with tag lines and subheadings in books - these seem to be filling up the font page!). The authors discuss the right mix of people, process and security technology that organizations can use to prevent such breaches... Interestingly enough, the trends they talk about are very data-centric - "Secure the message as well as the medium" and "Address data at rest, in flight and in use"... In particular I like this paragraph... "Even with SSL (Secure Sockets Layer) and VPN, strong passwords, fire walls and a flood of security patches, the medium (the network and the attached servers) should be considered inherently insecure. The greatest security comes from protecting the data itself. Even a gargantuan data breach will be of no real consequence if the data is undecipherable." Could not have said it better - and I could not agree more... |
| Posted: 28 Jul 2008 11:59 AM CDT Click this, then read this, then wonder wtf the news station is actually going on about. I'm all for safe gaming for kids, but I'm pretty sure someone was having a slow news day over at Local 6 when they threw that thing together. Maybe they used the David Bowie method and pulled out segments of "think of the children" type articles and random and stitched them together. Journalist: Okay, we got paedophiles, a web cam, ooh ooh! We'll randomly name Grand Theft Auto and Halo 3 for no real reason whatsoever, then mention some vague stuff about giving people "gamer points" with no indication of how that actually works in practice. Sales gold! Editor: I am so horny right now. |
| Data breaches: Technology, process or management? [Data-Centric Protection and Management] Posted: 28 Jul 2008 11:32 AM CDT Being part of a technology company, one tends to think of solutions to data breaches as mainly to be solved by technology. Well, with a bit of process thrown in for good measure as well! Did not think much about the important role of management till now... Just came across an interesting opinion by Jonathan Armstrong, a partner at Eversheds, a law firm. He contends that current best practices of management do not train executives how to respond to crisis - he talks about various types and data breaches is one amongst them. I tend to agree to a point. However, I also think that it is the type of management and their core values that dictate how such a crisis be addressed. Is management concerned about the customer? Or is management just looking to save face? I can remember the Tylenol crisis and how well J&J handled it. While I agree with Jonathan that the frequency of incidents have gone up and management needs to be trained better, I also believe if executives have the best interests of their constituents in mind, things will work out okay... |
| Steve Jobs the "arrogant [expletive]" [Donkey On A Waffle] Posted: 28 Jul 2008 08:57 AM CDT A friend just passed me a link to this wonderful article about the public disclosure of the health of executive officers of a company. Right now there are no laws/rules in place with the United States government or SEC that requires senior management and other high ranking officials to disclose serious illness to stock holders. Part of me agrees completely with this in that the health of an individual is a private matter and should not have to be disclosed to the public. The inventor part of me says screw that! The particular CEO in the article is none other than Apple Computers CEO, Steve Jobs. In the past, Steve has been diagnosed with a tumor on his pancreas that was "cured" with surgery. He has recently been seen in public looking very haggard and slim. When called on his health, Apple's only public response was: "Steve loves Apple, Steve's health is a private matter." So this begs the question, should a publicly traded company be required to disclose serious health issues about it's senior management team? In most cases it wouldn't matter all that much, but in this case the implications are HUGE. Without Jobs, Apple is far less of a company. His track record of innovation and marketing excellence are what keeps the Apple stock price at a staggering out of control high. If he were to fall seriously ill, Apple stock would (and rightfully should) plummet. So should companies be required to report on the health of their senior management team? They all have to get physicals for insurance, so why not make them disclose their results to the world? Thoughts? Oh, and one other thing, there really are some awesome quote magnets out there, and much like Linus Torvalds, Steve Jobs doesn't disappoint: "This is Steve Jobs. You think I'm an arrogant [expletive] who thinks he's above the law, and I think you're a slime bucket who gets most of his facts wrong." (Quoted from NY Times article located here) |
| Security Briefing: July 28th [Liquidmatrix Security Digest] Posted: 28 Jul 2008 06:53 AM CDT  I hope this week is an upturn for me. Last week was less than pleasant. Click here to subscribe to Liquidmatrix Security Digest!. And now, the news…
Tags: News, Daily Links, Security Blog, Information Security, Security News |
| Keynote Sessions Moving Forward for RSA Conference Europe [RSA Conference - Blog] Posted: 28 Jul 2008 06:20 AM CDT |
| Louisiana Rejects REAL ID [Liquidmatrix Security Digest] Posted: 28 Jul 2008 06:18 AM CDT The states have been backing away from the REAL ID act as they get their heads around it. Louisiana is the latest to do so. From KATC TV:
OK, who’s next? |
| Great "New" VMware Resource - VI:Ops Virtual Infrastructure Operations [Rational Survivability] Posted: 28 Jul 2008 12:26 AM CDT  I wanted to make you aware of a "new" excellent budding resource for VMware infrastructure, VMware's VI:Ops - Virtual Infrastructure Operations. Steve Chambers of VMware pointed me over to the site which is growing in both content and contributors. VI:Ops currently includes the following sections:
Check out the site and join the community! /Hoff |
| The Last HOPE Not So Final? [Liquidmatrix Security Digest] Posted: 27 Jul 2008 08:40 PM CDT Well, as I was working through my email this evening I found a thank you note from Richard Cheshire and he made an interesting comment in the closing paragraph. From the email:
Hmmm, so I guess you can’t write off HOPE just yet. I just hope they can have it at a cooler time of year. It was freakin hot. Hats off to everyone who made it possible. |
| Chinese hackers steal 9 million items of personal information from South Koreans [The Dark Visitor] Posted: 27 Jul 2008 04:12 PM CDT Coming from the Korean Herald:
More on the BILLIONS of Won lost here. Update from Jumper:Here is a screenshot of the HDSI tool: |
| Chinese cyber nationalism revisited [The Dark Visitor] Posted: 27 Jul 2008 10:13 AM CDT First a question: Is there a difference between nationalism and cyber nationalism? The mixture of youth and patriotism has been a defining characteristic of the Red Hacker Alliance and was essential to the group’s formation. What has been running through my head, is trying to sort out the differences between ordinary nationalism and cyber nationalism, if there is indeed a difference. An article from The New Yorker touched on this question during an interview with Tang Jie, the producer of “2008 China Stand Up,” a nationalist short clip that went viral. Tang made the video in response to the negative press China received in their handling of the demonstrations that occurred in Tibet. Watching the video, you will see that it was heavily influenced by anti.cnn.com. The New Yorker article is well worth reading if this subject holds any interest for you. Through the interview, you get the sense that there is a psychological distinction between online cyber nationalism and real life. Perhaps it is just the difference in intensity levels that appear more vocal online but I think there is more to it than that. Fortunately, the article also mentions a book written by Xu Wu titled, Chinese Cyber Nationalism, that I ordered today. So, I’ll get back with you on that after I have a chance to read the book. UPDATED: Jumper has read the book and left his review in the comments section but I thought they would be better out here. Let’s just say, he does not give a glowing report on the book:
Too many facts ruin a good argument, so before we receive information from a guy who might know what he is talking about… What is the difference between nationalism and cyber nationalism? |
| Buzul, I know Chinese hackers and you sir, are no Chinese hacker [The Dark Visitor] Posted: 27 Jul 2008 08:31 AM CDT According to BiaNews.com, Panasonic.cn was hacked by Buzul. Sorry, that was all the details available in the article. Can someone tell me if the name Buzul is Turkish? |
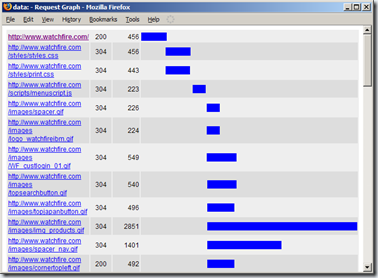
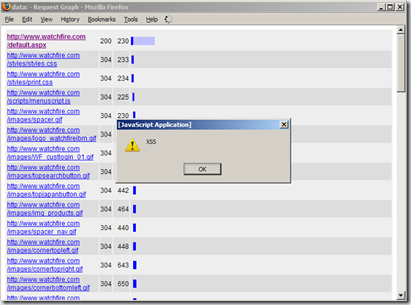
| Tamper Data Cross-Site Scripting [Watchfire Application Security Insider] Posted: 27 Jul 2008 03:00 AM CDT I recently came across an XSS vulnerability in the Tamper Data plug-in for Firefox.
Tamper Data is capable of generating HTML based graphs of request timings. The graph view includes a variety of information about the requests, such as HTTP status, timing, and URL. Vulnerability: The displayed URLs are not sanitized before being printed to the output stream, this allows malicious users to inject HTML into the Graph View's DOM. An attacker can trigger this vulnerability by various methods. One method might be to convince a naive user to visit a specially crafted URL that contains a malicious script, while Tamper Data is activated. Another method might be to convince the victim to surf into a site which the attacker controls. The attacker can then make the site cause the victim's browser to initiate a request to a URL which contains HTML of the attacker's choice. If the victim runs the "Graph All" feature after the malicious URL has been captured by Tamper Data, the attacker's HTML will be rendered in the context of the Graph view's DOM, enabling the attacker to run malicious scripts, as shown below:
Impact: 1) Information Leakage: This vulnerability can be exploited to access data displayed on the victim's Graph View page. 2) Phishing: This vulnerability can be exploited to display false information on the victim's Graph View page.
Test Environment: Firefox 3.0, Tamper Data 10.0.4
Fix Recommendation: A new version (10.1.0) of Tamper Data has been released in order to address this issue.
Acknowledgements: I would like to thank Tamper Data's author, Adam Judson, for his quick response and the efficient way in which he handled this security issue. |
| Weekend Catchup: SCC Discussion Forum Update (July 26 2008)HeThedi [The Security Catalyst] Posted: 26 Jul 2008 08:55 AM CDT The discussions continue to expand and inform in the Security Catalyst Community. Here are some of the recent hot conversations (including some I have listed before; this week they really exploded).
With Blackhat/Defcon approaching, here are two discussions related to that:
Want to participate in the next Security Round Table? We are recording the August SRT on Monday night using TalkShoe so you can listen in!
Join the in the Discussion! The Security Catalyst Community Your participation is your currency (means no charge to join) - the more you contribute the more you learn and the more valuable the community becomes to everyone (so dive in and share). If you have not yet registered, please remember to use firstname.lastname as the standard. |
| Podcast Number One [The Dark Visitor] Posted: 25 Jul 2008 10:08 PM CDT Dear TDV Readers, Heike and I invite you to listen to our first podcast. The podcast covers some blog background and the history of Heike’s “The Dark Visitor” project. It is 49 minutes long. The show notes are here. Please enjoy and send comments to podcast [at] thedarkvisitor [dot][com]. With Warm Regards, Jumper This posting includes an audio/video/photo media file: Download Now |
| Posted: 25 Jul 2008 09:07 PM CDT Well, try to do someone a favor and see how it backfires on you! Sure, a little sticky malware gets attached but is that your fault? Yeah, it really is: Give a man a phish and he eats for a day, teach a man to phish and he infects the whole bloody interwebs. More from Trend Micro on Chinese hacker virus cleaning tool |
| Going to Blackhat? join the “impromptu” onTour Tailgate [The Security Catalyst] Posted: 25 Jul 2008 11:51 AM CDT With more details to come soon, we launch the next Catalyst onTour Adventure on Tuesday. After a quick stop at Hershey Park, we’re heading through Ohio to pick up some books and then into KC for the weekend. We’ll arrive in Vegas on Monday. A few of us have been kicking around pulling together an informal, low-key, low-stress gathering while in BH. Since we’re bringing the RV (the whole point of the onTour approach), this is a good time to work out the “onTour Tailgate” series. Since my Tuesday event got cancelled, I am looking at hosting people at our location on Tuesday, 4-7p. This allows time for BH and the evening parties - but also a chance to unwind and meet new people, make some friends, unwind. Depending on when people come in, I’d be happy to consider Wednesday or Thursday, too. (note: if you cannot make it Tuesday but want to meet/speak - shoot me a note and we’ll connect). I know there are a lot of parties, events with booze and such. I see this as a chance to pull together, meet each other and have some time to kick back. There are no sponsors for the tailgate (though I wouldn’t refuse ‘em); instead, this is a self-supported event where everyone brings something and makes new friends. DetailsMore details/discussions here: http://www.securitycatalyst.org/forums/index.php?topic=900.0 Unless otherwise noted (or encouraged to go a different direction), plan for Tuesday 4pm. Here: http://www.oasislasvegasrvresort.com/
Companies Coming to VegasI am working on publishing a criteria list for pitches. I like learning about different solutions - but I want to make it easier to pitch me and explain the value. Look for something in the next 10 days. Meantime, if you’re going to be at BH and want to share your vision - shoot me a note and we’ll connect. I’ve already declared where I’m staying - and happy to meet anyone at the “rolling office.” |
| Security Briefing: July 25th [Liquidmatrix Security Digest] Posted: 25 Jul 2008 07:19 AM CDT  Good morning. The end of a strange week. I hope to be back to full stride next week with the postings. News is brief this morning but, I’ll update it later on today. In the meantime have a great weekend everyone! Click here to subscribe to Liquidmatrix Security Digest!. And now, the news…
Tags: News, Daily Links, Security Blog, Information Security, Security News |
| DNS Sploit Weaponization [Liquidmatrix Security Digest] Posted: 24 Jul 2008 08:24 PM CDT  So, unless you’ve been hiding under a rock for the last little while you’ll know that Dan Kaminsky broke DNS in a rather big way. And you’d know that the gory details hit the tubes of the internet a couple days ago. Hell, there was even a poem about the whole mess. (bless you Hoff) Now, the DNS ’sploit has been weaponized. HD Moore and company over at Metasploit have released it. For a full write up on it check out our friend, Nate McFeter’s, blog posting on the DNS exploit. Yes, it is being actively exploited. This storm has of course reignited the inevitable (and tiresome) disclosure debate. Let me save you the trouble and cut right to the chase… PATCH YOUR FSCKING DNS SERVERS. Consider yourselves warned…again. OK, I’m tired talking about this subject. What else is going on in the world? Tags: DNS Exploit, Exploit Code, DNS Hack, HD Moore, |)ruid, Dan Kaminsky |
| MindshaRE: Cross References in IDA [DVLabs: Blogs] Posted: 24 Jul 2008 04:29 PM CDT Posted by Cody Pierce I would say besides the navigation keys (Esc, Enter, Ctrl-Enter, Arrows), the most often sequence I use is X / Ctrl-X. That's right, cross references. Okay, maybe I use others just as much, but for today's MindshaRE we will be discussing cross references in IDA (I wanted to add some impact to the topic). I will briefly cover what they are, the different types of references, and share some scripts utilizing xrefs that hopefully make your day easier. MindshaRE is our weekly look at some simple reverse engineering tips and tricks. The goal is to keep things small and discuss every day aspects of reversing. You can view previous entries here by going through our blog history. Cross references in IDA are invaluable. They show any code, or data, which reference or are referenced from your current position within the binary. This can be in the form of function references, local variable cross references, or data xrefs. When navigating a binary one of the most common uses is function cross references. We need the ability to see what other pieces of code may hit the one we are interested in. This is exactly what xrefs are for. Lets say we want to see all functions that call the following routine: .text:76F2CA90 Dns_GetRandomXid proc near ; CODE XREF: Dns_BuildPacket+79 .text:76F2CA90 ; Dns_NegotiateTkeyWithServer+20C .text:76F2CA90 .text:76F2CA90 call Dns_RandGenerateWord .text:76F2CA95 jmp loc_76F23D8A .text:76F2CA95 Dns_GetRandomXid endpPressing Ctrl-X (JumpXref) when are cursor is on the functon name we get the following dialog listing the cross references.  Note that references are also visible as automatic comments under the function name. This is useful for enumerating xrefs at a glance. The number of references shown is configurable through the SHOW_XREFS variable in IDA.CFG. Looking at the dialog box we see four columns, Direction, Type, Address, Text. The first column denotes which direction in the binary the caller is located. Up being before the current function, at a lower address. Down being after the function, at a higher address. Type, indicates what type of cross reference we are looking at. In our example all our references are of type "p" meaning procedure, later we will see others also exists such as write, read, and offset. Address is the location of the cross reference. In this instance the address is the location of the call to our current function. In our example we have symbols so it is an offset from that symbol, but if we didn't have symbols it would be a typical hex address. Text, is the text that appears at our references address. For this example we see a typical call, others may show the instructions reading or writing to our cross reference. Having symbols helps us easily identify the purpose of a function. Cross references help us identify the path code takes to a function. As an example I created an IDA Python script called get_recursive_xrefs.py that takes matters one step further. This script will take a function, and recursively grab cross references to the function. This gives us a calling tree as far back as possible to the current function. Running the script produces the following sample output: Getting xrefs to 76f39c9f (Dns_RandGenerateWord) ======================================================================== Dns_RandGenerateWord Dns_GetRandomXid Dns_BuildPacket Query_SingleName Query_Main Query_InProcess DnsQuery_W privateNarrowToWideQuery DnsQuery_UTF8 DnsFindAuthoritativeZone DoQuickFAZ CompareTwoAdaptersForSameNameSpace DnsQuery_A ShimDnsQueryEx CombinedQueryEx DnsQueryExW QueryDirectEx Dns_FindAuthoritativeZoneLib Dns_PingAdapterServers DnsModifyRRSet_Ex DnsRegisterRRSet_Ex DnsModifyRRSet_Ex DnsRegisterRRSet_Ex Dns_UpdateLib Dns_UpdateLibEx DnsUpdate DoQuickUpdateEx DoMultiMasterUpdate DoQuickUpdate Dns_NegotiateTkeyWithServer Dns_DoSecureUpdate sub_76F3BB68 Dns_UpdateLib Dns_UpdateLibEx DnsUpdate DoQuickUpdateEx DoMultiMasterUpdateAs you can see we get a nice list of calling functions. In an instant I can find what might create transaction IDs in Windows. I mentioned earlier that functions are certainly not the only thing you can cross reference. When in a function we can also reference local or global variables in an operand (JumpOpXref). Lets look at the next cross section of assembly. .text:76F39CCC inc edi .text:76F39CCD push edi .text:76F39CCE push offset aMicrosoftStron ; "Microsoft Strong Crypto"... .text:76F39CD3 push ebx .text:76F39CD4 lea eax, [ebp+var_4] .text:76F39CD7 push eax .text:76F39CD8 call ds:_imp__CryptAcquireContextA .text:76F39CDE test eax, eax .text:76F39CE0 jnz short loc_76F39CE5Putting our cursor on the local name "var_4" at address 76F39CD4 and pressing "X" gives us a familiar dialog box.  We discussed all of the columns already, the only new information is the "w", and "r" types. I alluded to this earlier but it simply means the instruction either reads, or writes to the target variable. This can be extremely helpful in identifying when a variable is initialized. Lets move to a different section in the binary. Looking through the .data section of most binaries can be interesting. We obviously see lots of global addresses that are used to hold values. Knowing both the x-ref shortcuts (Ctrl-X, X) can get us the references to those locations. But lets look at another common occurrence in the data section. Vtables are accessed via the data section in most cases. The problem is the only xref from the data section will be at the beginning of the vtable. However if we do a xref on each function in the binary we can determine a function that is called from the data section. For instance the xrefs to the function MxWireRead look like this.  Following those show us an obvious table of handlers. .data:0104E300 RRWireReadTable ; DATA XREF: Wire_CreateRecordFromWire+43 .data:0104E300 dd offset CopyWireRead .data:0104E304 dd offset AWireRead .data:0104E308 dd offset PtrWireRead .data:0104E30C dd offset PtrWireRead .data:0104E310 dd offset PtrWireRead .data:0104E314 dd offset PtrWireRead .data:0104E318 dd offset SoaWireRead .data:0104E31C dd offset PtrWireRead .data:0104E320 dd offset PtrWireRead .data:0104E324 dd offset PtrWireRead .data:0104E328 dd offset CopyWireRead .data:0104E32C dd offset CopyWireRead .data:0104E330 dd offset PtrWireRead .data:0104E334 dd offset CopyWireRead .data:0104E338 dd offset MinfoWireRead .data:0104E33C dd offset MxWireRead... ...This is clearly a tedious process, perfect for automating with a script. So I wrote an IDA Python script called find_data_section_functions.py which runs through every functions xrefs that originate from the data section producing the following example output: 0x0104e164: AFileRead ... 0x0104e234: AWireWrite 0x0104e1d0: AaaaFileRead 0x0104e030: AaaaFlatRead 0x0104df60: AaaaValidate 0x0104e1e8: AtmaFileRead 0x0104e048: AtmaFlatRead 0x010135a8: ControlCallback ... 0x0104e0f4: KeyFlatWrite 0x01013acf: Log_PrintRoutine 0x01006f9c: MIDL_user_allocate 0x01006fa0: MIDL_user_free ... 0x0104edb4: MxFileWrite 0x0104edc0: MxFileWrite 0x0104edcc: MxFileWrite 0x0104dffc: MxFlatRead 0x0104e008: MxFlatRead 0x0104e014: MxFlatRead
0x01006ff0: R_DnssrvComplexOperation 0x01007004: R_DnssrvComplexOperation2 0x01006ff4: R_DnssrvEnumRecords 0x01007008: R_DnssrvEnumRecords2 0x01006fe8: R_DnssrvOperation 0x01006ffc: R_DnssrvOperation2 0x01006fec: R_DnssrvQuery 0x01007000: R_DnssrvQuery2 ... 0x01017044: freeDpInfo 0x01018b41: freeServerObject 0x0101736d: freeStringArray 0x0101aa4f: pluginAllocator 0x0101aa4a: pluginFree 0x0104ed00: processPrimaryLine 0x0101b67d: recurseConnectCallback 0x01041e90: respondToServiceControlMessage 0x0104eea4: startDnsServer 0x0104d20c: sub_1020330 0x0104d214: sub_1020330 0x0102f8c7: updateForwardConnectCallback 0x0103606d: zoneTransferSendThreadFinally, there are three additional graphs IDA provides the user for viewing cross references. These graphically display the same cross references we covered, and can even display a down graph showing all the functions your current function may call. These can be located in the Views->Graphs->Xrefs to/Xrefs from/User xrefs chart. While these may be handy they suffer two problems. First and foremost you can't navigate them. That means you can see an interesting function but have to switch back to IDA and manually type the address in to jump there. Secondly, it can be unwieldy often times showing thousands of functions. This can be limited using the User xrefs chart and limiting the recursion depth, but i would rather just run a script I can interact with. Play around with the graphs, you may find them very helpful. There are many many other uses for cross references. I can't possibly cover everything in this little post. I hope this has been a good intro to them, or maybe sparked some ideas of your own. Leave a comment if you have any novel uses, or other useful hints. I hope you enjoyed this weeks MindshaRE. -Cody |
| You are subscribed to email updates from Black Hat Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Black Hat Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |






No comments:
Post a Comment