Spliced feed for Security Bloggers Network |
| Pointing a Finger at ??? [ImperViews] Posted: 18 Jul 2008 08:24 AM CDT This weekend a heated debate fired up on the WebAppSec mailing list. Jeremiah Grossman happened to spark it with a merely innocent short question "Anyone want to make an open source WAF fingerprinter?"
Turning the question around as happens in these bonfire circles the basic question becomes whether it is necessary that a Web Application Firewall (WAF) actually hide its identity.
Actually, I don't even grant this a fruitful discussion. Most of the thread participants agree that the worst kind of security is security by obscurity. So having any kind of discussion regarding obscuring the fact that there is a WAF, and which kind of WAF is deployed, is just painfully useless. A security analogy which comes to mind is encryption. It would be as if an e-vendor hides the fact that they use AES-256 for encryption purposes rather than proudly displaying the usage of this standard. And even more to the point, it is possible to fingerprint any network device, granted that the device is active (and needless to say, an inactive WAF is not a WAF). Which actually means that when the response to a request, or a series of requests, is different than the expected response returning from the target server, then obviously there must be some sort of inline security device. And since devices by different vendors behave differently, then of course it is possible to differentiate between the different devices.
Andres Riancho actually dies the fire somewhat on this one when he provided the algorithms for the detection of the different WAFs.
I guess we'll just have to wait around the fire (-wall) until we get around to those real spooky stories.
- Amichai | ||||
| Lack of usable emails for your pentest got you down...metagoofil FTW! [Carnal0wnage Blog] Posted: 18 Jul 2008 06:07 AM CDT Hopefully a useful day in the life of a pentest post... So there I was, trying to gather emails for our pentest. The only problem is that we were doing an assessment of city.domain.com but all the emails are listed as @domain.com. Just for clarification, searching domain.com for email addresses wouldn't necessarily give me emails that were in scope, so I had to think of something. First step was some google-fu of "site:city.domain.com + @domain.com" that brought in a few emails addresses in. Next step was metagoofil. Metagoofil is awesome because it will download ms office, open office, and pdf documents from the domain you specify. It will parse the metadata and give you a list of the usernames in the documents and the path to where the document was saved. How it works (images from the Edge-Security site) 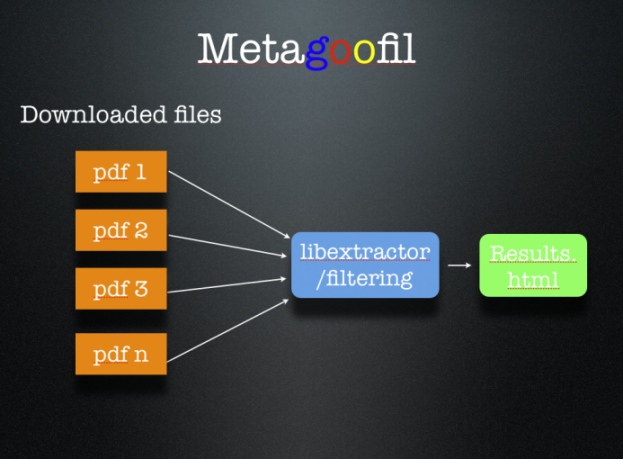 It downloads the documents to your local computer so you can view them for extra info gatherings. It also gives you a nice little html page with the results. 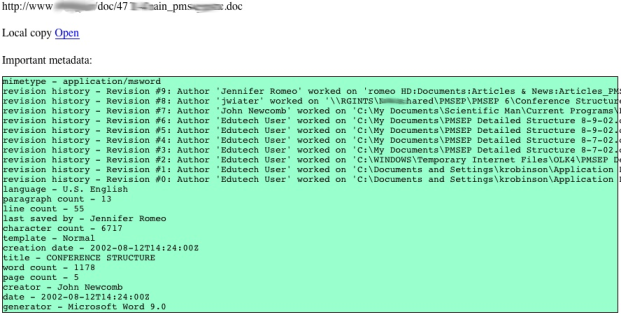 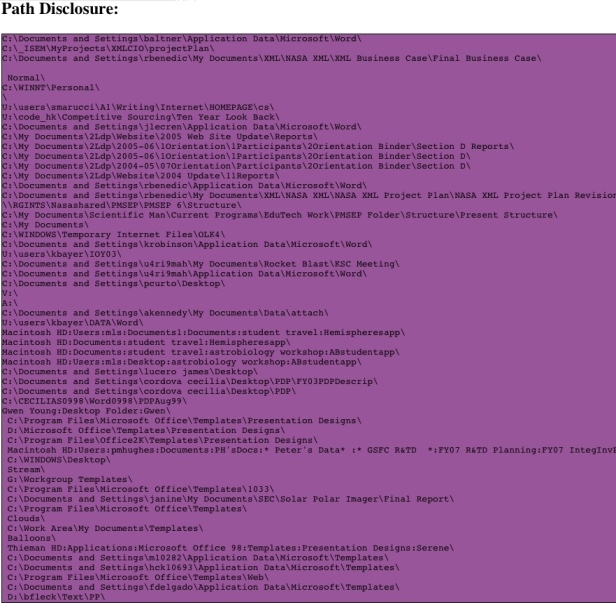 After that I took the possible usernames, put them in the proper naming convention for the domain, rocketed off my SE email and crossed my fingers. The result? Metagoofil for the win! Overall I had about 160 possible email addresses, 20 actually made it to someone's inbox...sad face but not bad considering how I got the possibles. 5 of the 20 opened it :-) 2 were forwarded (meaning the user that opened it was not initially emailed), 1 was from google, and 2 of the 5 were from metagoofil :-) Not bad if you ask me. | ||||
| Security Briefing: July 18th [Liquidmatrix Security Digest] Posted: 18 Jul 2008 05:27 AM CDT  Friday morning in NYC and we’re heading for The Last Hope. Click here to subscribe to Liquidmatrix Security Digest!. And now, the news…
Tags: News, Daily Links, Security Blog, Information Security, Security News | ||||
| Has Fortis bought an online not so secure bank (ABN-AMRO) [belsec] [Belgian Security Blognetwork] Posted: 18 Jul 2008 03:48 AM CDT | ||||
| Check Your DNS Resolver [/dev/random] [Belgian Security Blognetwork] Posted: 18 Jul 2008 02:31 AM CDT
Since the announce of the major DNS vulnerability (multi-vendors), it’s patching time for all admins around the world. Did you already perform your homework? The people at OARC have crafted a special DNS name and server that you can query to check whether or not your resolver is using random ports. A simple “dig +short porttest.dns-oarc.net TXT” should return a good, fair or poor rating, depending on your setup (Source: BELNET CERT Newsletter NEW2008-28). Here is an example: $ dig +short porttest.dns-oarc.net TXT z.y.x.w.v.u.t.s.r.q.p.o.n.m.l.k.j.i.h.g.f.e.d.c.b.a.pt.dns-oarc.net. "88.191.254.6 is GOOD: 26 queries in 3.9 seconds from 26 ports with std dev 19554.27" This one is not yet patched: $ dig +short porttest.dns-oarc.net TXT z.y.x.w.v.u.t.s.r.q.p.o.n.m.l.k.j.i.h.g.f.e.d.c.b.a.pt.dns-oarc.net. "212.35.96.66 is POOR: 35 queries in 4.3 seconds from 1 ports with std dev 0.00" | ||||
| Phishing attacks getting more advanced (or not) [remes-it] [Belgian Security Blognetwork] Posted: 18 Jul 2008 02:17 AM CDT Today I saw an e-mail passing by, announcing the launch of Mult Mail Group Service. Of course I subscribed as it promises to offer a powerful tool to network and share knowledge ... NOT. Damn, as we are looking to protect our e-mail users from advanced and nifty phishing attacks, simple messages slip through our nets. Once again a lesson that we can never let our guards down or 'forget' about previous attack methods. | ||||
| The Last HOPE Countdown - Hack Minus 1 [Liquidmatrix Security Digest] Posted: 17 Jul 2008 10:15 PM CDT As noted by El Jefe… We’re in NYC. And yes, I took the bus.  Hey - I couldn’t figure a way to make work pay for the trip - well legitimately anyways… and besides… it wasn’t too bad - I had an outlet and wifi - what else does a geek need! Note: The Greyhound NEON bus (Toronto/NYC Express Service) is highly recommended. Went and picked up my badgey goodness… Front:  Back:  There’s high rez images available if you ask nicely. Oh - and while walking around midtown, I came across this scene… and was terribly interested in yelling one word… anyone know what word that was?  /me feels bad for the cliche, but hey - it’s a classic. Should you be at HOPE, you can find me at 1300 on Friday in the Turing room. I'll be the guy at the front talking. To keep up on all that the LSD guys are up to at the event, please follow us on Twitter (as long as the fail whale stays down) at this lovely Tags: TheLastHOPE, Security Conferences, Hacker Conferences, NYC, Wheeeeeeeeeee, hacker badges, Greyhound NEON | ||||
| Liquidmatrix In NYC [Liquidmatrix Security Digest] Posted: 17 Jul 2008 09:49 PM CDT OK, sorry for the lack of postings today folks. We’ve been on the road. Myrcurial made his crossing into the US on bus and yours truly flew into Newark. Gotta love frequent flier miles. I’m beat but, I’m looking forward to the Last Hope tomorrow. Myrcurial already has his badge and will be posting shortly (if he hasn’t already) We will be live blogging where possible. Conversely you can follow us on twitter.com @gattaca and @myrcurial This should be interesting. | ||||
| Root password for BackTrack, DVL and other LiveCDs [Security4all] [Belgian Security Blognetwork] Posted: 17 Jul 2008 08:01 PM CDT | ||||
| Network World misses the reasons why more companies are deploying NAC [Napera Networks] Posted: 17 Jul 2008 02:41 PM CDT Network World suggested with its headline this morning that a recent Infonetics study outlined the top reasons for delaying network access control (NAC) deployments. I think that’s an overly negative headline. While the Infonetics report did discuss some of the blockers to NAC deployments, most of it was positive and covered the increased level of NAC deployments expected over the coming year, and indicated that NAC is becoming a budgetary line item for most companies. In fact, the report states that nearly two-thirds of the respondents have a budgetary line item for NAC in their fiscal 2009 budgets. That's double the number for 2008. I agree with the body of the Network World article that regulatory compliance demands, lower prices and improved NAC technologies, especially around reduced complexity, are key reasons enterprises will move forward on a network access control deployment. Current solutions are too heavily focused on the large enterprises and require large investments and infrastructure upgrades and are complex to use and manage. The whole reason Napera launched its solution for small and medium-sized enterprises was to provide a comprehensive solution focused on simplicity and cost effectiveness. This is a missing piece of the NAC market today and critical for our SME customer. The Napera N24 is the first shipping NAC product for the SME to utilize a Software as a Service approach that removes the need for local servers and leverages Microsoft's Network Access Protection architecture to minimize the need to deploy agents. The Network World article points out that respondents to the Infonetics study clearly see security as the number one driver. This is because most security and network IT staff are still experiencing security issues, in spite of the fact that they have multiple security products already deployed. This is a common theme we discuss with our customers. Even though companies are spending more than ever on anti-virus, anti-spyware, firewalls, and other security solutions, they still need to ensure that devices accessing their network are secure, up to date, compliant with policy and authorized before gaining access to the corporate network. This is the added layer of defense that NAC brings, tying together these disparate security solutions to control network access. Another driver is workforce mobility. The reason security solutions are not fully protecting the network from attack or virus outbreaks is because of the lack of control IT has over laptops. Workers now demand access everywhere and work from Starbucks or a hotel as frequently as on the corporate network. In addition, consultants, customers, and other guests are demand access to the Internet and printers while at your offices, making guest access another key driver for NAC. Finally, it's important to put the Infonetics user survey in context of another key report released at the same time about NAC: an updated market forecast that suggests the NAC market is alive and well and expected to reach $800 million by 2010. This Infonetics report came on the heels of an IDC report, featuring an aggressive forecast for the network access control market of $3.2 billion by 2011. While there do remain blockers to NAC deployments, companies are including NAC on their list of IT purchases, because the pain is great and current security and networking solutions are not solving their security and other challenges. With Microsoft's NAP agent on Windows on the road to becoming ubiquitous (with XP SP3 appearing on Windows Update last week), we are confident there will be a faster uptake of both NAP and product like Napera that integrate with the Microsoft architecture. | ||||
| some books about computer science [belsec] [Belgian Security Blognetwork] Posted: 17 Jul 2008 10:57 AM CDT
| ||||
| CISSP value [Security Balance] Posted: 17 Jul 2008 10:20 AM CDT Congrats for Andrew Hay on getting his CISSP. He does a great job when describing the value of this certification: “Due to the scope of the exam I forced myself to learn aspects of security that I had neither the reason, nor the desire, to understand. I feel that I have grown as a security professional because of my studies and hope that I can help others with the things that I have learned.” That’s exactly what I think about it. It won’t ensure that the certified person knows everything, but he(she) should have passed through a lot of different security subjects while studying for it. Personally it was an eye opener, I understood that Security is far wider than what I originally thought when I had to study to take the test. | ||||
| Carding sites come and go (reality check) [belsec] [Belgian Security Blognetwork] Posted: 17 Jul 2008 09:42 AM CDT so there was a site putting a sample of some thousands of mailadresses online, saying it was just a sample of a list of 5 million the site is gone now, suspended but it was full with information about how to start carding (playing stuff with cards and it ain't poker) http://thexeon.net/carding/showthread.php?t=5 5 miljoen emailaddressen Hello,I'm offering dumps with original track1 and track2 for sell EU dumps (Visa and Mastercard) EU Classic-150euro EU Gold/Platinum/Business - 250euro EU Infinite - 700euro I offer also dumps with pin in higher prices icq-416382863 http://fhq.forumer.com/services/80001-selling-different-stuff-carding.html it is an ongoing game of cat and mouse but there are too many mouses... :)
| ||||
| Groundwork and Wiki Integration [/dev/random] [Belgian Security Blognetwork] Posted: 17 Jul 2008 09:41 AM CDT
Next article regarding Groundwork, a very good monitoring and reporting environment. I already integrated WeatherMap with Groundwork (the community edition), or added a Security Dashboard. Now, let see how to integrate a Wiki into Groundwork. A Wiki is an online collaborative tool where everybody can update the pages content directly from a browser without specific HTML knowledge. A well-known example of Wiki is the free enclyclopedia Wikipedia.
Note: A Wiki will not replace professional tools but it can help you to build a change management procedure. 1. Wiki Installation The choice and installation of a Wiki won’t be covered here. Feel free to use your favorite Wiki application. Personally, I use WikkaWiki. This article assumes that the Wiki was installed on the same server as Groundwork. On a security point of view, it’s the best choice:
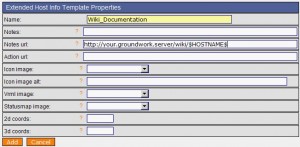
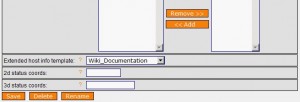
Finally, this article assumes that the Wiki is configured to provide URL pages as “http://your.groundwork.server/wiki/xxxxxxxx“. 2. Groundwork Configuration As Groundwork uses the Nagios engine, we will use the feature proposed by Nagios: the Extended Host/Service Information. It allows you to specify a custom logo or external URL to better describe your hosts or services. To configure this feature in Groundwork, go to Configuration , Hosts, Host Extented Info and create a new template:
Note the URL format: It accepts Nagios macro like $HOSTNAME$ or $HOSTADDRESS$! Then, for all your hosts (it’s better to fix it once in the default profile), select the created extended info template:
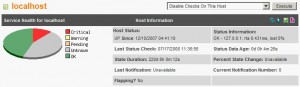
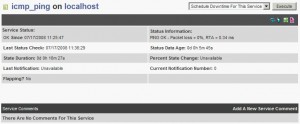
Then reload the Groundwork configuration (commit changes). But there is one major problem at thr momemt: the URL configured abose is only available on the old Nagios pages and not from the Status Viewer nor the dashboards! I contacted the Groundwork support to report this problem. They found this feature valuable but are not able to propose it right now (maybe in the next release?). Luckily Simon (working at Groundwork) provided me a way to achieve my request. Thanks Simon! 3. Groundwork Patching To display the Wiki URL in the Groundwork main pages, there are two files to be patched: /usr/local/groundwork/guava/packages/sv2/templates/host.xml /usr/local/groundwork/guava/packages/sv2/templates/service.xml Patches are available here: host.diff and service.diff. Copy them on your Groundwork server and apply them: # cd /usr/local/groundwork/guava/packages/sv2/templates # wget http://blog.rootshell.be/wp-content/uploads/2008/07/host.diff # wget http://blog.rootshell.be/wp-content/uploads/2008/07/service.diff # patch <host.diff host.xml # patch <service.diff service.html Warning! The patches are provided “as is” and are not supported by Groundwork nor myself. They worked for my Groundwork installation. Also, there are risks to have the patched files overwritten during any future upgrades! Log out Groundwork, clear your browser cache and log again. You should now see host and service names converted to URLs in the Status screen and Dashboard:
When a page does not already exist, the normal Wiki behavior is to create a new empty page. Now, the biggest challenge is for you: Fill the pages with all your hosts and services data and keep them updated! Feel free to exchange your experiences or suggestions. | ||||
| Just so you know it is not me [StillSecure, After All These Years] Posted: 17 Jul 2008 08:37 AM CDT I know many of you think I am like a pavlovian dog the way I respond to Richard Stiennon's anti-NAC vitirol. After my last article, I really decided to just lay off Richard. But just to show you that it is not me, I wanted to point out Richards recent attack on Grant Hartline, CTO of Mirage Networks. Grant blogs and put up an article regarding the latest exchange between Richard and I. Both Richard and I commented. Check out Richards expective laced reply that I think shows just how unhinged he has become on this subject. Richard rambles and stumbles taking shots at anyone he can. I am telling you, he is really losing it. In the meantime based on this, I am going to change my prediction on the great debate and say Joel Snyder in 2! | ||||
| Posted: 17 Jul 2008 08:14 AM CDT | ||||
| Goodie 5 OPML exchange (RSS feeds) [belsec] [Belgian Security Blognetwork] Posted: 17 Jul 2008 04:47 AM CDT As you will see in the coming months some feeds will be made more public in a kind of dashboard. THis blog is nevertheless built upon a collection of a 1500 other feeds that are still availabe at the bloglines collections. THose collections will not be updated anymore for the time being. I have now reorganised and updated and selected and am adding new RSS feeds (that are updating quite often and are not only an echo of other stuff) to my private collection. If you think that you have an interesting set of RSS feeds and you can send them me in a OPML file than I can make it maybe even better (french, dutch and english are welcome and the subjects are those that are used in the present bloglines collections). Your OPML won't be made public and the new integrated updated one neither. For the moment is bloglines stalling and there is no real advantage at continuing to put an effort in it. Netvibes has made a fantastic update and igoogle and yahoo pipes are really a pain in the ass to make yourself. I have never seen something that simple as netvibes.com | ||||
| Getting “electronically” naked at the Beijing Olympics [The Dark Visitor] Posted: 17 Jul 2008 04:38 AM CDT I swear people have to sit around and think of phrases like this…from the WSJ:
| ||||
| Posted: 17 Jul 2008 02:35 AM CDT
Interesting article about traffic filtering based on countries: http://www.securityfocus.com/infocus/1900/4. (It’s based on Microsoft ISA server but can be easily extended to other platforms) | ||||
| eBay Will Track Your IP Addresses [/dev/random] [Belgian Security Blognetwork] Posted: 17 Jul 2008 01:32 AM CDT
Like many of us, I’m an eBay user. Regularly, I buy or sell unused or deprecated stuffs. eBay (as Paypal, same group) should be one of the most targeted attacks (phising, fraud, …). Today, I received the following alert in my eBay mailbox:
Like Google did recently, eBay will start to track your favorite locations (read “hosts” or “IP addresses”) and assign them to your account. When eBay will detect a connection from an “unknown” location (from a friends’ PC, from a hotel or a hot-spot), you’ll have to authenticate again to prove your identity. That’s a great feature! | ||||
| Posted: 16 Jul 2008 08:45 PM CDT | ||||
| Posted: 16 Jul 2008 08:38 PM CDT | ||||
| goodie 4 Belsec TV [belsec] [Belgian Security Blognetwork] Posted: 16 Jul 2008 05:50 PM CDT The start of a collection of youtube vids and others to follow about hacking (real or forged), without all the crap around, so sit back and relax http://sites.google.com/site/belsectv/system/app/pages/sitemap/hierarchy | ||||
| Something Old and Something New [Matt Flynn's Identity Management Blog] Posted: 16 Jul 2008 02:14 PM CDT Eric Norlin provides some insight into what to do (related to identity management) in an economic slowdown: Something Old: "1. SSO and Password Reset: The facts are on the wall. If you can reduce the number of helpdesk calls for password reset, you're going to save a TON of money. You can do that through self-service modules, E-SSO, web sso, or even federation. Just do it." Something New: "2. Automating Compliance: This is a big one, and you probably won't get it done before the recession ends. However, the more you achieve automated compliance controls, the more big bucks you can save on manual audits. Throw everything from RBAC to de-provisioning into this bucket and then get started looking at what really will slice greenbacks soonest." Password Reset and SSO have long been good entry points into Identity Management and also proven creators of cost reduction and efficiency. Automated Compliance is a somewhat more recent phenomena that also yields cost reduction and efficiency. You may be wondering though how many companies are able to get to automated compliance without giving an arm and a leg to define requirements and processes that enable automated compliance. Might the initial effort might defeat the purpose of cost reduction? One thing Eric wrote is probably key to that discussion – "the more you achieve automated compliance controls..." which to me means, let's not get caught up in the grand notion of automated compliance. Implement a few key automated controls that eliminate significant manual effort in the compliance audit process. And that will bring you cost reduction. | ||||
| SaaS Eases Security Cost and Complexity [Matt Flynn's Identity Management Blog] Posted: 16 Jul 2008 12:57 PM CDT I first read an article in InformationWeek titled SaaS Makes A Run At Security and then found this very similar article by the same author online. I've posted recently about identity as a service (be sure to check the comments and links if you visit that posting). But my day job dictates that I think more about identity reporting as a service. (intelligence around who has what access and what changes are being made). One of the striking take-aways from the article is the Gartner estimate that by 2018, 85% of security intelligence will be offered as a service. I guess the words "offered as" seem to deflate the energy of the claim. I wonder what the estimates are for how much will be consumed as a service in 10 years. In any case, I think the writer hits on the right points - cost and complexity. Especially for the mid-market (his target audience). I think (particularly in the mid-market) the simplification of key capabilities will outweigh the emotional hurdles that make SaaS a tough sell for security. Of course, actual security capabilities may remain a harder sell than security capabilities. That is, companies may be more willing to have managed identity reporting than managed provisioning. I think mid-market security practitioners want their lives to be easier. They're not driven by the same concerns as large enterprises. What do you think? |
| You are subscribed to email updates from Black Hat Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Black Hat Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |




3 comments:
I always search such wonderful blog and after so many efforts finally I got you. Keep writing the same
Pharmacy home delivery in UAE
Pharmacy near Business Bay
Always look forward for such nice post & finally I got you. Really very impressive post & glad to read this.
Architects in Indore
Civil Contractors in Indore
Good luck & keep writing such awesome content.
Virgin Linseed Oil BP
flaxseed oil
cmsed
Post a Comment