Spliced feed for Security Bloggers Network |
| God took me off the grid [StillSecure, After All These Years] Posted: 05 Jul 2008 01:00 AM CDT I had every intention of blogging during the long holiday weekend. Catching up on email and work at some point was on the agenda as well. However, this morning in the middle of email my laptop froze up. I could not do anything with it and so had to power down. On start up I got a missing media notice and it looks like my hard drive went kaput. Luckily my Windows Mobile phone has everything I need to stay connected. Email, typepad blog platform, etc. Well we went to my family in Hollywood Beach for a fireworks display and BBQ tonight. I left my phone in a backpack, so I would not take it in the beach or water with me. Great, it rained, the backpack got soaked and my phone is down now too! So I think it is God telling me to go off grid this weekend. I am writing this on Bonnie's desktop machine. The kids are staying with my cousins and Bonnie and I are headed down to Key Largo for the weekend. I have her spare pink Razor with my Sim card for phone calls, but that is it. No email, no computers, no blogging! Speak to you all Sunday night or Monday, enjoy your weekend! Hopefully, I had one article written scheduled for tomorrow morning. I hope it publishes. | |
| Passport-peeking probably pervasive [Emergent Chaos] Posted: 04 Jul 2008 04:56 PM CDT Back in March, we wrote about unauthorized access to Barack Obama's passport file. At the time, a Washington Post article quoted a State Department spokesman: "The State Department has strict policies and controls on access to passport records by government and contract employees" The idea was that, while snooping might occur, it would be caught by controls put in place specifically to detect accesses to the records of high-profile people. Well, as it turns out the State Department may not be quite as good at detecting such accesses, or at following up (shocking, I know). In a July 4 article, the Los Angeles Times reports: A federal investigation of unauthorized snooping into government passport files has found evidence that such breaches may be far more common than previously disclosed, and the State Department inspector general is calling for an overhaul of the program's management. According to the article, passport files may be viewed by over 20,000 government workers and contractors. In a sample of 150 celebrities chosen for examination by investigators, 85% had been accessed at least once. One was accessed over 100 times (!) in the last six years. Amusingly, at a press conference held on July 4, State said that half of those who had access in March no longer have it. They also were unable to say whether spot-checks on detected accesses were taking place in the past. Put those together and you have a system where at least twice as many people have access as need it, and privileged operations are recorded but the folks in charge do not know if the audit trail is used. The redacted report is available at the C-SPAN web site, but not at the State Department's near as I can tell. Draw your own conclusions. | |
| Maybe privacy is dead after all [Network Security Blog] Posted: 04 Jul 2008 10:52 AM CDT At least it will be for YouTube viewers if this judge has his way. I rarely agree with Michael Arrington, but in this case he’s right: with all due respect, Judge Stanton is an idiot. If nothing else, this judge needs to go back and review some recent history about what can happen when huge databases of user activities are released. Even if user names weren’t part of the equation, we’ve learned that given an IP address and a sampling of activities, it’s possible to track down people by their search habits. I’m sure Sony is firing up Splunk or some other form of database search engine. I’m not sure if Sony thought of reviewing the data with intent of litigation against posters and viewers of YouTube videos, but they’ve got the bug in their ear now. And there’s going to be the chance of some really embarrassing revelations in the database. The EFF is already weighing their options in getting into this fight and they really do need to. I could get rabid about the stupidity of this ruling, but there are already more than enough people doing that. I’ll just say that a judge who probably had never heard of YouTube before this landed on his docket is probably not the best person to be setting this sort of precedent, especially since he doesn’t seem to be in the least bit familiar with the laws protecting the privacy of YouTube viewers. I’m just glad I’ve never created a YouTube account and rarely turn off NoScript long enough to view anything there. | |
| Exclusive : 8 months of belsec blog in one PDF [belsec] [Belgian Security Blognetwork] Posted: 04 Jul 2008 09:49 AM CDT We are going to have a celebration around here. Yes, all the postings since 8 months are in one big PDF file (nearly 100MB) but well those 378 pages, yes 378 pages of postings are all that we have done so far here at this blog. | |
| Happy Independence Day [Security Karma] Posted: 04 Jul 2008 09:46 AM CDT | |
| 8 months of the Belsec security blog [belsec] [Belgian Security Blognetwork] Posted: 04 Jul 2008 09:05 AM CDT We are already 8 months underway and maybe it is time to look back and before us. The RSS feed of the Belgian security bloggers is nearing its 300.000 views since than. First I am preparing to take a break soon for 2 weeks or so. Secondly we would like to see more bloggers coming here and more stuff coming that can't be published elsewhere. Thirdly we have been quite responsable and a few times the information has not been published as it could have been. Fourth we had a big incident that could have had legal incidents. We could have played the don quichots of the freedom of speech but we all have lives and jobs and families so we set our principles aside. At the same timie, the internet doesn't forget. It reminds us that Belgium is still a very restrictive country when it comes to debating things. Fifth we have been invited to speak for the Belgian parliament, which is a first and we are having talks and contacts with different parliamentarians and journalists. If you want to contact us or keep us updated, no problem we work with any democratic politician. Six it has been a very busy year if you take all into account. EID, Evoting, Ehealth, Belgacom ADSL problem to name but a few of the subjects in which we tried to play our role. Seven it is curious to see that we still are more or less the only Belgian platform about critical ITpolicy and ITsecurity. Nonetheless we can say that in some ways the omerta has been broken about some subjects. I don't think the EID study would have been done in that way by the professors if we haven't published already all that material before and he wouldn't have gotten curious and began doing more tests. Eight we have gotten some press which is fine, but not always for the good reasons. We would like the ITpress to become more critical and not just believe on first hand what was being told. A bit of googling and calling some stakeholders would sometimes change the view of things. The fact is also that those journalists have more protection and money than we. Nine we only have so much time in a day and so some other things weren't followed up anymore. The scamblog was a nice one, but took too much time. The be-hacked blog is the only repository of hacked belgian sites but it took too much time and so we only publish the most important belgian .be site hacked that day. Ten. We will be launching some new things between now and september. Some because some stuff doesn't work as it did (netvibes that is), others because it is more fun to do. Just watch out. and don''t forget, belsec that is also more than 1500 RSS feeds you can follow in bloglines, more than 13.000 articles or links in Furl.net and more than 100 freewares that are monitored for updates. This is also about more than 50 .be sites that are being monitored for uptime since 8 months and much more. So if you want to blog and don't know how and about what, there is material enough around here. And there are also the Belgian security bloggers network, part of the famous Security bloggers network which are now with 16 individual security bloggers. Who would have thought 8 months ago that we would do all that in so little time ? | |
| Posted: 04 Jul 2008 08:19 AM CDT If Marx was alive he would write a communist manifesto :) while seeing this presentation of the world as it is today.
* IMF report about rising fuel and food prices http://www.imf.org/external/np/pp/eng/2008/063008.pdf (58 pages)
| |
| London mayoral elections got a bad audit [belsec] [Belgian Security Blognetwork] Posted: 04 Jul 2008 07:38 AM CDT Votes for London Mayor and the 25 member London Assembly were counted electronically, and overall the election was well-managed by the independent body set up to run elections in London, London Elects. However, transparency around the recording of valid votes was a major issue, leading many of our team of 27 official observers to conclude that they were unable to observe votes being counted. And while hundreds of screens set up by vote scanners showed almost meaningless data to observers, London Elects admit that the system was likely to be recording blank ballots as valid votes. The report also details how London Elects are unable to publish an audit, commissioned from KPMG, of some of the software used to count the London vote, because of disputes over commercial confidentiality. The situation highlights the problems that arise when the very public function of running elections is mixed with issues of commercial confidentiality and proprietary software. In the context of a public election, it is unacceptable that these issues should preclude the publication of the KPMG audit. London Elects will pay Indra – the company who supplied both Bedford and Breckland during last year’s chaotic trials of e-counting technology in local elections – upwards of £4.5 million for delivering the London e-count. Today’s report recommends a full cost benefit analysis of any future e-count, set against a properly costed manual count. ORG’s report into e-counting of votes cast in the London Elections is out today They are also the source for this posting. The Belgian parlementarians busy with evoting should read this report carefully because it is full of things that should interest them so they won't make the same mistakes | |
| Posted: 04 Jul 2008 07:20 AM CDT The french presidents wants the EU to take the same measure that he has decided for France and that is being applauded by the media industry. It is the rule of three strikes and you are off the internet. If you have received two warnings from your ISP for illegal downloads, than at the third you will be cut off and I reckon you won't find another ISP that will connect you (except if you hack or use the wireless connection of your neighbor who has forgotten to secure his post and router (and because 'his ISP's doesn't do anything why should he ?' he thinks). If you are against this, these are place you can help to organize things http://www.laquadrature.net/wiki/Mobilisation_Paquet-Telecom http://www.openrightsgroup.org/
| |
| The flying dutch policecar [belsec] [Belgian Security Blognetwork] Posted: 04 Jul 2008 06:08 AM CDT | |
| OWI: Yet Another Anonymous Point of Attack? [GNUCITIZEN Media Portfolio] Posted: 04 Jul 2008 04:35 AM CDT About a month ago I traveled by train for a pre-sales meeting with a prospective customer. The trip was about two hours long, which would usually mean that it’d be boring. In this case it was different though: I was surprised with free OWI (Onboard Wireless Internet) on the train! Simply connect to the available open (no encryption) wireless access point and you will be redirected to a login portal, aka captive portal. Just like any hotspot you find at coffee shops such as Starbucks. However, I was very pleased to find out that users could login as a “guest” which means that all passengers could go online without paying any additional fee! Just to make things clear, going online as a guest was a legitimate form of access provided, as opposed to bypassing the security of the captive portal. NO illegal cracking (i.e.: SQL injection without permission) was done whatsoever! Kudos to the train company that provides the service! The connection wasn’t super fast, but fast enough to be able to check my email, read the news, update my RSS feeds, chat with my buddies, etc … It was quite reliable though, which is a big plus as I hate being disconnected while I’m on-line (it reminds me of the old days of dial-up Internet access). A bit of enumeration 101 led me to learn that:
From a security point of view, this technology adds another “anonymous” point of attack to the already-large list. I say “anonymous” (within quotation marks) because there is no such thing as truly anonymous connectivity. However, one thing is true: if the bad guy knows what he is doing, it becomes unfeasible to track the point of attack and the attacker’s identity. i.e.: it’s not worth starting an investigation if the committed crime didn’t lead to a serious profit loss. From the top of my head, these are some anonymous points of attack that come to mind:
Although there are tons of ways for attackers to hide their location and identity, somehow I find OWI more scary than most of them. It’s scary because the attacker is always on the move, which might make tracking his location more difficult due to time correlation issues when comparing logs. I know what you’re thinking: how is this different to the attacker using a stolen 3G Internet card? After all, using a 3G card would also allow the attacker to be constantly changing his geographical location (i.e.: by being inside a moving vehicle). Well, that’s a good point. However, in the case of using OWI the attacker doesn’t need to steal any equipment. If you think that being on a fast train won’t make tracking the location of the bad guy when a break-in occurs hard enough, how about doing it on a plane at 800 kmph? Yes, that’s right: free Onboard Wireless Internet aka In-flight wireless internet access, will most likely become very common in the future, which adds another anonymous point of attack to our list. Oh dear, remote Internet break-ins from planes, that’s gonna be fun! | |
| 4th of July, Business as Usual [Didier Stevens] [Belgian Security Blognetwork] Posted: 04 Jul 2008 03:39 AM CDT
VirusTotal coverage: 17/33 (Caveat emptor) Let me draw your attention to VirusTotal’s Hash Search function:
The MD5 of the malware I uploaded is: 213391f50aac3580fa8b7b5e8a671afe  | |
| Metasploit on an iPhone [/dev/random] [Belgian Security Blognetwork] Posted: 04 Jul 2008 03:12 AM CDT
An other good reason to get an iPhone (still not announced in Belgium, btw): Metasploit is available on the iPhone. See Muts’ Blog. | |
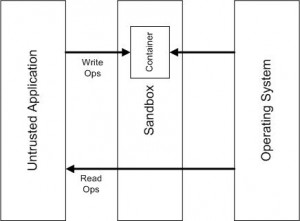
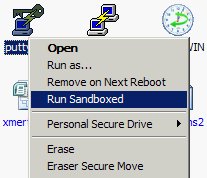
| Let’s Play in Sandboxes! [/dev/random] [Belgian Security Blognetwork] Posted: 04 Jul 2008 01:44 AM CDT
Children like to play in a sandbox. Computer users should also play in sandboxes… to increase their security! A sandbox is a mechanism (a software) used to execute untrusted applications. A sandbox can be seen as a light-virtualization system. True virtualization (performed with products like VMware, VirtualBox or Virtual PC) is a different way to work: You run several instances of one or more operating system on the same hardware platform. With a sandox, you just protect some resources (memory, devices or file systems) from being used by the untrusted program. Why use a sandox?
How does it work?
When running “sandboxed”, the application does not have a direct write access to the computer resources (Files, Disk Devices, Registry Keys, Process and Thread objects, Driver objects, and objects used for Inter-process communication: Named Pipes and Mailbox Objects, Events, Mutexs (Mutants in NT speak), Semaphores, Sections and LPC Ports). Read operations are simple: data are fetched directly from the OS. Write operations are intercepted and data are stored in the container only. Finally, for updates, first a copy of the data is fetched from the OS and updated in the container. Other restrictions can be applied:
The sandbox can be configured to automatically start specific application “sandboxed” like a web browser. All process started by a sandboxed applications will remain in the same sandbox. For other applications, you can use a shell integration and a new option will be available from Explorer: It’s really easy to test applications. Once installed, you don’t need to un-install it, just delete the sandbox content and your system will remain clean (like the snapshot feature of VMware). There are also mechanisms to retrieve files from a sandbox (example: when you downloaded a file from the Internet). Recovery can be automatic or manual (based on directories). You can also browse the content of a sandbox. Tip: there is no limitation of sandboxes, create one per “application group” (ex: browsers, internet, suspicious, …). It’s impressive to see the amount of files a Windows application can create! The Sandbox I use is Sandboxie. | |
| Spoofed User-Agent by AVG [/dev/random] [Belgian Security Blognetwork] Posted: 03 Jul 2008 11:20 AM CDT
I just read an interesting story on The Register: It seems that the latest AVG antivirus is generating a lot of web traffic with spoofed user-agents (IE6). Read the story here: http://www.theregister.co.uk/2008/06/26/avg_disguises_fake_traffic_as_ie6/. | |
| Whitepaper: Vulnerability Assessment Plus Web Application Firewall (VA+WAF) [Jeremiah Grossman] Posted: 03 Jul 2008 10:33 AM CDT For those interested we've released a whitepaper on how Vulnerability Assessment Plus and Web Application Firewall (VA+WAF) function independently and collectively. We spend a few pages describing the technical fundamentals of both which many should find educational – especially on the WAF side with industry material in painfully short supply. Very few people really understand the nitty gritty details of how WAF work and deployed in the real-world. I've learned a great deal in the last couple months talking with those who have. There is a little F5 ASM marketing in the paper so beware! :) Enjoy, snippets: "WAFs at their core are designed to separate safe Web traffic from malicious traffic before it's received by the website. And, if an attack does find a way to sneak past a WAF, it still has the ability to prevent sensitive information from leaving the trusted network. To get a better understanding of how the technology works, it's helpful to view a WAF's functionality as three discrete components - policies, policy generation, and policy enforcement. Depending on the particular WAF in use, they may go about implementing each component in a number of different ways. No one particular way has proven to be the right way, as each has its pros and cons." "Every effective vulnerability assessment program requires a cohesive combination of people, process, and technology. Qualified people are necessary to carry out day-to-day tasks, manage the technology, and interpret the results to make them meaningful to the business. Process is required for coordinated efforts between executive management, IT Security, and software development groups to share information, prioritize vulnerability fixes, and enable organizational improvements. The right technology is essential for consistency, efficiency, and comprehensiveness. Whether an organization chooses to perform vulnerability assessments with internal resources, a consultancy, or a Software-as-a-Services vendor, the overall vulnerability program must always account for people, process, and technology. If not, the effort will cost more in time and dollars than it should. Or worse, simply not work." | |
| Google Serves Up Malware [Alert Logic] Posted: 03 Jul 2008 10:07 AM CDT | |
| Posted: 03 Jul 2008 09:29 AM CDT  Rob and I get this kind of question all the time. After Blackhat last year we got some many requests from people that wanted to learn to hack Gmail accounts it was funny. Last week I actually got an email that contained this rather cryptic string: Hello, I do not know how to develop code but wish to hack wifiWhat do you say to that? | |
| Oooohh, more cocktail parties at the airport Hilton... [Errata Security] Posted: 03 Jul 2008 09:12 AM CDT Awesome, another industry organization. ICASI From their website: "ICASI intends to be a trusted forum for addressing international, multi-product security challenges. " Its amazing these mutinational companies can put the desire to sell their own wares out of the way and work together for a common goal of...selling more products? I think what we need is an organization to stamp out industry organizations. | |
| ratproxy - Passive Web Application Security Audit Tool [Darknet - The Darkside] Posted: 03 Jul 2008 03:42 AM CDT Ratproxy is a semi-automated, largely passive web application security audit tool. It is meant to complement active crawlers and manual proxies more commonly used for this task, and is optimized specifically for an accurate and sensitive detection, and automatic annotation, of potential problems and security-relevant design patterns based on the... Read the full post at darknet.org.uk | |
| bpmtk: A New Version With bpmtk.dll Included [Didier Stevens] [Belgian Security Blognetwork] Posted: 03 Jul 2008 03:41 AM CDT Here is a new version of the Basic Process Manipulation Tool Kit (bpmtk). Some noteworthy changes:
So now you can also load the bpmtk as a DLL in a process and it will execute its configuration. The configuration is embedded in the DLL as an ASCII string. To change the configuration, you’ve 2 options:
 |
| You are subscribed to email updates from Black Hat Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Black Hat Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |













No comments:
Post a Comment