Spliced feed for Security Bloggers Network |
| Hyprocisy and Irony in Minnesota [The Falcon's View] Posted: 04 Sep 2008 08:43 AM CDT |
| Chrome epidemia globale controllata [Sicurezza Informatica Made in Italy] Posted: 04 Sep 2008 06:39 AM CDT Forse bisognerebbe riscrivere alcuni libri di marketing. Quale prodotto (gratuito) si è imposto così velocemente fino ad assumere le sembianze di un epidemia su scala mondiale? Nemmeno il blaster ai suoi tempi seppe far di meglio.  Le statistiche si riferiscono ad hackerscenter.com , che è un sito principalmente visitato da utenti eruditi in termini di sicurezza. E ciò è preoccupante. Aggiornamenti dal fronte privacy : Matt Cutt ha annunciato la revisione della privacy policy eliminando il paragrafo 11 . Meno male se ne sono accorti. |
| Posted: 04 Sep 2008 05:18 AM CDT My fellow blogger Didier Stevens apparently was interviewed in the Audioparasitics podcast. Some might know Didier from the test he did with Google ads to demonstrate how it could be used to distribute malware. His blog didierstevens.com is very interesting and also hosts several interesting tools he has written. The podcast episodes are listed below:
|
| Posted: 04 Sep 2008 04:43 AM CDT The socialist party is (after all that time) at last beginning to understand that political activism is also made online and can be bolstered online - although it wouldn't make any difference if the rest is not good. So at its national conference it has organized a workshop with some firm that probably does some of the modernizing of their website - but still lacks the global strategic view for the movement an sich or doesn't have the go ahead to implement it - and a conference with two interesting US speakers. The most interesting thing to see will be the reaction of the Belgian politicos. http://www.huffingtonpost.com/amanda-michel http://davidsgrewal.googlepages.com/ programma 18th october http://www.visie08.be/Program.aspx Not sure yet if I will put a Free Georgia tshirt on ..... :) |
| BelsecTV the future of the internet (OECD june 2008) [belsec] [Belgian Security Blognetwork] Posted: 04 Sep 2008 04:15 AM CDT This page has links to interviews captured during the meeting of the Organisation for Economic Cooperation and Development on the Future of the Internet Economy, in Seoul, Korea, June 16-18, 2008. Foreign ministers, business leaders, technical experts, and representatives of civil society and academia conferred at this OECD ministerial event, with the goal of comparing experiences, seeking answers to common problems, and coordinating domestic and international policies. A series of very interesting speakers and subjects. |
| belsectv : internet and flood management [belsec] [Belgian Security Blognetwork] Posted: 04 Sep 2008 04:00 AM CDT |
| Posted: 04 Sep 2008 02:30 AM CDT This presentation says that it does because of the fact that so many different parts of the production process are done in so many different countries. It also talks about the globally integrated enterprise and takes as an example IBM click on the image to enlarge |
| freeware of the day Active@ KillDisk [belsec] [Belgian Security Blognetwork] Posted: 04 Sep 2008 01:45 AM CDT Active@ KillDisk - Hard Drive Eraser is powerful and compact software that allows you to destroy all data on hard and floppy drives completely, excluding any possibility of future recovery of deleted files and folders. It's a hard drive and partition eraser utility. Active@ KillDisk conforms to US Department of Defense clearing and sanitizing standard DoD 5220.22-M. The most secure Gutmann's data destruction method is also implemented. You can be sure that once you clean up with Active@ KillDisk, sensitive information is purged out forever. New Wipe function that wipes out all unused space on existing drives, not touching existing data. We highly recommend you to run this FREE utility for the hard and floppy drives you want to dispose of, recycle, re-use, sell or donate to somebody. http://www.download.com/Active-Kill-Disk-Hard-Drive-Eraser/3000-2092_4-10073508.html?cdlPid=10852099 |
| Electronic voting machines. FAIL. [Security4all] [Belgian Security Blognetwork] Posted: 03 Sep 2008 11:13 PM CDT  In a previous post, I mentioned the risk of electronic voting machines. It seems that our doubts where not totally unfounded. From Schneier.com:
I would prefer that there is a paper trail that can be audited. Have a further read at Schneier's essay: "Why Election Technology is Hard." Also Robert Halbeer seems to share our concerns. Previous post: (Photo under creative commons from Squonk11's photostream) |
| Quoting Dilbert is a Best Practice [Emergent Chaos] Posted: 03 Sep 2008 10:15 PM CDT |
| Catalyst Conversation Starter: The High Cost of “Freeware” [The Security Catalyst] Posted: 03 Sep 2008 09:16 PM CDT When it comes to protecting home computers, “Is freeware free?” This is not a question aimed at the enterprise. Instead, this is a question that cuts to the heart of the advice that security professionals offer to those who depend on that experience and insight to guide them, be they parents, siblings, friends, co-workers or even people we met in passing. Professionals are often called upon to make quick decisions based on experience and training (we can argue later whether this is good or bad). While this may be an accepted business practice - does it work as well when it comes to advising families on how to protect their computers? I think we need to step back and consider. If someone asks you if they should spend money for a paid software solution to protect their home computer or simply use “freeware” solutions - what is the best answer? What do you recommend today? Why? To aid in the process, I offer for consideration a report that details my experience evaluating freeware through the lens of a consumer. The report is short. It is designed to be an opportunity to stop, think and engage in the conversation. Based on a challenge, I stepped back and examined the situation in a manner different than normal for me. I worked to experience the process of finding, downloading, installing, configuring and using freeware solutions. I considered the time spent and took an effort to measure pop-ups, messages and potential frustrations. Taking the time to step back literally changed what I thought and what I recommend. It forced me to examine the “truths” I believed in favor of real experience. Get the report here: http://www.securitycatalyst.com/eGuides/Security-Catalyst-The-Hidden-Cost-of-Freeware.pdf Come join the discussion in the Security Catalyst Community here: http://www.securitycatalyst.org/forums/index.php?topic=960.0 (and join me for a live Talkcast on Thursday — Noon Eastern — to discuss this with special guest Dave Cole) This posting includes an audio/video/photo media file: Download Now |
| Posted: 03 Sep 2008 08:56 PM CDT
It goes something like this:
You'll laugh, you'll cry. You'll want to know what I used to make my slides... ;) Coming soon to a disturbed audience near you (seriously.) /Hoff |
| The Most Overused Term In Security Product Management/Marketing... [Rational Survivability] Posted: 03 Sep 2008 08:36 PM CDT Sick of it. Sucks monkey balls. Is about as relevant and non-sensical to me as "kosher ham." I've been really annoyed by this term since I ashamedly added it to my lexicon of "roll-off-the-tip-of-my-tongue" buzzwords years ago for reasons I can't rightly remember. Too much TV. I suppose temporally, anything not shipping, regardless of how (r)evolutionary it may or may not be, is technically "next generation," but it's today overly (ab)used to imply some quantum leap in capability, functionality, or saleability. Oh, and one usually has to pay more for it. The truth is -- and as I pointed out in my disruptive innovation presentations -- there just aren't that many "big bangs" that deserve to have this moniker hung upon the mantle, but rather a series of dampened oscillations due to punctuated equilibrium until everything settles down and looks pretty much the same. Then version 1.17 ships and BAM! Next generation, baby! To all you product managers and marketers, "next generation" is so over-played at this point that the populous at large simply regards it like the features lists plastered on the trunk lids of automobiles advertising the niftiest new (but abundantly standard) set of features purchased on the luxo-barge meandering about in the lane ahead. Whilst I am happy to know that Bob got the GLX, limited edition, R-Series with ABS, sunroof, intercooled turbo with XM radio and AWD, the suggestion that his "seats 8 but still makes him look like a dork" mini-van is a "next generation" platform doesn't really say much about Bob, now does it? -- On the flip side, I'm just thrilled to learn via press release today that "Secure Computing [is] to acquire Securify to drive [its] next generation firewalls" which oddly enough includes a list of features that are aimed squarely at competing with folks like Palo Alto Networks'* "next generation" firewalls which were released sometime ago. Further, someone at PAN and Secure Computing will undoubtedly be shocked to learn that Crossbeam, Fortinet, and Cisco all have "next generation firewalls" too. Crap! What comes after "next generation?" I suppose whatever it is would have to be made of pure unobtanium... I knew I should have trademarked that... /Hoff * Speaking of Palo Alto Networks, you may have missed that a couple of weeks ago, PAN secured a C-Round of $27M. That ought to be good for a couple more 'next generations' of something...they also finally got a new CEO back in July (Lane Bess from Trend Micro.) |
| Google's Chrome: We Got {Secure?} Browsing Bling, Yo. [Rational Survivability] Posted: 03 Sep 2008 08:31 PM CDT
Back in June/July of 2007, I went on a little rant across several blog posts about how Google was directly entering the "security" business and would eventually begin to offer more than just "secure" search functions, but instead the functional equivalent of "clean pipes" or what has now become popularized as safe "cloud computing." I called it S^2aaS (Secure Software as a Service) ;) OK, so I'm not in marketing. Besides the numerous initiatives by Google focused on adding more "security" to their primary business (search) the acquisition of GreenBorder really piqued my interest. Then came the Postini buyout. To be honest, I just thought this was common sense and fit what I understood was the longer term business model of Google. To me it was writing on the wall. To others, it was just me rambling. So in my post from last year titled "Tell Me Again How Google Isn't Entering the Security Market? GooglePOPs will Bring Clean Pipes..." I suggested the following:
Now we see what Google's been up to with their announcement of Chrome (great writeup here,) which is their foray into the Browser market with an open source model with heaps of claimed security and privacy functions built in. But it's the bigger picture that's really telling. Hullo! This isn't about the browser market! It's about the transition of how we're going to experience accessing our information; from where, what and how. Chrome is simply an illustration of a means to an end. Take what I said above and pair it with what they say below...I don't think we're that far off, folks... From Google's Blog explaining Chrome:
Here come the GooglePipes being fed by the GooglePOPs, being... ;) /Hoff |
| Looking for Hotspots in Antwerp [Security4all] [Belgian Security Blognetwork] Posted: 03 Sep 2008 05:36 PM CDT  I was visiting the site of www.antwerp.be to see if there were some fun activities this month. By chance, I stumbled upon a page that contained a list of hotspots in Antwerp. After looking at the list, I noticed that they only mentioned hotspots with a (billable) captive portal. A pity, because there are other ways then *cough* DNS tunneling *cough* to get free wifi (which is reallllyyy slow and not legal). For example, McDonalds, Foodmakers and Exki all are member of www.free-hotspot.com. You can look on their map for these or other restaurants that will provide free internet. The map is not up to date as the Exki on the Keyserlei and the McDonalds on the Meir is not on the map, but they do exist. They are all located in several places in Anwerp. Have fun checking your email for free (and don't send anything cleartext) !!! Use encryption. Related posts:
|
| What do we call Twit Spam? [An Information Security Place] Posted: 03 Sep 2008 04:30 PM CDT I have been blocking more and more Twit spam followers lately on my Twitter account. Some of the accounts have been suspended by Twitter, which is great, but it is still a a nuisance. Just one more by-product of Web 2.0 I guess. But the real quandary is what to call Twitter Spam. SPIT is already taken (Spam over Internet Telephony). Maybe SPITT, with an extra “T”? How about TWAM? But most spam names are acronyms and start with “SP”. How about SPER? Uhhh, that would probably not be good. SPITTER? Hmmm, that might work. Any ideas? [UPDATE]: What about “Spittle”? Vet |
| I Don’t Get It [securosis.com] Posted: 03 Sep 2008 04:14 PM CDT From the “I really don’t get it” files: First I read that Google’s new Chrome browser & Internet Explorer 8’s features are threats to existing advertising models. And this is news? I have been using Firefox with NoScript and other add-ons in a VMWare partition that gets destroyed after use for a couple years now. Is there a difference? What’s more, there is an interesting parallel in that both are cleansing browsing history and not allowing certain cookie types, but rather than dub these ‘privacy advancements’, they are being negatively marketed as ‘porn mode’. What’s up with that? Perhaps I should not be puzzled by this Terror database failure, as whenever you put that many programmers on a single project you are just asking for trouble. But I have to wonder what the heck they were doing, to fail this badly with the ‘Terror Database Upgrade’? This is not a very big database- in fact 500k names is puny. And they let go 800 people who were just part of the team? Even if they are cross-referencing thousands of other databases and blobs of information, the size of the data is trivial. Who the heck could have spent $500M on this? What, did they write it in ADA? Can’t find enough good Foxbase programmers? For a couple of million, I bet you could hire a herd of summer interns and re-enter the data into a new system if need be. It’s a “Terror Database” all right, just not the way they intended it to be. MIT develops a network analysis tool that “enables managers to track likely hacking routes”. Wow, really? Oh, wait, don’t we already have a really good tool that does this? Oh yeah, we do, it’s Skybox! -Adrian |
| Google Chrome - Sicurezza e privacy che non c'è [Sicurezza Informatica Made in Italy] Posted: 03 Sep 2008 03:44 PM CDT  Esattamante dopo 4 ore dal rilascio di Google Chrome versione beta ecco il primo Denial of Service: Esattamante dopo 4 ore dal rilascio di Google Chrome versione beta ecco il primo Denial of Service:Inserendo questo link in una pagina web e facendo semplicemente posizionare il mouse sul link (non occorre cliccarci sopra) Google Chrome va miserabilmente in crash nonostante l'utilizzo di processi separati per ogni tab. Ironia vuole che proprio il Tg1 oggi parlava di come il nuovo browser fosse immune da tali tipi di attacchi: "In caso di crash di una tab il browser rimarrà comunque funzionante". Così non è e complimenti a Rishi NarangHERE A quanto pare anche inserendo un bookmark troppo lungo il browser va in crash. Medesimo risultato inserendo about@nella barra degli indirizzi. Più che una beta sembra una alpha release che sconsiglio di usare finchè tutti questi errori non saranno risolti, considerando che siamo solo al primo giorno e un eventuale esecuzione di codice tramite un buffer overflow è del tutto possibile a questo punto. (A proposito, solo oggi già l'1% della popolazione di internet ha navigato con google chrome, non è poco) L'unica vera feature di sicurezza al momento sembra essere l'esecuzione con privilegi da utente semplice (non Administrator) che dovrebbe evitare il peggio in caso venisse fuori un exploit di remote code execution. Molti discutono sulla privacy policy che si accetta al momento dell'installazione. Ecco un estratto: 11.1 You retain copyright and any other rights that you already hold in Content that you submit, post or display on or through the Services. By submitting, posting or displaying the content, you give Google a perpetual, irrevocable, worldwide, royalty-free and non-exclusive licence to reproduce, adapt, modify, translate, publish, publicly perform, publicly display and distribute any Content that you submit, post or display on or through the Services. This licence is for the sole purpose of enabling Google to display, distribute and promote the Services and may be revoked for certain Services as defined in the Additional Terms of those Services. Inoltre: You confirm and warrant to Google that you have all the rights, power and authority necessary to grant the above licence Comprate una vocale?
|
| FBI Opens Anti-Fraud Hurricane Gustav Hotline [Infosecurity.US] Posted: 03 Sep 2008 03:23 PM CDT
|
| Cisco Security Advisory VPN and SIP Vulnerabilities [Infosecurity.US] Posted: 03 Sep 2008 03:12 PM CDT |
| NIST Hosts 4th Security Automation Conference [Infosecurity.US] Posted: 03 Sep 2008 03:03 PM CDT
The National Institute of Standards and Technology (NIST) will host a conference and accompanying workshops demonstrating the utilization of open standards to automate computer security tasks. The 2008 Security Automation Conference and Workshop will take place at the campus in Gaithersburg, Md. from Sept. 22-25, 2008, and is co-sponsored by NIST, the National Security Agency (NSA), the Defense Information Systems Agency (DISA), and the Department of Homeland Security (DHS). General registration closes on Sept. 16. More information on the conference can be found at the NIST Conference Page. |
| Carnegie Mellon Releases New Firefox Security Plugin [Infosecurity.US] Posted: 03 Sep 2008 02:50 PM CDT
[1] CMU Perspectives |
| Carnegie Mellon’s SEI Published New Forensics Report [Infosecurity.US] Posted: 03 Sep 2008 02:31 PM CDT
|
| Security Industry in a Nutshell? :) [The Falcon's View] Posted: 03 Sep 2008 02:11 PM CDT |
| Danchev - Indian CAPTCHA Solving Economy Exposed [Infosecurity.US] Posted: 03 Sep 2008 01:37 PM CDT
|
| UPC (Austrian ISP) started using Sitefinder Service [Robert Penz Blog] Posted: 03 Sep 2008 01:06 PM CDT The Austrian ISP UPC (Chello, Indo, Telesystem) has activated a system which sends your browser to UPC site if a domain could not be resolved. They say that this helps their less tech-savvy customers but I believe it helps them more. Because they can put some ads on this site. They are not the first to try this. 2003 Versign tried something similar (called Sitefinder) but it was stopped by ICCANN and user protests. But that was not a provider. The system is an Opt-Out one and not Opt-In. You need to perform 5 clicks, fill out a form and time to wait for a support employee to get it deactivated. You should really Opt-Out as the system can lead to problems if an DNS server is responding too slow and the system tells you you’ve a wrong domain name. The other question is what happens with the data gathered by the search engine on this site, which tries to guess what you meant. |
| My first issue. [IT Security: The view from here] Posted: 03 Sep 2008 12:59 PM CDT I read a post somewhere last week (it may have been one of Rich Mogull's?) where a simple question was asked about what people liked about IT Security blogs. The (rather ironic) answer from one commenter was that they didn't like all the complaining that went on - and preferred it when people explained answers to security problems. Having written a post just beforehand having a good old moan about things that people do stupidly, I thought I'd try and redress the balance in the force by starting to discuss a few issues, and how I would solve them. I hope to get some input as to why I'm wrong, and as many complaints about my stupidity as my comments can hold. Issue of the day for me is secure email. Without discussing any more politics, let us assume that we have a business requirement for secure email. I can't tell you what we are sending out, because then I'd have to kill you, just rest assured that we need to. We need to send out to lots of different domains, and we want to initiate that exchange every time. Users of the system must be registered with us. The solution that was proferred to me was one of the IBEs (Identity Based Encryption). There are 2 that I know of, Trend and Voltage. I'm not going to say which one has been picked, because they are much of a muchness as far as I can see, and neither is right for me. Requirement - must be standards based.IBE isn't a standard as yet. It's a great technology, lots of fun, and has some great applications, but it isn't something that's tried and tested. I'm worried by it. Requirement - must not add complexity of management.IBE isn't as simple as you might think. Key management is still the major issue, especially when you are dealing with external clients coming into your network to pick up decryption keys. Requirement - Blackberry compatible.Those people who have a requirement for Blackberries probably have a requirement for secure email. It's bad planning not to be addressing this immediately. Requirement - must integrate with current architecture.As with the 'standards based' requirement, this is going to be hard work. Anything so new is going to be crowbarred in. The only thing it integrates with is Exchange and Outlook, but then all email solutions do... how about working with certificates, protecting attachments end to end, and being able to vary the levels of security via policy. Which reminds me - who's writing the policies on this thing. I don't really understand who needs to be encrypted to, or in fact... why? Requirement - fully audit when this data is sent out of the network.You just can't do that with the system which created it. If it's being emailed, an internal user can email it out, but there is no reliable automated process to log this. It's either a manual process by the user - so more policy writing, more holes for errors to slip into - or it's nothing. That's scary, especially when the next step is emailing data out of the network. Which brings me back to the politics I'm afraid. Why does anyone need secure email? Email is NOT secure. The only reason you need secure email is because another process is broken, it is a sticking plaster option to my mind. Better to create a secure extranet, register your users there, use a third party PKI if you need to use keys at all, and use the certificates to authenticate your users too whilst you're at it. Use a CMS type too to publish pages to individual users as and when they require to download data from your network. That way you have a full audit trail too... In short, no matter how hard a security person tries to be helpful, they will always end up moaning. It's kind of |
| Hidden Firefox feature and the plugin Pencil [Robert Penz Blog] Posted: 03 Sep 2008 12:38 PM CDT I found something interesting, which I guess some already know, but still I though its a nice feature. Copy following into your Firefox browser address bar and hit enter.
You can now change a homepage by deleting stuff or replacing some text to test something or making a faked screenshot. I think this can be really handy sometimes and it is build in. Something more sophisticated is following Firefox 3.x plugin, called Pencil (You can also download it here). Pencil is a Firefox add-on to do GUI prototyping and simple sketching, take a look at this blog post which shows what Pencil can do. As a teaser I put a screenshot at the end to this post 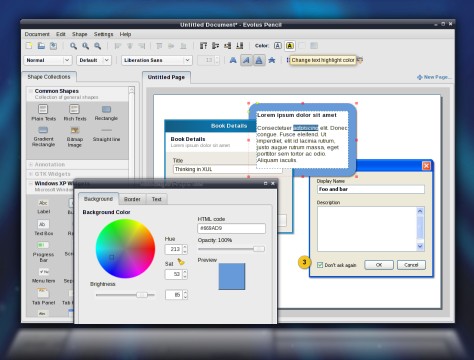 |
| DIRECTI Demands Takedown of KNUJON Post [Infosecurity.US] Posted: 03 Sep 2008 12:30 PM CDT
The email essentially demands the ‘takedown’ of the Infosecurity.US post, reporting on the KNUJON discoveries pertaining to the DIRECTI Group’s Internet Registrar activities. Also, attached to the email from DIRECTI, is a point by point refutation to the KNUJON research. We have redacted Mr. Turakhia’s cellular telephone number in the email (which he so graciously supplied us).
On Wed, Sep 3, 2008 at 01:09, Bhavin Turakhia <bhavin.t@directi.comwrote: Given below, is a list of all the false information, conclusions and 1. EST is NOT affiliated to the Directi Group in any way: EST just 2. Your claim that the accredited companies we own are: a) Phantom 3. You claim that the Directi Group is somehow closely linked with 4. There are several other domain names that you have listed for various 5. The statement “While Directi claims they will suspend illicit 6. The statement “If a consumer complains to 7. On several prior instances, we have attempted to explain to your 8. Also, as a Registrar, we must categorically state that we have no 9. During the Prescription Addiction Radioshow, you claimed that the Based on all of these false assumptions, misrepresentations and factual I believe you understand as well as we do that a true cleanup process Well also be glad to clarify your doubts on the above mentioned facts, over Considering the defamatory nature of the content in your posts and the Best Regards, |
| Hans Monderman and Risk [Emergent Chaos] Posted: 03 Sep 2008 12:04 PM CDT Zimran links to an excellent long article on Hans Monderman and then says: When thinking about human behavior, it makes sense to understand what people perceive, which may be different from how things are, and will almost certainly be very different from how a removed third party thinks them to be. Traffic accidents are predominantly caused by people being inattentive. Increase the feeling of risk, and you increase the attention. I know when I am in traffic on my bike, I'm hyper-vigilant, and this has made me a better car driver.Some interesting quotes from the article: Without bumps or flashing warning signs, drivers slowed, so much so that Monderman’s radar gun couldn’t even register their speeds. Rather than clarity and segregation, he had created confusion and ambiguity. Unsure of what space belonged to them, drivers became more accommodating. Rather than give drivers a simple behavioral mandate— say, a speed limit sign or a speed bump— he had, through the new road design, subtly suggested the proper course of action. And he did something else. He used context to change behavior. He had made the main road look like a narrow lane in a village, not simply a traffic- way through some anonymous town. On Kensington High Street, a busy thoroughfare for pedestrians, bikes, and cars, local planners decided to spruce up the street and make it more attractive to shoppers by removing the metal railings that had been erected between the street and the sidewalk, as well as “street clutter,” everything from signs to hatched marks on the roadway. None of these measures complied with Department for Transport standards. And yet, since the makeover there have been fewer accidents than before. Though more pedestrians now cross outside crosswalks, car speeds (the fundamental cause of traffic danger) have been reduced, precisely because the area now feels like it must be navigated carefully.We talk about Monderman's thinking about risk in the New School, and I wanted to talk a little about the implications for computer security. The idea of giving a user experience a sense of place is a great one, if we could constrain it to the good guys. Unfortunately, bad guys can design their websites to look like a narrow lane in a village, a welcoming mall, or whatever else they want. The designer of a space can make you feel safe or feel like you must navigate carefully. What do you think phishers are going to do? |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |






 The New Orleans, Louisiana Field Office of the
The New Orleans, Louisiana Field Office of the  Cisco
Cisco The
The  Carnegie Mellon University’s Software Engineering Institute
Carnegie Mellon University’s Software Engineering Institute Dancho Danchev’s
Dancho Danchev’s The following is an email transcript, of a message I received this morning from the
The following is an email transcript, of a message I received this morning from the
No comments:
Post a Comment