Spliced feed for Security Bloggers Network |
| Security Briefing: September 2nd [Liquidmatrix Security Digest] Posted: 02 Sep 2008 06:14 AM CDT  Tuesday (and September) has arrived. That new(ish) project that I mentioned last week is my way of kicking myself in the backside. I have been building some girth over the last few months and now it has to come off. Today is the beginning of the midsection meltdown. I have a new gym membership in hand and I’m ready to get it done. Click here to subscribe to Liquidmatrix Security Digest!. And now, the news…
Tags: News, Daily Links, Security Blog, Information Security, Security News |
| Attack Visualizations Using GraphViz and Google Earth [BlogInfoSec.com] Posted: 02 Sep 2008 06:00 AM CDT There is a saying, a picture is worth more than a thousand words. This certainly holds true, especially with determining the source of network attacks and what kind of network attacks are at your edge or internal networks. We are going to explore two kinds of visualizations that use the same data source, but convey very different messages. The sources of data is the net-flow traffic summary that can be generated by Argus or network devices and security event logs that are generated from your SIEM (in my case, OSSIM). From the net-flow traffic summary, we’re only interested in the source and destination IP addresses and ports, as this is all in which is required for matching threats identified by the SIEM. The first tool that we will employ to help create the first visualization is GraphViz (http://www.graphviz.org/). GraphViz uses a relationship language called DOT, whose grammar is easy to understand and interpret by two easy steps: define a graph and create relationships. For our purpose, we want to create a flow graph that helps us visualize attackers, and possibly further define attack types. To do so, we simple write a script that will parse the net-flow data from our network, and query those IP addresses against our SIEM’s threat database. If there is a match on the IP address, we can change the context of the relationship in the visualization. For instance, if the source is an internal IP address going out, we can color the bubble red based on the assumption that it is infected. The lines that radiate from that host can have two relationships, a solid for TCP protocols and dotted for UDP with a label on the line for the communicating port. If there is a virus infection running amok in the network, you can then imagine the visualization that is rendered, and further more if there is a Command and Control in use it may become more easily identifiable. With the discussion above, you would have the following DOT syntax, and once rendered the following graph snippet that shows a spoofed UDP communication going to my DNS server, along with hosts attacking it. The second tool we will use is Google Earth. The technique used above to extract the information will be slightly modified; we wont use source or destination ports, and we also wont be as fancy with our line classifications. What we will add to the information is a Geo Location database so that we can lookup the IP address and get a latitude and longitude, and we’ll only consider three forms of communications: clean (green), hostile (red), and live hostile (purple). (...) © Russell Handorf for BlogInfoSec.com, 2008. | Permalink | No comment This feed is copyrighted by bloginfosec.com. The feed may be syndicated only with our permission. If you feel that this feed is being syndicated by a website other than through us or one of our partners, please contact bloginfosec.com immediately at copyright_at_bloginfosec.com. Thank you! |
| Posted: 02 Sep 2008 05:51 AM CDT It is true what many of you have heard. Google is releasing their own browser. Google Chrome, as they call it, is based on WebKit rendering engine and introduces some novel approaches to interacting with web technologies. I must say, it is very exciting to see all of this happening. What makes Google Chrome different is its architecture. The browser is no longer single-threaded process. Each tab is actually a separate process with own memspace. I am not sure if we are talking about threads or actual program instances but what is more important is that when you close a tab, you are virtually terminating the process. At least, this is what Google says. This seams to have some interesting implications on the security of the browser. If you corrupt the tab’s memspace then you will cache only that particular process. The browser and all other tabs should continue working just fine like nothing ever has happened. This approach has its own advantages and disadvantages. The advantages are obvious: the user experience is intact. The disadvantages are that pwning might get easier. It is very early to me to say more on this topic because I haven’t seen Google Chrome in action, but I have the slight suspicion that there will be some security consequences as a result of this security model. Google Chrome also implements a new privacy feature. I think they call it incognito or something. Basically if you browser while being in Another interesting feature which I need to mention is that popups are not blocked but they open in a minimized window. If you want to see them you just drag the popup icon and there you go. Again, this is very interesting but I can already see how this may be abused. For example, it will make a huge difference if the rendering engine has already processed the content of the popup even if it is minimized. If this is the case, then this feature could turn into a very handy mechanism of hiding malicious activities. For example, if during the attack, the page flickers or the attacker is rendering too many corrupted ANIs :) then certainly, hiding it behind a minimized popup will be a great way of avoiding detection by casual observation. Of course these are pure speculations. Google Chrome also provides sandboxing functionalities. Apparently each process is sandboxed but I have no details how was that implemented. I would say that perhaps sandboxing JavaScript is fairly easy but doing that on a process level may not be as much. Maybe each process runs with unprivileged account which does not have many rights. But still, it must have some rights in order to do something. So taking over a process may not result into an immediate pwnage but it will certainly give the attackers some advantage. I am very interested to learn how this sandboxing mechanism is implemented for the various operating systems if the browser is cross-platformed of course, which I believe is the case. If everything is implemented correctly, which I hardly doubt, then Google Chrome may turn into a very nice technology I may consider using it in the near future. However, none of these security features interest me as much as those that allow me to prevent poorly coded web applications leaking my details over unencrypted channels. Or even features which will prevent certain types of CSRF and XSS attacks. I’ve said it before! Most of my data does not reside on my computer any more. Of course this philosophy had some bad side effects on me, but my point is that the data is on the Web and therefore I am concerned how my browser protects me when it comes down to Web related bugs. I believe that Google Chrome lacks mostly that and if they decide to implement any of recommendations then in my eyes, I will certainly have a winner in the upcoming browser wars. |
| The 7 Greatest Ideas in Security [Amrit Williams Blog] Posted: 02 Sep 2008 01:29 AM CDT It is easy to criticize, in fact many have built their entire careers on the foundation of “Monday morning quarter-backing”, not only is it human nature to look for improvements at the detriment of old ideas, but it is also far more humorous to point out what is wrong than to espouse the virtues of what works. I recently posited what I believed to be the “11 Worst Ideas in Security” (here), but to every yin a yang, to every bad a good, to every Joker a Dark Knight, for the purpose of finding balance, I give to you the 7 Greatest Ideas in Information Security… 7. Microsoft and Security as part of the SDL (Lord Vader finds your lack of faith disturbing) The greatest flaw in information security is that we try to build security on top of a fundamentally weak foundation, whether we are talking about the core routing infrastructure, the open standards and protocols that drive them or the operating systems themselves, the majority of the Information Security industry is squarely aimed at resolving issues of past incompetence. Nowhere has this been more apparent than the decades plus of vulnerabilities found in Microsoft products. Crappiness exists in other products and is not an attribute solely patented by Microsoft, they just happen to power everything from my Mom’s computer to the Death Star, so when they fail it is almost always epic. The Microsoft SDL (here) and the work that folks like Michael Howard (here) have done to develop security into a critical aspect of the SDL is not only admirable, it is inspiring. To have witnessed a company the size of Microsoft essentially redesign internal processes to address what was seen as a fundamental deficiency and to then continue to develop these processes changes into thought leadership sets an example for all of us, small business and world dominating enterprise alike. Implementing security as part of the SDL and utilizing concepts such as threat modeling to identify weaknesses and eradicate them before releasing code to the public is arguably one of the greatest ideas in security. 6. The Principle of Least Privilege (Not all of us can know Zarathustra) Since Saltzer and Schroeder formulated the concept as part of computing we have been striving to achieve it. It is neither new nor is it novel, but it is critical to how we design computing systems and how we develop and implement security controls. It contradicts our own Nietzschean side to feel like constraints and rules are important for the common man, but shouldn’t apply to us personally, but nothing should be afforded more privilege than needed and this is one of the “laws of security”. 5. Segmentation (Your Mendelian trait is in my algorithmic reasoning) Segmentation of duties, of networks, of memory, of code execution, of anything and everything that should never mix. Combine lack of segmentation with a lack of implementing the principle of least privilege and you turn a simple browser based buffer overflow into a highly damaging payload that can easily replicate throughout the Internets. For us to truly realize improvements in security, as defined by less successful security incidents - real and imagined - and marked by an increase in visibility and control over all of our computing systems, segmentation of everything is an ideal to strive for. 4. Inspect what You Expect (Question everything) Also known as “trust but verify” as used by the Gipper in his dealings with the Russians during the cold war. Trust is important, but it is even more important to validate that trust. One of the most significant changes every software developer can make today, whether they are developing COTS or internal applications, is to allow security persons to inspect that the application is functioning, being accessed, and managed to the controls that the organizations expects. From networking to applications to users to virtualization to quantum anything, this principle must extend across every layer and concept of computing today and tomorrow, 3. Independent Security Research (So, I’ve been playing with something…no not that) The ridiculous vulnerability disclosure debate aside, independent security research has had a significant benefit on the security industry. The best example is the recent DNS vulnerability that has been discussed, dissected, and covered ad nauseam. Since it’s disclosure it has not only resulted in providing more awareness of the fundamental flaws in the core infrastructural protocols like DNS and assisted in the implementation of countermeasures, but it has actually driven government policy as the OMB (Office of Management and Budget) has recently mandated the use of DNSSEC for all government agencies (here) - Sweet! 2. Cryptography and Cryptanalysis (From Bletchley with Love) From the Greek Historian Polybios to the German surrender in May of 1945 to ECHELON, cryptography and cryptanalysis has played a major role in our lives. It has shaped the outcome of wars and changed foreign and domestic policy. It is becoming the cornerstone of the highly distributed, intermittently connected world of technical gadgetry we live in and can make the difference between coverage on the front page of the Wall St. Journal vs. a brief mention in a disgruntled employees blog - Although I wouldn’t argue that encryption as a technology is without flaw, the theory and practice of hiding information and it’s dance partner code breaking, continue to drive some of the greatest advances in information security. 1. Planning, Preparation, and Expectation Setting (Caution: Water on Road, may make road slippery) Yes a bit of a yawner but since the beginning of forever more failures, more disastrous outcomes and more security incidents result from a lack of proper planning, preparation and expectation setting than all the exploits of all the hackers of all the world combined. As an analyst it became shockingly clear that the majority of failed technology deployments were not the result of a failure in the technology, but a result of poor planning, a lack of preparing and little to no expectation setting, the entire “trough of disillusionment” is riddled with the waste of mismatched technological expectations. The greatest idea in security is not sexy, funny, or terribly enlightened, but it is simple, achievable, repeatable and can be immediately implemented today - plan, prepare and set the proper expectations. Some may argue that something has been forgotten or that the order is wrong, but I would argue that we must learn to develop securely, implement the proper security controls, verify the functioning of these controls, leverage the research of the greater community, ensure that what cannot be protected is hidden, and from the beginning to the end properly plan, prepare, and set the right expectation - these are the greatest ideas in security and if we learn to embody these principles, we would be moving the industry forward as opposed to constantly feeling like we can only clean up the incompetence that surrounds us.  |
| Google Gets Chrome On Your Browsing [Liquidmatrix Security Digest] Posted: 01 Sep 2008 07:08 PM CDT  Google has managed to do what most people have been speculating on since they picked up the GreenBorder folks back in May 2007. Word came out today that Google will making it’s own foray into the web browser market space. The browser named Chrome, will have it’s own Javascript virtual machine called V8. “Should had a…” a little marketing genius. One piece that I’m initially wary of is the auto-completion feature in the address bar of the browser. Personally I’m never too keen on the system trying to decide for me what I’m really looking for. Google has also taken a page from the Opera browser with their use of a “speed dial” feature which for its default home page. Imitation being the sincerest form of flattery. The google browser will also have a “porn view” mode much in the same vein of the proposed IE8 feature. Google gears will be installed by default. From blogoscoped:
I’m looking forward to getting more detail on the new browser offering when they release it tomorrow. From Googleblog:
Looking forward to this. UPDATE: Google has a released a comic to explain the new release. 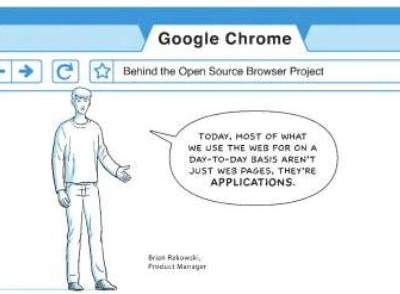 Tags: Google, Google Chrome, Google Browser |
| Russian Web Critic Shot Dead [Liquidmatrix Security Digest] Posted: 01 Sep 2008 06:15 PM CDT Free speech gets another kick in the twig and berries in Russia. Journalists and bloggers there seem to have a bad habit of dying from sudden high velocity lead poisoning. One such vocal critic of Putin and company was shot dead on Sunday under questionable circumstances. Namely, while in police custody. Interesting wording on the cause of his death. On Reuters:
On AFP:
OK, I have to wonder what the Russian words for “bullshit” and “murder” are at this point. Sadly, I have $10 that says this case will never be resolved. |
| Lawyers: Gonzales Mishandled Classified Data [Liquidmatrix Security Digest] Posted: 01 Sep 2008 05:46 PM CDT  Alberto, how we’ve missed ya. Our favourite memory challenged Bush staffer is back in hot water for his apparent mishandling of secret government documents. From WOKV:
Hmm, shoud make for some interesting headlines on Tuesday. Oh wait. There’s the storm in the Gulf. And the RNC are having their shindig. I’ll be surprised if this gets any press time on CNN, MSNBC et cetera. For the full article, read on. |
| Google Chrome Security First Look [RioSec] Posted: 01 Sep 2008 01:37 PM CDT Google has announced a new browser, called "Google Chrome" that aims to improve the way applications are delivered on the web. In typical Google fashion, they've created a comic book that depicts the features of the new browser. The browser should be officially released tomorrow at www.google.com/chrome (not yet live). Below are a more details I've gathered about the security features of this upcoming browser. As they say in the comic book "when we started this project, it was a very different landscape from when other browsers started." This difference in focus is apparent due to the plethora of announced design decisions which, if done as stated, should create a much more secure browser. Read on for some of the details. |
| UK Hacker Gary McKinnon Loses Appeal Against Extradition [Darknet - The Darkside] Posted: 01 Sep 2008 01:01 PM CDT So the latest news with the Gary McKinnon case that was he was trying to fight against Extradition, he started off with Appeals against US Extradition, then he Won The Right to Lords Appeal Extradition Hearing and then he lost the Lords case then went for the European Court. Sadly it seems he lost his appeal [...] Read the full post at darknet.org.uk |
| links for 2008-08-31 [Andrew Hay] Posted: 01 Sep 2008 01:02 AM CDT |
| Microsoft Patents ‘Page Up’ and ‘Page Down’ [Liquidmatrix Security Digest] Posted: 31 Aug 2008 09:17 PM CDT Absurdity, thy name is Microsoft. I have heard of some dumbass patents over the years but, this one is an example that the US Patent Office really needs to undergo an extensive review. From ZDNet:
Yes folks, that would be “previous art”. Hell, I still have one of those keyboards in my closet. I’m going to bed. That’s where I get to be a Viking. |
| Privay, please.. la serie continua. [varie // eventuali // sicurezza informatica] Posted: 31 Aug 2008 05:08 AM CDT Questa volta, per proteggere la nostra privacy, abbiamo una versione estiva grazie all'uso di un telo mare:  (grazie a Mara e/o Oreste) Per la vostra privacy, restano sempre valide la versione da piscina, quella invernale e quella da campeggio, senza dimenticarsi la versione fru-fru. |
| End Summer Camp 2k8 [varie // eventuali // sicurezza informatica] Posted: 31 Aug 2008 04:35 AM CDT Volentieri segnalo:
|
| Let’s fix the Web [GNUCITIZEN] Posted: 31 Aug 2008 03:12 AM CDT I am heavily frustrated from the way the Web works today. Everything seems to be broken beyond reason. I really want to fix the damn thing but I realize that it is not up to me to do that. It is up to all of us to make sure that code is written in the most secure possible way. Can we do that? Perhaps not! What can we do then? Before I get to the point, I need to tell you how I fixed my insecure Wordpress blog. Wordpress has many security shortcomings and I was so frustrated that I decided to fix whatever I can once and for all. I believe that we can fix the Web in a similar way, but first these are all the patches that were implemented:
I believe that this makes the blog a lot more secure. There still might be ways to attack it but this is all I can do in the most reasonable possible way, without completely breaking Wordpress. All of these fixes are implemented as a plugin which I will make available for free download soon. So how can we fix the Web? I have a few ideas in mind and all of them can be implemented in a plugin. Here they are:
I think that this type of solution will make the Web a lot more secure. It definitely wont fix it, but it will make Sidejacking attacks not easy. It will block the majority of CSRF and XSS attacks. It will provide certain mitigations against persistent XSS attacks. It will provide some mitigations against Browser exploits which employ Flash or Java technology to root the browser. It is not perfect, but it looks good enough to me. Next stop: fixing the browser! |
| PaulDotCom Security Weekly - Episode 120 - August 28, 2008 [PaulDotCom] Posted: 30 Aug 2008 10:03 PM CDT Paul & Larry rock out to some punk music and bring you the latest security and hacking news!
 Hosts: Larry "HaxorTheMatrix" Pesce, Paul "PaulDotCom" Asadoorian Email: psw@pauldotcom.com |
| QuickPwn an iPhone [Network Security Blog] Posted: 30 Aug 2008 01:34 PM CDT The Mac version of QuickPwn is up and worked flawlessly for me! I’ve already installed Metasploit and a terminal program, though I haven’t really had a chance to play with either of them yet. And now that I’ve written that I’m not having problems, the iPhone just rebooted on it’s own. I’ll know soon if that’s a problem of the jailbreak. The phone’s back up but I don’t see either the Metasploit or the terminal programs available. I’ll look through to see what’s required to enable them. Got the terminal program working, now playing with some of the other capabilities built in tho Cydia. The link on the QuickPwn developer site seems to be down, so here’s an alternative link to the QuickPwn files. |
| Posted: 30 Aug 2008 01:01 PM CDT Passing through Portland's PDX Airport, I was struck by this ad for SeaPort Airlines:  It's actually sort of impressive how much hate and resentment the TSA has built in the few long years of its existence. |
| WaterISAC Document Leak Cover Up Failed [Liquidmatrix Security Digest] Posted: 30 Aug 2008 12:49 PM CDT  Security is an interesting thing. Some people get it. Others just have no idea. A few days ago Myrcurial found that a DHS document had been erroneously posted on the Water ISAC site. Mistakes happen lets be fair. But, rather than say “Yup, we goofed. It won’t happen again and here’s why” the rather apt description of the Keystone fellas reared its head, again. An email was sent out on the SCADA security mailing list instructing folks to cease talking about this issue (thx to anonymous for the copy). 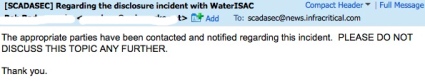 So, being a curious sort I went to the publicly accessible archive to view the message thread so I could catch up on the story. 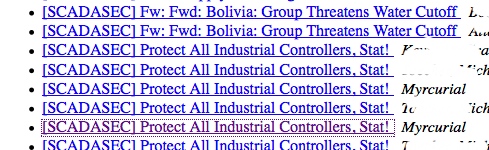 Only to discover that any message relating to the document posting was now deleted. Guess they might have forgotten that every subscriber on the list also has a copy. 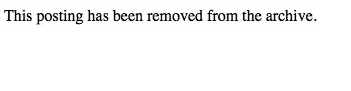 How can one ever hope to have a frank and open discussion about security in the critical infrastructure space when the default action is to close your eyes and bury your head in the sand? Anyway. So, I decided to go have a look at the archived document on Google. Nope, not there anymore. Guess someone had Google take the link down. Well, that showed me. Or did it? Oh right, there are other search engines besides Google. You might of heard of some of them like say a small little site called Yahoo? 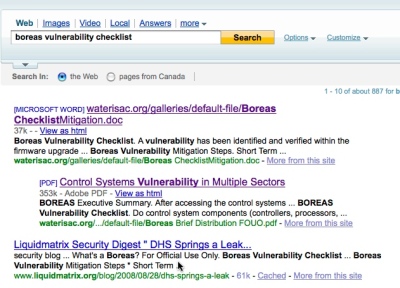 Yup, they have an archived copy as well. As will the rest of the search engines out there.  What’s the moral of the story? Once the genie is out of the bottle on the internet there really is no way to get that sucker back in. As our readership from the various three lettered agencies can attest. WaterISAC and other organizations that have critical infrastructure roles really need to review their document classifications and how things get published to the web. Seriously, this isn’t rocket science. Be a little more careful next time folks. Oh, and WaterISAC, please turn off directory browsing on your web server. Tags: WaterISAC, FOUO, DHS, security advisory, boreas |
| Bookmarklet of death: Domain hijacking without 0days [GNUCITIZEN] Posted: 30 Aug 2008 06:49 AM CDT So we all know about cross-domain vulnerabilities that allow attackers to run code within the security context of the target domain. Typically, they are either a XSS bug on the server-side application, or a bug in the client (web browser plugin or web browser itself). Most of the times, these vulnerabilities require some type of interaction from the victim user. i.e.: being tricked to click on a link or visit a malicious page. Now, most techies are familiar with bookmarklets. Well, what’s funny is that many users with knowledge of security - including many infosec professionals - are not aware of the security implications of running a bookmarklet. The two most common ways to run a bookmarklet are:
On one hand, a bookmarklet is a piece of JavaScript that allows you to do something cool with the current webpage. On the other hand, from a security point of view, a bookmarklet is scripting code injection within the security context of the current domain/site by design. Or put it this way: you’ve got the equivalent of a XSS vulnerability in the target site or a cross-domain vulnerability on the web browser. Except that you don’t need to discover a new vulnerability. No 0days required! So like in cross-domain vulnerabilities we can inject payloads that allow us to:
Also, as in cross-domain vulnerabilities, there is some level of user interaction required: in this case, the attacker must trick the victim to run a bookmarklet while on the target site. So how can we increase the chance of the victim being tricked to run a bookmarklet? Well, a nice trick is to use a fun and flashy bookmarklet, such as one that reads the images of the current page and creates an animation with them. You could of course write the code from scratch, but we won’t do that as we’re too lazy aren’t we? Instead, we’ll trojan a publicly available (fun and flashy) bookmarklet with our malicious code. In this case, our malicious payload steals the victim’s cookie for the purpose of hijacking his/her session. Notice that the cookies would be sent to x.php which the attacker would need to host on his/her site. This PHP script sends any received data (cookie in this case) to the attacker’s email: Notice the malicious payload is within JS comments. There is nothing special about the evil code. It simply creates an image tag which results in the victim’s cookie being sent to a third-party site in the background. The non-malicious payload will also execute, which results in the images of the current page moving around the screen. It’s quite neat, as the user won’t notice anything suspicious actually happened. Needless to say, you need to replace You can picture this kind of attack actually happening in sites where there are cross-user functionalities. i.e.: social networking sites such as Facebook, MySpace and so on … Thinking about the dangers of running a bookmarklet brings us to the next question: Why in the world do browsers NOT show a warning before running a bookmarklet? After all, browsers do display warnings for other potentially dangerous actions such as:
I do understand that it would be annoying to warn users every time they run a bookmarklet, but I think it would be sensible to show a warning at least the first time a given bookmarklet is executed. If you work for a popular web browser vendor such as Microsoft or Mozilla, you can think of this as my wish for the day! I’d love to hear your feedback if you are reading this! |
| PhishGuru Training System [Jon's Network] Posted: 30 Aug 2008 01:11 AM CDT
|
| Firefox Better than Safari on MobileMe [Jon's Network] Posted: 30 Aug 2008 12:17 AM CDT
My wife uses iWeb to maintain the family website. A couple of weeks ago, the comments stopped working. I figured it was just another MobileMe problem and planned on switching to Wordpress or something. Tonight we noticed that people were leaving comments. We viewed the site in Firefox and the comments worked. Comments on our MobileMe hosted webpage do not work in Safari. Here are the comments viewed with Safari:
Here are the comments viewed with Firefox:
If anyone has any idea how to fix this, feel free to let me know, but I’ll probably be moving it over to another platform soon. Marsedit and Wordpress will be just as easy iWeb. As far as I’m concerned, MobileMe is alpha software. A few minutes on their Apple’s support site shows as much. |
| Not the smartest... [The Security Shoggoth] Posted: 29 Aug 2008 03:30 PM CDT I was looking at a bot the other day I received though email. The "botmaster" (and I use that term loosely) was using mIRC-based bot, something I haven't seen in a long time. It wasn't packed, didn't perform any tricks to get installed, etc. Everything screamed amateur. So, I ran it through my honeynet and just sat there and watched. Since it was mIRC I could open it up and just watch the channel. To my complete amazement, after confirming I was a bot (by asking me to echo some text back to him) the "botmaster" gave me admin access to the IRC channel. Huh!?! (In the picture below the botmaster is @Gigi, my infection is @Childse.)  So, what is a self-respecting malware analyst like myself to do? Oh, I don't know. :)  |
| 2012: Internet Armegeddon, Preparing for the Eventual End [Amrit Williams Blog] Posted: 29 Aug 2008 02:00 PM CDT Well my friends the end is near, no more internet porn, no free downloading of pirated movies or music, and for me personally the most devastating will be the loss of LOLCatz. Recent highly public vulnerabilities against the core routing infrastructure of the Internet, such as the DNS or BGP vulnerabilities, highlight what some already knew - we have built an industry on an inherently weak foundation and these are clearly the first signs of the apocalypse. The eventual end was prophesied in the 16th century by Nostradamus in his 15th quatrain
And written in the book of Revelations 9:13-17
It is far more likely that nothing will happen and by 2012 we will deploy converged technologies that allow one to bank online, listen to Britney’s daughters new album “Freaknut”, write their blog, program their HVAC, and toast a bagel from their wirst watch, of course some 15 year old Chinese kid with acne, an anti-social disposition and advanced computer skills will now be able to burn toast from across the world.  |
| Posted: 29 Aug 2008 11:11 AM CDT  Mary Dudziak posted the testimony of Fannie Lou Hamer before the credentials committee of the 1964 Democratic convention. It's worth reading in full: Mr. Chairman, and to the Credentials Committee, my name is Mrs. Fannie Lou Hamer, and I live at 626 East Lafayette Street, Ruleville, Mississippi, Sunflower County, the home of Senator James O. Eastland, and Senator Stennis. |
| Security Briefing: August 29th [Liquidmatrix Security Digest] Posted: 29 Aug 2008 07:35 AM CDT  Ah, Friday before a long weekend. So happy that the weekend is here. And yet, I find myself looking forward to Tuesday. A new(ish) project that I’ve been working on may finally be coming to fruition. Fun and games. At any rate I hope everyone has a great weekend! Click here to subscribe to Liquidmatrix Security Digest!. And now, the news…
Tags: News, Daily Links, Security Blog, Information Security, Security News |
| ISR-evilgrade - Inject Updates to Exploit Software [Darknet - The Darkside] Posted: 29 Aug 2008 05:55 AM CDT ISR-evilgrade is a modular framework that allow us to take advantage of poor upgrade implementations by injecting fake updates and exploiting the system or software. How does it work? It works with modules, each module implements the structure needed to emulate a false update of specific applications/systems. Evilgrade needs the manipulation of... Read the full post at darknet.org.uk |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |







 A
A 

No comments:
Post a Comment