Spliced feed for Security Bloggers Network |
| Twitter Targeted by Malware Distributors [Darknet - The Darkside] Posted: 05 Sep 2008 02:15 AM CDT This one is of interest to me as I do actually use Twitter as a microblogging service and to keep up with what various friends are up to. It’s quite an interesting wep app especially paired with something like Twitterfox in your browser and Twibble in your mobile phone. It must have made it big now though [...] Read the full post at darknet.org.uk | ||
| Posted: 04 Sep 2008 11:05 PM CDT Here is some of the recent press coverage on topics relevant to content on my blog:
Podcasts/Webcasts/Video:
I am confirmed to speak at the following upcoming events:
I will be attending the following events:
/Hoff This posting includes an audio/video/photo media file: Download Now | ||
| Wisdom from Randy Pausch [Kees Leune] Posted: 04 Sep 2008 08:16 PM CDT Everyone who reads this post has probably heard of Dr. Randy Pausch's world famous "Last Lecture". Anyone who has not heard of it must stop reading now and go view it.
What else is there to say? As information security professionals, we are faced with this every day. One might even leap to the conclusion that had the field been approached as a mature engineering discipline, there would be no need to have as many dedicated security professionals as we do now. An article well worth reading. | ||
| OPC UA: Part 2 - Positive Findings [Digital Bond] Posted: 04 Sep 2008 02:00 PM CDT Security assessments by their nature focus on negative findings that could lead to vulnerabilities, and the preponderance of our report focused on what Digital Bond viewed as security deficiencies in the OPC UA specification and SDK code. That said, there are numerous examples of positive findings and text in the report. In fact, there is no comparison between the security in OPC UA and the security of any other control system protocol, with the possible exception of Secure DNP3 and its IEC equivalent. The OPC Foundation should be commended for their security efforts and pressure should be applied to other protocols to step up. [Note: The security details of OPC UA are being written on a SCADApedia page as the OPC UA blog series is being published] The major positive security findings are:
See the rest of the OPC UA Blog Series:
| ||
| Protesting Now Considered Terrorism [The Falcon's View] Posted: 04 Sep 2008 01:41 PM CDT | ||
| CISSP Study Sheet Access Control [SecurePuter] Posted: 04 Sep 2008 01:35 PM CDT Series: CISSP Study Sheet | ||
| The Daily Incite - September 4, 2008 [Security Incite Rants] Posted: 04 Sep 2008 08:15 AM CDT  September 4, 2008 - Volume 3, #74 Good Morning:
Top Security News All that glitters isn't Chrome
Top Blog Postings It's a big world and it takes time for them to do anything | ||
| Posted: 04 Sep 2008 06:40 AM CDT How can I not be seduced by technology? I am currently sitting in a bus, traveling through Norway. And using the wireless AP of the bus, I am able to work as normal! I check my email, I update my blog, and I even did a Skype call. How can I not love this? Security? Well, it is a good idea to use VPN, of course, as the connection is open for anyone... | ||
| Are you Owned? [Roer.Com Information Security Blog - Information security for entrepreneurs] Posted: 04 Sep 2008 01:07 AM CDT Anton posted about Cyber Security Plans. I follow you 100%, Anton! There has been a large number of these hijacks lately, and it is obvious that being paranoid is not enough. It is due time to set up your cyber security plan, and as a bare minimum I suggest it should include:
The list will grow. Please help me - what should the Cyber Security Plan look like? What would you do if the worst happens? | ||
| XTest - VoIP Infrastructure Security Testing Tool [Darknet - The Darkside] Posted: 04 Sep 2008 12:39 AM CDT What is XTest? XTest is a simple, practical, and free, wired 802.1x supplicant security tool implementing the RFC 3847 EAP-MD5 Authentication method. It can be used to assess the password strength within wired ethernet environments that rely on 802.1x to protect IP Phones and the VoIP Infrastructure against rogue PC access. XTest is developed in C... Read the full post at darknet.org.uk | ||
| Risk and CVSS (Post 5) *FINAL* [Risktical Ramblings] Posted: 03 Sep 2008 07:57 PM CDT I had no idea that the CVSS topic would turn into a five post series. There was just too much information and thoughts to cram into one or even two posts so for those of you that read even a few let alone all five – thanks for persevering. Final thoughts on CVSS; two good and two not so good: NOT SO GOOD: 1. The CVSS framework is probably not being *fully embraced* or properly utilized by the people that need to leverage it the most – consumers of vendors that use it to score vulnerabilities with their products. Scoring the environmental metrics and observing the impact to the base metrics could add a lot of value. Other frameworks or organizations that reference CVSS scores as part of a vulnerability management process should mention the optional metrics that can influence the base score that a vendor provides. Better yet, maybe throw a disclaimer that the CVSS score listed today may be outdated and needs to be updated. 2. The CVSS risk vernacular needs to be updated. I would recommend that the CVSS-SOG consider participating in "The Open Group" "Risk Management and Analysis Taxonomy" forum. Better yet, the CVSS-SOG should consider adopting the FAIR methodology. Specifically, use CVSS metrics that could factor into FAIR taxonomy elements. Some of the CVSS metrics focus more on impact then on the vulnerability itself. This can be a slippery slope especially when there are no metrics for "threat event frequency" let alone "loss event frequency". GOOD 1. Pretty much all the CVSS metrics have some usefulness and should be able to be used by most information security professionals and especially risk analysts. I am already creating a small utility to use so I can consistently analyze various vulnerabilities and when appropriate – use the metrics as contributing factors for FAIR. 2. Industry adoption. A lot of vendors use the CVSS framework. PCI-DSS references it for vulnerability related PCI guidelines. Just remember, use the whole framework and do not rely upon what is spoon-fed to you by PCI QSAs or value added resellers. If applicable, take back your ability to analyze risk and make informed decisions. There you have it. Again, thanks for reading and submitting comments. The feedback and scrutiny has been well taken and appreciated.  | ||
| Posted: 03 Sep 2008 06:54 PM CDT Synopsis: Blue Box Special Edition #26: Astricon 2007 presentation - "Hacking and Attacking VoIP Systems: What you need to worry about" Welcome to Blue Box: The VoIP Security Podcast Special Edition #26, a 55-minute podcast from Dan York and Jonathan Zar covering VoIP security news, comments and opinions. Download the show here (MP3, 6MB) or subscribe to the RSS feed to download the show automatically. You may also listen to this podcast right now:
Show Content: A year ago in September 2007, I (Dan York) spoke at Astricon 2007 in Arizona, USA, about "Hacking and Attacking VoIP Systems: What You Need To Worry About" My presentation covered a lot of the typical VoIP security threats, tools and best practices but also expanded a bit into specific security issues with Asterisk. Please do keep in mind that it has been a year since this presentation and so some of the issues I mention have been addressed. (Astricon, for those who don't know, is an annual developer conference for those who work with the Asterisk open source telephony platform. Astricon 2008 is, in fact, coming up in about 3 weeks but I will not be attending this year.) The slides for this talk are available from Slideshare: (And yes, at some point I'll sync the audio with the slides.) Production assistance on this Special Edition was provided by Michael Graves who had a very tough task given the poor quality of the recording that I gave to him! Kudos to Michael for getting it to sound as good as it does. Comments, suggestions and feedback are welcome either as replies to this post or via e-mail to blueboxpodcast@gmail.com. Audio comments sent as attached MP3 files are definitely welcome and will be played in future shows. You may also call the listener comment line at either +1-415-830-5439 or via SIP to 'bluebox@voipuser.org' to leave a comment there. Thank you for listening and please do let us know what you think of the show. This posting includes an audio/video/photo media file: Download Now | ||
| Google Chrome Silent File Download Exploit [Hackers Center Blogs] Posted: 03 Sep 2008 06:00 PM CDT As I said my previous post was destined to be outated very soon. This is what appeared few minutes ago on milw0rm and packetstorm:
This script should (I haven't tested it yet, will do it later) trigger a silent download on the client machine. | ||
| Download the 5th Website Security Statistics Report [Jeremiah Grossman] Posted: 03 Sep 2008 03:29 PM CDT Whew, what a mountain of work! I'm ecstatic the complete 5th installment of our Website Security Statistics Report report (all 13-pages) is finally published and available for everyone to see – and comment. I'm also extremely proud that we're able to capture a measurable improvement in overall website security. Good news from inside InfoSec!? I know, weird huh!? We still have a long way to go, but these statistics show we're on the right path and doing the right things:
Today's webinar went extremely well, slides are available for those interested. And some quick numbers: Total Websites: 687 The shiny new WhiteHat Top Ten
Also covered is: Feedback on what other numbers people would like us to report on in the future is very welcome. | ||
| Crazed Bovine Traversal in RL [Room362.com] Posted: 03 Sep 2008 01:13 PM CDT As you may have heard me rant and rave about a special USB stick that downloads contact, messaging, and other information from phones just by plugging them in on Episode 5 of Securabit or read about it via an earlier posting on my blog (Crazed Bovine Traversal). A company called Paraben Corporation went out and made it (Motorola and Samsung support only so far) I first learned about it via CNet’s report “CSI Stick grabs data from cell phones” and you can find it directly on http://csistick.com/ for $199.00 plus you have to buy the accessory “DS Lite” just to read the data on it. (another 99.00). I think they should at least send me one for free for stealing my idea
| ||
| Risk and CVSS (Post 4) [Risktical Ramblings] Posted: 03 Sep 2008 12:09 PM CDT We are now up to the CVSS "Environmental Metrics" group. According to the CVSS documentation, this group 'captures the characteristics of a vulnerability that are associated with a user's environment'. This group is also optional from a scoring perspective and is intended to be completed by someone familiar with the environment the vulnerability resides within. In "Post 1" I mentioned that CVSS does not take into consideration "threat event frequency" or how often I expect to get attacked nor does it take into consideration "loss event frequency"; how often I expect to realize a loss. The "environmental metric" does not fill this void either – but there is still value in being able to quickly analyze vulnerability in the context of these metrics – again, as contributing factors to various FAIR risk taxonomy elements. Collateral Damage Potential. This metric measures the potential for loss of life or physical assets through damage or theft of property. Now real quick, I scoffed when I saw the loss of life – and none of the risk issues I have ever dealt with ever involved estimating loss of life. However, there are real life examples of software defects (essentially vulnerabilities) that have loss of human life implications. Take a look at "Geekonomics" by David Rice, there is some fascinating information in the book that will give you a whole new perspective on vulnerabilities. Getting back on track, the collateral damage metric maps very well to the "probable loss magnitude (PLM)" branch of the FAIR taxonomy. I do not want to dive into PLM right now – but let me state this – the word potential is not the same as probable, nor does it imply expected loss. So with the CVSS metric it could be very easy for someone to err on the side of a worst case loss versus choosing a value that best resembles expected loss. Either way, with CVSS this would just result in the CVSS score being raised. I would prefer to see a value in terms of dollars; whether it is monetary ranges or actual expected loss amounts based off simulations. Target Distribution. This metric measures the proportion of vulnerable systems. I like this metric and I think it can be very useful as a contributing factor to the FAIR taxonomy element "threat event frequency"; specifically "threat contact" and possibly "threat capability". The number and placement of vulnerable systems in my environment could directly factor into how often or what type if threat agents I expect to come into contact with the vulnerable systems – let alone attack them. Remember, within FAIR – attacking an asset with a vulnerability does not guarantee loss. We have to take into consideration the ability of the attacker to overcome the control resistance applied to the asset. Security Requirements. These metrics enable the analyst to customize the CVSS score based on the importance of the affected IT asset to a user's organization in terms of confidentiality (CR), integrity (IR), and availability (AR). Possible values include: LOW, MEDIUM, HIGH, or NOT DEFINED. These metrics were designed to work with the CVSS "Base Metrics" group; specifically the CIA Impact metrics. So if the vendor analyst states that a vulnerability has a Confidentiality Impact, and the analyst for the organization that has the vulnerable asset states that her or his organization has a Confidentiality Requirement – then the CVSS score could increase. Sounds pretty straightforward – seems to map nicely into the PLM branch of the FAIR taxonomy. Specifically, as contributing factors to estimating loss should the vulnerability be exploited and a loss occur. It is too bad that the CVSS environmental metrics are optional. I understand why they are and regardless of CVSS generating a score and not taking into account loss event frequency - just imagine how much more informed a security folks and decision makers could be if they took a few more minutes to analyze a given vulnerability and the CVSS score that was provided to them from a vendor in light of these metrics. In the next (and final) CVSS post, I will share some final thoughts on CVSS and finally put a nail in what was not intended to be a series of posts. Thanks for reading!  | ||
| Are the weather people disappointed? [StillSecure, After All These Years] Posted: 03 Sep 2008 12:04 PM CDT Is it me or do you all feel that the media people covering recent hurricanes seemed almost disappointed that Gustav and some of the other storms have not been as strong as they could have been and not as destructive? I definitely sensed it with the coverage of New Orleans. It felt like the media had gathered for a party and it just wasn't up to the level of carnage they expected. Today though in listening to the weather forecast on Hanna, the next storm coming up, the weather person seemed disappointed that the storm seemed to be losing muster and was not as well formed. Hey, there is plenty of bad news to go around without worrying about a storm that fizzles out. Why not report on the economy, the housing market or any one of the other multitude of problems out there. I for one am glad that the storms are not as bad so far! | ||
| Brass Tax on Chrome [Room362.com] Posted: 03 Sep 2008 10:58 AM CDT So there is already an exploit: http://blogs.zdnet.com/security/?p=1843 There are naysayers: http://www.tgdaily.com/content/view/39154/108/ And then there is the truth: http://www.stillsecureafteralltheseyears.com/ashimmy/2008/09/sucking-the-chr.html I like the design of the tabs and address bar, but I can do that with a theme in firefox. I want my add-ons, even with the memory problems. Chrome is great for Mom and Pap, but for “Internet Power Users” it falls lightyears short on features. So where is the brass tax? IMHO: Firefox > (INSERT CHROME HERE) > Opera > Safari > IE7 > IE8 > IE6 In other news: Yousif Yalda has made it to the coveted “Stupid People” link category, where until now was solely held by Ashley Park. And the hits just keep rolling in:
AUTOMATIC DOWNLOADS? What?! http://www.milw0rm.com/exploits/6355 | ||
| August SCADApedia Entries [Digital Bond] Posted: 03 Sep 2008 10:18 AM CDT SCADApedia - - all can read - - subscribers can write. New entries in August:
A number of the other pages have been updated as well. You may also want to look at All Pages or the links to Control System Vulnerability Notes or the links to Digital Bond’s Research Projects. | ||
| Posted: 03 Sep 2008 09:15 AM CDT Google released its own web browser, named Chrome, yesterday, and many blog posts have already been dedicated to it. I agree with Martin McKeay's judgement: "So what?" The browser seems to have some interesting ideas, but it does not warrant switching over it. I'm not sure if Google is trying to make a serious attempt at getting into the desktop browser market, or if they want to use the product to push the envelope of technology by demonstrating that certain enhancements are possible in production-quality code. The fact that Chrome installs (and runs) on Windows without administrator privileges is interesting though. Another thing that we have to remember is that Google will probably package it with their bundle. Basically, anyone downloading Picasa or Google Earth will probably end up with a copy on their system. Even if they never use that, it is yet another source of potentially insecure code. | ||
| I stole an iPhone... NOW WHAT?! [Donkey On A Waffle] Posted: 03 Sep 2008 08:49 AM CDT I was just spending a bit of time catching up on my blogosphere reading this morning when I was intrigued by a statement made by none other than my brother. Over at his AtariNinja.org blog, he authored a brief piece downplaying the risk of the latest iPhone screen lock bypass hack. While I agree with nearly all of his points, one line stood out from the rest. This is a serious bug but I really don't suspect people stealing iPhones are doing it to get at your personal information. They are likely after the hardware to sell. I'm not entirely sure I agree on this subject. While the comment makes sense at face value, and indeed the majority of iPhone thefts today are primarily geared at the resale value of the hardware itself, why wouldn't a thief at least entertain the opportunity to peruse and potentially abuse the data on the stolen device. Given the fact that it's apparently quite trivial to bypass the phones security screen lock features, what economic opportunity cost is there that would stop a "bad guy" from at least reviewing your data for potential money making opportunities? If a thief steals a car, they wouldn't ignore what's in the trunk and just sell the car (hardware) off quickly. I'd imagine they would pop the trunk (trivial to pass the trunk lock once your in the car) and see what is inside to plunder. Because of the above opinions, the risk of the iPhone screen lock bypass vulnerability is quite high dependent upon what data you have stored in your phone. Sure there are some mitigating factors, as wxs has outlined in his post, but they don't lessen the risk of the vulnerability, instead they only serve to lower the likelihood of exploit. What are you thoughts on the issue? Is the business risk of the iPhone screen lock bypass vulnerability really that high? Or are the majority of criminals in the world just going to wipe and sell your phone to the highest bidder on ebay? I don't know about you, but I'm not leaving my data to chance... (comments are open) | ||
| Humans - the weakest chain in the link? [StillSecure, After All These Years] Posted: 03 Sep 2008 07:57 AM CDT The old adage that you are only as strong as your weakest link is a fundamental truth in security. According to Tim Greene, the weakest link in the chain of protection that NAC can provide is too often the human being behind the computer. Tim relays in his most recent NAC newsletter the experience of a college IT administrator who when they turned NAC on flooded his help desk with calls from students who could not remediate their own computers. This is a real problem. Tim points out that this is a good reason why you should not turn on enforcement right away. This gives you a chance to profile the devices on your networks and work on getting them to look like what you want before you enforce. This is right in line with a "phased approach to NAC", a white paper we have done at StillSecure. It also points out another issue I have written about before. Too many NAC vendors have "self-remediation" as their solution for getting computers up to speed. Fact is for non-IT personnel, self0remediation is just not a viable option. Your NAC product needs to have other options around patching and remediating devices. Also, I just don't understand colleges that are content to test a device once a semester. Tim's article mentions this too. Once you have gone through the trouble of setting NAC up, it doesn't cost you anything more to test these devices every time they come on the network. Defeats the whole purpose if you ask me. | ||
| Sucking the chrome off a bumper [StillSecure, After All These Years] Posted: 03 Sep 2008 07:41 AM CDT There you have it, my entry into the chrome blogosphere sweepstakes. In my years of blogging and more years of reading blogs, I have never seen such coverage of a new product launch or any other topic for that matter. Maybe I should start a Chrome Bloggers Network? Did Google pay bloggers to write about it? Did I miss the memo about the prize for the best blog post on Chrome? Personally, the geek in me had me download it. I played with it, looked at a bunch of sites and than put it in the same place I keep Safari. No icon anywhere on the desktop and who knows if I will open it again over the next year. I like Firefox. I hope the Google marketing machine will not hurt the Mozilla team. | ||
| Bandolier Update: New Applications on the List [Digital Bond] Posted: 03 Sep 2008 07:25 AM CDT Big news for Bandolier… last week at the PCSF Annual Meeting (now called the Process Control Systems Industry Conference), we presented on the project and unveiled an updated list of audit files. Newcomers include the AREVA eTerra and Emerson Ovation applications among others. Check out the complete list in the presentation or over at the List of Bandolier Audit Files SCADApedia article. We are excited about the crossection and industry saturation represented in the Bandolier project. Don’t forget, some of the audit file are available now in alpha versions. Stay tuned for a beta release of those and several more from the list. As always, we welcome your feedback and look forward to getting more of these audit files into the hands of asset owners and operators. |
| You are subscribed to email updates from Security Bloggers Network To stop receiving these emails, you may unsubscribe now. | Email Delivery powered by FeedBurner |
| Inbox too full? | |
| If you prefer to unsubscribe via postal mail, write to: Security Bloggers Network, c/o FeedBurner, 20 W Kinzie, 9th Floor, Chicago IL USA 60610 | |





 Yes! CSRF finally make the list!
Yes! CSRF finally make the list!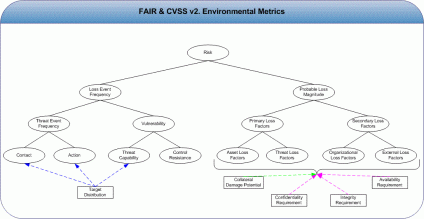
1 comment:
Wow, you have a great blog. Very informative too. I’ll be visiting next time…
Blackened Fish Recipe
Post a Comment